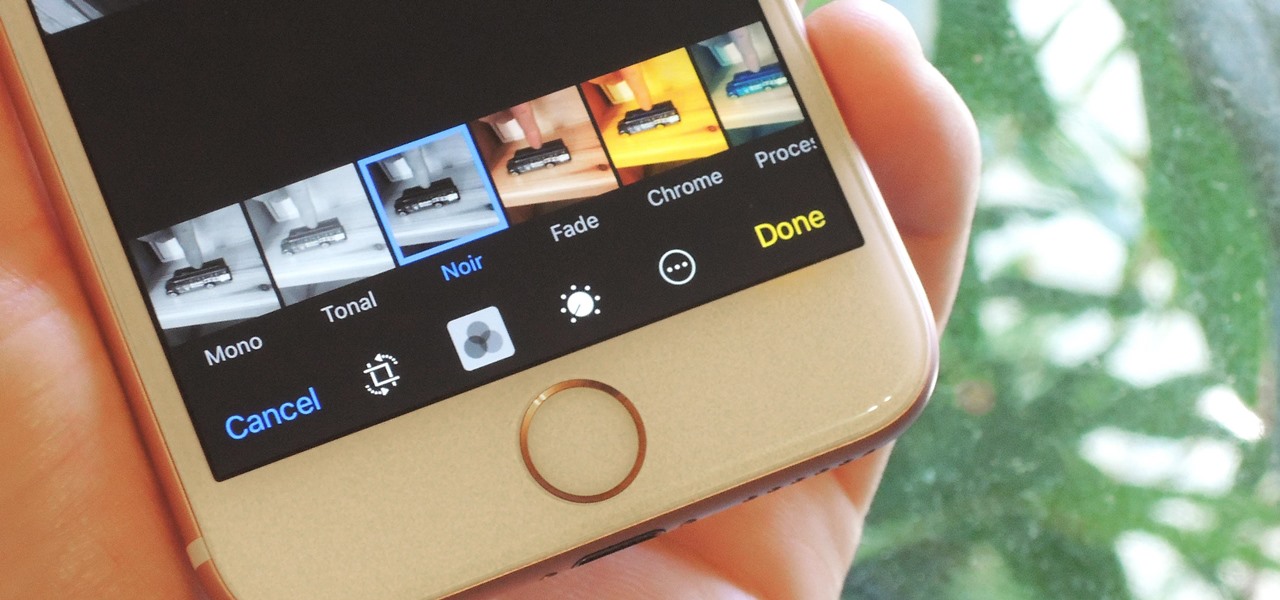
A new telemedicine application for the Microsoft HoloLens is promising paramedics and EMTs a new tool for diagnosis and treatment of patients in the field.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.
As expected, Magic Leap closed a Series D round of equity funding, raising $502 million from new and existing investors. Less expected, however, were a fresh set of rumors that the company's first devices could ship within six months.
If you're new to Plex, there are a couple of things you should know up front. First is how to use it — simply install the Plex server app on your computer and point it to your media library, which you can then access anywhere using the Plex app for iOS or Android. All of this is free.

In an early morning blog, Jimmy Alamparambil of the Unity team announced a major new update to their ARKit plugin. Developers now can use Unity and ARKit to create AR experiences and test directly from Unity's editor, without deploying to the device.

Earnings calls can be a mixed bag. If things are business as usual, the meetings can be, well, boring.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

In Indianapolis, two-year-old Kenley Ratliff has passed away from what is suspected to be Rocky Mountain spotted fever (RMSF), a tick-borne illness. The young girl fell ill with a fever, and just a week later, passed away. Now her family and doctors are looking into the cause of her death and warning others to check themselves for ticks this summer.

Sepsis is not only a gross sounding word but also a deceptively dangerous and fatal infection. Which is why more than 40 hospitals nationwide are coming together to a new collaboration to help reduce sepsis mortality, named Improving Pediatric Sepsis Outcomes (IPSO).

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

Merge VR, a company mostly known for its virtual reality experiences, is moving into and creating an augmented reality experience that combines an iPhone or Android smartphone, a set of goggles to put your phone in, and a box about the size of a Rubik's Cube which looks more akin to the Lament Configuration seen in the Hellraiser film series. When used in concert with the smartphone and goggles, the toy cube, called Holo Cube, becomes one of many AR experiences.

I bet you've never put much thought into the water and ice dispensers that comes preinstalled in a lot of modern refrigerators and freezers. For chilled water or perfectly formed ice cubes, all you need to do is push the button and wait, right?

The iPhone 6s models introduced Live Photos in iOS 9, a cool new camera feature that takes a GIF-esque moving image every time you snap a pic, but the cool factor pretty much stopped right there. You couldn't take them on older iOS devices, share them with non-iOS users, or even edit them.

The Weather Channel, by virtue of its name, has always been tasked with the difficult problem of making the weather interesting. As Mashable notes, they've turned to augmented reality for a solution and can now render a 3D storm in their studio, as well as help us understand how bad a storm might be with 3D forecasts.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Developers across the U.S. and Canada have started getting their augmented reality headset packages from Microsoft, and so far, everyone's raving about one gaming experience that shatters all doubts of just what the HoloLens can do... RoboRaid.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

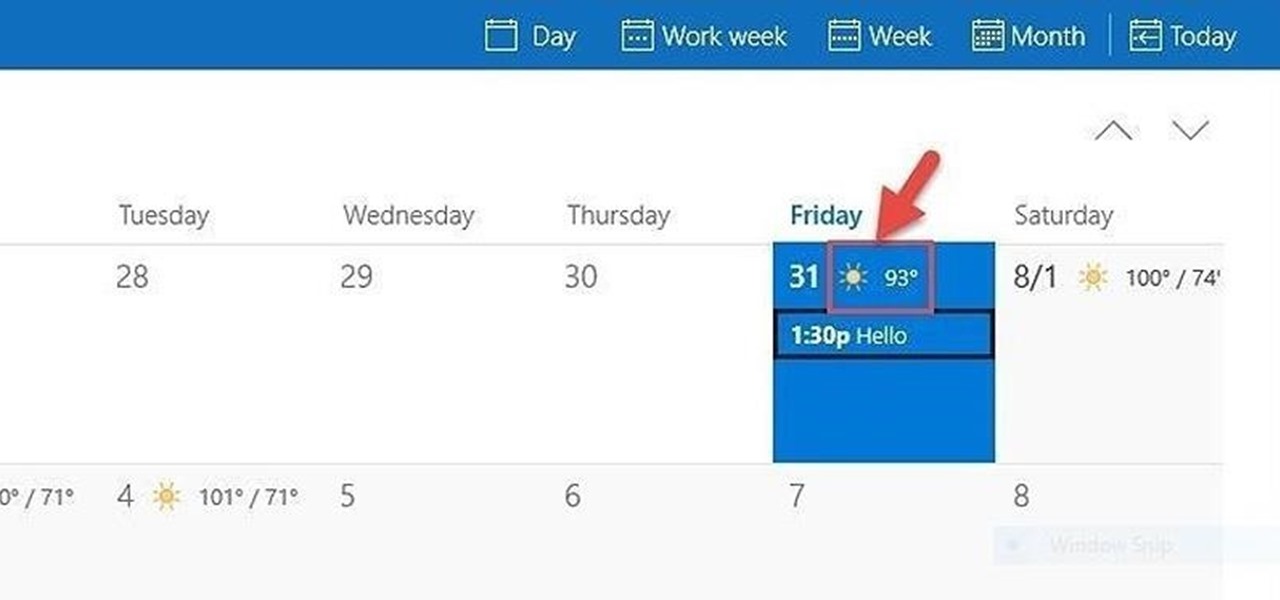
The Calendar app that ships with Windows 10 has a nice little feature that will help make your days more productive by showing the current five-day weather forecast.

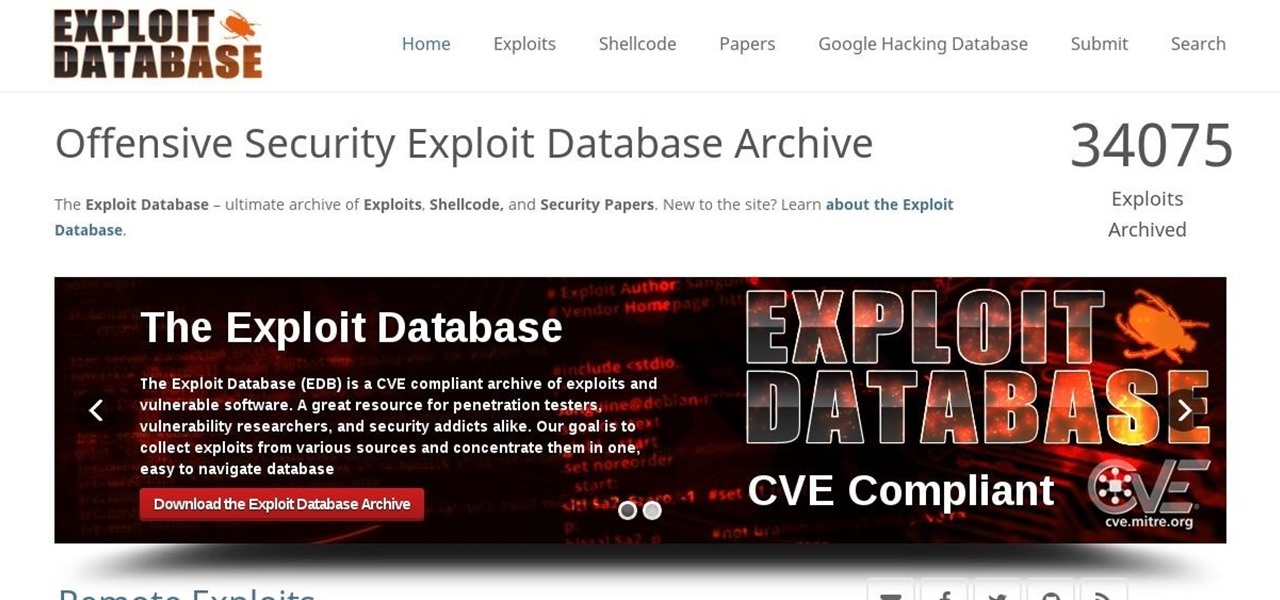
Hello everyone! Hope everyone having good day!! I wanted to share an easy way to locate an appropriate exploit from the EDB, get it compiled, and run it all from inside the terminal.

Nearly nine months after the release of the iPhone 6 and 6 Plus, we finally have some solid information on the "S" model of Apple's flagship device, slated for release this fall. Coming straight from Apple analyst Ming-Chi Kuo of KGI Securities (via AppleInsider), quite a few upgrades will be included in the next iPhone model.

Bacon isn't hard to cook on the stovetop, but every cook who's been hit by splattering fat knows it's not the most pleasant kitchen task to tackle. If you're cooking bacon for a lot of people, you can avoid this by cooking it in the oven on a roasting rack, DIY or otherwise.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

Bearded women are typically more freaky than scary—yet when it comes to American Horror Story, nothing is as it seems.

While the majority of photos taken on phones are used for personal reasons, mediums like Instagram and Flickr offer a means to show them off to the world. But those pictures of your brunch or beach day can actually go beyond that to make you some money.

Although we are months away from the next generation iPad, a model of what seems to be the iPad Air 2 has just been released on the interwebs for your lovely eyes to view.

Peaches—to peel, or not to peel? For some, it's not a question at all. The fuzz on the outside of the fruit is enough to turn some off to it completely, even though the peel doesn't have a bitter taste. Others may not mind the peel, but don't want it in their pie or cobbler. Regardless, getting rid of it is a gigantic pain.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

Antique car collecting and restoration is a very popular hobby practiced by many around the world. A quick drive through my town turns up with a handful of classic cars parked in their respective driveways, some in pristine condition, and others not-so-much. While some people end up eventually fixing up their classics, many also do not. Some cars end up rotting away, left to be either salvaged or sold off in pieces—mostly due to time consumption and excessive costs.

There is no such thing as too much space when it comes to our smartphones. Space is the great equalizer of all things. No matter how many awesome features a device has, the amount of storage space available will always be a determining factor. Be it music, apps or photos, it's easy to fill up your phone's memory fast.

This tutorial is for those who are new to Windows 8.

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.

How to adjust a sliding door. Sliding doors are great when they are sliding but can be a real pain in the bum when they don't. Today's video will concentrate on adjusting the wheels to help alleviate some of these annoying issues. It doesn't matter if it's a robe sliding door, a closet sliding door, a glass sliding door or a patio sliding door, the principle is still the same. Obviously there can be other factors like the sliding door track or the sliding door wheels being in a state of disre...

Hello! This post will be about the special care your dwarf rabbit needs during hot weather. There are many ways to keep your pet happy. Step 1: Choose the Environment

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

One of the best ways to reduce stress is to see a therapist. Interviewing a therapist can be tricky, but picking the right therapist for you is crucial. Get advice on reducing and managing stress in this stress management how-to video.

In this automotive repair video you will learn how to replace the front and rear brakes on a 1998 Dodge Dakota 4x4 truck. Brakes are a crucial safety element that shouldn't be neglected so if you have bad brakes, watch this video and learn how to replace them.