Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.
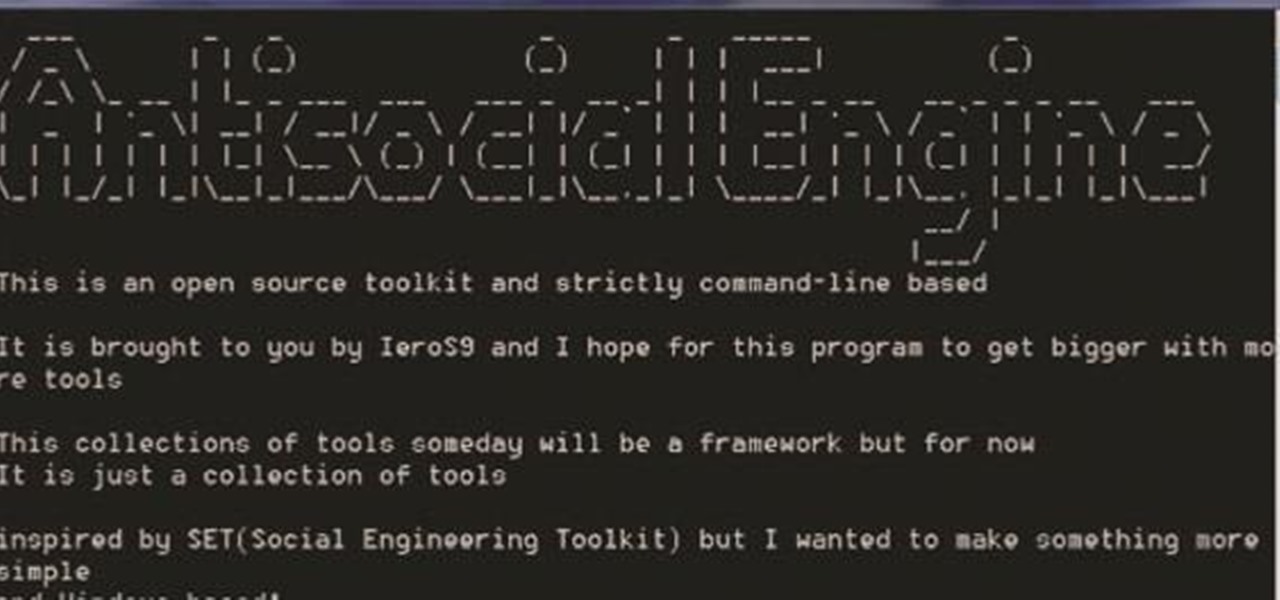
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

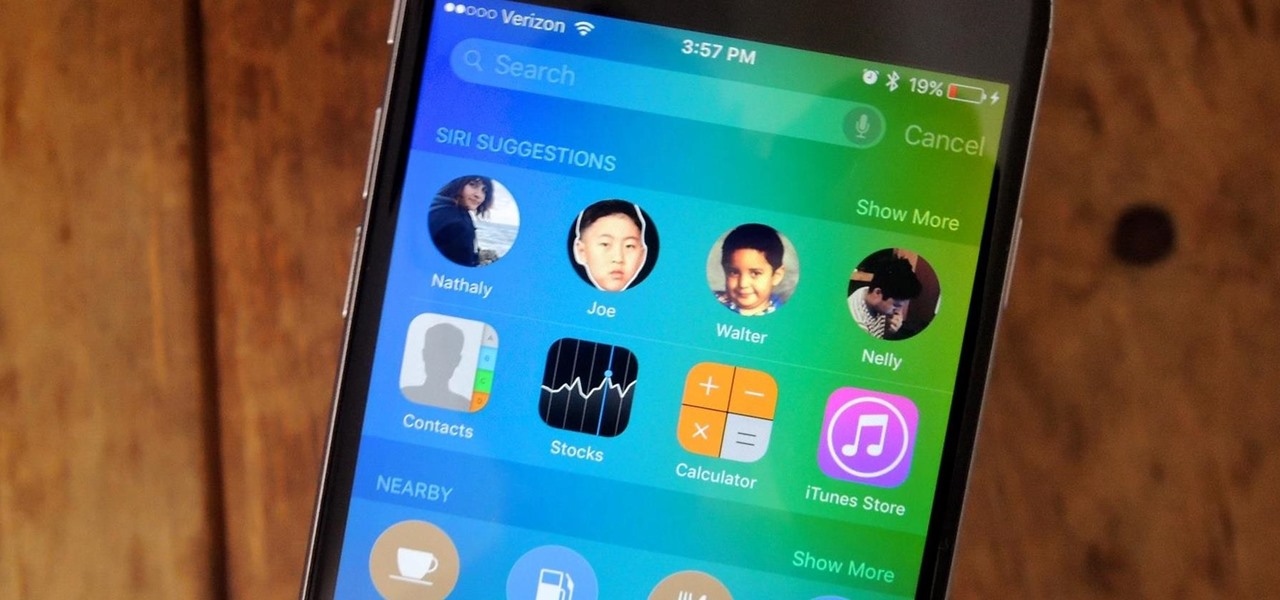
Apple certainly took a page from Google Now with its new "Proactive" search page in iOS 9. Located to the left of the home screen, the page provides quick access to contacts you've recently corresponded with, suggested applications, nearby places, and news articles based off of your Safari activity.

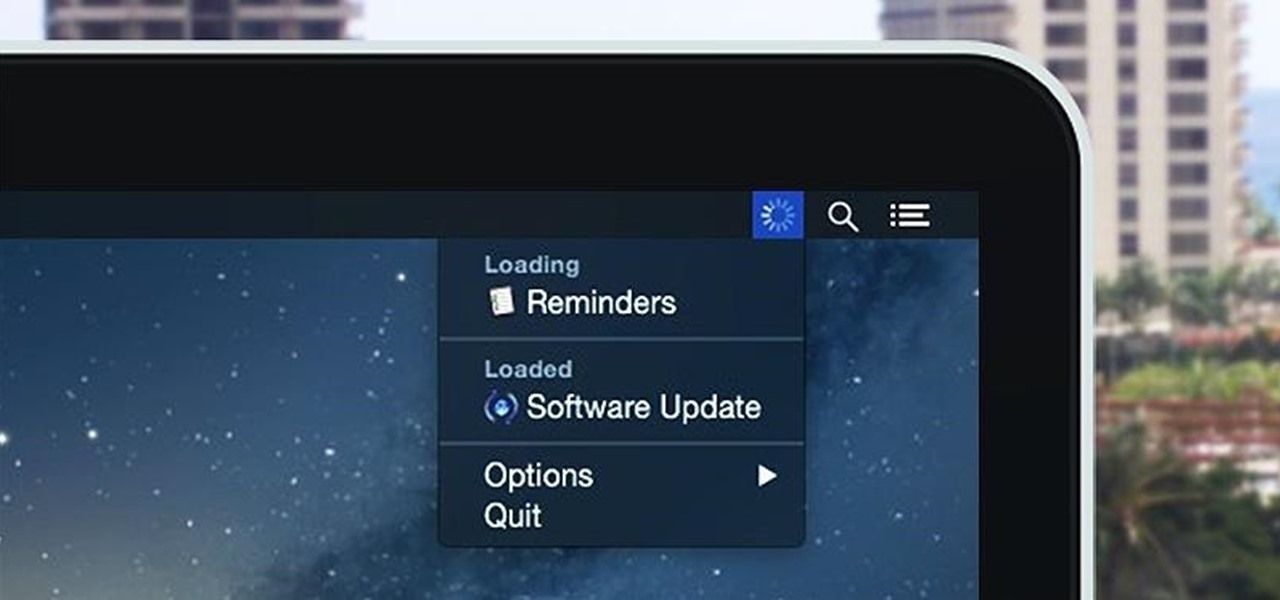
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

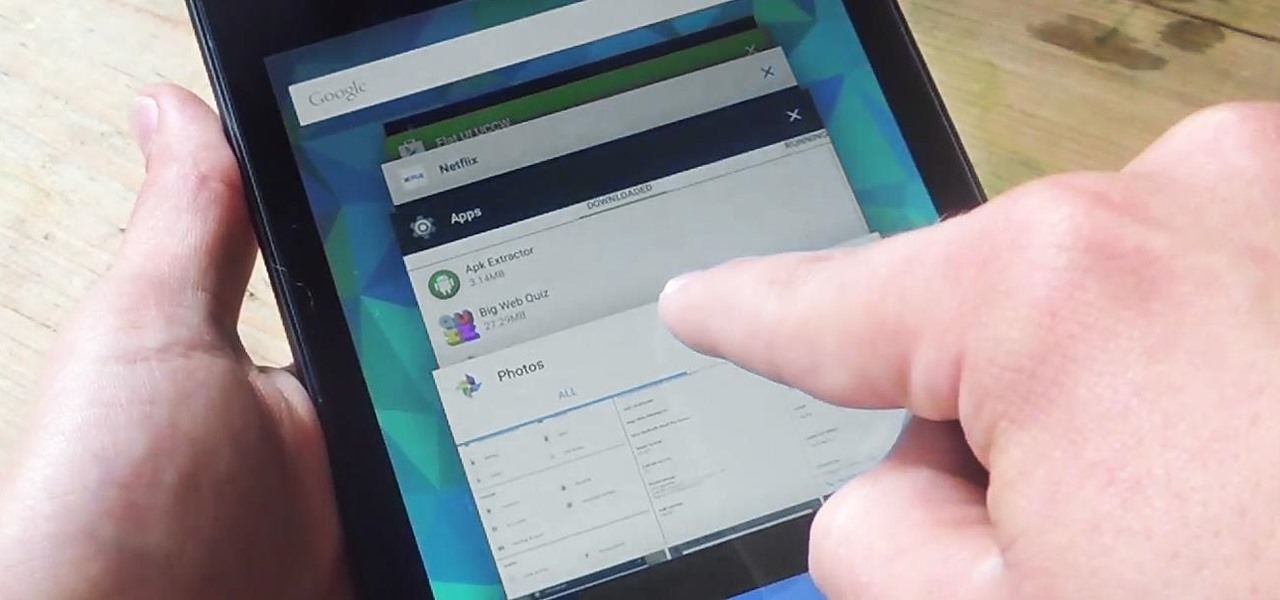
On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data.

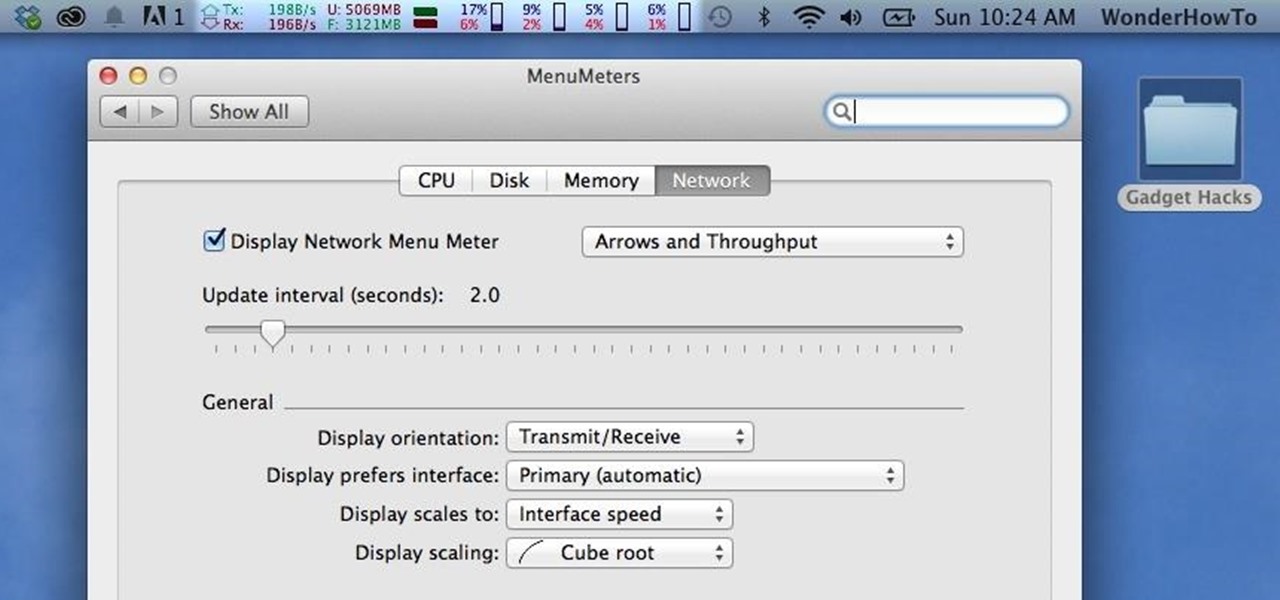
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

Thanks to Apple's new extensibility features in iOS 8, developers are now able to create extensions for their apps that let you perform actions in notifications, widgets, and in stock Apple apps without having to open up the specific app itself.

As soon as you plug a set of headphones into a Samsung Galaxy series device, a bar pops up in the notification tray that lets you select from a list of "recommended apps" for earphones. It's a convenient little feature that shows the apps you're most likely to use based on previous activity.

Well folks, the dream is coming to life. While we still may be a ways away from mind control, the team over at Thalmic Labs has created the Myo, and with it, the power of the Force comes to motion control, so long as you use it wisely.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

If I could think of one thing the world was missing, it would surely be more tablets. While people struggle between shelling out 200 to 500 dollars for a new iPad, Nexus 7, Kindle Fire, Microsoft Surface, or one of the hundred other tablets on the market, the folks over at DreamWorks have decided to make their own, aptly named the Dreamtab. The Dreamtab will have an 8-inch screen and favor applications with the use of a stylus, for coloring and the like. Total cost is rumored to be under 300 ...

Cavandoli Macrame (also called Tapestry Knotting) is an intricate form of knotting used to create geometric patterns. The Cavandoli style is done mainly in a single knot, the double half-hitch knot. Reverse half hitches are sometimes used to maintain balance when working left and right halves of a balanced piece.
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

I'm all about safety in my life. I even put on safety goggles when someone opens a bottle of champagne—high life problems. But when it comes to driving, you have to be double safe, because the other drivers on the road may not have your safety in mind.

Since the emergence of GoPro, the company's cameras have been been on a steady incline for the past several years. Adventure enthusiasts had difficulty recording their extreme activities without a huge price tag before the GoPro came along in 2002.

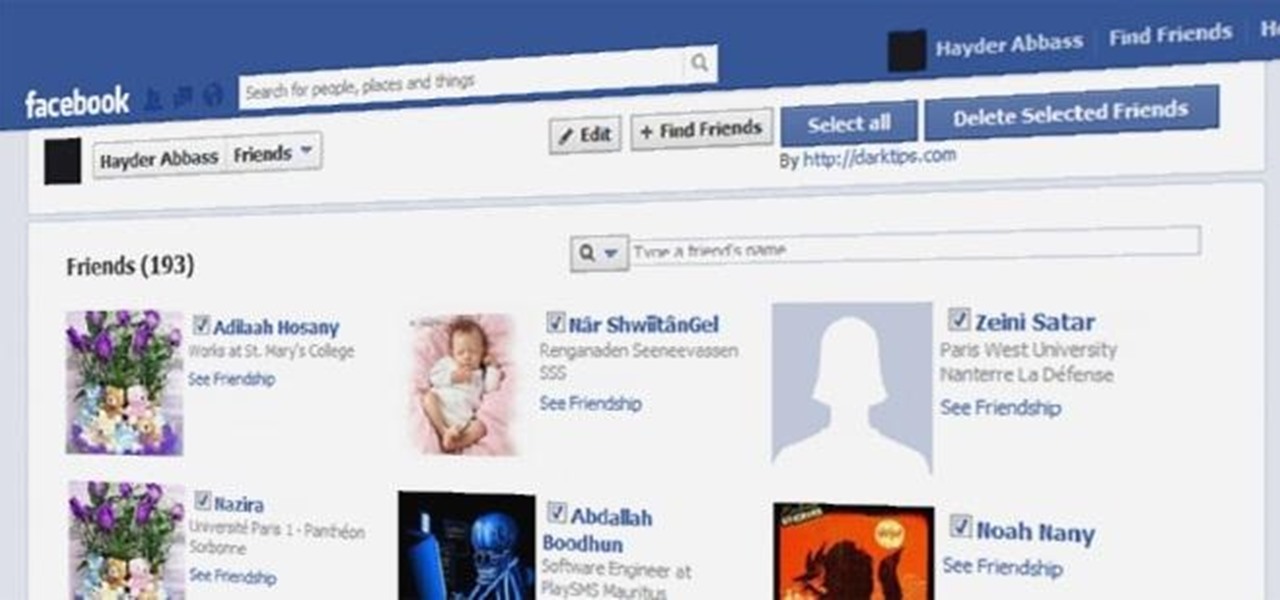
Facebook makes it extremely easy to keep in touch with family and friends, while maintaining those relationships with little to no face-to-face contact. It's the perfect tool for recluses.

Google has just launched a new revolutionary augmented reality game for Android called Ingress. Their new mobile game centers around the fight for control of the minds of everyone here on Earth. It's a freaking worldwide fight—from your smartphone! While augmented reality in is nothing new in the smartphone gaming world, it has never seen the likes of this. With an almost Halo-like storytelling, Ingress seeks to bring out gamers all across the globe to perform physical activities by transform...

Whether you've got an itch for a mini-flamethrower, a shower of burning sparks, or a exploding ball of flames, these little fireworks-producing lighters may be the answer to your pyrotechnic cravings!

Assuming that you are living north of the equator, ‘tis the summer season for brewing your own sun tea. Unlike the conventional method of dunking tea bags in boiling hot water for several minutes, sun tea is brewed over the course of several hours through the natural heat of direct sunlight.
1 Identify the child's talents, and discuss the opportunities he has to use them in productive ways. If you notice that the child you're mentoring is excellent with counting money, talk about how the child should consider a career in banking or running a business one day.

It's nice to have the family together for Thanksgiving dinner, but having so many people together can make it tricky to figure out what you can do after dinner. Here are a few good ideas you can use for family friendly activities.

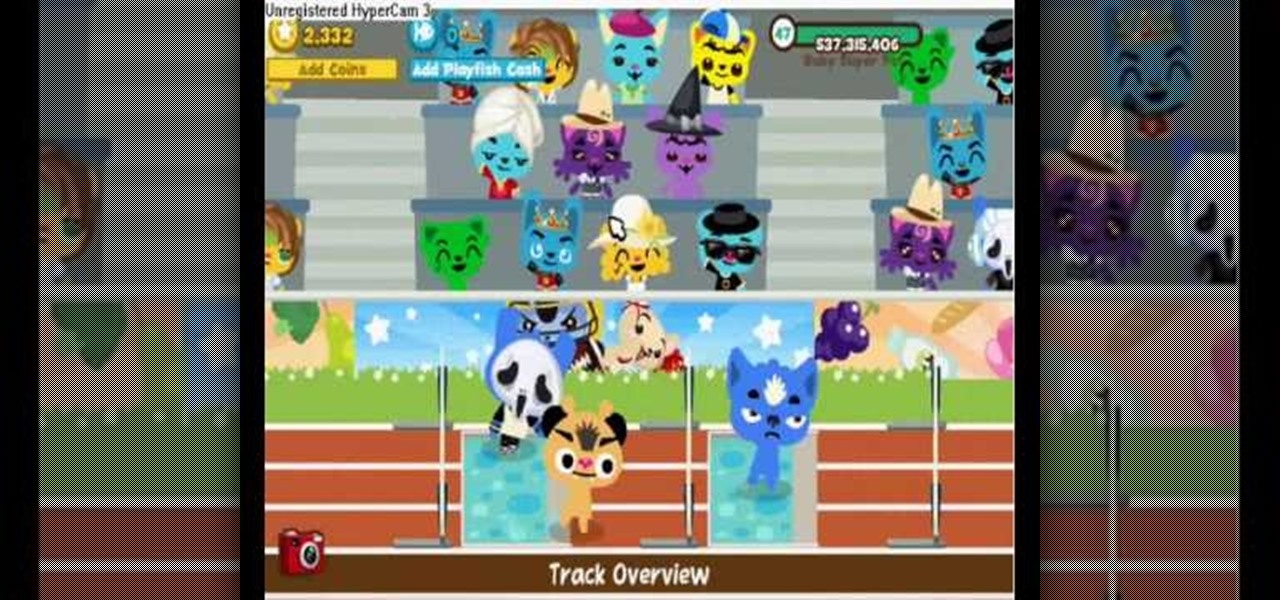
Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.

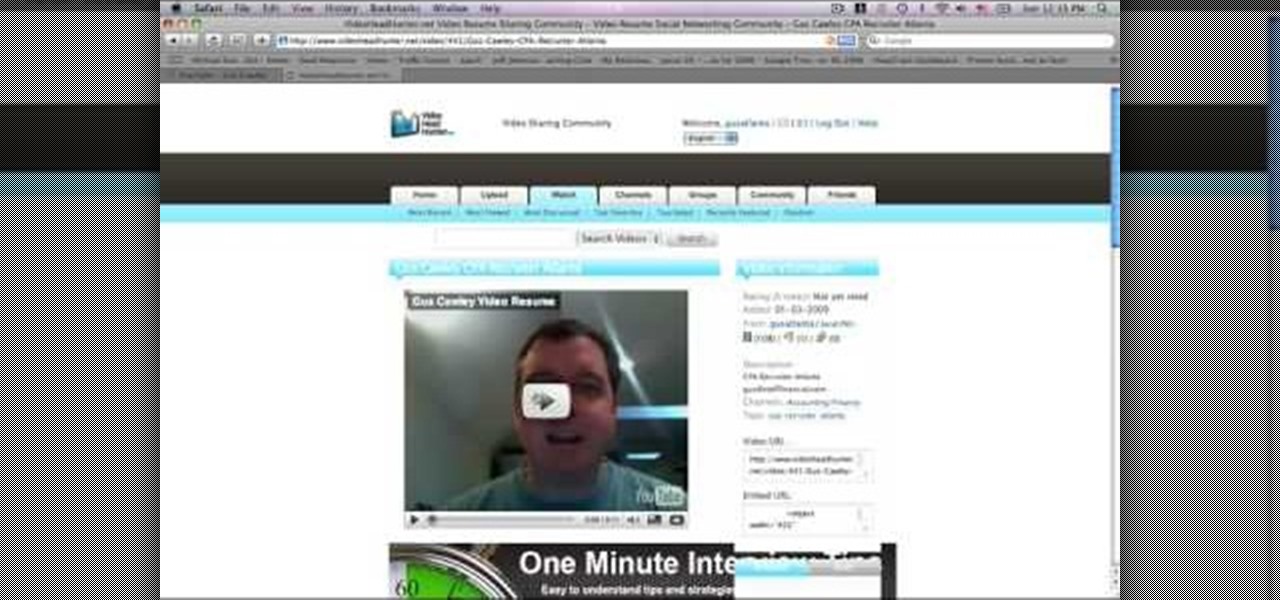
Gus Cawley shares the ways to make a video resume with the help of free online tools. 1. Log in to YouTube. 2. Click upload and select quick capture. 3. Click the record button (be sure to have good lighting, good background and a high quality microphone for a more effective recording) 4. State the information of your resume. 5. Click the red square button to stop the recording then choose publish. 6. Edit the information of the video. In the description, put your contact details and informat...

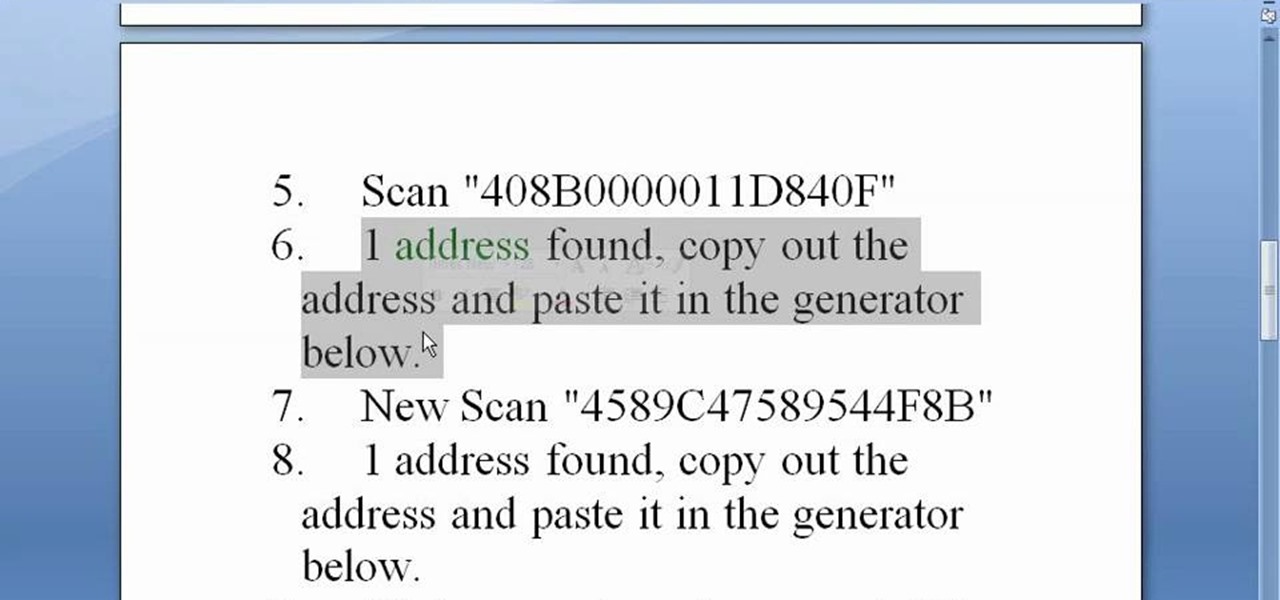
This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

This short video teaches you how to make real ice cream with your preschooler with just some plastic bags. This is a wonderful activity for using measuring skills, scooping and pouring skills, and experiencing a science reaction. The best part is the great tasting ice you can make in about 5 minutes!

For preschoolers an activity good for counting and recognizing numbers. You can easily make and play this game at home.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

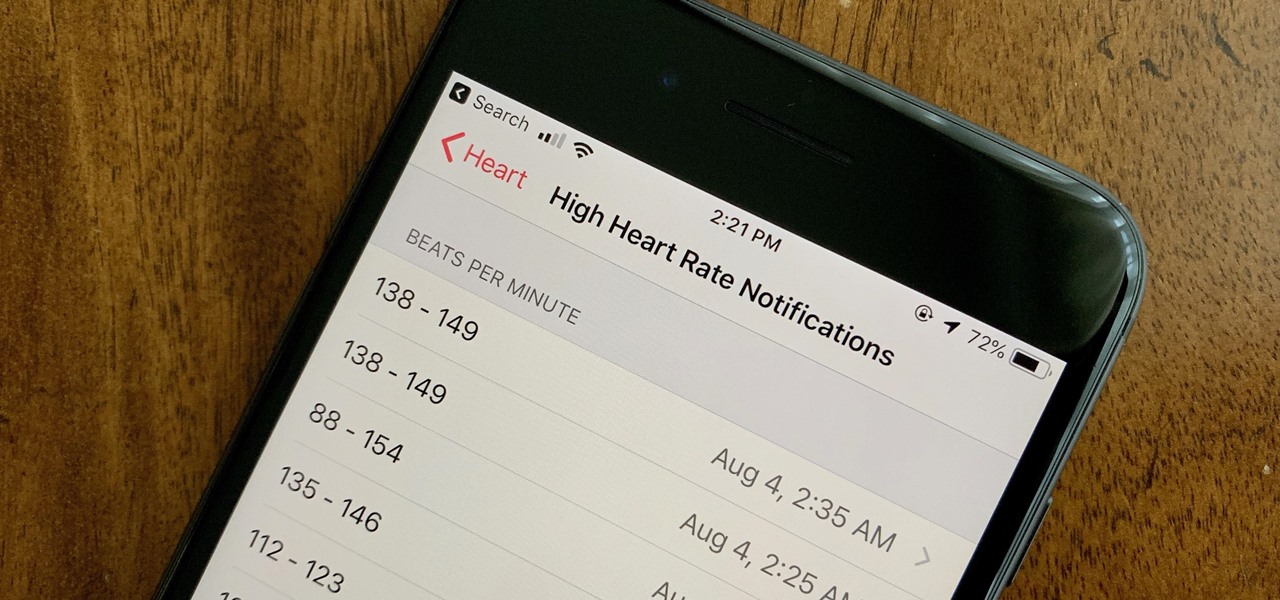
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.