How To: Download All Loven Musics Free N Legally ! (Music Lovers)
Are you scared that the RIAA is about to track you down for illegally downloading songs. Well, here is a method of obtaining many songs absolutely free that is virtually untrackable

Are you scared that the RIAA is about to track you down for illegally downloading songs. Well, here is a method of obtaining many songs absolutely free that is virtually untrackable

FAST is an expedited travel program for commercial truck drivers that travel between the US and Canada. FAST cards are available to citizens or permanent residents of Canada or the US. The FAST program is viewed as a privilege by both Canada and the US. You can be denied for the FAST program if you do not have a clean driving record and a clean record with the Canadian Border Services and The US Customs and Border Protection. Things such as being caught with undeclared items and having a crim...

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.
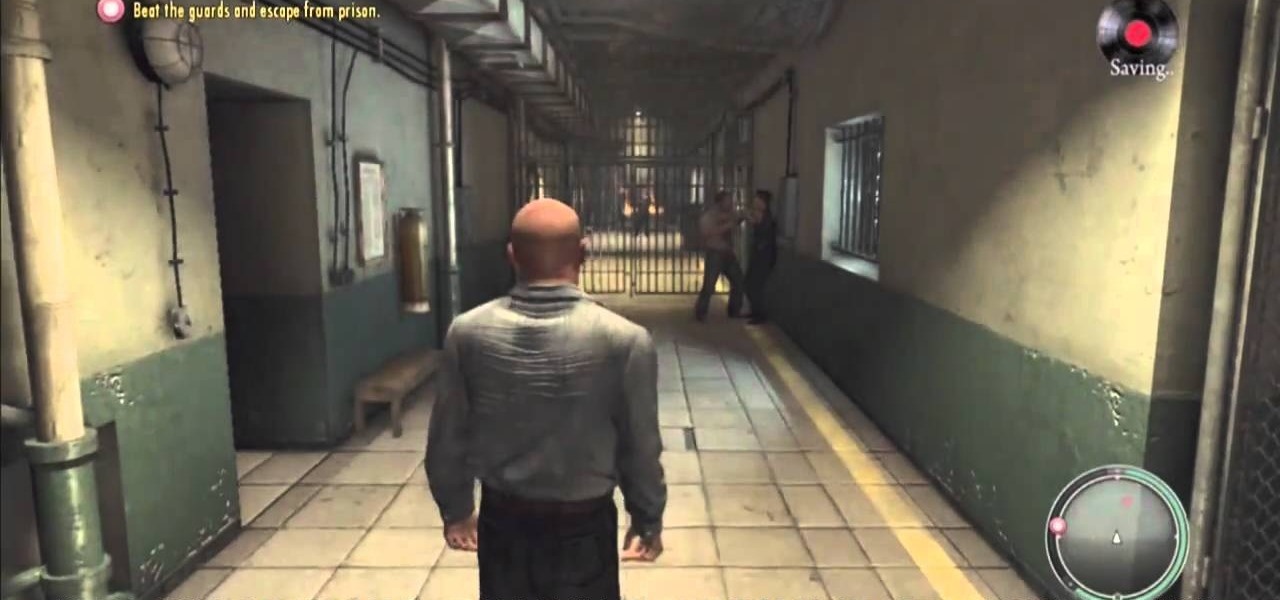
There's a new download available for Mafia II on the Xbox 360 (and PlayStation 3), and this walkthrough series will cover the entire gameplay for "Jimmy's Vendetta", which follows the first DLC for Mafia 2, "The Betrayal of Jimmy" (only available for the PS3). This is a lengthy add-on to Mafia II, so watch and learn to see everything involved with getting out alive, as both the Italians and Irish.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Remember that scene in Tim Burton's Batman where the Joker and his goons defaced dozens of priceless works of art? A collective of digital artists have found a less criminal, more geeky way to do the same thing.

Uber's legal team may have finally sold their engineering golden boy down the river as their war with Waymo continues. Anthony Levandowski isn't your average sacrificial lamb either — given the alleged stealing and all that — but Uber seems set on distancing themselves from this whole fiasco as fast as they can.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.
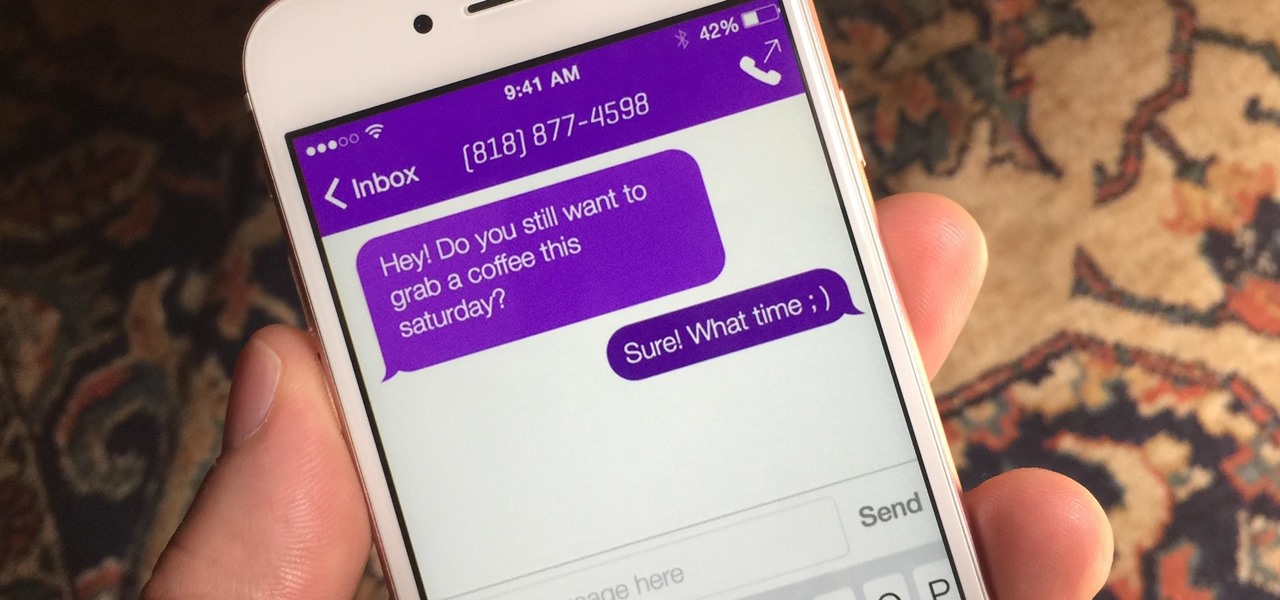
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

Watch this video conning tutorial and learn how to pick a door lock. Maybe you locked yourself out of the house, or you're just a criminal trying to get in somewhere you don't belong. You will need a lock pick and a tension wrench. To make the lock pick in this video take a hacksaw blade and trace a lock pick onto the surface. Lock pick templates can be printed out all over the internet. Next grind it down to size either with a bench grinder or a dremel. To make a tension wrench take out the ...

In Grant City, crimes has taken over, and there's only one man who can help: Jack Slate. With the help of his trusty sidekick canine, Shadow, maverick cop Jack Slate will help restore Grant City to its previous renowned existence as of one of the world's greatest cultural and financial centers, one criminal at a time. While ridding the city of its filth in Dead to Rights: Retribution, Jack and Shadow uncover a conspiracy that threatens their whole existence. And it's up to you to stop it.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.
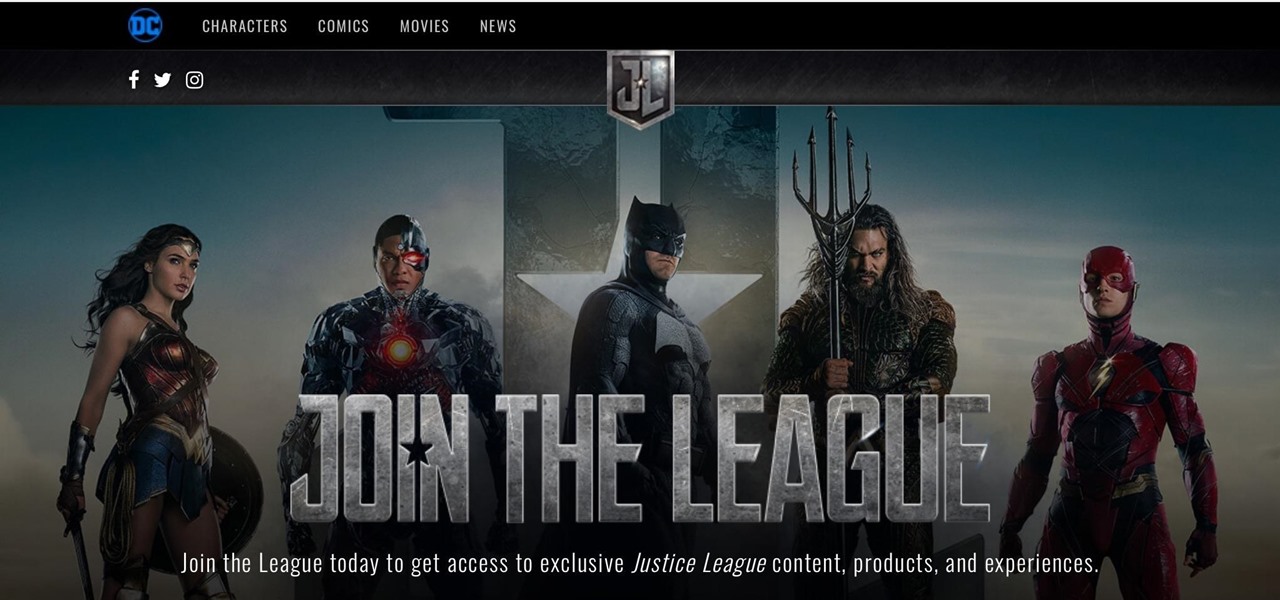
This fall, DC Comics fans will be treated to an augmented reality experience promoting the Justice League movie. Likewise, history buffs will be able to enjoy their own augmented reality content by way of the Terra Cotta Warriors exhibit at The Franklin Institute in Philadelphia, Pennsylvania and an in-store promotion featuring famous convicts from 19 Crimes wines.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.