You may think you know Microsoft's apps, but did you know that you could be using them as a power user and make yourself way more productive in the process? Thankfully, the easiest way to master them from home is on sale right now, as The Premium Microsoft Office & Data Apps Certification Bundle is on offer for just $39.99 — a huge 97% off the regular price of $1,782.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

In this video, we learn the basics of breastfeeding and how to do it. Breastfeeding is natural and it helps connect the mom to her baby and give proper nutrition to the baby during the most critical months of their life. You will first need to start a technique of hot to breastfeed the baby and what works best for you. You may need to have a midwife help guide you or a counselor to help you learn how to breastfeed properly. You want to position your baby so their head properly hits the right ...

Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all the emails, has been compressed after the mail was deleted. If this hasn't been done it is possible to hack into this file and recover the deleted email. Text-based emails, like those one creates on programs like Eudora,...

Choosing a healthy pregnancy diet goes beyond just avoiding mercury and alcohol! It's critical to ensure that you get satisfactory pregnant nutrition - but the truth is that you're eating for baby at every meal. Watch this video for pregnancy diet tips!

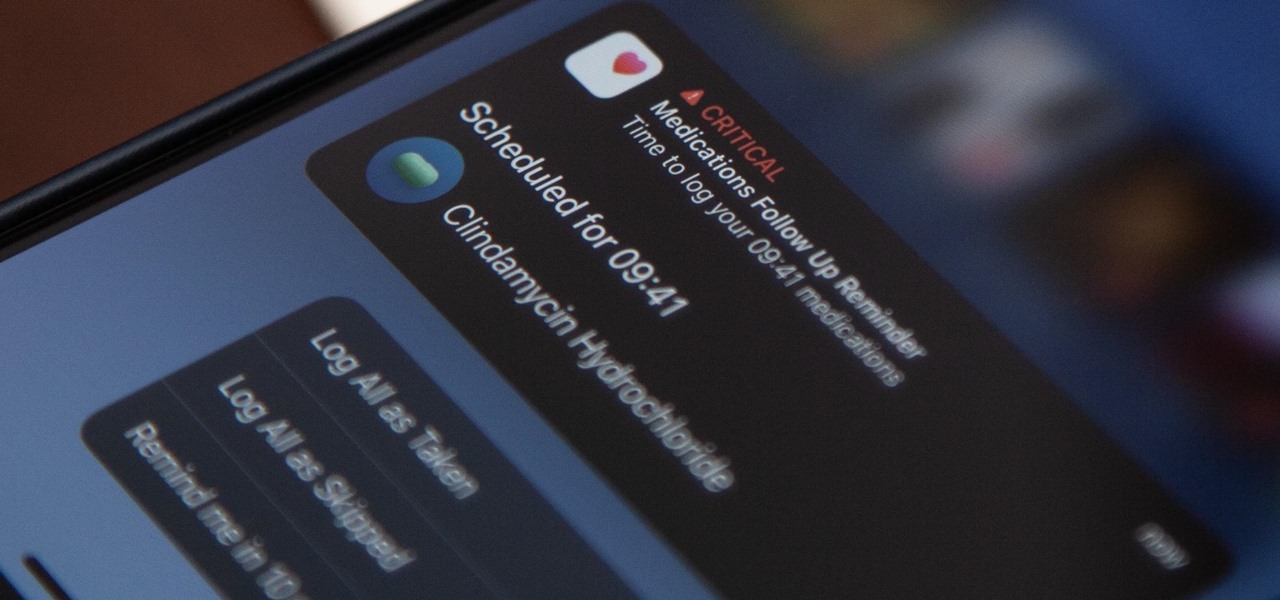
Since iOS 16, you've been able to add and track medication in the Health app, learn about potential drug interactions, and receive dose reminders. With iOS 17, Apple improves that last aspect with even more notification options to ensure you take your medicine on time and never miss a dose.

This week, Snapchat parent Snap came closer to fulfilling its smartglasses destiny by adding new 3D content capabilities to its third-generation Spectacles. At the same time, the now defunct Meta Company continued its fall from grace, as a judge ruled in favor of the plaintiff in the patent infringement case against the Meta 1 and Meta 2 headsets.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

Many people want to jump farther, but they have no progress. What's the problem? It's all about technique. Increase your jumping distance by following the simple tips pointed out in this video. You'll see how to push off and fully extend your body for maximum distance, see how getting extra momentum from fast heel recovery is critical, and learn how to land.

1. Open Web Browser and go to WWW.Google.com and type crucial memory mechanic and press enter. 2. Click the first result found on the search page( i.e., lolo memory mechanic)

Learn how to make some casual, traditional, and unique dishes with tutorial help from myrecipes.com. In this video recipe, learn how to make black forest trifle for kids and the whole family. This is an awesome dessert for anyone. Chocolate cake, chocolate pudding, and dark cherries make up this easy, make-ahead dessert. And since it's low-sugar, it works with a diabetic meal plan.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Creativity is one of our most unique features. We can dream up gods and demons and give them form through drawing. We can even take a two-dimensional surface and bring our ideas to life in three dimensions. It only takes a little training for our giant imaginations to blossom on the page.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

With many of the companies working in augmented and mixed reality focused on the Augmented World Expo, the finance side of the industry has been relatively quiet.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

Legal Services A group of lawyers refused to provide legal services to needy AARP members for $30 per hour, but when asked to do it for free, they readily agreed.

How much time do you spend outside, as opposed to inside? Whether it's because you're working, studying or just have a bunch of errands to run, it may seem like the majority of your day is spent indoors. Ever wondered exactly how much time you spend indoors and outdoors? Now you can, thanks to this DIY Arduino-powered tracking device by Instructables user Gramsky.

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

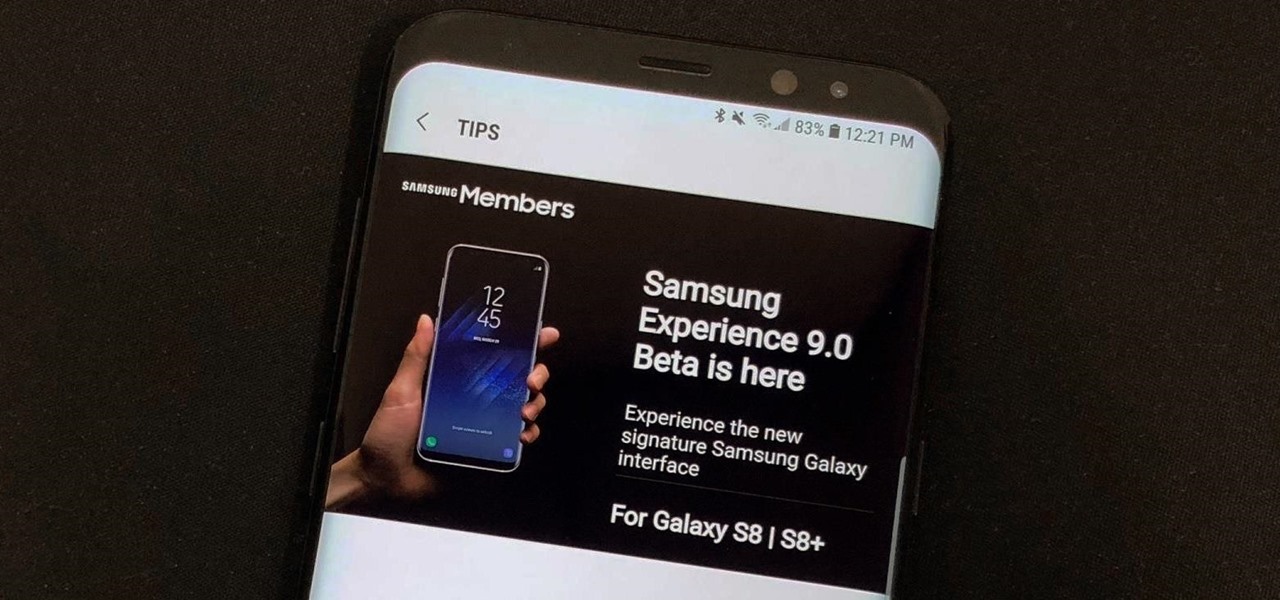
The Android Oreo Beta for the Galaxy S8 and S8+ has been available for nearly two weeks. Samsung started rolling out the Beta 2 update late last week in the UK, and just yesterday in the US. Unfortunately, the US version of the update firmware (G955USQU1ZQK6) experienced a critical bug with the phone app at launch. As a result, Samsung has completely pulled the US Beta 2 update for the time being.