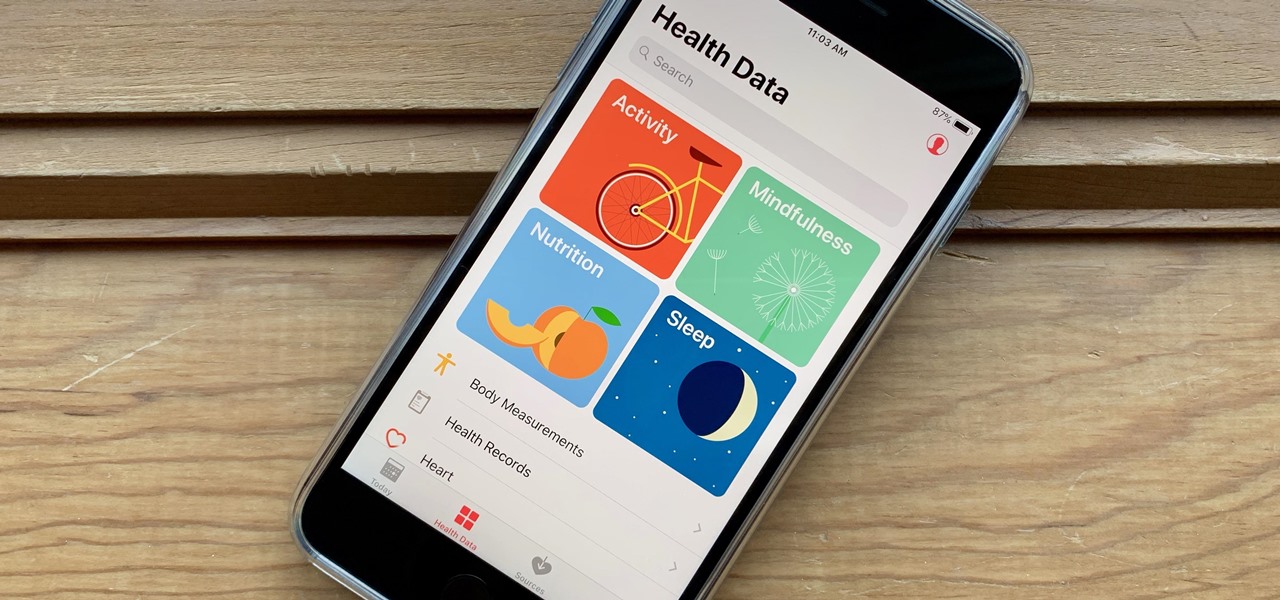
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

So, you accidentally sent a voice message to someone in an Instagram DM. Maybe it contains an unflattering conversation about the recipient. Maybe it's a record of something embarrassing you said. Whatever your message contains, it's out there, on someone else's smartphone. You might think you're out of luck, and that your life is over. If you act quick, however, it won't be.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.
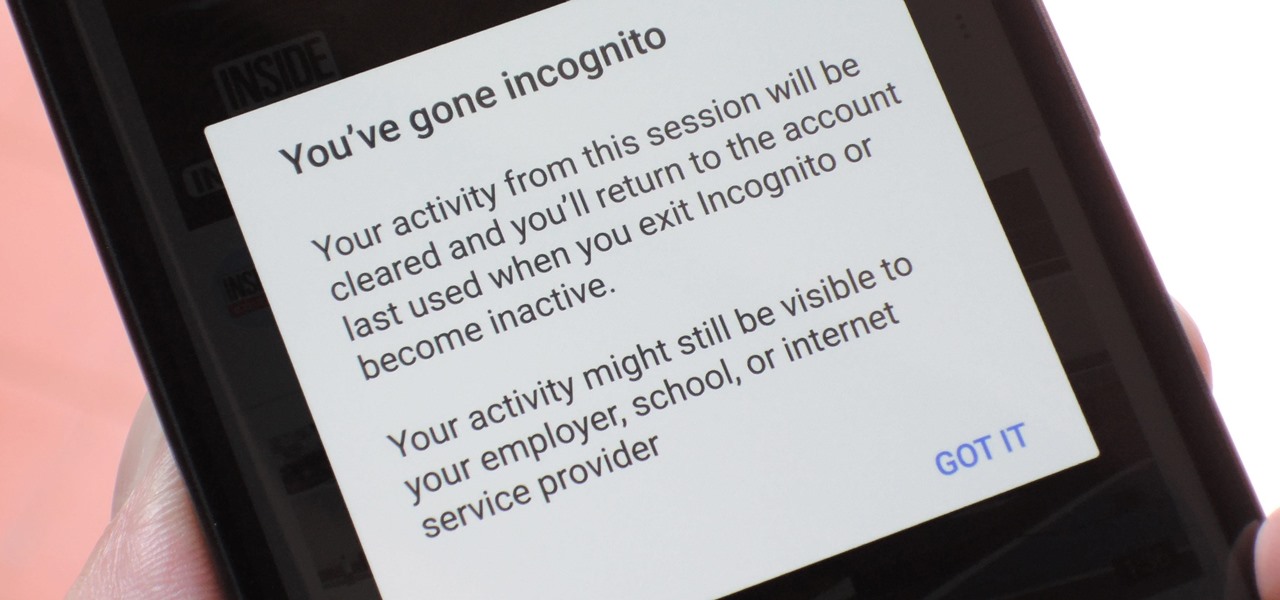
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

If you are an active player of Pokémon GO, you may soon be capturing more than just virtual pocket monsters.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

It's always a pleasure when your activity syncs across all of your devices. Herein lies another reason to use Samsung Internet — the app natively syncs with your open tabs on desktop Firefox. Anything you do on your computer can be easily accessible from your smartphone.

It's been a long time coming, but Tamagotchi has finally ditched its iconic toy egg and arrived as a mobile game. The new iteration is called My Tamagotchi Forever, and though it's currently only available in Canada, you can actually download the game anywhere and care for your very own virtual pet right now.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

Newly appointed Ford Motor CEO Jim Hackett admitted yesterday that demand for driverless transportation could take many different forms and that Ford was rethinking how it would tailor its cars and mobility services for self-drive modes of transportation in the future.

Heathrow Airport's most recent arrival isn't a flight, but rather an interactive children's game featuring augmented reality technology.

These past few days have brought more bad news for our national parks. Interior Secretary Ryan Zinke confirmed that there will definitely be big cuts to national park budgets. This comes after Donald Trump's budget request revealed a call for $300 million cuts to national parks.

There's a general belief that augmented and mixed reality is going tied to enterprise solutions for the foreseeable future, and most developers in the field are focused on business use-cases. Without a dramatic breakthrough in the next couple of years that will likely be the case, making that decision the sensible one.

The number of Legionnaires' cases in New York over the last couple weeks has led to concern and recommendations of caution for those at risk.

Niantic announced today that all gyms in Pokémon GO will be closed while the company prepares to celebrate two major anniversaries for the game. There will be updates, in-game celebration, and the first ever real-world Pokémon Go event.

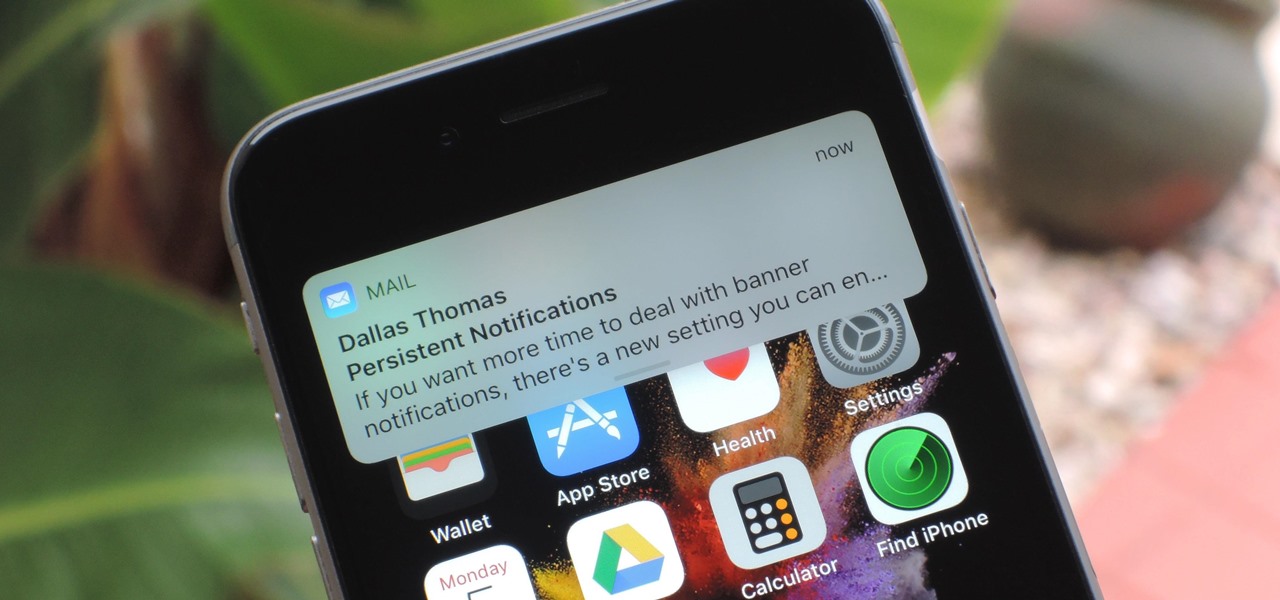
You're working on your iPhone or playing an awesome game when you receive a notification. You take too long to look up from your activity, so before you get a chance to see what's up, the notification is gone. Persistent notifications won't disappear on you like the default disappearing ones in iOS 11 and iOS 12, giving you as long as you need to check them. Here's how to set them up.

Tuesday gave us what I am dubbing a "patent dump." Can you blame me? The U.S. Patent Office released 56 patents from Apple. 56! Among them, there are patents confirming Apple is working on embedded Touch ID, edge-to-edge displays, and a 3D camera system (surprise, surprise). Some of those things we've heard rumors on for some time, but what is new is one of the patents hidden amongst the bunch, describing an Apple-made avatar system. One whose end-goal is to reflect your current emotional sta...

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

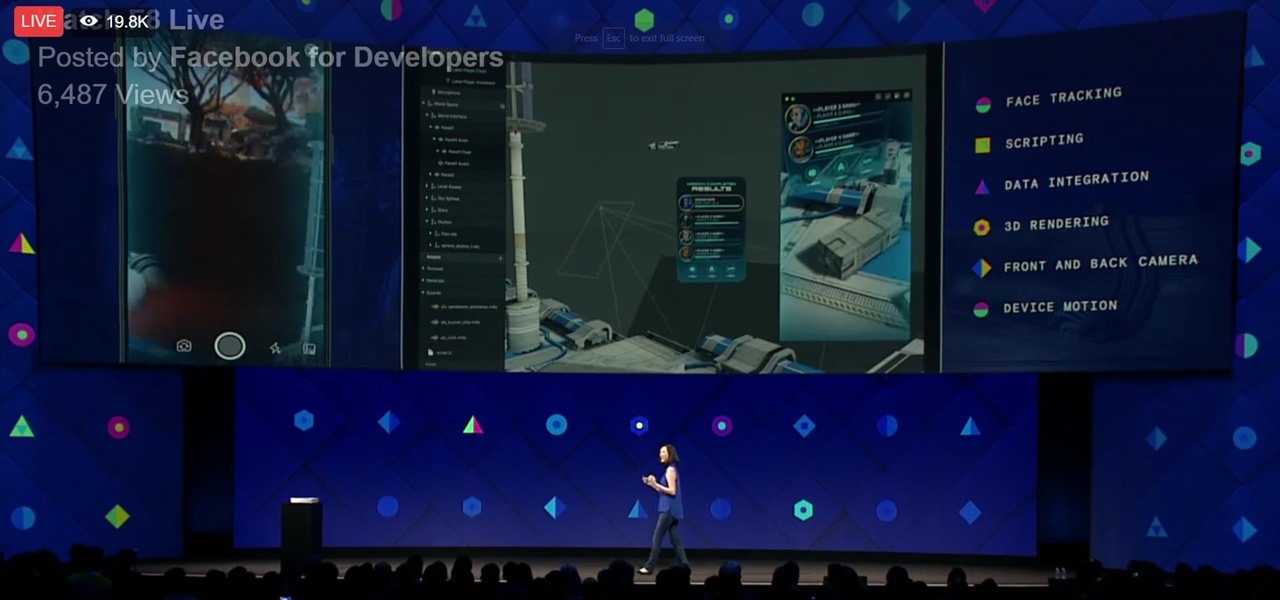
During his opening address on April 18 at F8, Facebook's developer conference, CEO Mark Zuckerberg launched the company's augmented reality platform centered on artificial intelligence-powered cameras.

Apple's music streaming service just got a major update on Android devices. The Spotify competitor has implemented some changes for users on non-Apple phones that have been available to iOS devices for some time now. Nevertheless, Apple Music users on Android should welcome these updates.

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

Pennies may only be worth $0.01, but if you want a coin with everyone's favorite donut-eating dad on it, you're going to need to shell out a little bit more.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

Android Nougat is a godsend for tablet users, as it's packing some serious multitasking improvements. It goes well beyond the new split-screen mode, too, because as it turns out, there's a hidden setting that turns your apps into completely resizable windows within a desktop-like interface.

Rooted users have been able to remap their hardware buttons since the earliest days of Android, allowing them to change the functionality behind one of the most centralized methods of interacting with a phone or tablet. Up until now, however, non-rooted users have been left out in the cold, meaning these buttons could only perform the functions assigned to them by the device manufacturer.

Summertime means lots of parties, picnics, and barbecues—and wherever a group of fun-loving adults can be found basking in the sun's rays, delicious cocktails are sure to flow freely.

If you're sick of playing chess in Facebook Messenger, there's another little-known game you can play with your friends directly in the app—basketball. This hidden game was originally added to Messenger before March Madness 2016, and still works perfectly to this day.

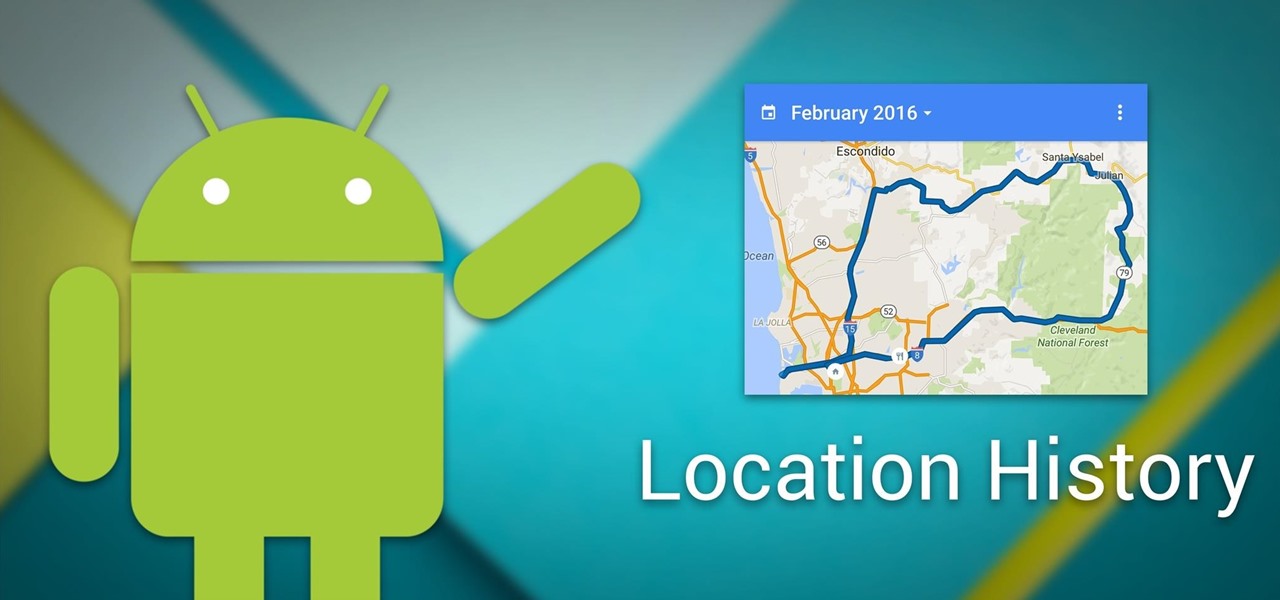
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

Five Phases of Hacking:- The five phases of Hacking are as follow:

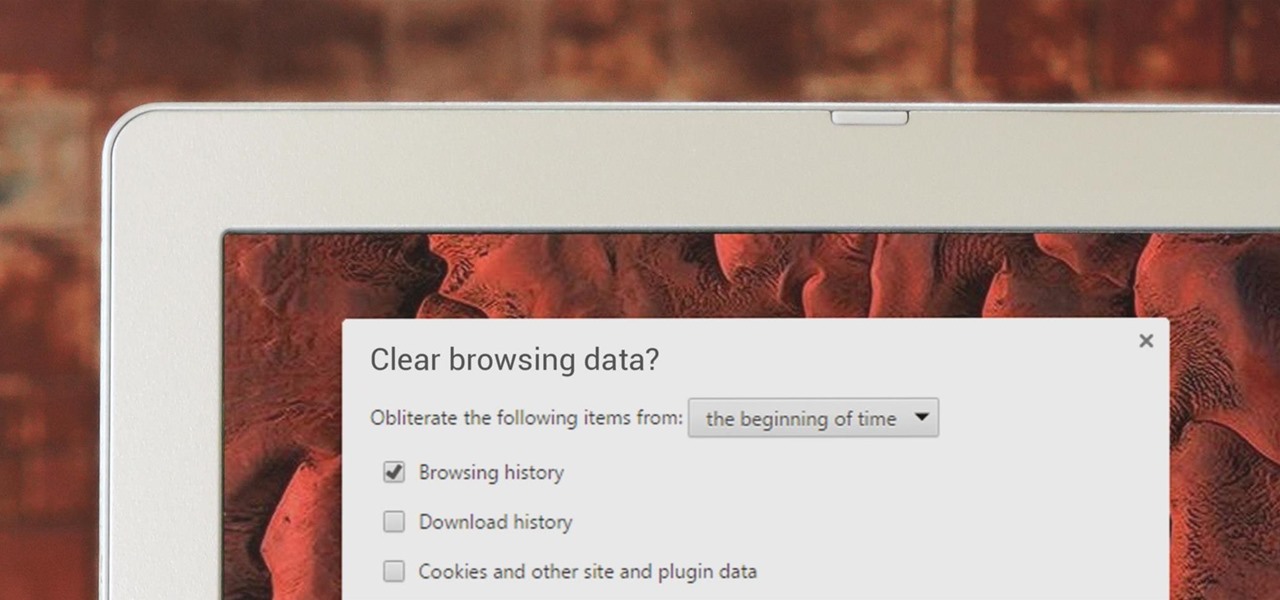
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

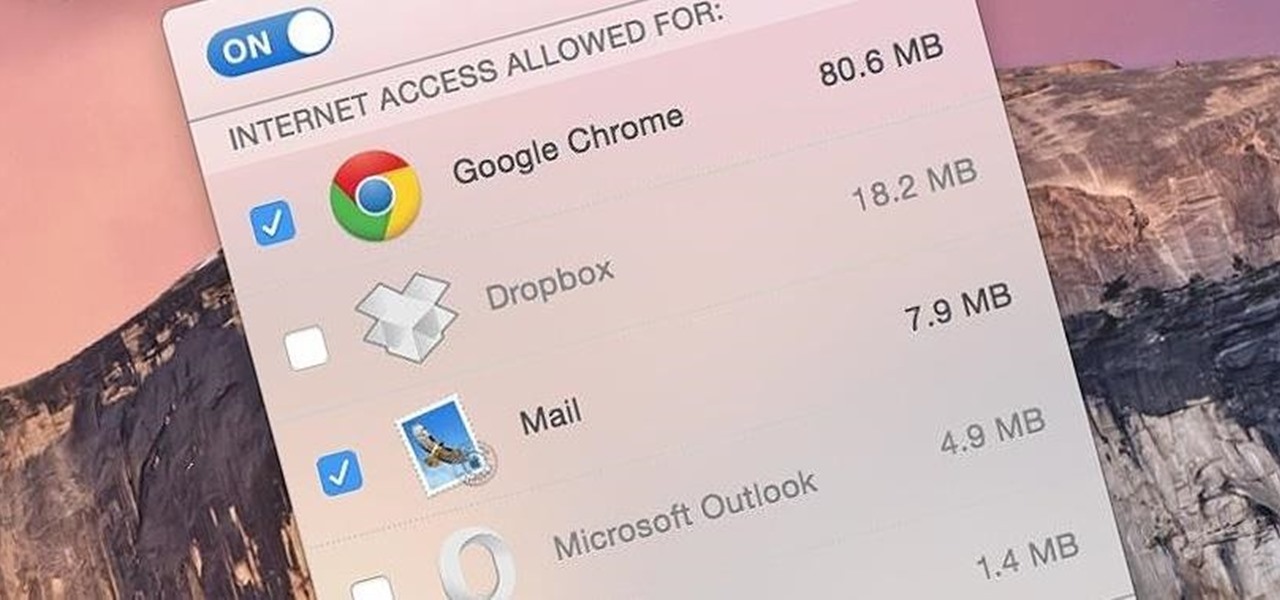
I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.