Is your fridge getting out of control? Can't identify that raunchy smell that has invaded your ice box? Can't find your ketchup? The best way to alleviate these problems is by organization. Organizing and keeping your fridge tidy is the best way to go, but it could be hard in a roommate situation where one said roommate will never give a damn. Nonetheless… chill out! Use these helpful tips to get your refrigerator organized.

With careful wording you can avoid lying and still avoid going to something that you just don’t want to attend. Even without a good excuse you can politely decline without hurting anyone’s feelings or ending up in an embarrassing situation.

What management style is best for you? Each situation can call on a different style. Learn about each style and when to use them from a communications and public speaking expert in the free instructional video series.
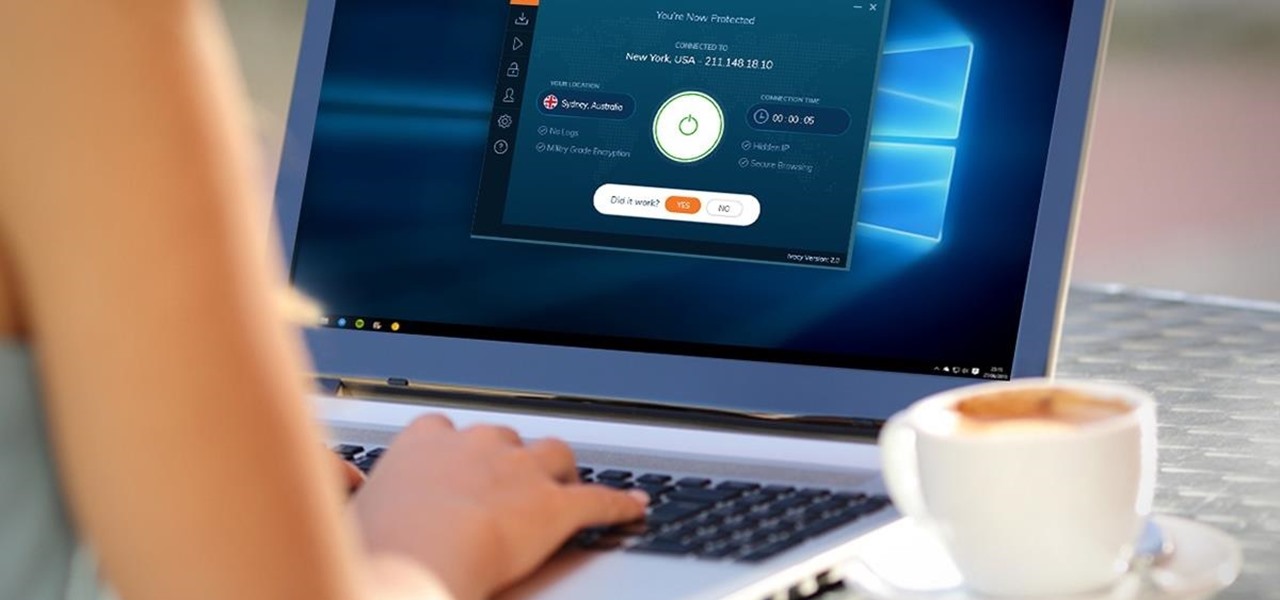
Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.

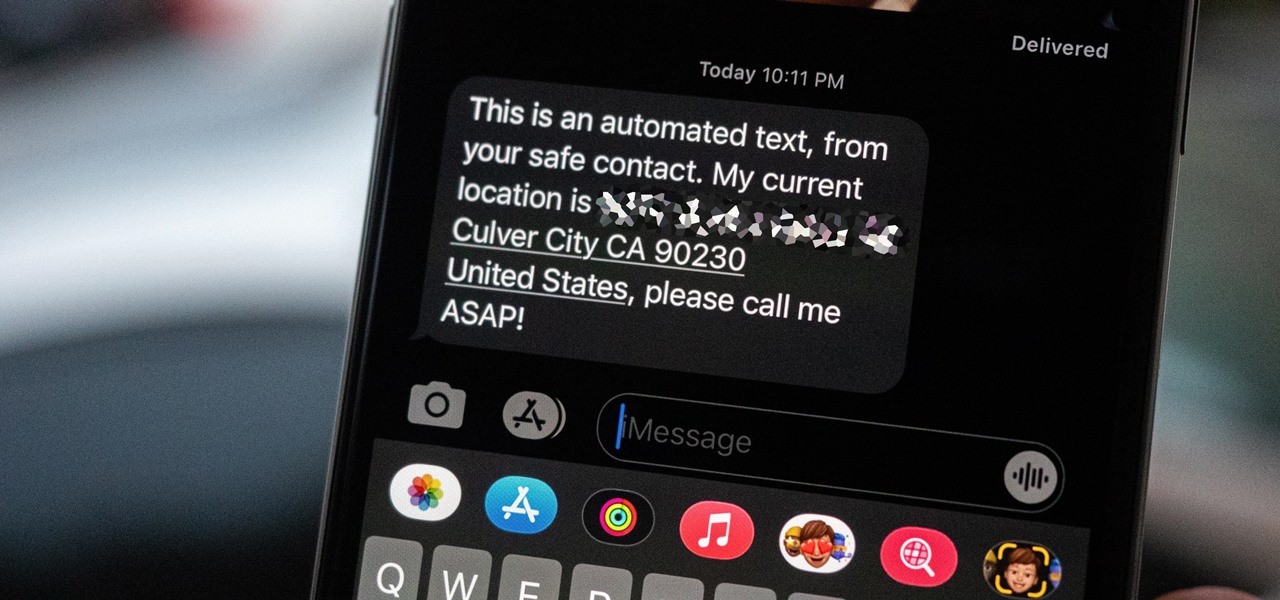
Strange or uncomfortable encounters can be difficult to get away from sometimes if you're overly polite and don't want to hurt anybody's feelings. Thankfully, your iPhone can help save the day, providing you with a plausible excuse to exit the scene without having to conjure up some last-minute reason on the spot.

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

Whether you're binging "Friends," "Game of Thrones," or Harry Potter movies, if you want to watch HBO Max downloads in the highest quality possible, you can't just use the default settings. Without doing the legwork, the TV shows and films you download onto your iPhone or Android phone will be lower quality than the full HD version you can have.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.

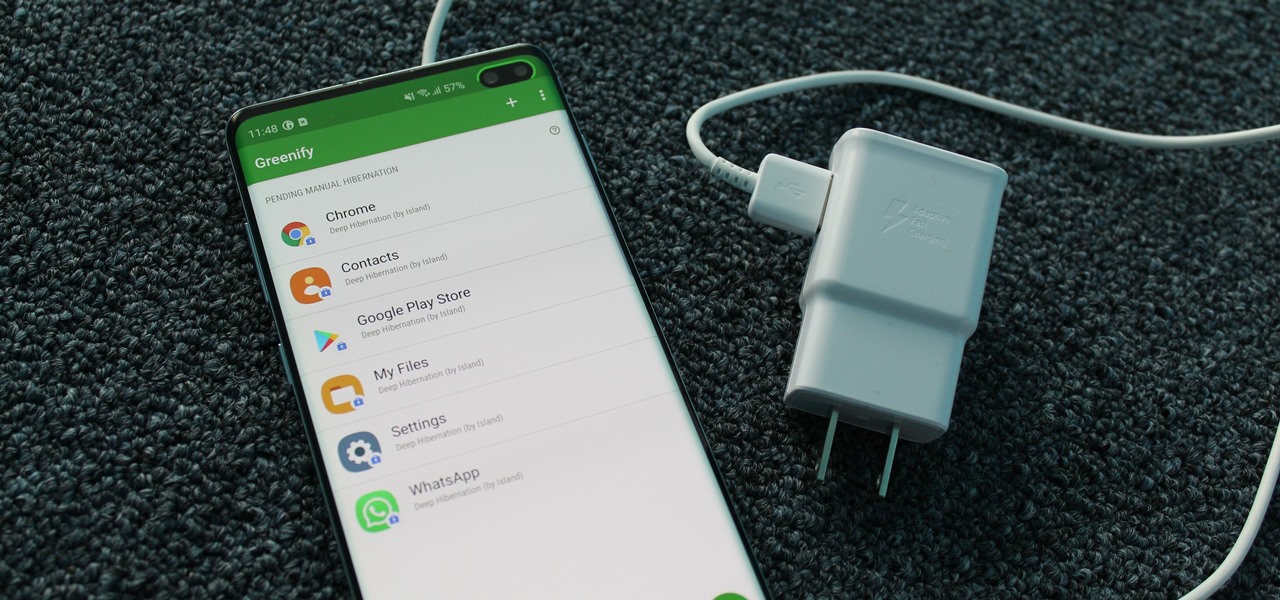
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need root to use it.

The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

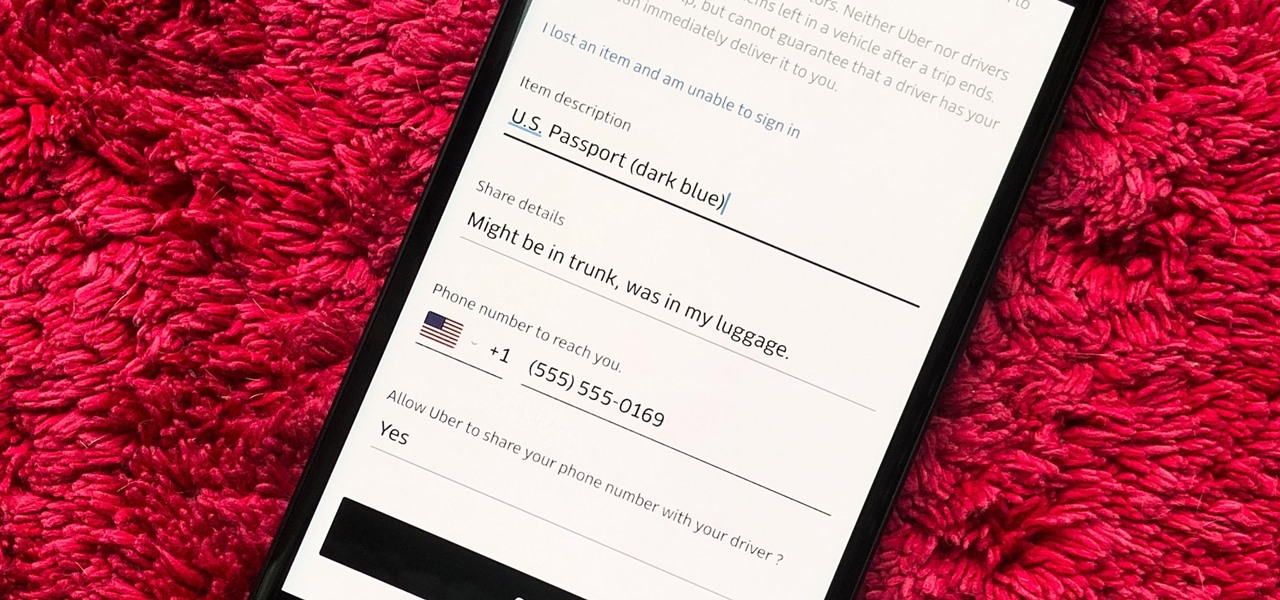
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Cited by many listed on this year's NR30 list as the most important event in the last 12 months, last year's release of ARKit catapulted Apple CEO Tim Cook to the top of Next Reality's rankings. This week, we dug deeper by explaining why he's at the top of the list of NR30 Mobile AR leaders.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Samsung's big reveal of the Galaxy S9 and S9+ at Mobile World Congress revolved around its "reimagined" camera and augmented reality capabilities.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

The LG V30 has solid battery life. With its QHD P-OLED screen and 4 GB RAM, it's able to maintain all-day performance with average use. Heavier users might find that its 3,300 mAh battery isn't quite enough for a full day of work, though, but with a few software tweaks, you can squeeze out even more battery life.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.