Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

Your iPhone's built-in Voice Memos app is a great way to record the audio around you, whether it be conversations, lectures, meetings, interviews, discussions, chitchat, gossip, or other kinds of talks. But if your goal is to record audio on the down-low without being noticed, you'll need to know the hidden shortcut.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Watch this video conning tutorial and learn how to pick a door lock. Maybe you locked yourself out of the house, or you're just a criminal trying to get in somewhere you don't belong. You will need a lock pick and a tension wrench. To make the lock pick in this video take a hacksaw blade and trace a lock pick onto the surface. Lock pick templates can be printed out all over the internet. Next grind it down to size either with a bench grinder or a dremel. To make a tension wrench take out the ...

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

So far in this game, my score card: 0-1 from saving a guy from coyotes. My first ever fail in the game.

Materials Needed! Video: Undo a door's chain lock from outside with string, yarn or shoelaces.

White criminal Conrad Zdzierak has committed the ultimate crime of racial stereotyping, plus multiple counts of aggravated robbery after robbing four banks and a CVS pharmacy. The robberies took place on April 9th of this year, but Zdzierak wasn't caught until now, thanks to an incredibly realistic, $650 silicon mask named “The Player”.

Austrian composer Peter Ablinger has created a "speaking" piano. Ablinger digitized a child's voice reciting the Proclamation of the European Environmental Criminal Court to "play" on the piano via MIDI sequencer. Apparently, the computer is connected to the piano, which analyzes the human speech, and then converts it to key-tapping.

An audio recording of an exchange between a teacher and a student at North Rowan High School in North Carolina serves as a reminder that the school system is becoming a training ground for teaching kids to be subservient to the state while indoctrinating them into thinking that the First Amendment doesn't exist.

Acclaimed Cinematographer Adam Kimmel Arrested:

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

(CNSNews.com) – There have been 2,527 Department of Homeland Security (DHS) employees and co-conspirators convicted of corruption and other criminal misconduct since 2004, according to a federal auditor Federal Auditor: 2,527 DHS Employees and Co-Conspirators Convicted of Crimes | CNSNews.com.
California grad student on no-fly list gets home after stranding An American student who discovered he was included on the government’s no-fly list and was barred from a U.S.-bound flight from Costa Rica was reunited with family and friends after he flew to Mexico and then walked across the U.S.-Mexico border Thursday evening.
Los Angeles County Attorney's Office:This website shows pamphlets in English and Spanish; however, not all the pamphlets are available in Spanish. The great thing is that there is a lot of information available in order for victims or any person to understand the proces of: child abuse, domestic violence, crime victims, elder abuse, families surviving criminal homicides, hate crime, Marsy's Law and much more. It is important to be informed at all times for the unexpected. Works Cited "LADA Co...
Anyone who follows the TSA blog, run by “Bob”, will know that from time to time the agency attempts to offset the ballooning negative public opinion directed towards it, and the openly criminal behaviour of its employees, by bragging about “dangerous” items that it has discovered and confiscated from the luggage and persons of those traveling through the nation’s airports.

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

Story, Characters, and Structure Note:
In case you haven't figured out already, our government is always on the move to figure out new ways to extend their control. The CISPA, for one, is one of the best examples, along with "re-education" programs, and racial divide (Trayvon). What I've noticed in the past few months is that their new "ideas" are coming out at an increasingly alarming rate.

Here at WonderHowTo, we are often presented with morally questionable HowTo's. When it comes to stocking our library, we have to weigh in the community value of indexing tutorials with potentially negative repercussions. Where is the line when it comes to areas like weapons, sex, and drugs?

Oleg Mavromati's latest project, Ally/Foe, allows online voters the chance to electrocute the Russian artist at a mere fifty cents a pop. From November 7th to November 13th, viewers of Mavromati's livestream can pay to vote “innocent” or “guilty.” 100 guilty votes result in the artist voluntarily shocking himself in front of the camera, live, with his homemade electrocution machine.

Do you know your constitutional rights if stopped by the police? Washington Post recently ran an interesting article on "10 Rules", a docudrama produced by the D.C. nonprofit Flex Your Rights.

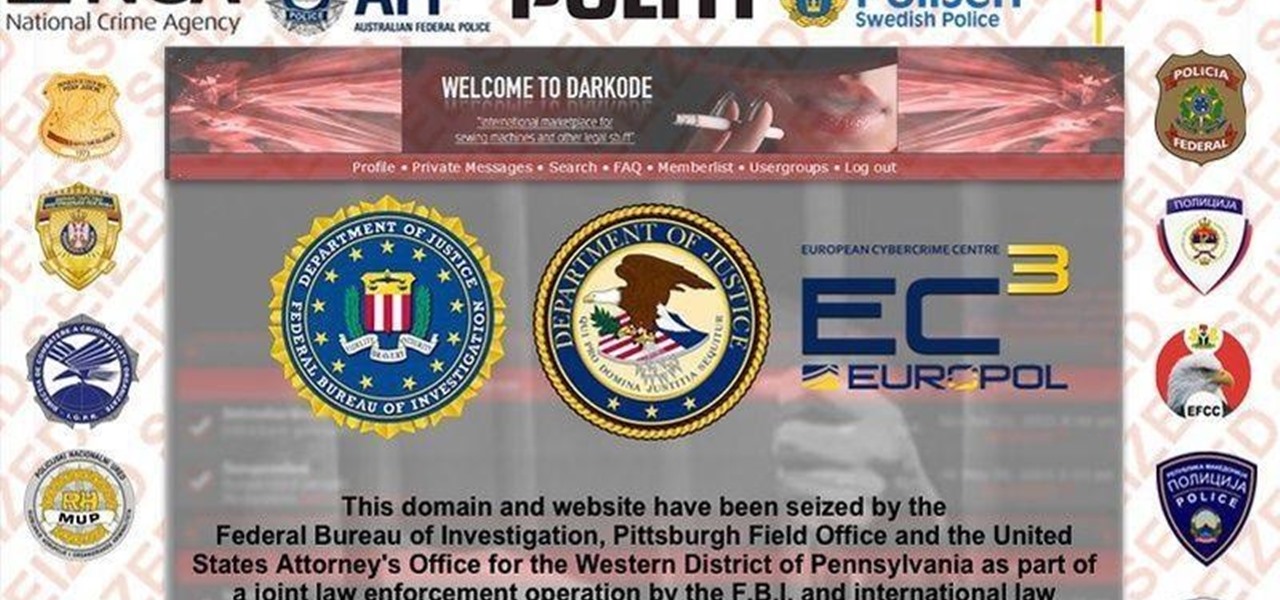
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

The battle between first-person shooters is officially underway with the release of Battlefield 3 today. Who will win? Most experts are already declaring Call of Duty: Modern Warfare 3 the champ of the holiday retail clash between EA and Activision, despite MW3 not coming out until November 8th.

He may have just started his teenage years, but Laurence Rock's future is looking pretty good after inventing an ingenious doorbell device called Smart Bell. He's already sold 20,000 units to telecoms giant Commtel Innovate, and is securing a second deal with an unidentified company that will land him £250,000. That's over $400,000!

For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines