You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:
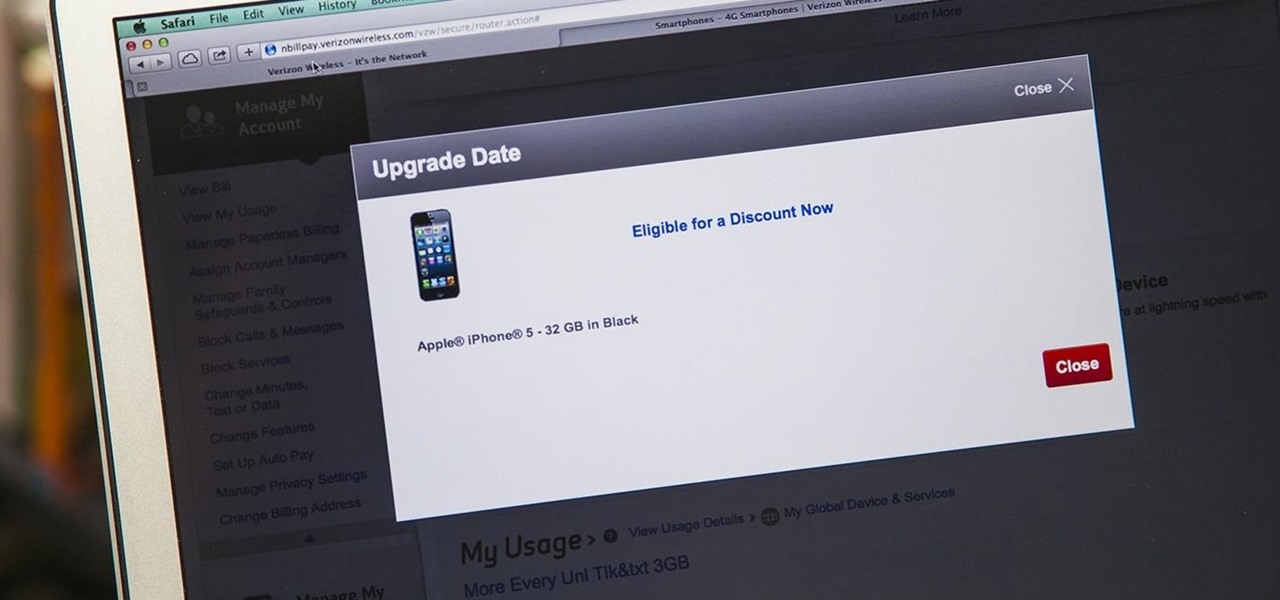
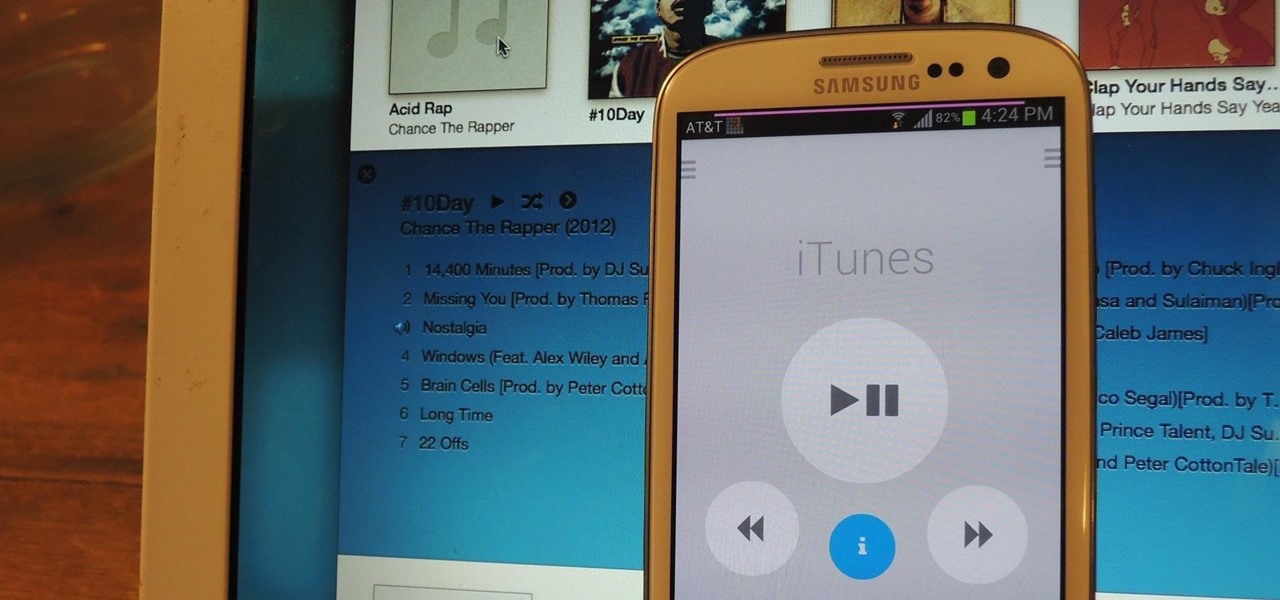
iPhone 6 pre-orders begin on September 12th, with the devices set for sale on the 19th. If you're ready to pick one up—no matter if you're a loyal iPhone user or an Android user about to make the switch—now is the time to check your upgrade eligibility.
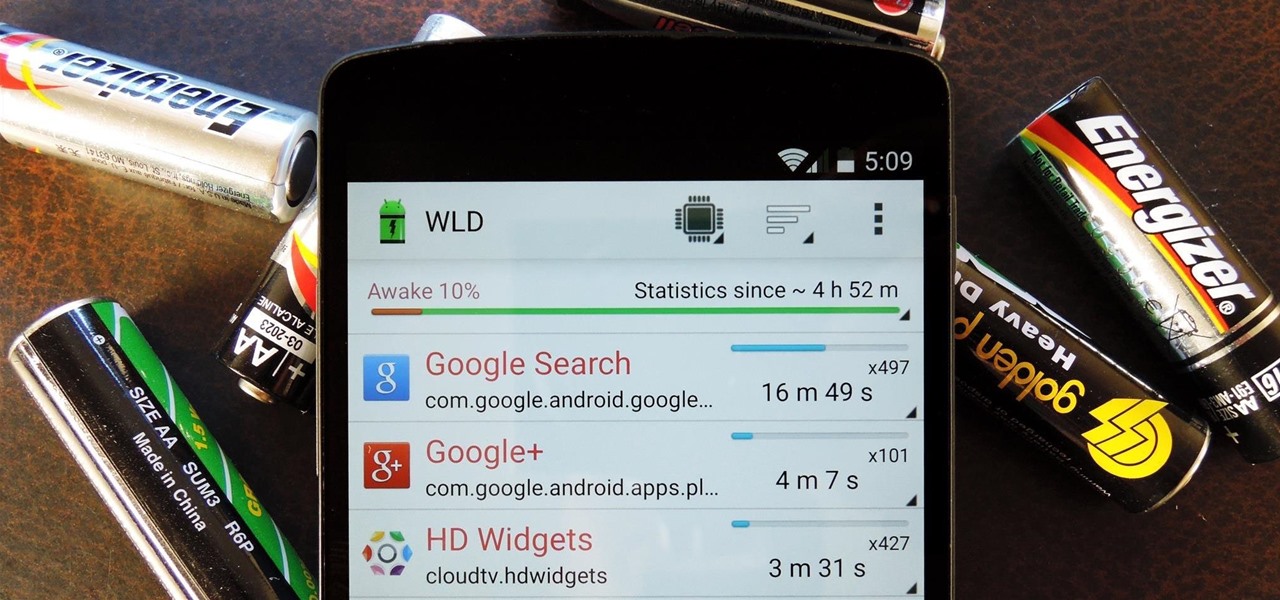
Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

As someone who's dependent on glasses to see on an everyday basis, losing or misplacing them is obviously a bad thing. I can't even see clearly enough to find the glasses that I just lost, so I'm pretty much blind now.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

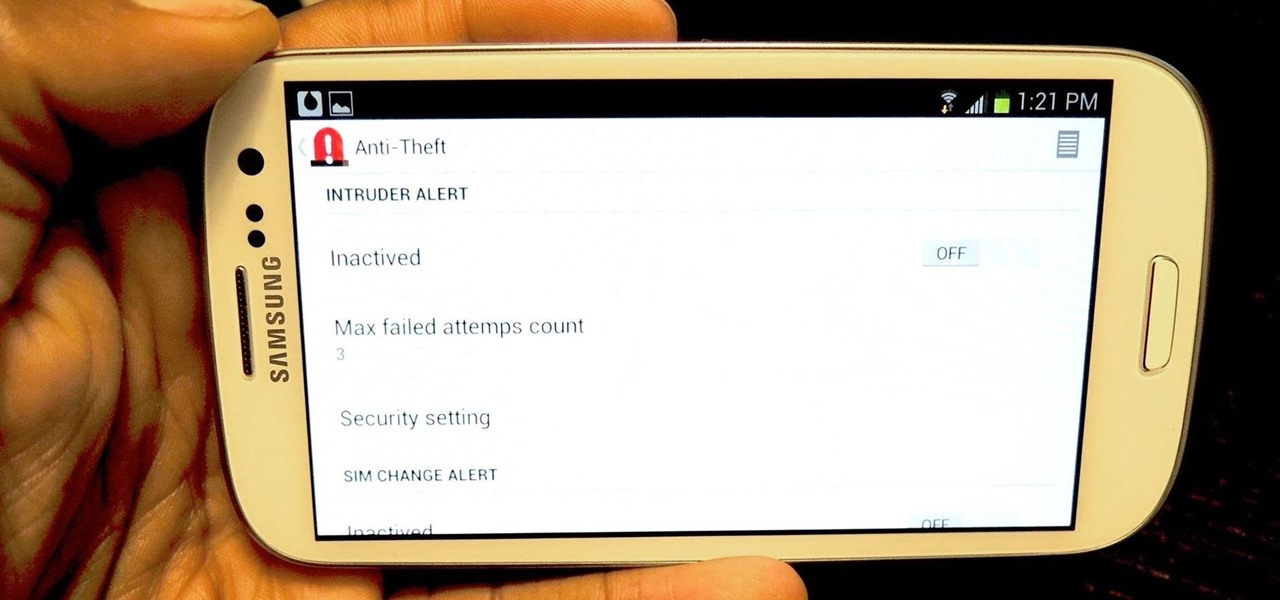
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

Finding love is tough. Movies like The Notebook and Twilight have ruined the expectations of love and relationships for us guys. Some women's ideal love situation is being kissed by a glittery sparkling vampire. "I know we only met a few seconds ago, but I'm deeply in love with you."

Whether you're heading to a frat party, out for Halloween or just looking for a cool way to tie your towel at the beach - this video is here to help! Learn how to tie a toga, the ancient Greek way of dressing, and be ready for whatever costume situation may arise with a quick and cheap outfit!

In this video clip series, our expert will demonstrate several first aid techniques that can easily be done to treat minor injuries and basic situations that you might find yourself afflicted with. Bee sting treatment, abrasion care, blister care and more.

There’s a good chance that you’ll be alone in life one day, and no... I’m not talking about a couch-bound, dateless loser with a pocket pussy and a bag of potato chips. I’m talking about alone. In the wilderness. Hungry. Cold. Lost. You can’t stay in one place too long, so it would be nice to have something to carry your belongings in. Maybe it’s post-apocalyptic land where you’re the sole survivor, and all the backpacks and rucksacks in the world are but mere ash. Either way, knowing this si...

In this video series, let comedian Les McGehee school you in the art of humor as he teaches you the importance of practicing improv comedy with kids and starting your kids with improv young. Learn different improvisational techniques and games, how to apply those techniques to different situations, and how to use the art of improv comedy to make people laugh.

For any comedian, aspiring or professional, this video series is a must see. Actually for anyone at all, the value of these clips to help with social interaction is also astounding. There is more to improv than just games. We improvise on a daily basis in every situation. Improv is only a reaction to something.

In this online video self-defense course you’ll learn the basic moves of Kung Fu for kids. Sifu Dan Schmidt demonstrates various stances, blocks, punches, kicks and jumps that will give children a means of defending themselves if they’re ever in a bad situation. These lessons are perfect for helping kids build strength, endurance, motivation, self-discipline and concentration, so watch these free video clips and start training today.

In this series of informative videos, you will learn how to find flea market finds to use in home decoration. Flea market events are often crowded with people and crafts, so knowing what to look for is imperative. In the video titled “About Flea Markets,” you will learn more about the general idea and practices included in the flea market experience. Learn how to and whether bartering is appropriate in different flea market situations. Get tips on dealing with vendors and finding the right pr...

In this series of informative videos, you will learn how to find flea market finds to use in home decoration. Flea market events are often crowded with people and crafts, so knowing what to look for is imperative. In the video titled “About Flea Markets,” you will learn more about the general idea and practices included in the flea market experience. Learn how to and whether bartering is appropriate in different flea market situations. Get tips on dealing with vendors and finding the right pr...

In this video series, let comedian Les McGehee school you in the art of humor as he teaches you how to do improv comedy. Learn different improvisational techniques and games, how to apply those techniques to different situations, and how to use the art of improv comedy to make people laugh.

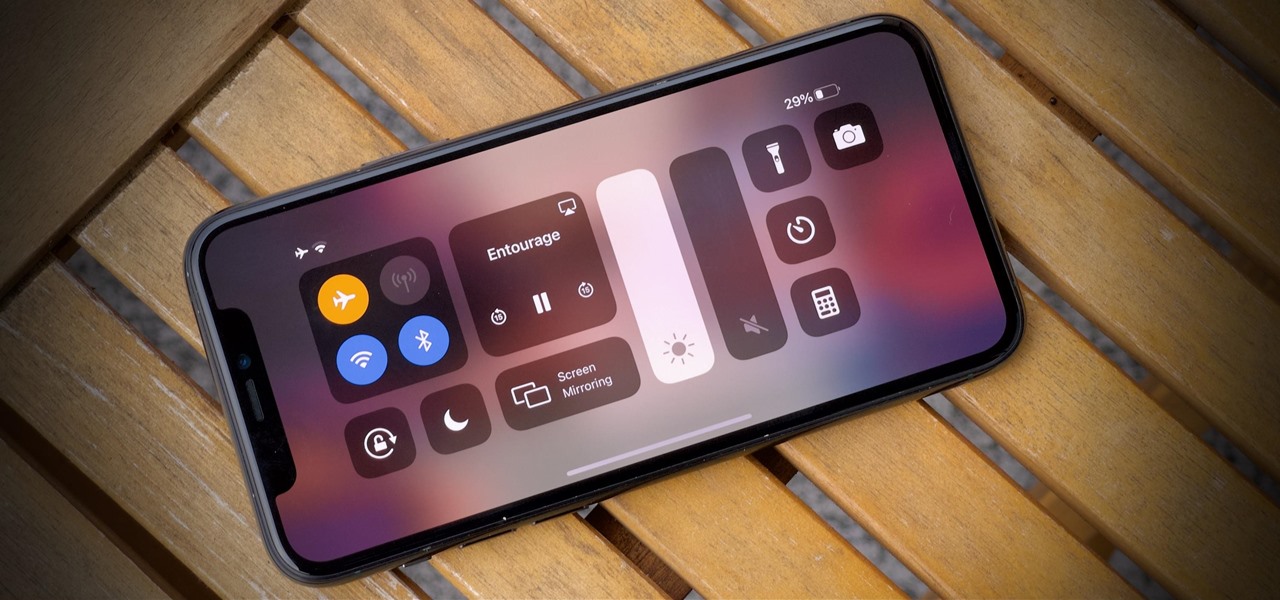
You're in the middle of the fight for your life in your favorite iPhone game when all of a sudden, that critical move you tried to make activates Control Center inadvertently, throwing you completely off track. Instead of fuming, do something about it — block Control Center when you're in apps.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.