Savor this moment: we've got a confirmed number of sales for the Google smartphone. We say this because unlike most hardware manufacturers, Google refuses to share official sales numbers for their phone. Instead, during earning reports they simply bundle the product under Alphabet's "Other Revenues", leaving us in the dark about how successful the product is.

Learn how to get your body bikini ready. Try these proven methods to get an awesome bathing suit bod.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.

Watch this science video tutorial from Nurd Rage on how to make nitric acid. They show three ways to make nitric acid based on two different chemical approaches, both of which can be done using easily accessible materials.

Want to impress your doctor? Check out this video and learn a few fancy names for common problems and soon your doc will be in awe of your smarts.

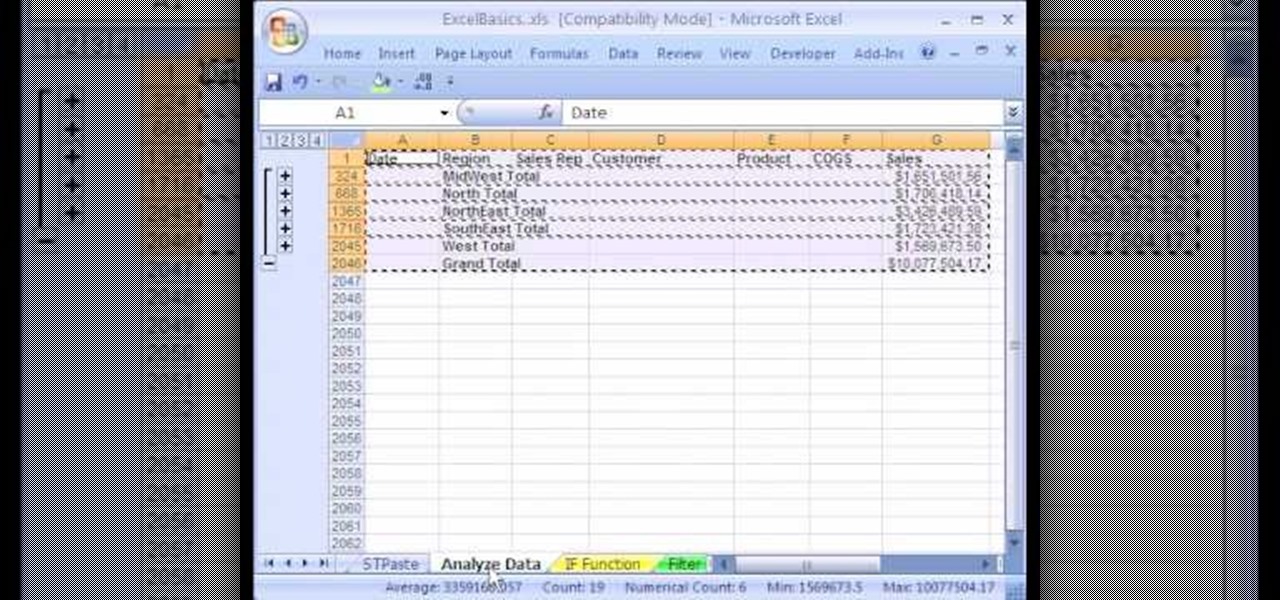
1. The following instruction describes how to generate sub totals in Microsoft Excel Sheet. 2. Take Region as a Primary column and Sales Rep as a Secondary Column. 3. First method to sort: Select a cell in Region and goto Data select A to Z. 4. Second method to sort: Select a cell in Region and Right click and select Sort A to Z 5. Then click a cell in Region and select Data->OutLine->SubTotal 6. In the SubTotal Window select 1.Each Change in: Region 2.Use function:Sum 3.Add subTotal to:Sales...

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Cited by many listed on this year's NR30 list as the most important event in the last 12 months, last year's release of ARKit catapulted Apple CEO Tim Cook to the top of Next Reality's rankings. This week, we dug deeper by explaining why he's at the top of the list of NR30 Mobile AR leaders.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

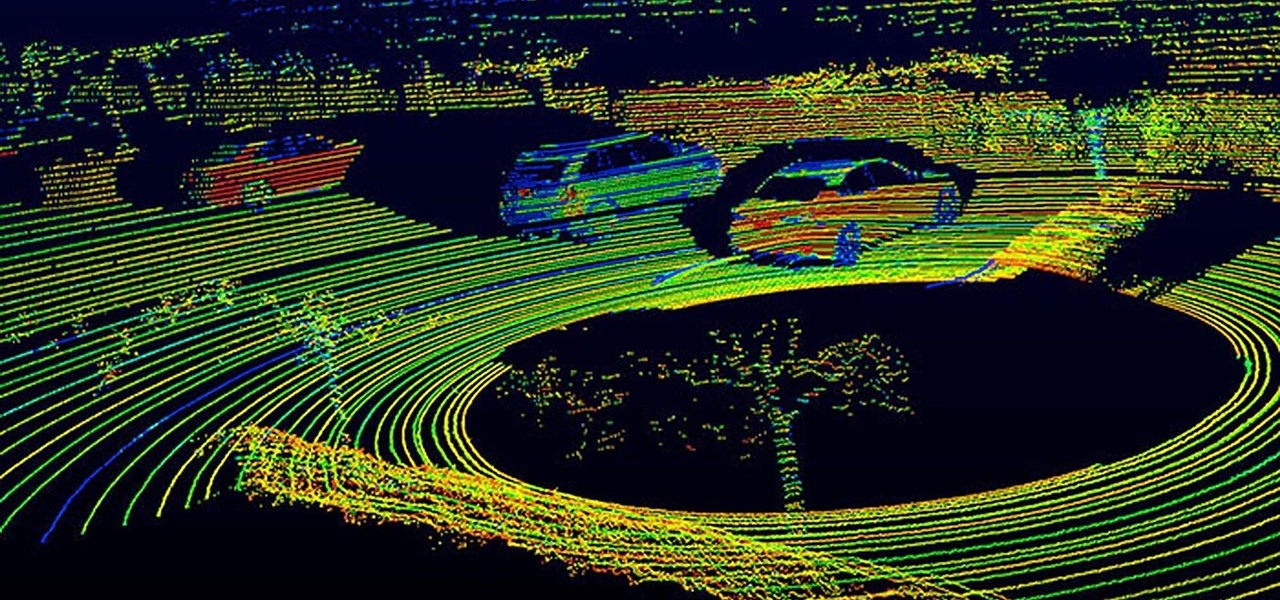
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Air conditioning systems are cold and wet and make great breeding grounds for bacteria and mold, and adding a nasty odor to the air coming out of the vents.

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

The best way to fish is with live bait, but buying bait can be expensive and it isn't always guaranteed fresh. Once you learn how to cast your own bait you will be able to catch large amounts of bait fish on your own, and cut out the middle man. Happy fishing!

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

If you're interested in becoming an in-demand project manager or leader in today's data-driven world, you need to know more than just a few generic management strategies to lead teams and companies successfully.

It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Following up on the initial tease over three months ago, Snap Inc. is finally letting the public get its hands on its new Spectacles 3 wearable device.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

Just when we thought the AT&T partnership with Magic Leap wouldn't really take off until the latter launched a true consumer edition of the Magic Leap One, the dynamic duo jumped into action this week to offer the current generation headset to customers.

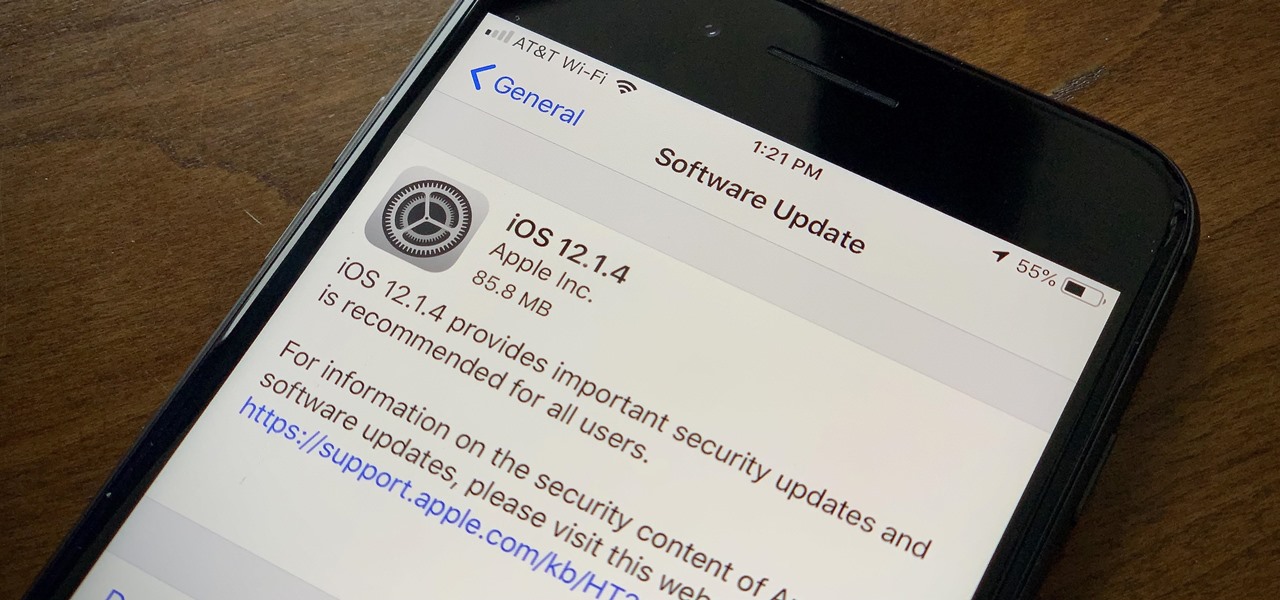
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.