Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.
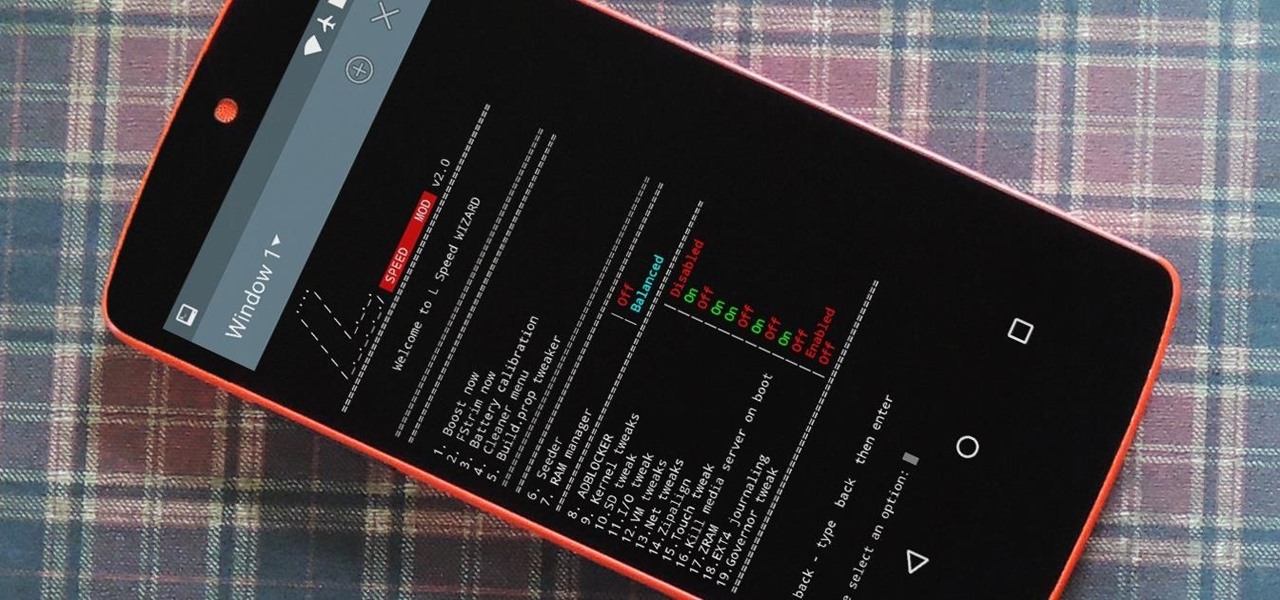
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.

If you are a tattoo enthusiast and love trying new designs but apprehensive about a permanent one, Arabic mehndi design is for you. The designs in this form are not ethnic, conventional or traditional but modern and jazzy. It is made using intelligent spacing that not only enhances the design but gives it a trendy look. They are bright and add a lot of glam to the hands as they are made using different coloured henna- brown, red and black and sometimes even glitters. These are the best form o...

There are so many Hollywood actors who simply love the fishtail braid hairstyle. From Tamsin Egerton to Cheryl Cole to Nicola Mclean, everyone gives thumbs up to this cute braided hairstyle. A lot of them prefer wearing it with their lovely gowns at award shows such as Cannes. It's not surprising at all as to why these celebs love this look- it makes the crown area of the head look voluminous, it can be done even with hair that has steps, it goes with every attire, apt for any occasion as it ...

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

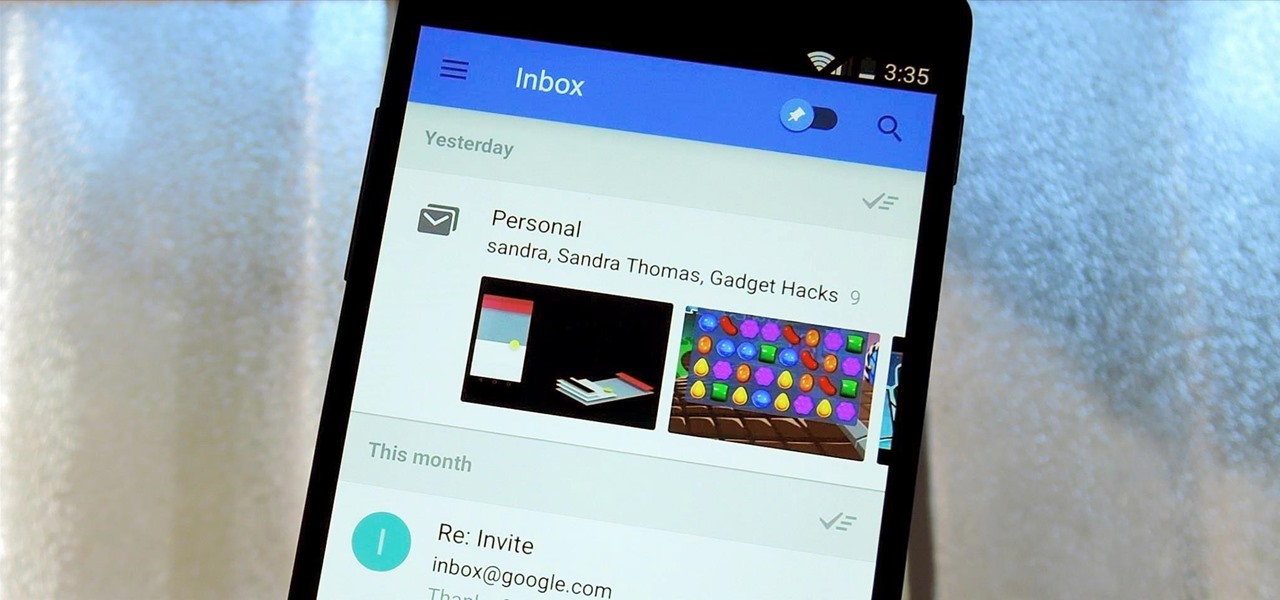
Google's new Inbox by Gmail service wants to fundamentally change the way you handle email, so a bit of a learning curve is to be expected when you're first using the utility. As of right now, the service is invite-only, but if you were lucky enough to get in on the ground floor, you're probably wondering, "How the heck do I use this thing?"

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

As we approach Samsung's unveiling of the next device in the Galaxy Note series—usually in early Fall—SamMobile has provided some exclusive information of the specs of the next phablet flagship.

Are you always afraid to apply lashes by yourself, or that you never get it right? Do you find that your false lashes fall off in the middle of the day? Watch to find out how to apply fake eyelashes or falsies! This is a live step by step tutorial, perfect for beginners!

Samsung released a teaser video today, touting its next flagship Galaxy device, presumably the Galaxy S5. With an official announcement expected on Monday at Mobile World Congress, this video should serve as a final teaser before the big day.

Google's long awaited 4.3 Jelly Bean update is officially out, only it has not been pushed out to some of our Nexus 7 tablets yet. Although there aren't really any new UI changes, most of Jelly Bean 4.3's magic is under the hood, meaning user's can expect better performance and battery life with the latest version.

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.

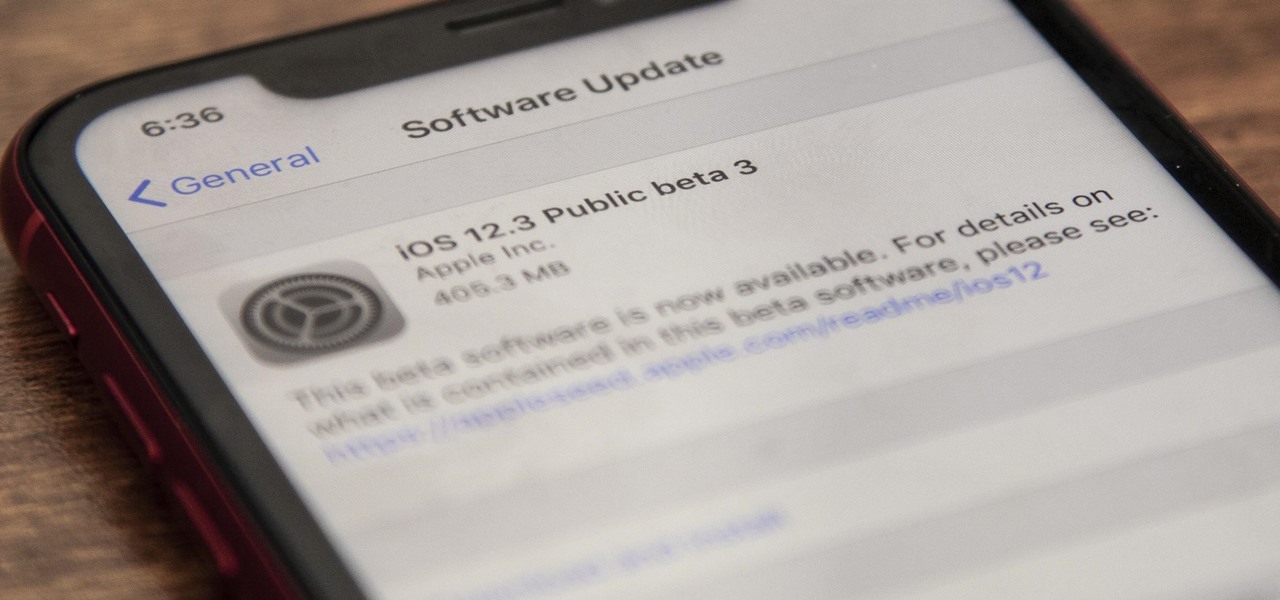
Apple quietly pushed out iOS 12.3 public beta 3 on Tuesday, April 23, just over a day after developer beta 3 was released. Just like with the developer version, there aren't any major features or changes to get excited about, but if you were experiencing any minor bugs with the previous betas on your iPhone, this update could squash some of them.

Developers, get excited. The new iOS 12.3 dev beta 3 just dropped. While this beta doesn't introduce any major features or changes, it means Apple is continuing to address unseen bugs and potential vulnerabilities from the previous versions.

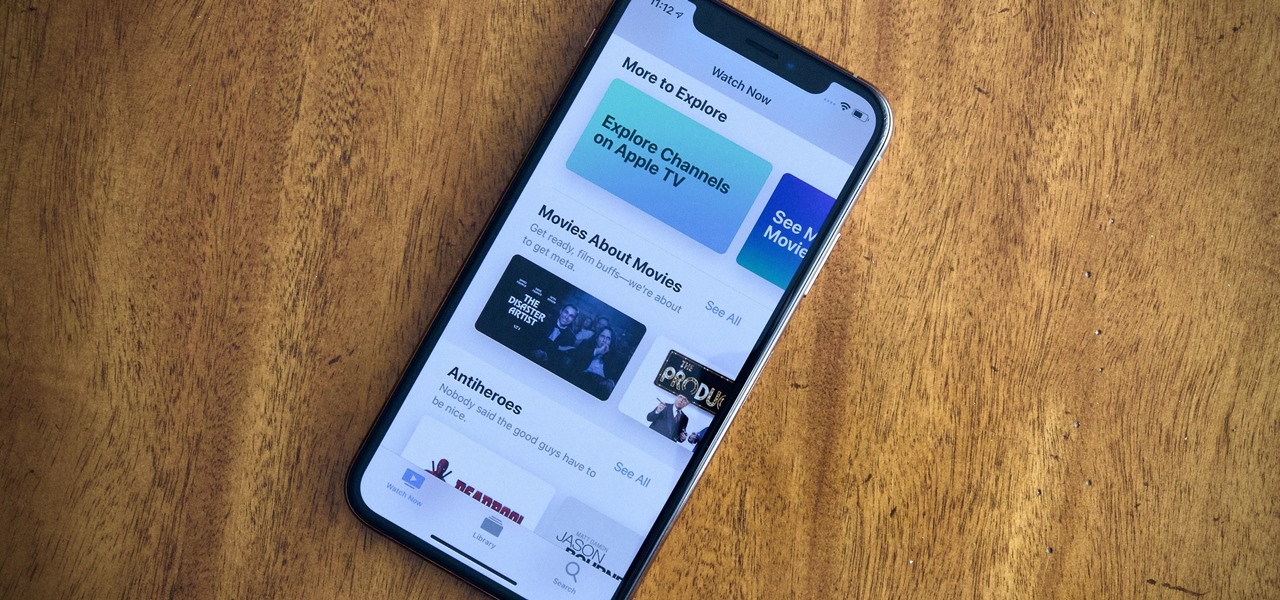
Apple just released the second public beta for iOS 12.3 today, Tuesday, April 9, one day after the release of the iOS 12.3 developer beta 2. This update introduces new Japanese "Date & Time" updates as well as changes to Wallet transactions. Overall, iOS 12.3 includes Apple TV Channels, premium monthly subscriptions with content available directly in the TV app across the Apple ecosystem.

Apple just released iOS 12.3 dev beta 2 today, Monday, April 8, which follows the first iOS 12.3 beta by twelve days. This update introduces new Japanese Date & Time features as well as updates to Wallet transactions. As a whole, iOS 12.3 introduces Apple's previously announced Apple TV Channels, premium monthly subscriptions with content you can watch right in the TV app across Apple products.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

Mere weeks after rumors surfaced that Apple may be working on a headset capable of VR and augmented reality, it appears that Samsung is taking the same approach, but with an assist from Microsoft.

There was big news today from Google, Apple, Volvo, and Nvidia regarding their self-driving efforts.

The Galaxy S8 and S8+ come equipped with all of the hardware needed to access live FM radio, but this feature was never really advertised or even spoken about. Thankfully, though, all you need is an app to enable it.

The new Leaf with Nissan's ProPilot driverless feature could launch as soon as this year, following a teaser image and video the Japanese carmaker released of its flagship EV yesterday.

Depending on your device, when you lower your brightness slider all the way to the minimum, it may still emit a considerable amount of light. This is because manufacturers have the option of setting a minimum brightness value, and while 1 would be the true minimum brightness that your display is capable of, some have set is as high as 5 or even 10.

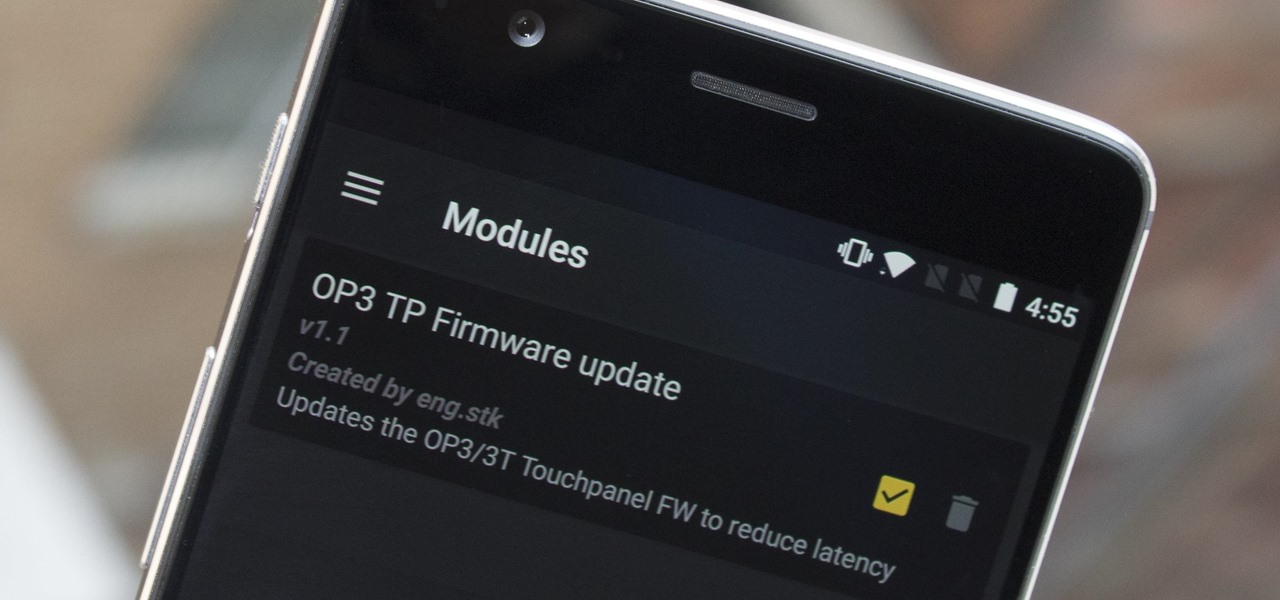
The OnePlus 3 and 3T are a pair of phones which allow you to do practically anything you want, because OnePlus is such a developer-friendly company. They almost always release kernel sources, and their phones sport an unlockable bootloader that doesn't void the warranty. But while their software is certainly solid (miles ahead of Samsung's TouchWiz), it still has room for improvement.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

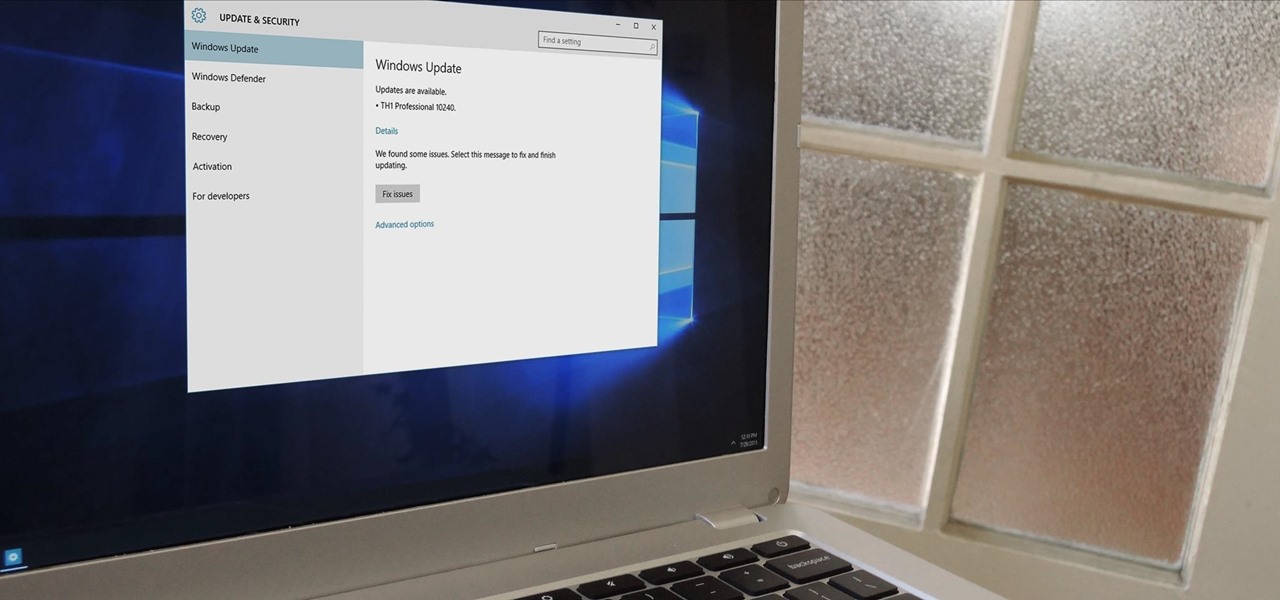
In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.

No one is perfect, and this goes double for software developers. All of the quality assurance testing in the world does nothing when you put a new OS in the hands of everyday users, since we all use our devices in different places and for different reasons. Recently, Cyanogen released their version of Android Lollipop, Cyanogen OS 12, and with it came a whole lot of great features, but some bugs also slipped in.

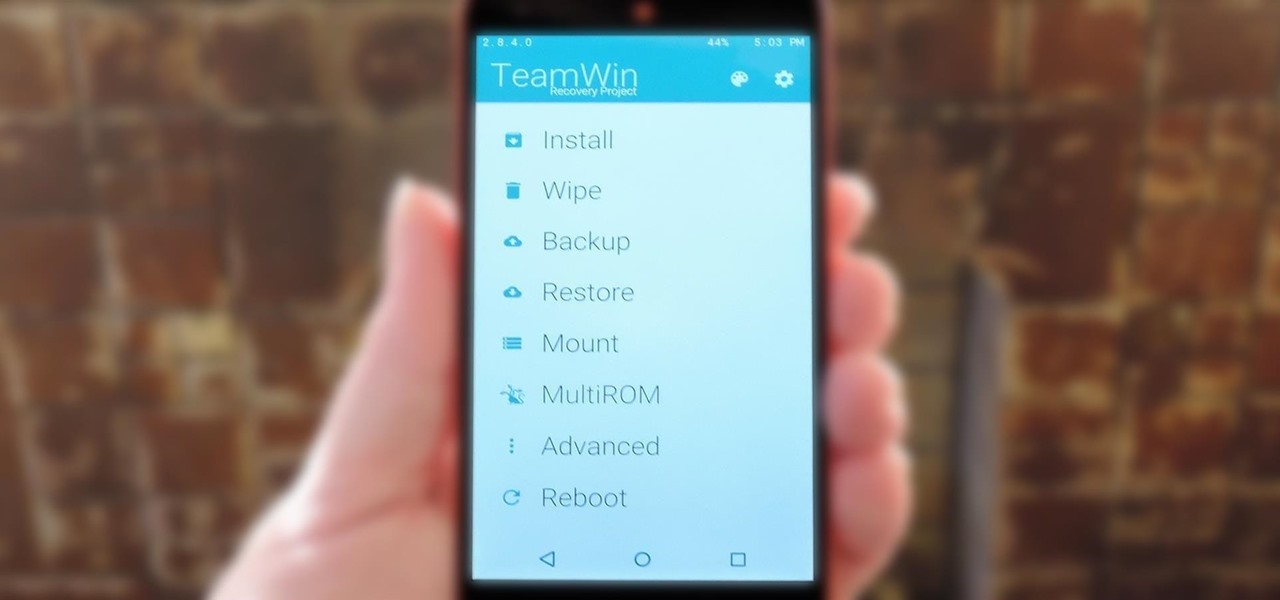
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.

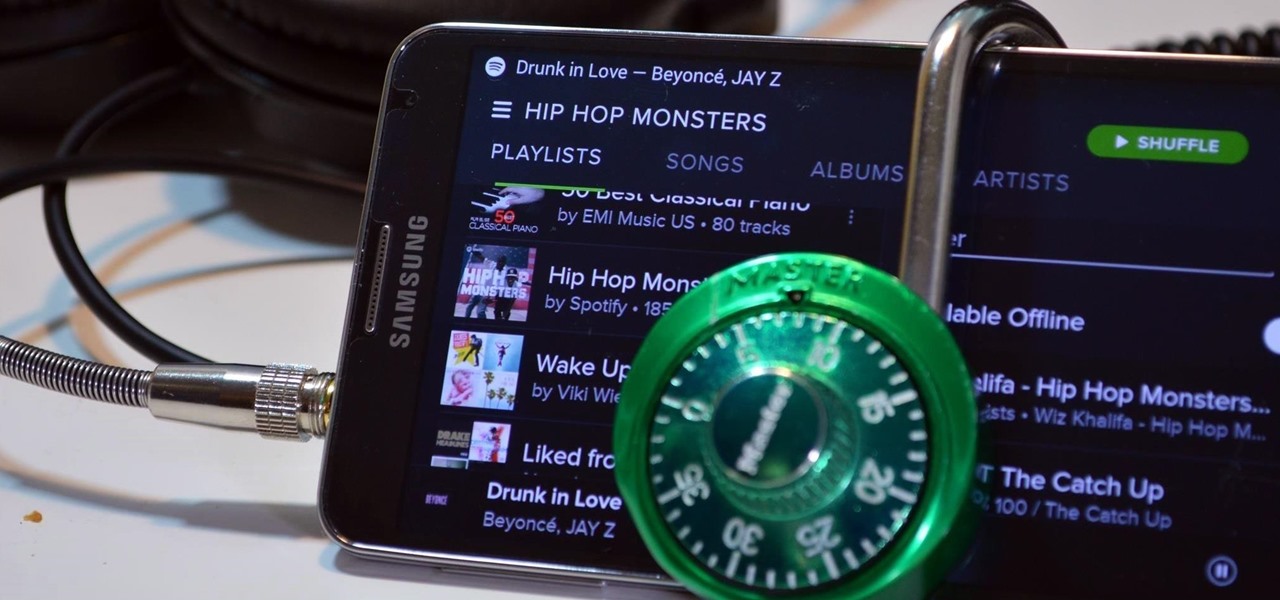
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

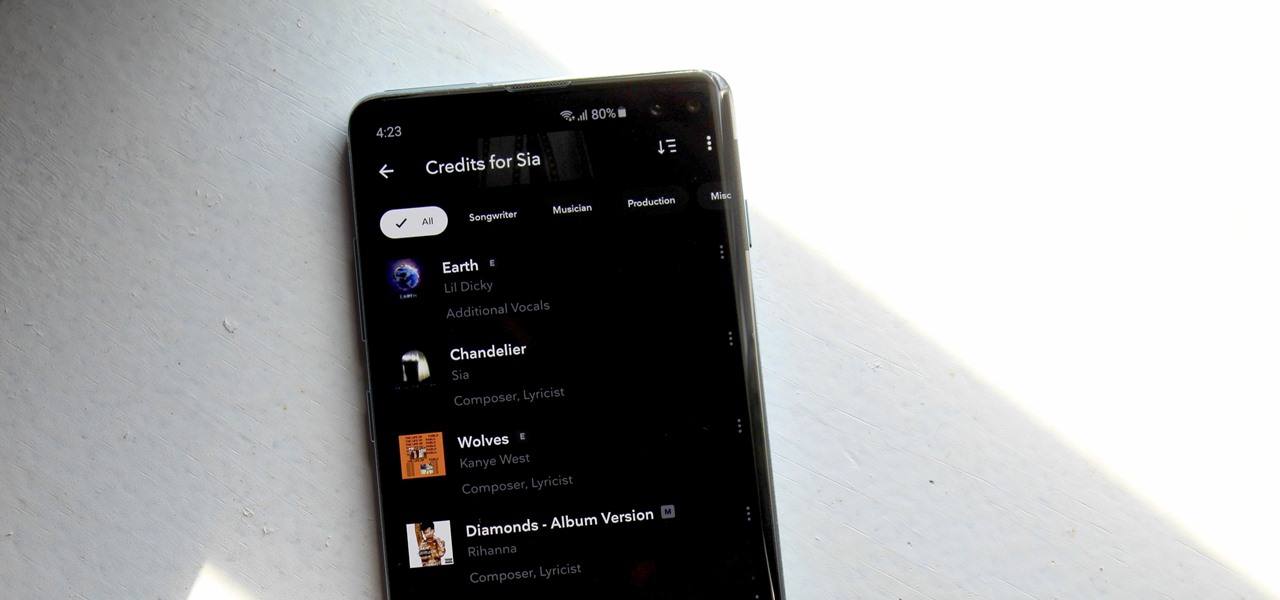
Contrary to popular belief, it takes more than just one artist to create the sound, lyrics, and vocals of a song. With most music being enjoyed digitally nowadays, it's harder to know all of a track's collaborators, as this info used to be in the CD booklet. Well with Tidal, you can now easily find this information and more.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.