The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Dawn Griffith creates a cute card with a 3D lemonade glass embellishment from start to finish. Create a template by making a rough sketch of an 8 ounce paper cup onto a piece of white cardstock and cut it out. Take the template and either trace it onto a piece of vellum cardstock and cut it out, or use Dotto adhesive to attach the template directly to the vellum and then cut around the shape. Score each side at about 1/4", fold on the score lines and trim the overlap at the top. Apply sticky ...

Watch this video tutorial from the Polish Guy to see how to polish aluminum alloy car rims with Simichrome and a buff ball. In this demonstration we use Simichrome Polish and a Flitz Buff Ball to clean and polish a Subaru wheel rim. The tutorial includes detailed work instructions and best practices.

A Millbank bag is a great way to filter water into drinking water. While bacteria is not removed by a Millbank bag, large debris is filtered out so the water can be boiled or purified by other means. Watch this video survival training tutorial and learn how to use a Millbank bag to filter water in nature.

In this video from Raw Radiant Health, Natasha explains how to begin a raw food diet. First, you need to decide when you want to start. Clearly define your goals and stick with them. Once you set a starting date, you can prepare your kitchen beforehand. Your fruit should be ripe. She always has ripe fruit in her kitchen, but she also keeps things that are jut beginning to ripen, so that there is always food that can be eaten immediately, and also food that can wait a while before eating.

Learn how to read a person just by looking at their hand using the ancient art of palmistry. Step 1

To grow beautiful flowers and plants in an outdoor garden, you need to feed your soil the right plant food – a fertilizer that will help your plants thrive. Watch this video to learn how to choose plant fertilizer.

All of these four videos are excellent. You will notice that while all the videos and articles have slightly different design dimensions, they are fundamentally very similar. I urge you to view and read everything I am serving up. Then, my final words of advice are simply....choose between a barbeque switch and a taser gun. (Hint: there is a right choice, and there is a wrong choice.)

With the latest version of ARKit and a new set augmented reality development tools set to arrive this Fall with iOS 13, Apple has taken an unprecedented step in recruiting Chinese developers to fill the App Store with mobile AR apps now, likely with an eye to the future.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again.

After raising more $100 million in funding from some of the tech world's biggest names, Mojo Vision is finally ready to show the world the building block of its "invisible computing" platform.

Spring is here across the US, but, through the lens of Snapchat and augmented reality, winter is coming to New York.

While the tech industries giants and eager startups chase the dream of widespread consumer augmented reality, enterprise AR is living the dream today.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

The city of London is getting a holiday gift this season, but it's not the kind you unwrap, since it's completely delivered in augmented reality.

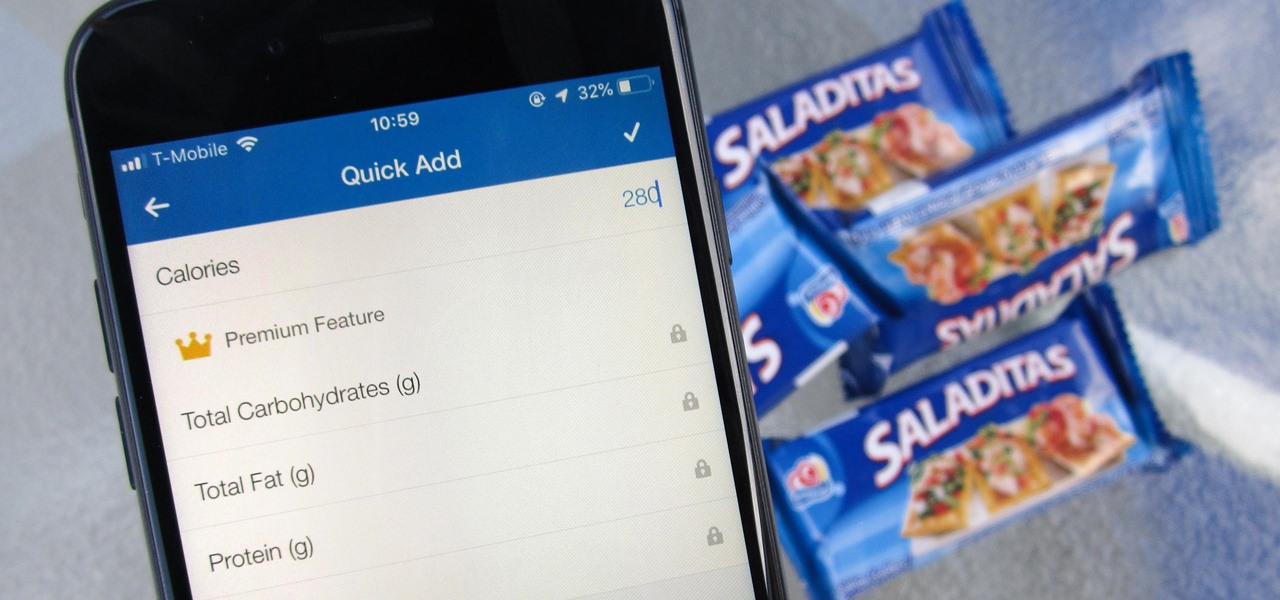
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

Smartglasses and AR headset makers like Microsoft, Magic Leap, and Google (and aspiring AR wearables makers like Apple and Snapchat) need display components for their products, and LetinAR is among the companies ready to supply those components.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

After a $20 million funding round fell through, augmented reality headset maker Meta Company has been forced to furlough (or place on temporary leave of absence) approximately 65% of its workforce for 30 days.

The display is one of the most critical components in augmented reality hardware, and on Tuesday, one of the companies making that component, Avegant Corp., closed a funding round of $12 million to support development of next-generation AR displays.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

On Tuesday, Unity released the latest version of its 3D engine, which brings improvements to the Scriptable Render Pipeline that the company introduced earlier this year.

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.