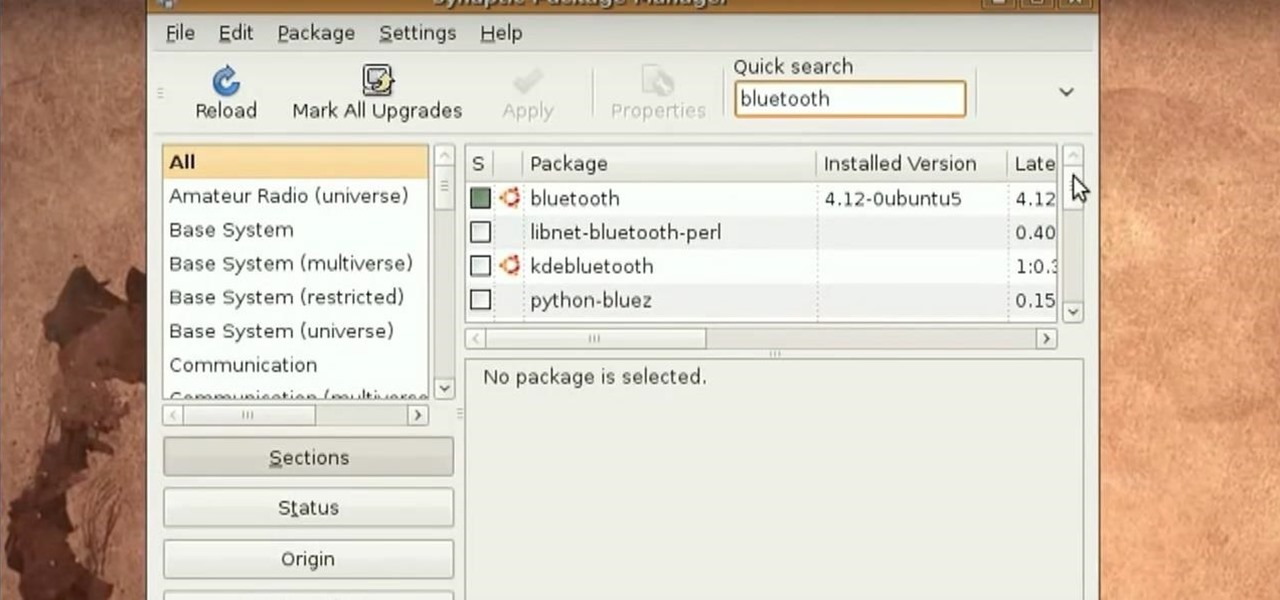
You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.

In order to begin, you will need the following: Three hair tiesBobby pinsHair spray or spray gelRat tail combHair net
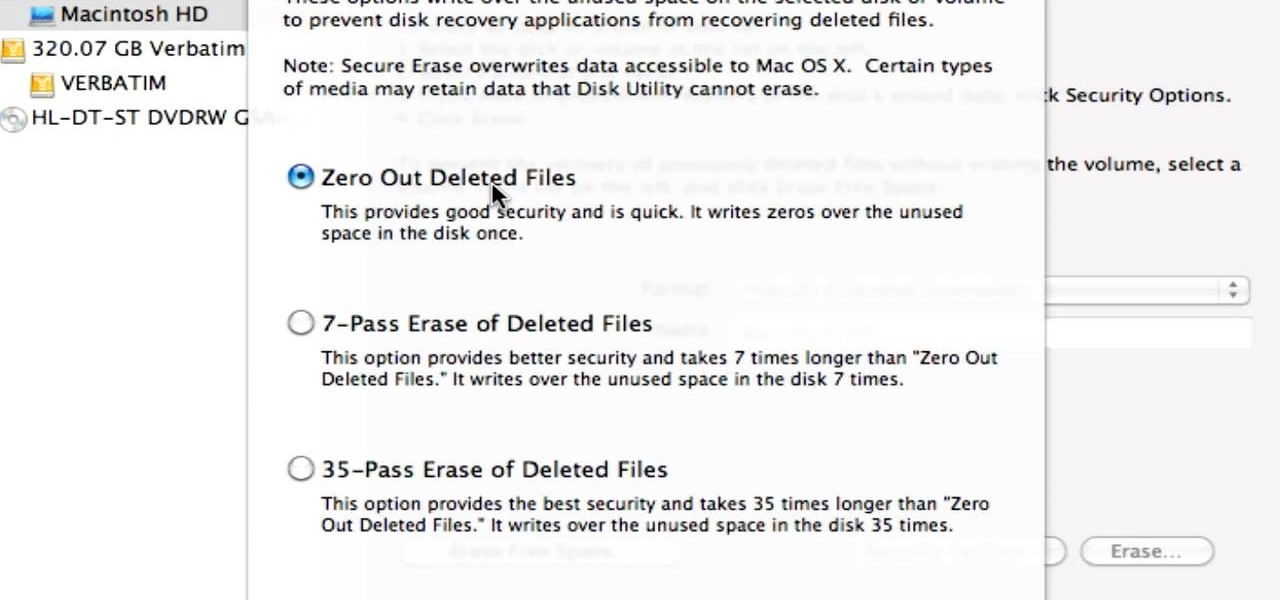
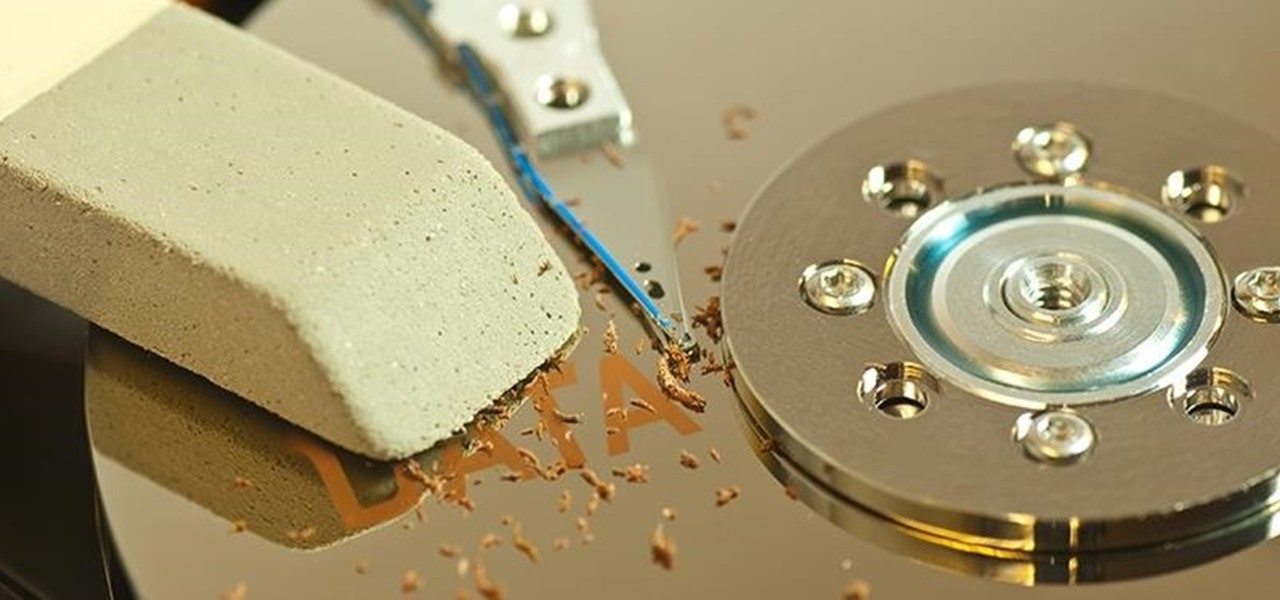
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...
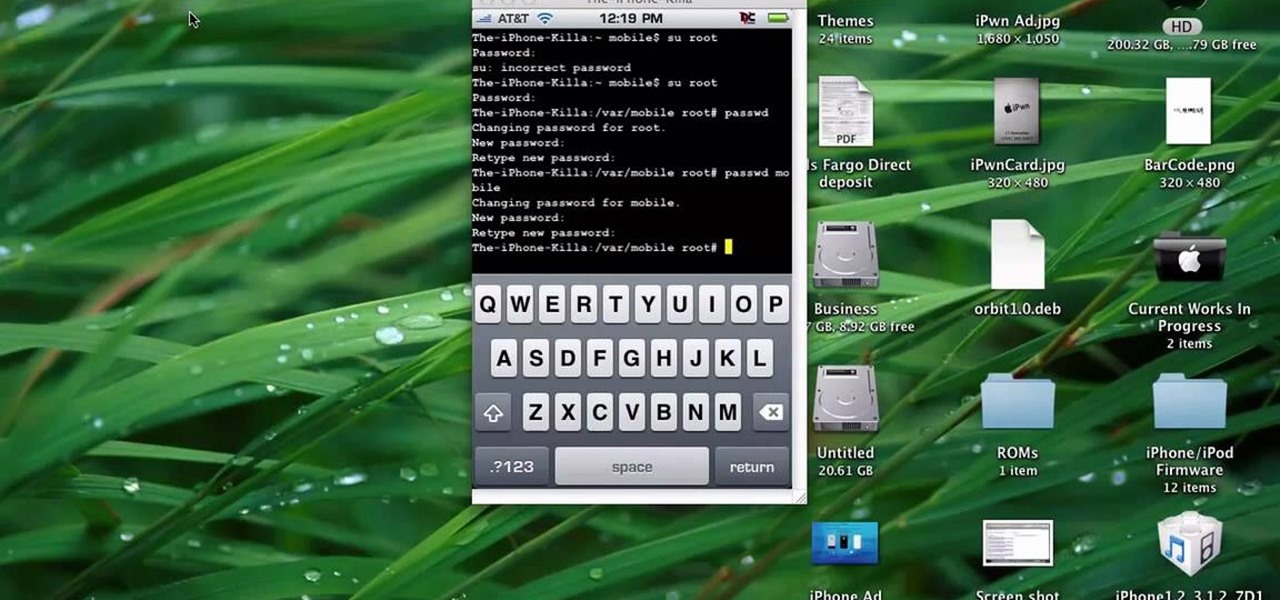
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

Notthecoolmom gives a craft lesson on how to make a diaper wreath for a baby shower. To make the wreath you will need the following materials: a package of 56 size 1 diapers (preferably with a design of some kind), a Styrofoam wreath, a spool of ribbon, and rubber bands (optional). Start by laying your diapers around the wreath to get an idea of spacing. Be careful not to make your wreath too full. You don't have to use all of the diapers it depends on the size of your wreath. To put the diap...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

Ever had a spoke break on your bike wheel? Don't throw the wheel away! Repairing a spoke only takes a few tools and some patience. You will need, at a minimum: a freewheel tool (used to remove the part of the wheel that engages the bike chain), a wrench, and a screwdriver. First, remove the tire and inner tube from the wheel. Next, remove any parts of the broken spoke that are accessible from the underside of the wheel rim. If the spoke is attached to the side of the wheel where the freewheel...

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Credit blocks appear at the bottom of nearly every mainstream movie poster (and even some indie films). This tutorial shows you how to create your own Hollywood-style credit block, from font to formatting, and shows you several different looks you can use.

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.

If your pet has recently had surgery or been ill, they may need to wear a medical collar. A medical e-collar or a cone will prevent your pet from chewing or licking an area of their body that they shouldn't be touching. In this video from Dr. Lauren, you will learn where to get an e-collar and how to secure it to their head so that they stay safe and happy.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.

Tinkernut presents the Bluetooth headset hack! This video shows one of the vulnerabilities of some bluetooth headsets. To prevent this vulnerability, it's best to invest a little more money into a more secure headset and making sure your headset is turned off when not in use. You can find all of the links and scripts used in this video, as well as find answers to questions you may have at the link below:

Uh, oh. You’re at your front door without a key. If you’ve got a credit card, see if you can get it to open the door before you use it to pay for a locksmith. Learn how to unlock a door with a credit card. The lock needs to be the right kind of lock & you need to have patience. Learn how to unlock a door with a credit card next time you are locked out!

This how-to video shows you how to open your above ground pool after it has sat there all winter. Make sure to remove water on top of the cover, any debris, and tubing securing the cover. Open your above ground pool and get it ready for summer. Check the skimmer, filter, and pump before allowing anyone in. Don't forget to install the diving board properly.

This how-to video shows you how to open your in-ground pool after it has sat there all winter. Make sure to remove water on top of the cover, any debris, and tubing securing the cover. Open your in ground pool and get it ready for summer. Check the skimmer, filter, and pump before allowing anyone in. Don't forget to install the diving board properly.

This how to video show you how to keep your shoe from sliding up and down your heel while running. This will making those longs runs less painful.

Did you know that someone could be watching what you're doing on your computer via another computer? That's right - if they are using VNC or Apple Remote Desktop software they can moniter what you're doing and even control your computer?

2 Mins To Show You How To Tie The Ultimate Secure Knot That You WONT BE ABLE TO UNDO... After Its Tied You Have To Cut It To Get It Off...

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

An invisible number controls your financial destiny. So until the revolution, you might as well learn how to raise your credit score.

Got some valuables that need to be protected in your Minecraft world? Watch this video to learn how to build a seriously secure, heavy duty, combination lock. This video will show you what materials to use to make this combination lock.

This is a great, sophisticated hairstyle you can achieve without using any heat (which can often damage your hair). It's an easy and useful secret - just braid your wet hair in the evening, secure in place and then undo it all in the morning!

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network helpful video guide.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

Board Games With Scott presents the boardgame Settlers of Catan. Scott talks about how to play the popular board game and covers some strategy for securing the win.

Learn how to tie a Tack Knot - a secure way of attaching a rope to a fixed object such that it won't come undone even if shaken and flogged. This is a fine knot for camping, climbing, sailing or Boy Scout training.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.