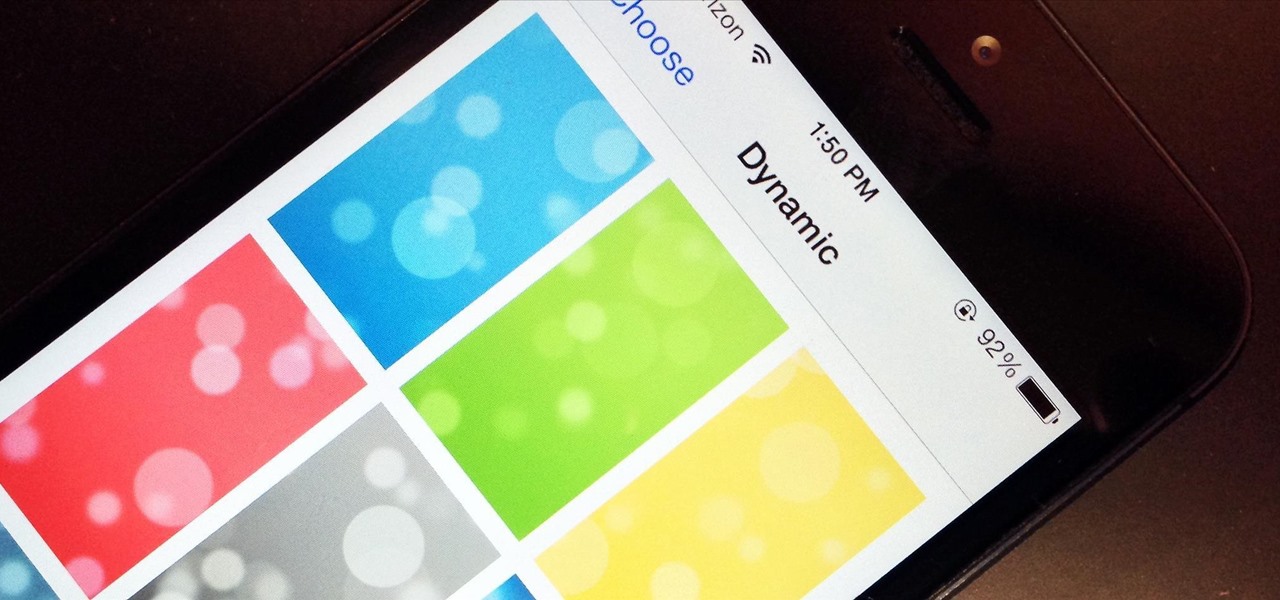
Google's Chromecast streaming device is a marvel of functionality and form. Even with powerful features such as screen mirroring and collaborative party playlists, it's the device's idle screen that first catches the eyes of most folks.

We're a little citrus-obsessed, and with good reason: lemons, limes, oranges, grapefruit: Mother Nature really packed those babies with flavor, from peel (which you can zest without special tools) to juice. Now executive chef Amanda Freitag of Empire Diner has come up with a way to make those lemons and limes give up even more flavor by applying a lot of heat.

Twitter found a sweet spot with its 160-character limit, but Snapchat sports a social media low of 31 characters, forcing us to condense our ideas into a few short words when typing in picture captions because of their ephemeral nature. While this severely limited amount of words is Snapchat etiquette, I've got so much more to say than 31 characters!

Your shiny new HTC One M8 is a pretty stellar device. From controlling your entertainment center to lock screen gestures and camera shortcuts to being pretty damn indestructible, this device has a lot going for it.

If you look at the label on your favorite processed snack, there's a good chance you have no idea what half the ingredients are. It's nothing new, but with natural and organic foods becoming huge trends, we're hyper-aware of all the "chemicals" we eat.

Facial, voice, and hand gestures are the way of the future for controlling our devices, and even gaming consoles like the Xbox One have incorporated them. Unfortunately, our Nexus 7 tablets have not. We're currently limited to using soft keys for most actions, but we can inch closer to the future by replacing one critical action with a simple touch gesture—going back.

We've all been there. Rushing to find an outlet because your smartphone's battery is about to die and you're in the middle of uploading a picture on Instagram or something else of dire importance. Android's operating system shuts down automatically when ever there is 1% left in order to allow for a proper shut down, and so as not to mess with the calibration of the battery, extending its overall life.

Call of Duty may be one of the best video game franchises ever, but I doubt you'll see very many people dressed up as COD characters this Halloween. As awesome as the games are, there just aren't any memorable characters when it comes to looks—besides one.

I want my Halloween costume to take as little effort as possible and be cheap—extremely cheap. That means I don't want to pay 50 bucks for some costume online or spend all day playing with liquid latex, and I most definitely do not want to visit a super crowded costume store in Hollywood.

During today's press event at the company's headquarters in Cupertino, California, Apple announced that iOS 7 will come bundled with several new ringtones—something that has stayed relatively static the past few years.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

Panoramic live wallpapers for the iPhone? If the first beta version of iOS 7 is indicative of the imminent public release of Apple's revamped mobile operating system, the answer is a resounding yes.

Live wallpapers are part of what make Android's features so unique and wonderful, making your homescreens come alive and much more interesting. The wallpapers are extremely customizable and interactive, many times sensitive to swipes, finger-tapping, and other multi-touch gestures—Ditalix being one of the frontrunner apps in the field. The only problem with these live wallpapers is the toll it takes on the device's battery. While not all live wallpapers kill the battery, there are many of the...

In yesterday's tidbit, we learned that across the planet women seek material wealth in their mates. This stems from our hunter-gather past in which females depended on male hunters to provide them and their children the meat necessary to support their large brains.

LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene.

On average, it takes three seconds to move your hand from the keyboard to the mouse, then click once and move your hand back to the keyboard. While the time wasted my sound trivial, it can add up quickly throughout the day.

Lucid dreaming, in which you're aware that you're dreaming, can be profoundly beneficial to us. It gives us freedom to do things we couldn't possibly do in the real world. It can show us the true potential of our brain power. You can even use lucid dreaming to question the nature of our own reality. For whatever reason, people everywhere are interested in this mysterious phenomenon...especially in achieving it. Whether it be visiting another planet or flying around, the possibilities in lucid...

There are plenty of ways to take double exposure photos, even if all you have is your cell phone. If you have access to a darkroom (or Photoshop), you can do it by stacking negatives. But if you have the right kind of DSLR, you can do it right from your camera by using the multiple exposure setting.

No one likes to think about the possibility of natural disasters, but we all know they could happen at any time. Some of us are a little more paranoid than others, but wouldn't it be nice to know that you'd be protected if anything really crazy ever happened? Like the zombie apocalypse?

Change your damage output, and make sure that every time you land a blow, it is a critical hit. You can also hack Ninja Saga to rocket your character to level 60 - all you need is Cheat Engine and Firefox.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

About a third of the methane released into the environment comes from the production and transport of natural gas. The gas leaks as it moves along the transport chain from gas wellheads to market.

The Great Barrier Reef in Australia is the largest living system on the planet. Yet more than 90% of the reef is bleaching because of the loss of a tiny algae that lives within the coral.

We may not fully appreciate all the important roles wheat plays in our lives until it's gone—or at least, when it's in very short supply. What would a world be like without bread, cakes, cereal, pasta, or wheat beer? If the dire warnings about an impending stem rust fungus come to pass, we may know all too soon.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Yossarian the Grammarian lays bare the nature of the indirect object and the much less well known objective complement. Great English grammar lesson for ESL students.

Not sure how to size your golf club? Thanks to expert golf site Golf Link, here's your chance for a free lesson. The most critical part of a golf club's size is the shaft, and it's necessary for a person to find out about the flex point and torque of a club's shaft. Discover why golfers with higher handicaps will want a flex point that will kick the ball in the air more in this video.

If your new window treatments include blinds, save the hefty installation fee by hanging them yourself.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

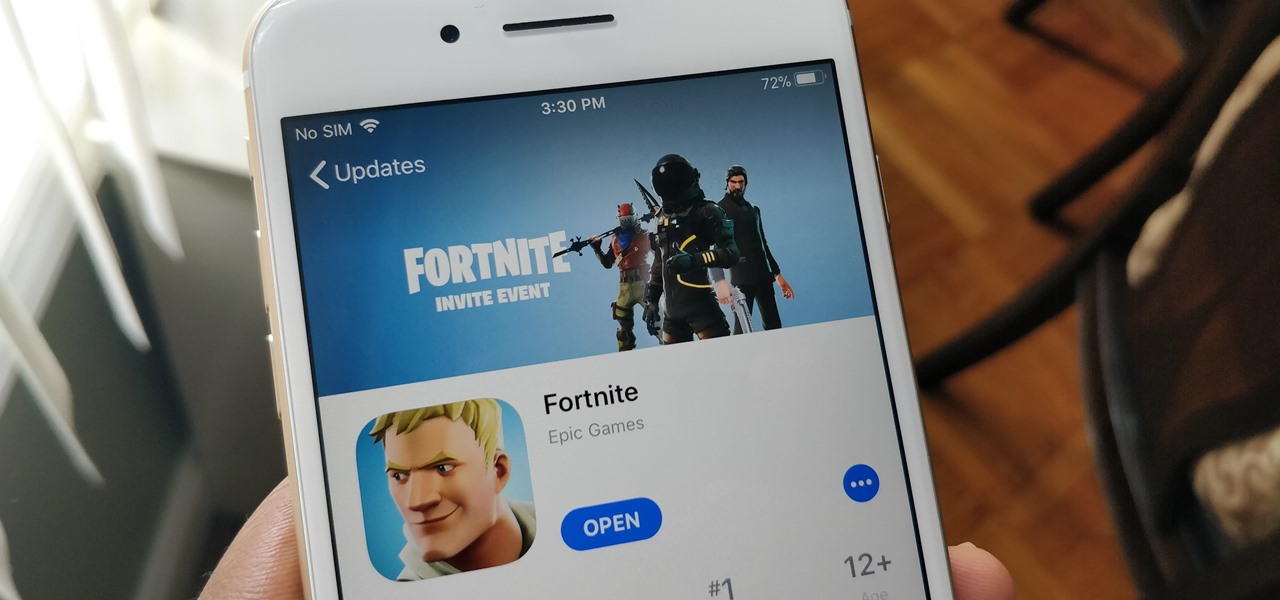
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

Twelve-year old Rory Staunton took a dive for a basketball during gym class and came up with a cut on his arm. The school nurse applied a couple of band-aids, without cleaning the cut, and off he went. In approximately three days, hospital physicians told his parents there was nothing else that they could do for their son; he was dead.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

The hunt for the mixed reality use-case that wins over consumers' hearts and creates a critical mass is a problem every developer would love to solve. Not only would they find themselves rich and famous seemingly overnight, but they would also end up making one of the various possible hardware solutions a viable place for other developers to put their time and energy.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.