There are a lot of people out there who don't like vegetables, but I would contend that that's because they haven't eaten any really good vegetables. I thought I hated tomatoes (okay, technically a fruit, but used mostly as a vegetable) until I ate some fresh from a garden. One bite of a juicy, ripe heirloom tomato made me realize that I love tomatoes—it's those bland, mealy supermarket tomatoes that I hate.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

Welcome back, my greenhorn hackers!

The lock screen in iOS 7 is great at giving you immediate access to notifications, weather forecasts, date and time, music controls, and even the camera, but for a sports fan like me, there's one critical thing missing—game scores and news highlights.

Slide to left, slide to the right, one hop this time. Okay, so maybe those are some of the dance instructions for the "Cha Cha Slide", but sliding and swiping on your Samsung Galaxy S3 can become so much more than just a simple gesture.

While the Galaxy Note 3 and Galaxy S4 are enjoying their official KitKat updates, those of us with Note 2s are left to play the waiting game. While we know our devices will eventually see an update to Android 4.4.2 KitKat, it's unclear when an official update for our devices will come.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

One of the best-selling video game consoles of all time is the Nintendo Entertainment System, better known by its acronym, NES. However, cartridge-based gaming consoles are a pain now when compared to the newer download-and-play alternatives.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

It may not seem like it, but the Status bar at the top of your Samsung Galaxy Note 2 is one of the most important and heavily utilized features. From checking the time, to finding out your battery percentage, to viewing Wi-Fi and cellular connections, the Status bar is critical for keeping tabs on your device.

For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.

Microsoft released a preview version of Windows 8.1 today, notably adding an updated Start screen, the ability to run several Windows 8 apps side by side in a number of configurations, fully integrated search, better HiDPI support for multiple monitors, and for those who miss it, options to bring back the Start button or boot straight to the desktop.

How to find a stud in the wall. How would you like to be able to find a stud in a plaster wall / drywall wall, easily and every time without an expensive stud finder? Let's look at how to find a wall stud using three conventional methods then l'll explain my foolproof method of how to find a stud in the wall without a stud finder.

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

We don't generally think of medicine as being very relevant to Steampunk, but it was a big part of Victorian science fiction. Notable examples that you may be familiar with would be Frankenstein and The Strange Case of Dr. Jekyll and Mr. Hyde.

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

In this video series, watch as Gnobo Calypso teaches all about mystical numerology. Learn all about patterns, anthropocosmic beings, nature's flow, the sacred geometry, universal vibrations, mystical energy as Ra, Isis, Maat, and Numena, and the Age of Aquarius.

This video explains how to train a Pit Bull terrier. Begin training at seven weeks, but formal obedience training should begin at 4 - 6 months. Be sure to use positive training methods that rely on praise and treats as motivators, rather than pain.

With all of the hype around the new iPhone 13 series and new iPad and iPad mini unveiled this week, it would be easy to overlook a very critical update for the device you already have in your pocket.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Depending on where you live, you will have to prepare for the hazards from different types of natural disasters. You can sleep easy if you have a secure location, stalked with food and supplied you might need if there is an emergency.

This video clip series will cover everything you will need to know about getting started improvising on the Native American flute. Not only will our very experienced expert show you some important improvising techniques such as vibrato and bending notes but you will also learn about the importance of using nature as an inspirational tool to help you create better music. Take these tips and start having fun with your new talent!

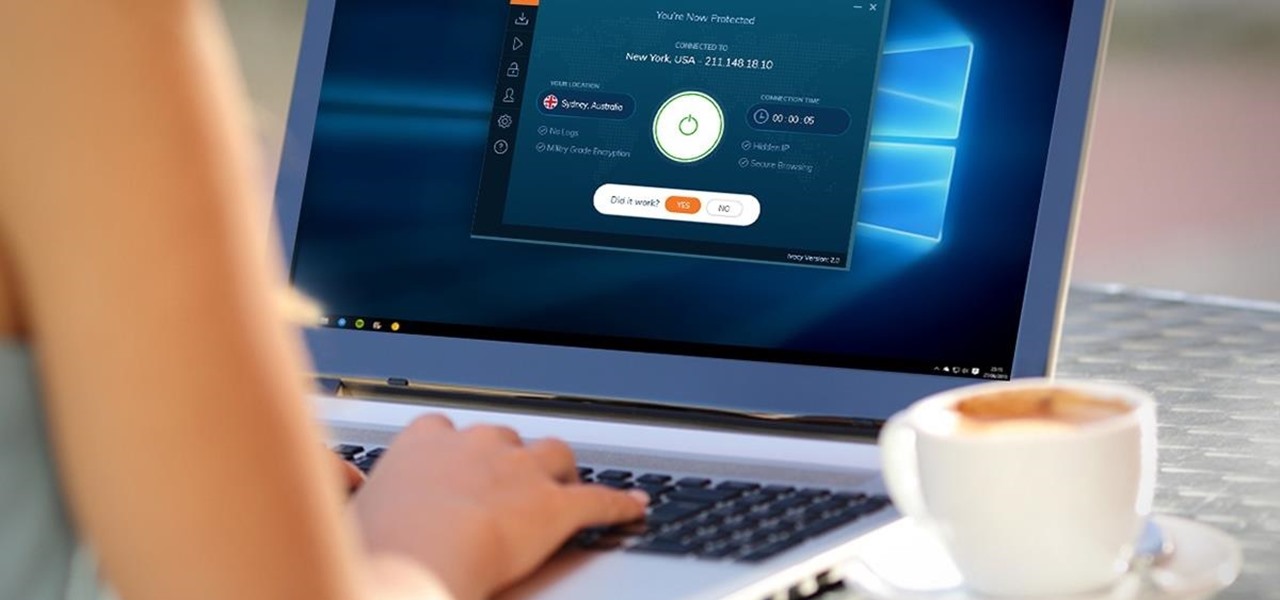
Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.