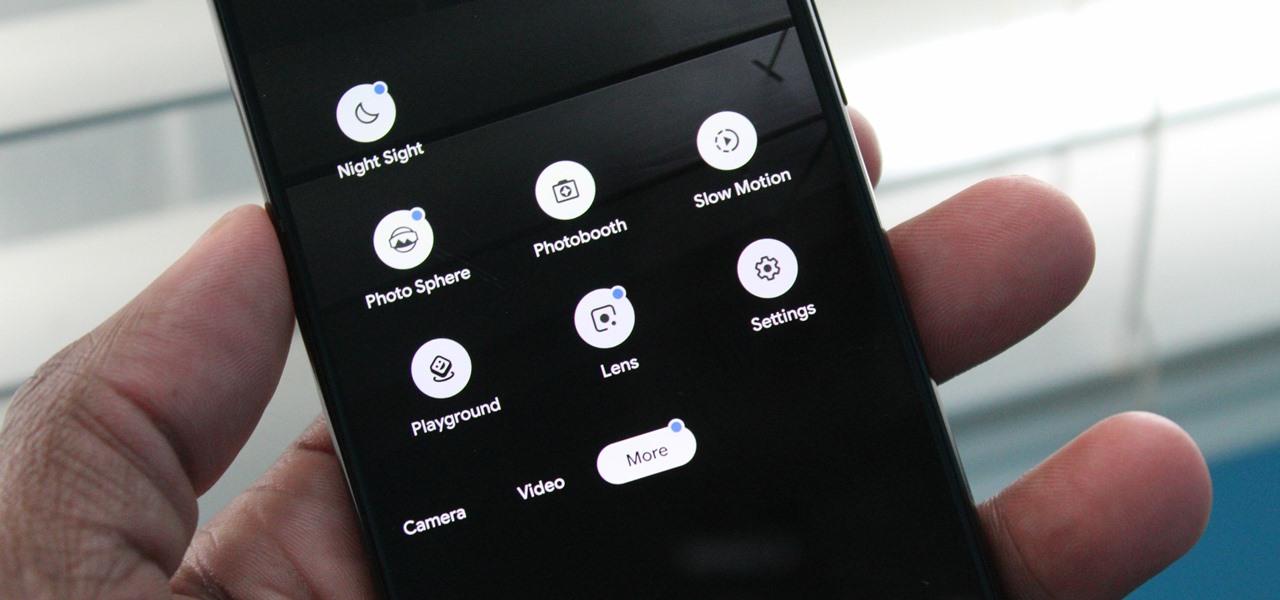
Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.
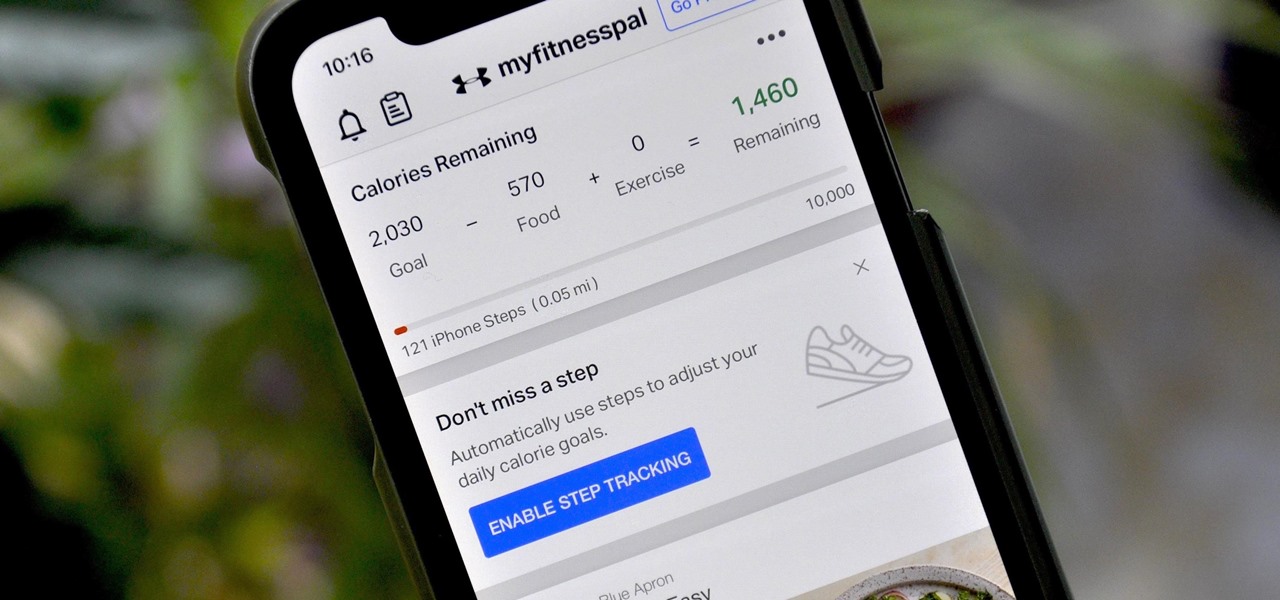
If you're new to MyFitnessPal, it might seem daunting. The app is way more than just a calorie counter, but that's because getting fit is just as much about changing your lifestyle as it is about watching what you eat. So don't let it overwhelm you — there are just a handful of tips you should know to hit the ground running.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

Crazy Taxi continues to be a favorite among gamers of all ages, from those who played the game in late-'90s arcades to those who discovered the game later on consoles. This weekend, Sega announced their mobile version of Crazy Taxi would now be available for free. What a time to be alive. So does the arcade classic still hold up in 2017? Let's find out.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Yes, I know it's autumn and the trees are losing their leaves, but the seasons do not decide when I can or cannot enjoy ice cream. No matter how warm or cold is is outside right now, I will remain completely fascinated by rolled ice cream. Yes, rolled.

It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

We've always loved a good summertime hot dog, placed lovingly in a soft simple bun with ample ketchup and mustard. But after eating hot dogs this way and this way alone for the majority of our lives, we grew tired of the same old thing.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

When a stuffy nose hits, it feels like breathing clearly and easily may never come again. Allergies, colds, and even changes in weather can leave our sinuses blocked, with medicine seeming like the only option. But don't break out the medication just yet — relieving the pressure of a stuffy nose, a stuffy head, and stuffy ears can be as easy as touching a pressure point.

At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say.

Video: . Optimize your Marketing with a Mobile Website

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

This walkthrough guide will cover the complete Overload DLC mission pack for the Mass Effect 2 action role-playing game on the Xbox 360. Overload became available for download in June 2010 on Xbox Live Arcade (XBLA), and features four different missions. Watch this series for all the gameplay action from Mahalo.

In the Xbox 360 game Darksiders, you're nearing the end of the game when you get to the Black Throne, which consists of three guardians and Straga. Proceed across the bridge as it constructs itself then enter the main room of the Black Throne. Here you will find Azrael who will tell you about Straga and how he gains great power from the Well of Souls. You will need to defeat the three Guardians that protect the Well of Souls and use their power to destroy the three statues that imprison Azrae...

This is the end of the Xbox 360 game Darksiders. It's the last level, the last quest, your last mission… the Destroyer. You'll need to summon Ruin to stand a chance against the Destroyer. Hold the Focus button to target lock onto the creature so you can keep in in view as you move around. The idea is for you to ride in close enough to the dragon and slash it with your Armageddon Blade. Watch out when you see the Destroyer's front claws glow red as this means he's coming to slash at you. Eithe...

Defeating the Ashland level of Darksiders on the Xbox 360 means getting past Tower A, Tower B, Tower C, Tower D, The Caverns, The Ash Field, Fracture Cannon, The Arena, Abyssal Gladiator, Leviathan's Drift, Stygian and lastly… the Soul Bridge. Before you lies an ash field. This ash is to thin for you to Dash in and makes moving around in it difficult. On top of that, a giant sand worm or Ash Titan, roams around freely. This massive creature will home in War as soon as he touches the ash groun...

In the Xbox 360 game Darksiders, you'll eventually have to play the Iron Canopy level, which consists of The Seesaw, Webbed Floor, Two Lifts 1 Bomb, Loom Wardens, Broodmother, Silitha and Return Silitha's Heart. War will be ambushed and captured as he enters the Iron Canopy. When he comes to, you'll find him hanging from a spider web. Tap the Action button to break free. Make your way around to the left to discover a Soul Chest in hidden nook behind your starting location. Now cross the webbe...

There's plenty of action on this level of the Xbox 360 game Darksiders. In the Hollows, there's Gas Mains, Tremor Gauntlet, Three Platform Room, Turntables, Pump Room, Griever, and Chronomancer. You enter way looks to have once been a train station. As you approach the Redemption lying on the ground you'll be ambushed by the Griever. Quickly pick up Redemption and begin to alternate between rapid fire shots and charge shots. You need to aim for the blue glowing belly of the monster. Dash arou...

Have you ever heard the phrase "Pinch your shoulders together as you lift the bar of the ground"? In this fitness how-to video, Mark Rippetoe describes the isometric function of the scapula in the deadlift. Follow along and learn how to work your shoulder muscles to improve deadlifts.

Dr. Stephen Langer introduces us to the thyroid gland and its important role in health.

This video is a demonstration of how to perform the Greek rhythm sirto with buzuki ensemble. This video is primarily a performance demonstration, however, everyone's role in the ensemble and how they relate to the rhythm is very clear.

This video is a demonstration of how to perform the Greek rhythm Haftalik with a buzuki ensemble. This video is primarily a performance demonstration, however, everyone's role in the ensemble and how they relate to the rhythm is very clear.