The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

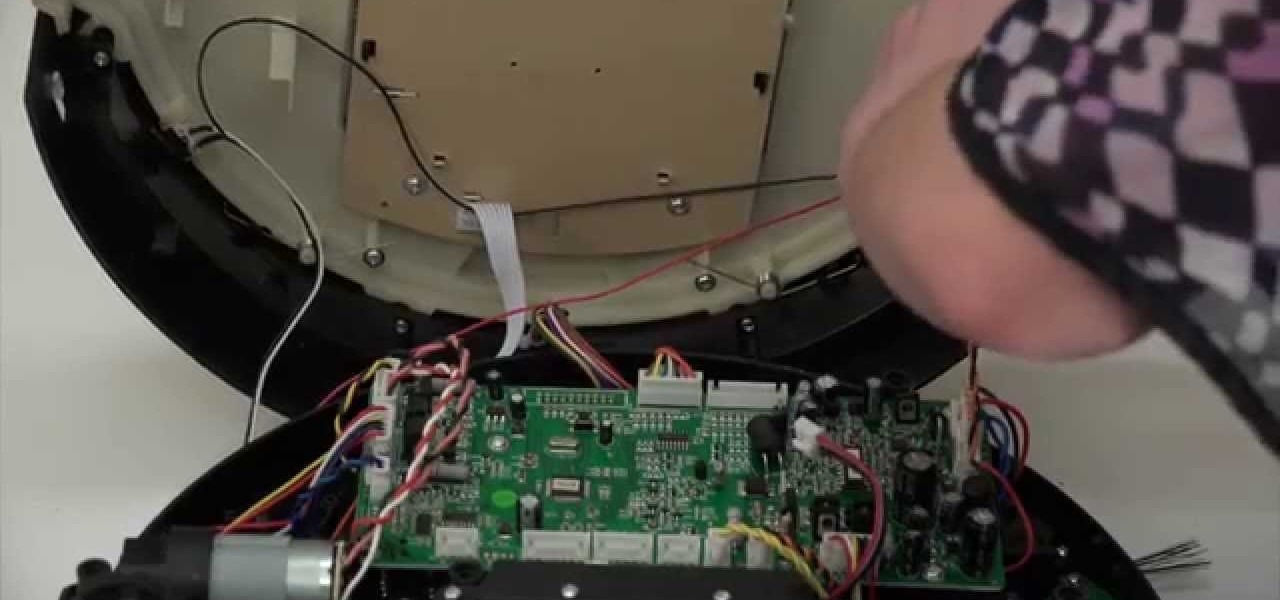
A step-by-step guide to replacing the side brush motor on bObsweep Standard or Pethair. Follow the video or multimedia directions in order to open up bObsweep, remove the main board, replace the side brush motor, then close your vacuum for future use.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

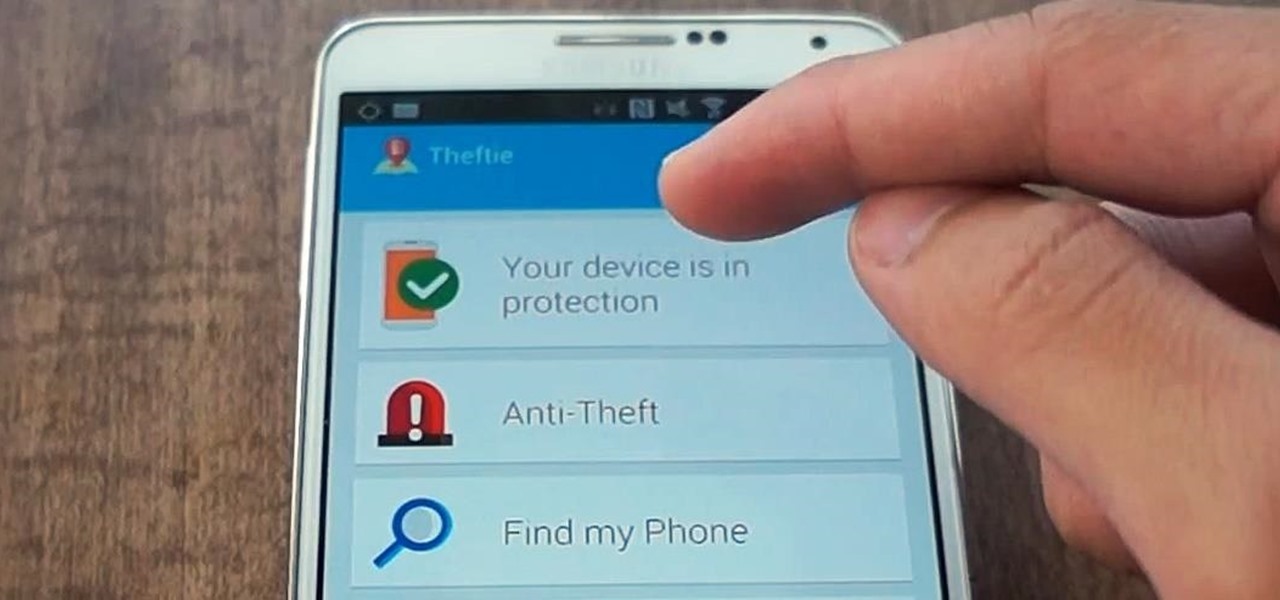
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

How to make a simple yet effective stand for your phone or tablet / iPad. Great for watching films or reading recipes whilst you cook.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

This absolutely Wonderful Pick of the Day could not be more conceptually different from yesterday's Pick. (Therein lies the fun of curating our site.)

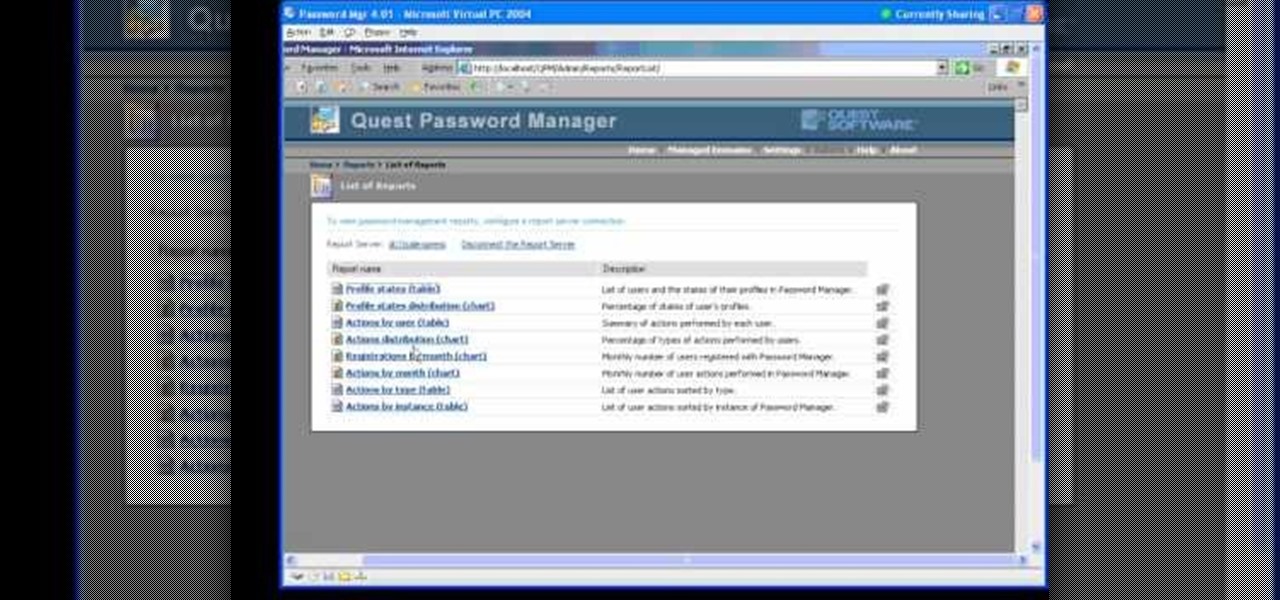
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

This video shows you how easy it is to use an OSI swinging trailer hitch mount bike rack. Learn how to put bikes on it, secure and lock them.

It's almost as easy as it sounds - just don't forget to secure the cover to the spare tire by the two hooks. This video shows you how to put on a spare tire cover.

The SportRack bike rack lock kit can be easily added to many of the SportRack model racks. It includes two locks, one that secures the bikes to the rack and another that locks the rack to your trailer hitch. It only takes a minute to install and is dead simple to use, as this video demonstrates.

Watch this video for instructions on making the Yukki Cross Artemis scythe from the anime / manga Vampire Knight.

By using sewing pattern Simplicity 4670, the author of this tutorial video takes you through the steps needed to produce a great shirt collar. First you should attach interfacing to one piece of the shirt collar. Here you will be using fusible interfacing and taking the facing to the shirt collar iron the interfacing to the wrong side of the fabric. Sew a guide line that is 5/8ths of an inch wide along the notched edge of the shirt collar's facing piece. At the dot markings of the collar clip...

When is a knot not a knot? When it's a grip. The knot outlined in this video isn't a knot per se but a way to wrap objects to increase their grip and also to store extra paracord. Specifically, this video demonstrates how to County Comm Micro Widgy Bar, which is a miniature pry bar. It’s made from hardened D9 steel and is around 3? in overall length.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

Botanically, tomatoes are fruits, but an 1893 Supreme Court decision changes that. They were ruled to be considered vegetables, allowing for a higher tax to be placed on imported tomatoes. Seems silly now. Tomatoes are rich in vitamins A, C, and K, as well as lycopene, a cancer-fighter. Enjoy tomatoes throughout the year by canning your summer harvest.

This video shows everything about how to put on a rented tuxedo. When you get your tux, the shoes will be hanging in a bag on the outside of the bag. Inside the bag will be the coat, shirt, vest or cummerbund, tie, pants and studs and links. Socks will be in the inside coat pocket, and the pocket square should be on the outside pocket of the coat. Remove the studs and links from the bag. Leave the collar button alone and start with the next button hole. Put the studs through the holea. Insert...

Here's how to make this Middle Eastern delicacy. You Will Need:

Learn how to make a bike repair stand with this video! Create the legs: 1. Two sets of 8 and 10 inch piece of steel pipe, a 90 degree angle, an end cap and a T pipe are the starting materials. About 0.5 inch diameter pipe is fine for the project.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.

If things are getting a bit stuffy at your desk, don’t fret. A cool breeze is just a USB slot away. Watch this video to learn how to make a USB fan.

Learn how to immobilize an ankle. The ankle is a complex joint, so when an injury occurs, and you can't get help right away, the first thing to do is keep it from moving – you'll prevent any more damage to the surrounding nerves and tissue.

Instead of pushing, pulling, and cursing, why not fix that door that sticks? You Will Need

Learn how to give your daughter a trim and you’ll save big bucks on trips to the hairdresser. Learn how to give a child a haircut, at home. This is a cost effective tip that will help you save money.

In this stage design and construction video series, learn how to build one of those small “portals.” Our expert—a director, actor, and producer himself—will show you tips and techniques for building a small, mobile stage that can be set up anywhere you or your acting troupe decide to give a performance. This step-by-step guide to stage construction includes clips on what tools and materials to use, how to measure and cut the frame, what type of bolts to use for ease of tear down, and how to b...

This is a tutorial showing you how to mod a ps2 slim. This will allow you to play backups as well as Guitar Hero 2 customs. If you want to learn how to make your own copy I might put up a video for that. This tutorial also shows the swap trick in action.

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

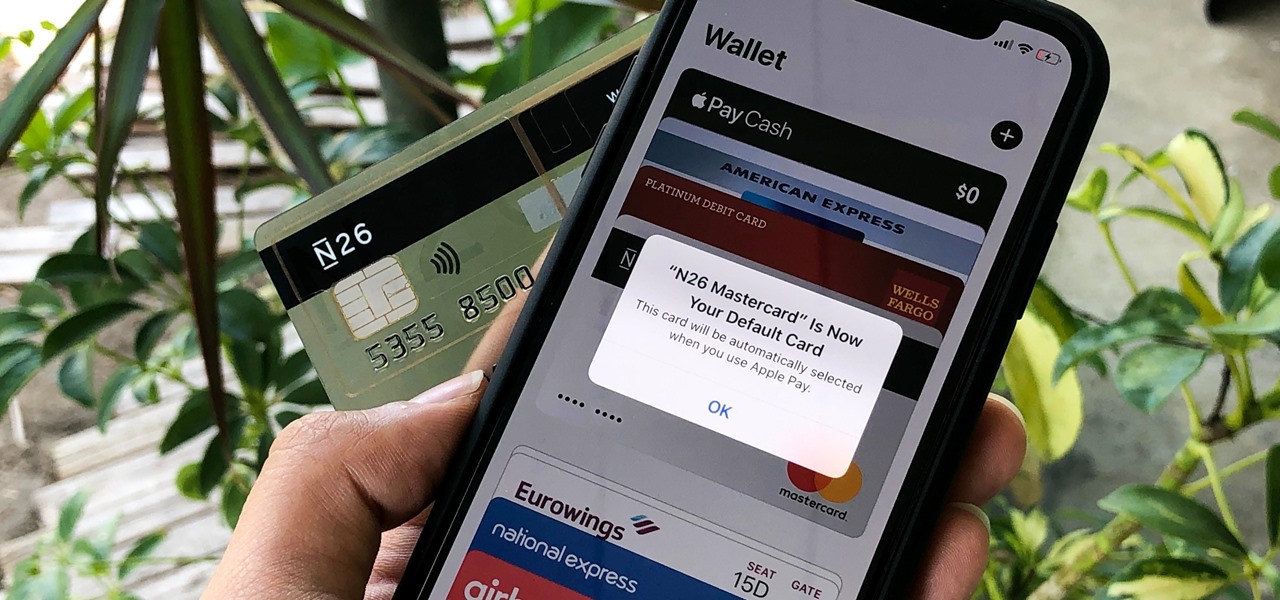
Using Apple Pay in stores to make purchases is as easy as holding your iPhone near the NFC reader and authenticating with Face ID or Touch ID. That method uses the primary payment card in Apple Wallet automatically, and your primary card may change from week to week based on your spending, so you'll probably need to change it periodically.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.