We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities.

Keeping your supplies of caps and ammunition high in Fallout 3 is one of the game's biggest challenges. No more! This video will teach you how to use a glitch in the game's shopkeeping interface to attain unlimited caps, ammunition, and free item repairs. You should have no trouble beating this epic game after following these instructions.

When it comes to working with people, the photographer can face quite a challenge. Everyone has a mind of their own, and with these few tips you will know how to advise your subject so they look fantastic in a picture. Join Erin Manning, professional photographer, as she shows us 5 handy tips for working with people.

If you're not an everyday woodworker, then building a deck may be a challenge for you. But it's not as hard as it might seem. If you follow all of the required steps for deck building, you'll have one of the best ones on the block, and be pretty darn proud of it, too!

This video tutorial from Live Monarch shows you how to fix a live butterfly's broken wing. You can help restore flight to a butterfly in need -- you can be a hero and make a real difference.

How do you know if he's The One? Many women find themselves asking this once they've been in a long-term relationship and are considering important future steps like getting married and having kids.

Socks may be one of the lamest gifts you could get someone, especially a child… or a boyfriend or girlfriend. But there is one exception… homemade knitted socks. Make these super simple, handcrafted socks for everyone in your family.

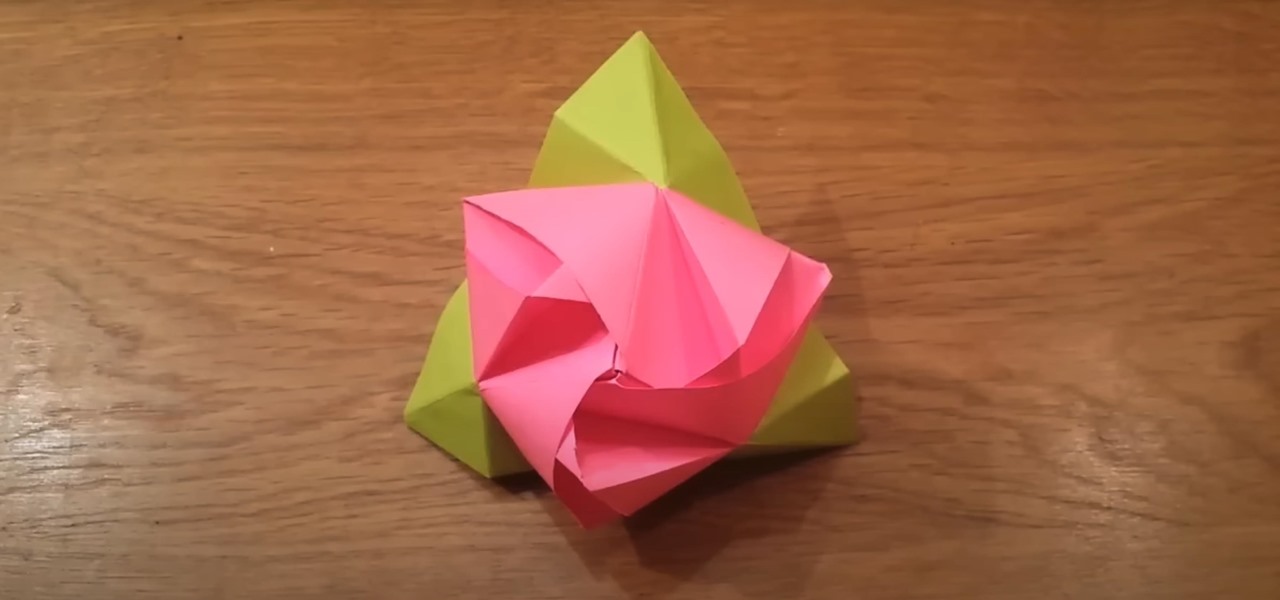
Origami, by its nature, injects a bit of magic into its incredibly tangled, convoluted folds and motifs that turn a flat sheet of paper into a living, breathing creature/work of art.

After you start drawing people, you will undoubtedly want to dress them. Drawing clothing is all about knowing how clothes fall, fold and wrinkle. Check out this tutorial, and you will be drawing realistic folks in no time.

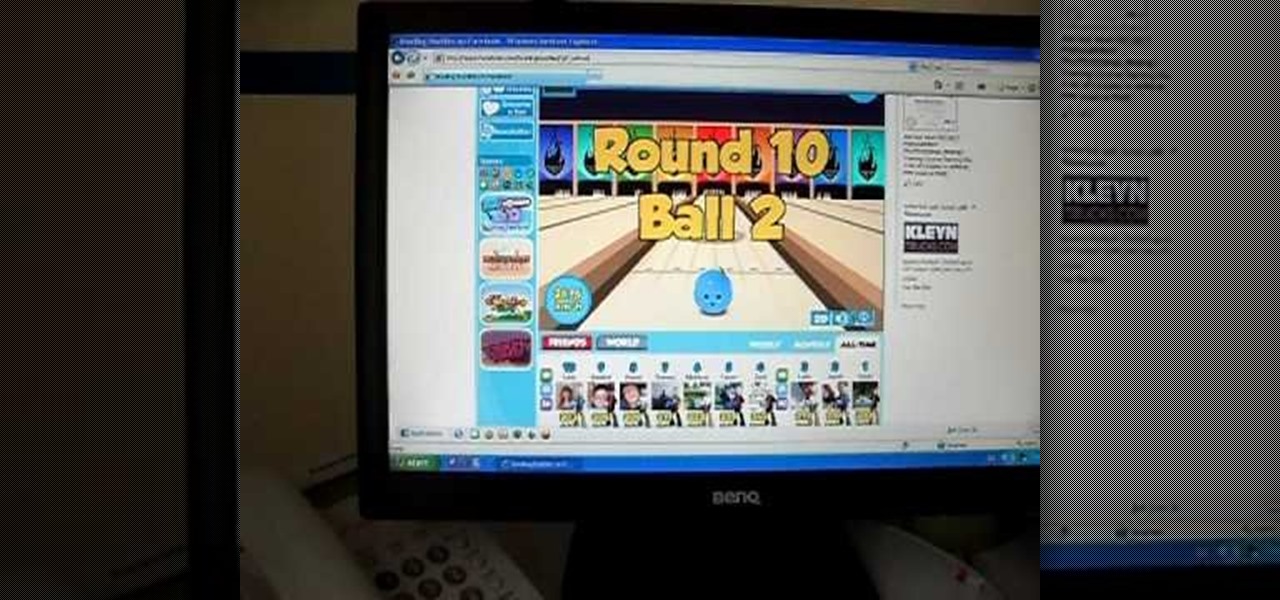
Kick butt in Bowling Buddies by bowling all strikes. How? It's easier than you think to get a few turkeys or baggers… and no Cheat Engine required.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to talk about group competition games. These make the party worth while. For example; if you have let's say about 14 party guest, you can divide them up into groups of 2, put 7 in one group and 7 in the other and have a different activity for each group competition. Let me show you an example. I purchased this bag of straws, M...

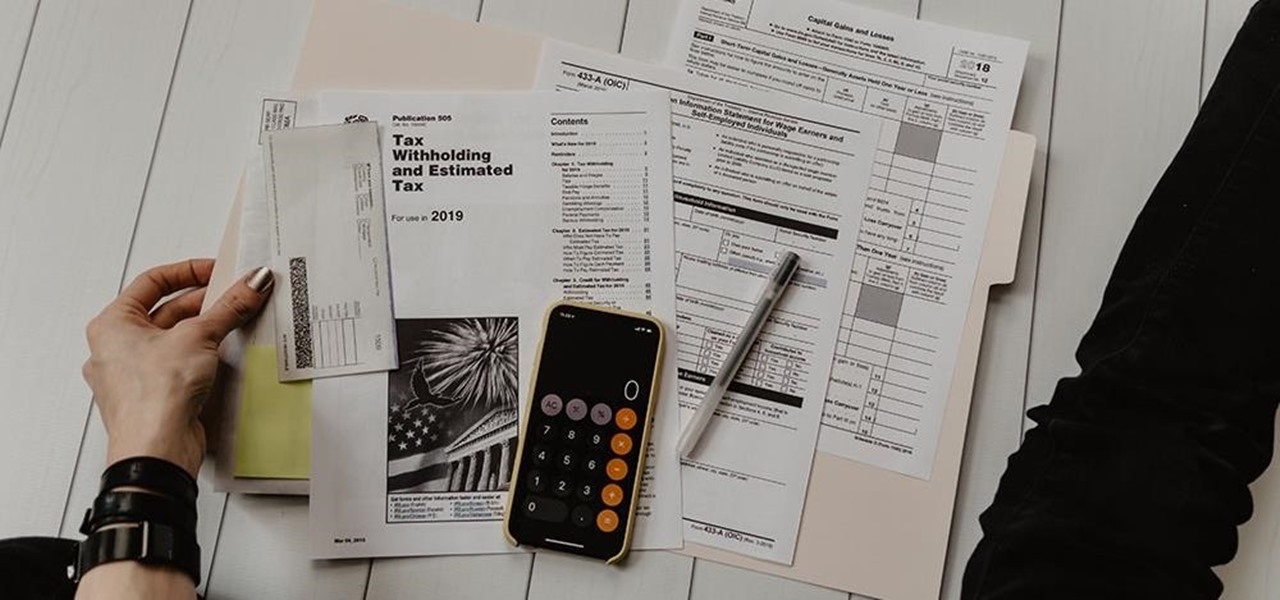
Keeping the books in order is one of the great challenges every business owner faces. Having a great product or service is one thing, but managing the minutia of invoicing can trip up a lot of small- and medium-sized businesses.

The COVID-19 pandemic has hit everyone hard. With over 36 million American workers filing unemployment claims, finances are at the front of everyone's mind. Understanding your accounts has never been as important.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

Producing professional video can be expensive and time-consuming. Green screens are cumbersome and require a lot of space, whereas dialing in the perfect lighting comes with its own challenges. For people working on a budget and space constraints, achieving the ideal background can be a nightmare.

The rumors have been circulating for months, but now there's a source attached to the notion that Magic Leap is looking to sell itself off after a rough couple of years following the launch of its Magic Leap 1 augmented reality device.

The world of CES, the annual technology conference in Las Vegas, usually brings a few surprises, but few expected Samsung to fire off its first real augmented reality salvo at the event.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

Your goal in Mario Kart Tour is to beat your rivals and come in first place, but that's never easy when you're also trying to avoid banana peels, red shells, flying bombs, and other items. One item you may be familiar with is Blooper, a squid-like creature found in most water levels. It squirts ink all across your screen, making it more challenging to navigate your driver on the track.

With the defending champion Golden State Warriors and Drake's favorite team, the Toronto Raptors, set to face off in the NBA Finals starting Thursday, Snapchat has gifted hoops fans with a pair of augmented reality experiences.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

Now even muggles can see how they'd look chasing the Golden Snitch on a Nimbus 2000. That's because Snapchat is gifting Harry Potter fans with a 3D Bitmoji Lens that adorns their digital doppelgängers in the robes of the houses of Hogwarts.

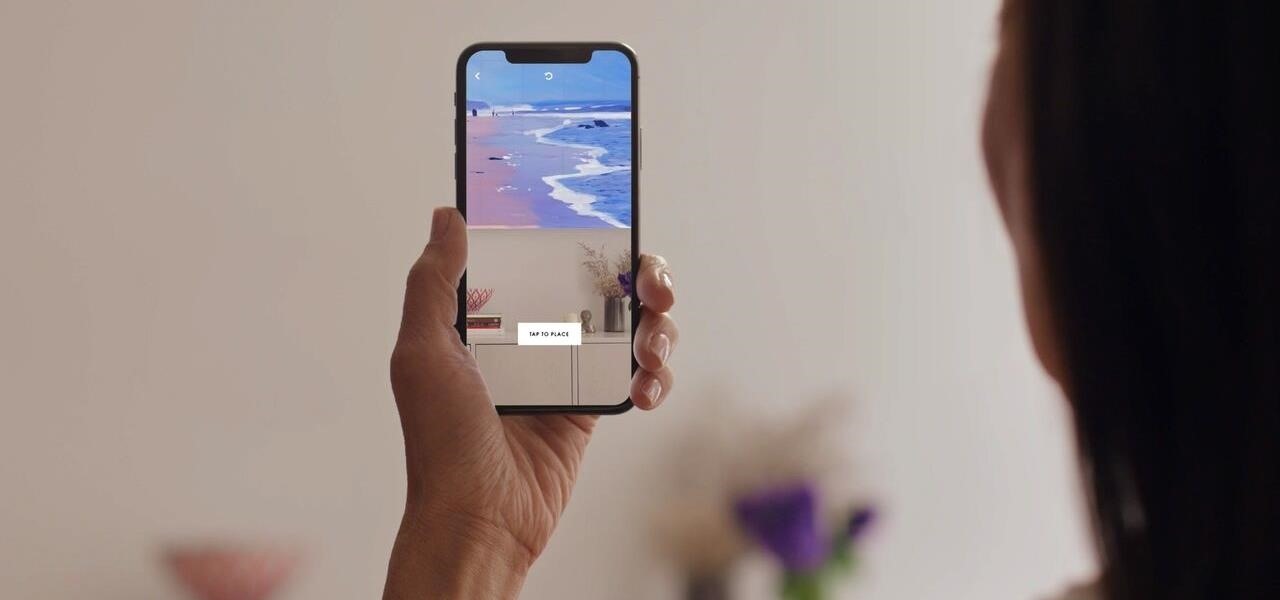
The old school staple of many US homes with children, the remote control race track, has been given new life in augmented reality thanks to the Room Racer app for iPhones and iPads.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

As if its users weren't already having enough fun with dancing hot dogs and face effects, Snapchat is upping the ante with a new kind of shared augmented reality content.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Less than a week after ARKit 1.5 became available to the public through the iOS 11.3 update, the App Store has its first app with AR features (Artsy) to leverage Apple's AR toolkit update.

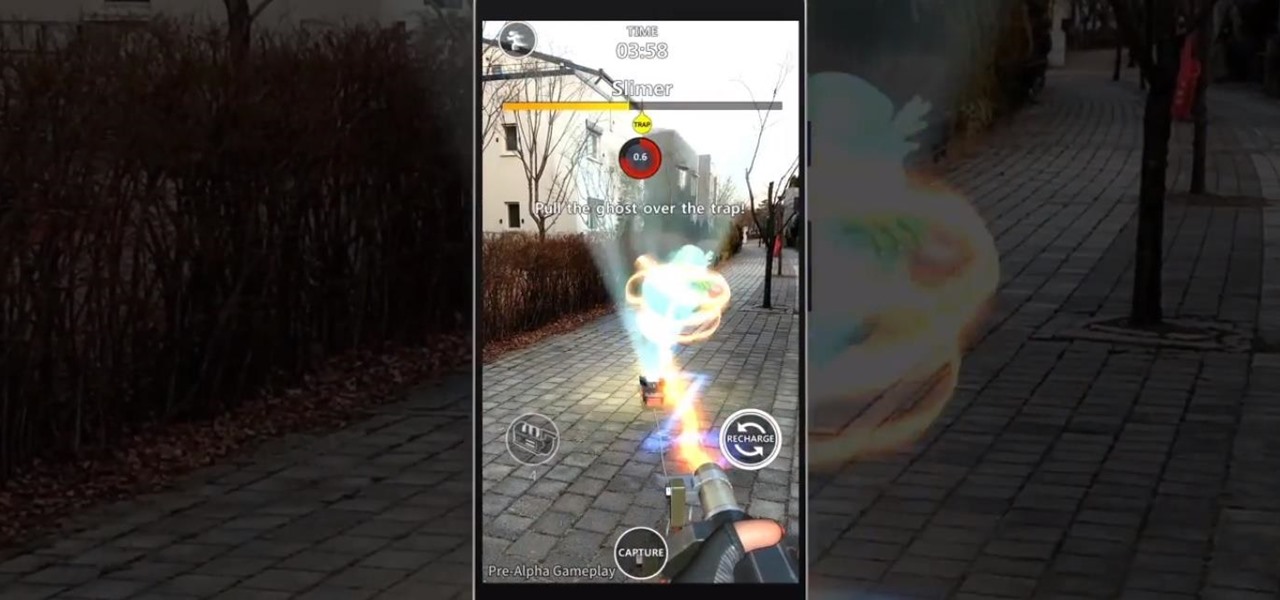
Sony's Ghost Corps, the caretaker of the Ghostbusters franchise, just released some pre-alpha gameplay footage from the upcoming Ghostbusters World location-based AR game to whet the appetites of would-be hunters of the paranormal.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

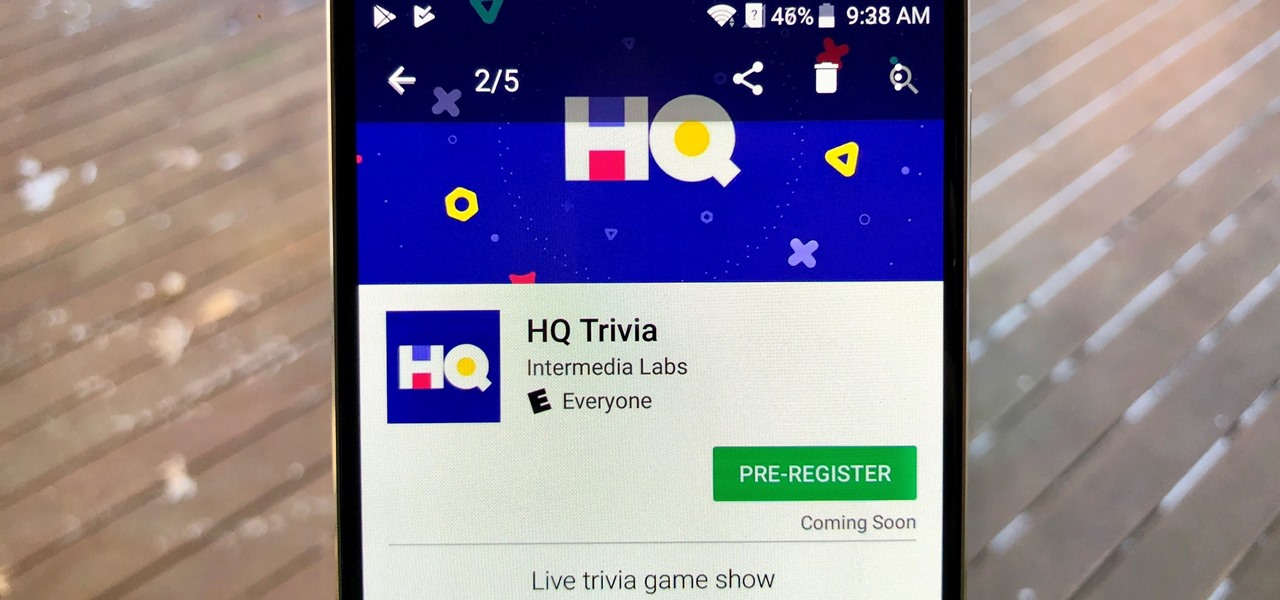
Attention Android users — the famously iPhone-only HQ Trivia is here! If you've been waiting for the worldwide sensation to come to your smartphone, now's your chance to dive into the excitement.