The new HTC One (M8) is a large phone, no doubt about it. Still, with those BoomSound speakers, 5-inch display, and 2600mAh battery, it's a wonder they managed to cram everything in that gorgeous, unibody metal shell. By that logic, it makes sense that the M8 makes the switch from a micro-SIM card to nano-SIM to save as much space as possible.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

A mustachioed Italian plumber collects coins and battles bullets, plants, fish, mushrooms, and turtles in strange environments to save a princess held captive by a crazy, spiked-shell, bipedal tortoise.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Walking the streets at night can be uncomfortably dangerous. In 2010, there were 32,885 motor vehicle deaths in the United States. Of those, roughly 13%, or 4,280, were pedestrians. Two-thirds of those pedestrian deaths occurred at nighttime. Along with darkness, drivers also have to deal with rain and other harsh weather conditions. Combined, all of these factors can be very dangerous for anyone taking a walk at night. As it happens, pedestrian deaths are on the rise since 2009.

For some people, a costume is just a necessary prerequisite to get into Halloween parties. If you're female and you're going the sexy route, it's not too hard to find something to wear, but transforming yourself into something terrifying takes a little more work.

Learn how you can apply red, white and blue drag queen style eye makeup with this tutorial. You will need

This how-to video is about how to reduce belly fat with the help of a better diet.

Learn how to clean your auto engine with these great tips. • Apply spray wax to fenders to prevent spotting on the paint, from engine degreaser. • An alternator is a crucial electrical device which must be protected from water and other chemicals. as a precaution, cover it with a plastic bag and the distributor cap if it is visible. • Spray WD40 on any exposed wires to prevent water or chemicals from penetrating. • Wet underneath the hood; wet the engine; use low pressure water on the engine ...

Teaching preschoolers to identify objects is crucial in developing language skills. Learn how Montessori teaches language with easy activities in this free educational video series about Montessori methods.

In this video series, professional guitar player and technician Bill MacPherson shows how to adjust the intonation of a guitar. With his expertise he explains what guitar intonation is, what the different factors that affect guitar intonation are, different tuning methods, different guitar bridges, and finally how to adjust and setup the intonation of the guitar string by string. Stop fighting your guitar when you play and learn how to make your guitar work for you?

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Sharing your personal information can come up for any number of reasons: you may want to get in touch with a colleague after work or you've been involved in a car accident and need to stay in contact with the other driver. Unfortunately, giving out information can be the key for others to find your social media accounts, such as Instagram, whether you want it to happen or not.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

Super Monkeys are the major factor in winning Bloons Tower Defense 3. Any do you know the best way to get Super Monkeys? Cheat Engine, that's how. With this hack, you'll get tons of money!

Weight loss is a very important factor in society today and everyone is looking for new ways to make it easier to lose weight. Learn what to expect when receiving acupuncture therapy and how it can help with hormone balance from a Chinese medicine expert in these free video clips.

Weight loss is a very important factor in society today and everyone is looking for new ways to make it easier to lose weight. Learn what to expect when receiving acupuncture therapy and how it can help with weight loss from a Chinese medicine expert in these free video clips.

Creating drum beats is a crucial part of making a great song. Learn how to use Logic Pro 8 Ultrabeat drum machine feature to create and mix your recordings in this free music production tool tutorial from a professional audio engineer.

In this health care video series, our expert, Dr. Susan Jewell, will explain the various risk factors for developing breast cancer and explain breast cancer symptoms.

Baklava is a wonderful dish for any dinner party you might be having. It is not difficult to make and does not require many ingredients to taste fantastic. In this video series you will learn how to make baklava from scratch including how to put all the ingredients together, why you should do certain things such as cut off the edges before you cook it and how to make the syrup mix to put the flavor factor over the top. So have fun and enjoy your just desserts!

In these rock and mountain climbing instructional videos, learn how to set anchors for lead and top rope climbing. Having strong anchor points is crucial to a safe and successful climb. Get professional tips and techniques on using strong rope knots to secure your climb. Learn how to rock climb with natural anchors like trees and boulders. Discover how to join anchors together for a more stable climb in unstable conditions. Watch this series and use these tricks on your next rock climbing trip.

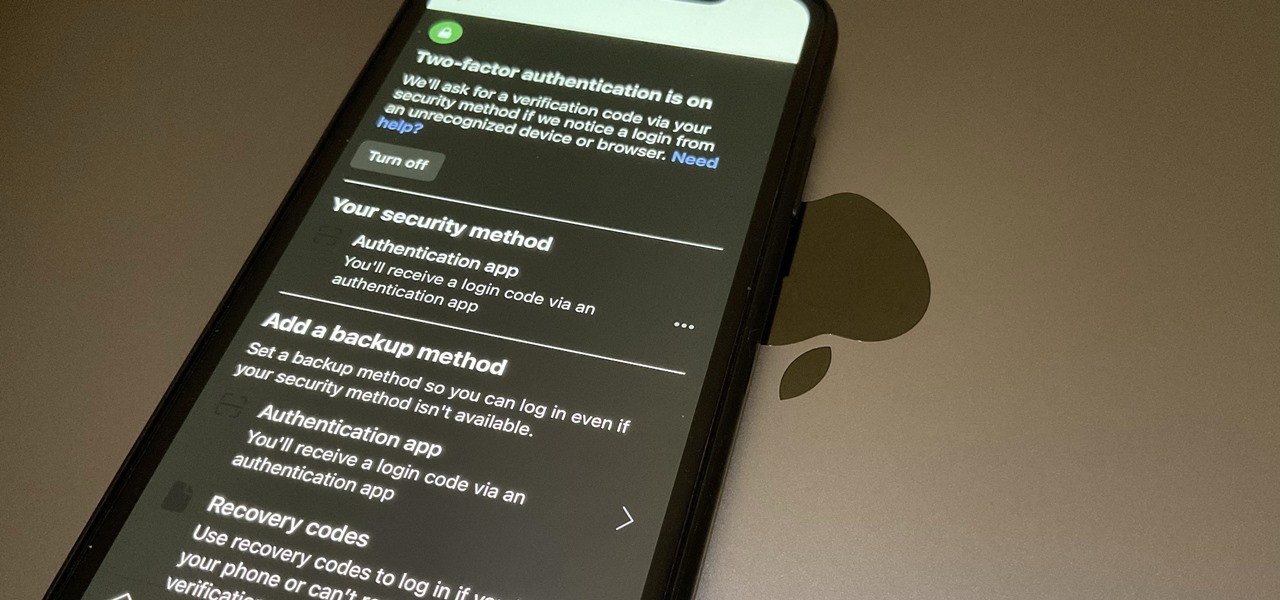
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Pushing music from your iPhone to your HomePod or HomePod mini by just moving the devices close to each other is certainly a great party trick. But if Handoff is too easily triggered, you might not think it's worth the wow factor. Thankfully, there's an easy way to stop your iPhone from sharing audio to your HomePod or HomePod mini (and vice versa) if you're finding it happens way too often.

Fake news was one of the main driving factors for Google News taking its current form. It offers verified sources to ensure more accuracy in your news feed to help control the spread of false information. Something you may not know, however, is that you can view your favorite Google News topics from your home screen with a single tap.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

No doubt, you've heard a lot about 5G lately. This might have you looking at your current 4G phone and lamenting your inability to connect to the faster network. But is 5G worth buying a new phone over, and should you buy one right now?

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

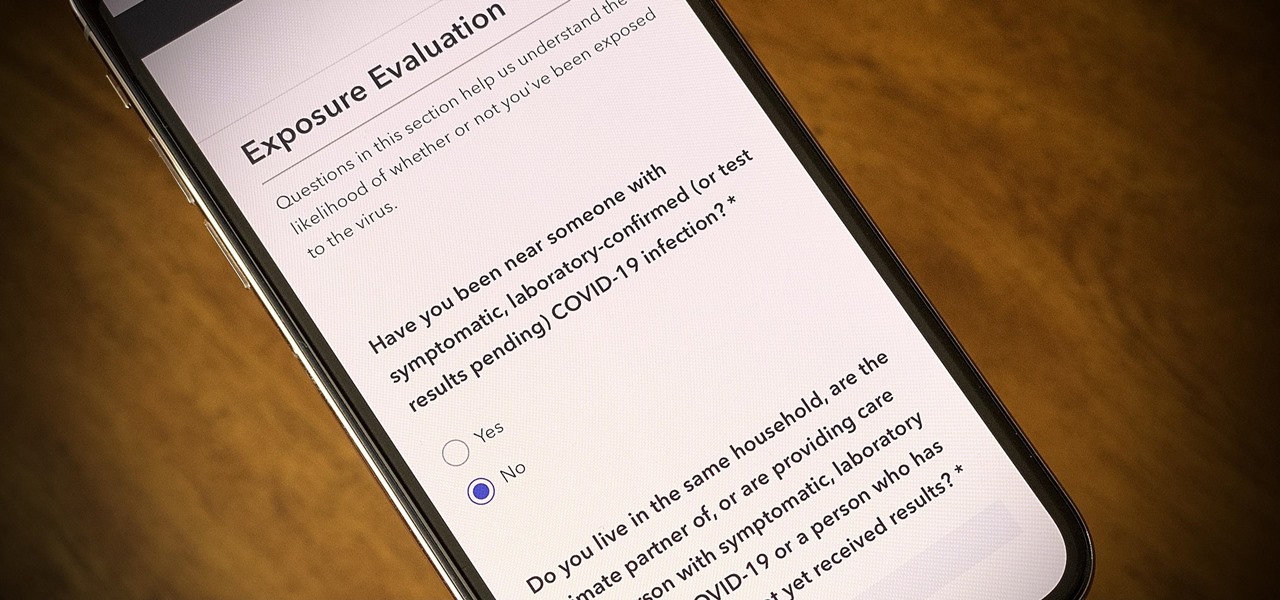
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Having already solved for functionality and form factor, Nreal appears poised to pull ahead of its consumer smartglasses competition as the third piece of the puzzle now falls into place.