Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.
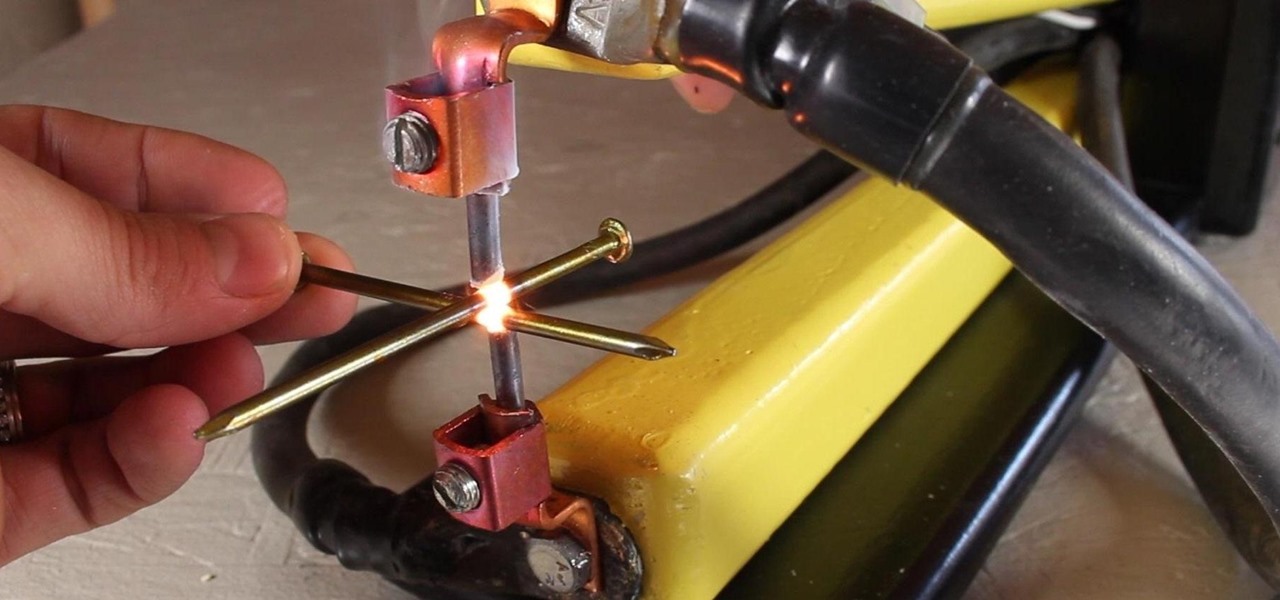
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

Grab your long-handled wooden spoon and let's get to bed making. There is a science in making the immaculate and consistent military-style bed. Use this method at home and know that your making your bed just like soldiers do every day.

In this tutorial, we learn how to build a PVC greenhouse. The dimensions of this will be 12' x 18'. First, you will use 1/2" PVC pipe that is 12' long that crosses in the middle to make a "t" shape. The frame can be made of treated 2'x 4's. Once you have the frame up, you can use thick plastic to securely cover the pipe and wood and clamp it into place. Once you have this done, you can place your tables inside of the greenhouse and start growing your plants! If you notice the plastic not hold...

In this tutorial, we learn how to get rid of wasps and hornets without using chemicals. Take a piece of bacon and wrap it around a stick. Then secure that stick by hanging it over a bowl of water with dish soap on it. The bacon will entice the bees to come towards it. Then, the bees will eat so much bacon they will have a hard time flying and they will end up flying down into the bowl of water. Then, the soap will make them be able not to fly and they will drown in the water. This is very eff...

There are two basic ways to twist hair so that it lies on the scalp. One way to twist the hair is to section the hair into the desired size of segments. Use one hand to twist the hair with the thumb and forefinger while holding the hair down secure with the other hand. Another way to twist hair is to separate the section into two pieces. Twist one section over the other and pick up another piece while twisting the strand around again. This will feel similar to braiding, but with only two stra...

Happy140 demonstrates how to fold and wear a bandana. Folding a bandana and placing it securely onto your head for everyday use is easy using a few simple steps. The first step is to take the bandana and fold it into a triangle so that all the points touch each other and are even. Then, fold the top point down so the bandana forms a trapezoid shape. The next step is to fold the bandana in half lengthwise. Wrap the bandana around your forehead. Tie the ends of the bandana into a knot behind yo...

This video is a tutorial explaining how to erect a tipi shelter. You must make sure all poles are 11' by 10' to have the correct height tipi. The instructor then aligns three marks and ties a clove hitch around all three poles. The next step is to raise the pole by using the rope to keep the structure stable. The next step involves putting the covering onto the lead pole and the bring the covering around 360 to complete. The last step involves securing the covering with rope by tying a knot a...

This video demonstrates how one can makes a homemade paint ball caddy on the cheap. The presenter uses a gallon sized kitty litter bucket. The presenter only spends $8.00 on the kitty litter bucket at Costco and it will hold at least two bads of paint balls. The presenter demonstrates how he added another screw top lid to the kitty litter bucket. By simply cutting a circle the same size as an existing screw lid and then super gluing the lid inside the kitty litter bucket, you have a secure se...

Find the indication light, located at the top of the Whirlpool refrigerator just inside the door. This tells you when to change your water filter. A green light indicates the filter is good and a red light indicates you need to change the filter.

Make sure your electronics gear stays in order! And make sure your running wires are safe. Check out this video tutorial from the Good Idea Guys at Good Buy Guys to learn how to tape down a cable correctly. Keep those microphone cables, audio cables, and extension cords secure and safely underfoot. Tape Tex shows you how in "How to Tape Down a Cable". A great helpful tip for cable safety.

This video discusses the basic steps necessary to start an online business. The first thing you need is a name for your business. Keep it simple, easy to spell and remember. Once you have your name, register it with the government. Next, find a good hosting company for your website. He recommends Godaddy.com. Also a good web designer is a necessity. They will meet with you to discuss your ideas, and your website should be ready in about a week.

It's summer again and it's time to get out of the house and there's no better way than with a fun game like some improvised baseball. You don't need a whole team of people all you need is a bat, a ball and another person to play with.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

Keeping the books in order is one of the great challenges every business owner faces. Having a great product or service is one thing, but managing the minutia of invoicing can trip up a lot of small- and medium-sized businesses.

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

If your phone has an A/B partition layout, there are two virtual hard drives that each contain a copy of Android. After every restart, it picks a partition to boot from, then the other lays idle. The idle partition can be overwritten with a new copy of the OS and it won't affect the active one. So the next time you reboot, it just switches partitions and it's as if you updated instantly.

When you place your iPhone over a card reader for Apple Pay, it'll always pull up your default card. That might work fine for you, but perhaps that isn't the card you want to use. The problem is, you don't have time to switch cards before the payment goes through. That might result in using your rewardless debit card to buy groceries when you could've snagged 2% back by using your Apple Card.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.

If you're an iOS developer, welcome back to beta testing. Apple just released the first iOS 12.4 developer beta today, Wednesday, May 15, just two days after the public release of iOS 12.3. While Apple has not shared any release notes, we know this latest version of iOS will support Apple Card, Apple's upcoming credit card.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

In keeping with its focus on loading the Magic Leap One with content at launch, Magic Leap has inked a creative partnership agreement with augmented reality production studio Square Slice Studios.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Uber is one of the best ways to get around, but nobody said it was cheap. What's even more infuriating is when you have a bad experience with a ride. Sure, you can get a refund, but then you need to figure out where to enter in the promo code for the coupon that Uber sends your way.

The Essential Phone was undoubtedly one of the most underrated phones of 2018. It launched with buggy software and camera problems, but the company worked diligently to push out updates. Many Android enthusiasts were anxiously waiting for the Essential 2 release later this summer. Unfortunately, news today from Bloomberg indicates that Essential will not release a phone in 2018.

Move over, Hype Williams, it looks like Snapchat is about to take some of your music video-making business, and pop rock group Maroon 5 is the proof.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.