Streaming apps like Netflix, Hulu and Amazon Instant Video have been available on game consoles for a while, but if you're in a country where they're blocked, it can be hard to find a way around. There are apps and extensions like Hola Unblocker and Media Hint and that to bypass location restrictions on your computer, but what about your Xbox?

There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

Bowling is such a fun group activity and is perfect for birthdays and other types of gatherings. However, if you are not a pro bowler the scoring system can be pretty confusing. This tutorial will walk you through the steps of keeping score so you will know a strike from a spare and everything in between.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Check out this three-part series on how to play Super Smash Bros. Melee (advanced). This is not a beginning tutorial for all you newbie gamers, it's more detailed and advanced for pros, or semi-pros.

When caring for your pet, finding and treating their insect bites which may cause allergic reaction in your pets. Bites from wasps, spider, bees, and other insects may cause an intense allergic effect. First, check if your pet is still breathing and check if there is a stinger still is in their body and scrape it out using a credit card. Using a medication that contains only chlorpheniramine if your pet is conscious, breathing, and not vomiting. Using this method, you will be able to ensure t...

The Shim Sham or the Shim Sham Shammy is a line dance with many different variations in choreography. This version may be different from the one you may have already learned. This version is credited to Leonard Reed and Willy Bryant of the Apollo Theater. Learn how to do the Shim Sham dance steps with this video tutorial. Though this video was shot with music in the background from another room, the tunes normally accompanying this dance include Chick Webb or Benny Goodman's version of "Stomp...

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Disney's animated film Toy Story 3 beat all expectations at the box office, and is now the highest-grossing movie of 2010 in North America and second worldwide. Can Disney Interactive Studio's Toy Story 3: The Video Game match the success? Who knows, but no matter how successful it is, it's still a fun game full of animated delight, and this Mahalo video walkthrough series will show you the entire gameplay for the game on the Xbox 360.

The new Medal of Honor video game is out for the PlayStation 3, Xbox 360 and Windows, and if you happen to have yourself the Xbox 360 version, check out this extensive video walkthrough series. It takes you through the entire gameplay for Medal of Honor— all 10 missions. Make your way through modern-day Afghanistan and eliminate all of the Taliban forces.

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

Have you been yearning to join a crime syndicate? Wishing you could you mob-like skills to proper use? Want to bust heads with a thick accent? Well, you don't need to live in a crime-filled city to become a gangster in the mafia, because Mafia II lets you do it right from home, from your Xbox 360.

Grab your PSP and get ready to ROCK Metal Gear Solid: Peace Walker! This video walkthrough guide will take you through every mission, from the main ones to the secondary ones. Follow along and learn the tips and tricks to the gameplay so you can beat the game yourself! Peace Walker is the fifth installment in the Metal Gear series.

The herd of augmented reality cloud startups that emerged in 2018 have been hunted to near extinction, with Google-backed Ubiquity6 the latest to move from an independent entity to a wholly-owned asset.

The Apple rumor mill never stops churning and when it comes to augmented reality smartglasses, the chatter has been particularly hot in recent months.

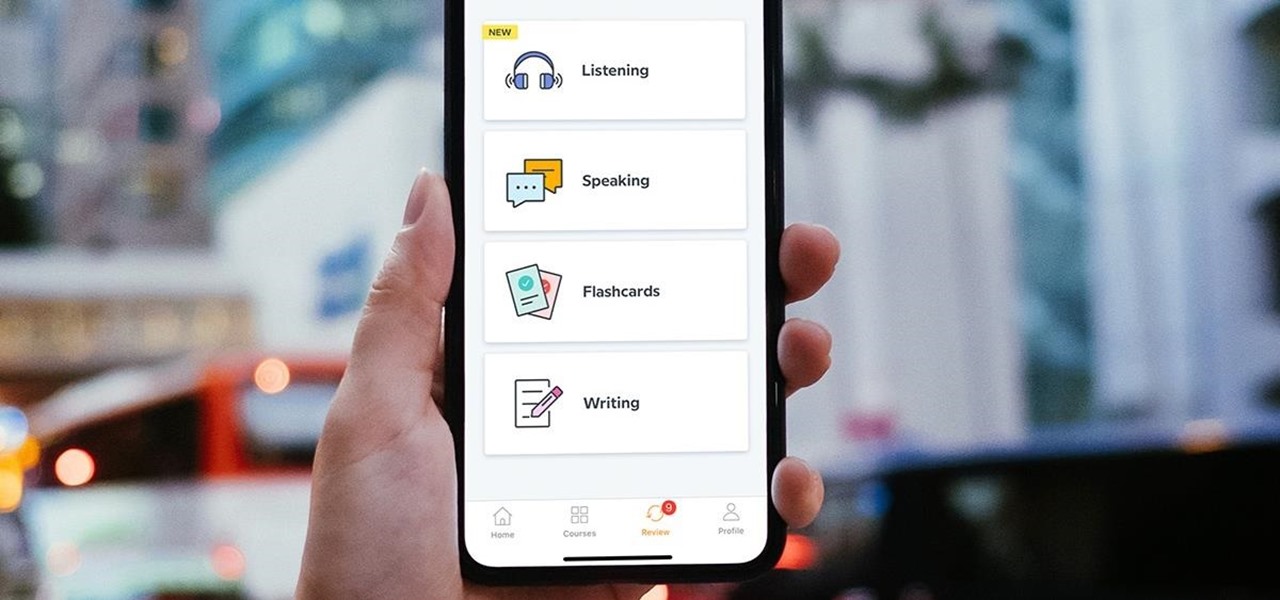
Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

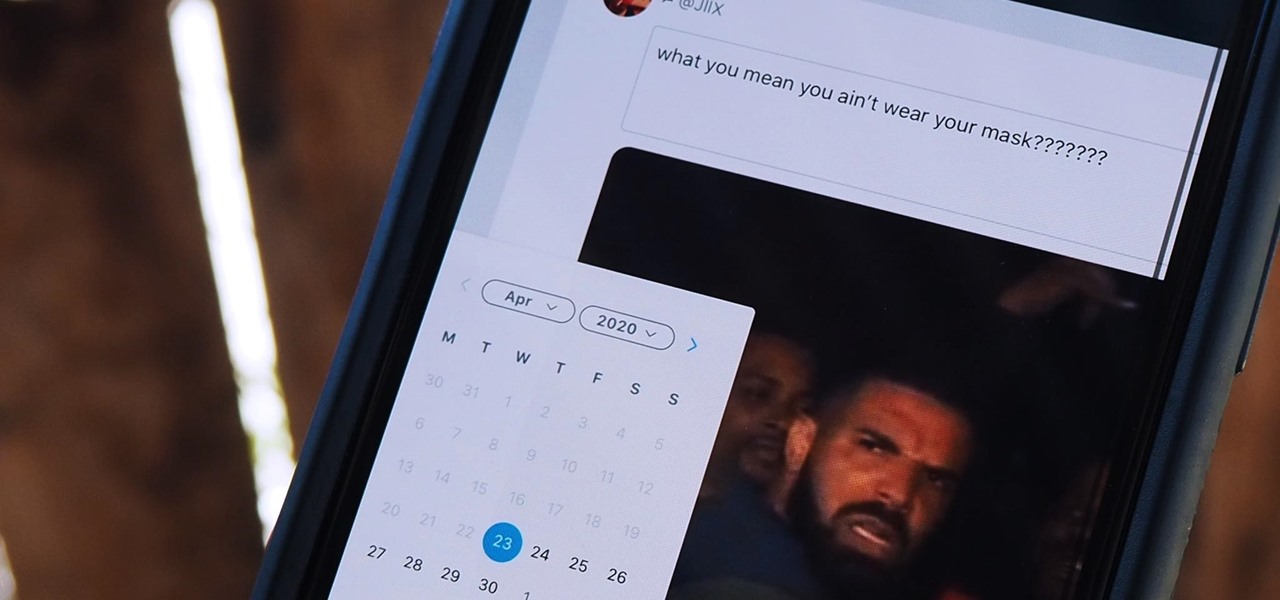
Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

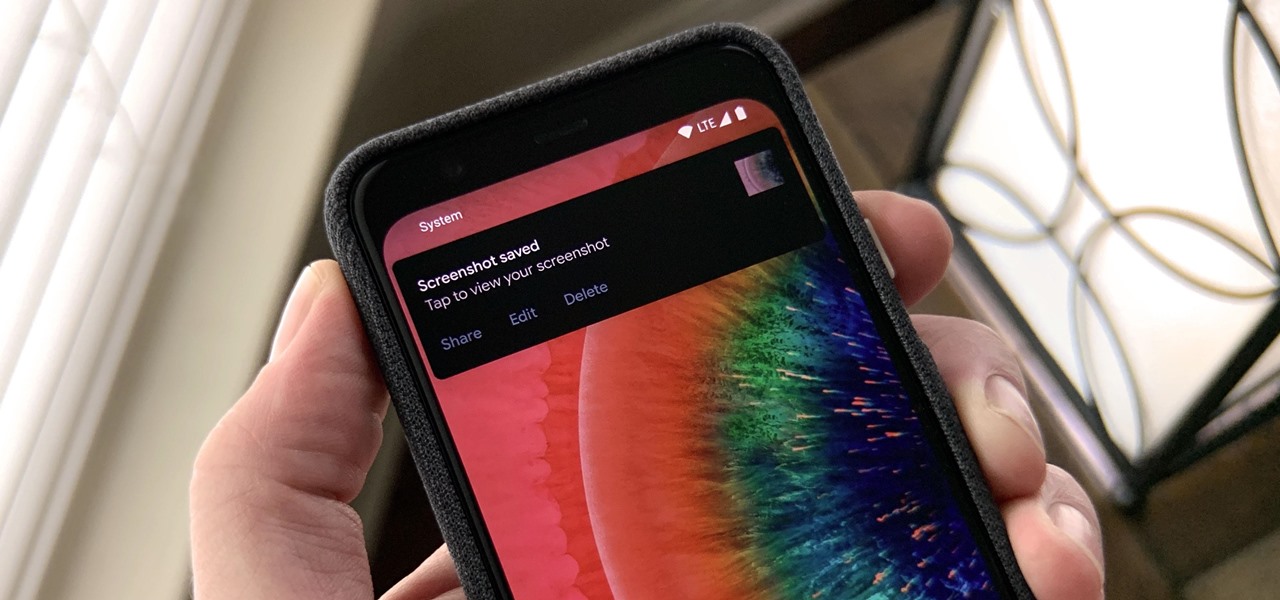
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

I go back and forth between two home screen apps: Nova Launcher and Action Launcher. While I prefer the aesthetics of Nova, I like Action's Quickpage feature since it puts some of my favorite apps just a swipe away. But now, I've found a way to replicate this feature on Nova (or any other launcher), and it works even better.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.