Over the past decade, touch screens have changed the way we interact with our electronic devices. Gone are the days of clicking and pecking at keyboards, with these gestures replaced by swipes, taps, and long-presses on most of our newer devices. From the early years spent swapping out vaccuum tubes and reading light indicators, human interaction with computers has been constantly evolving. Can Qeexo's FingerSense usher in the next era in manual input?

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

YouTube makes money hand over fist every year selling ad space to companies, but unless you're reaping those benefits, they can be pretty annoying. Luckily, there is a simple way to get rid them on your rooted HTC One with Xposed and YouTube AdAway.
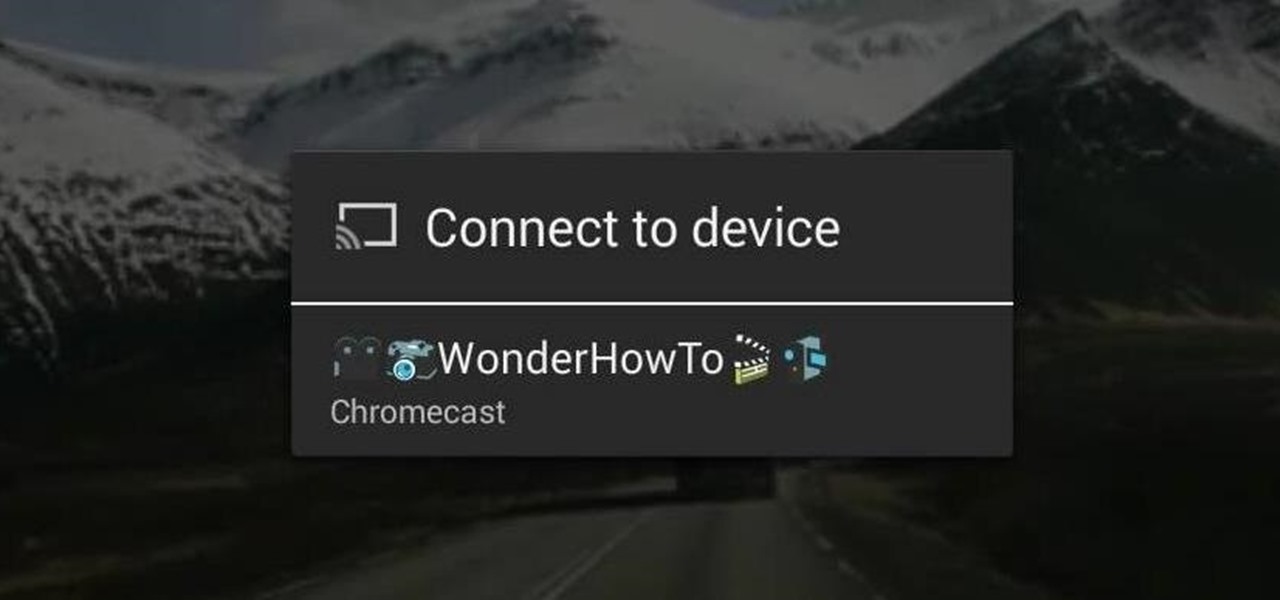
With the development kit fully open, the functionality of our Chromecasts seem to expand with each passing day. From a portable gaming system to your own personalized news station, our little gadgets have a lot going for them.

Much like the Pen Window feature in Air Command, Multi Window is extremely useful in its functionality, but bogged down by serious restrictions. While you can open and use two apps at the same time, you're limited to only a handful of apps that can utilize the feature, leaving all the other ones shit outta luck.
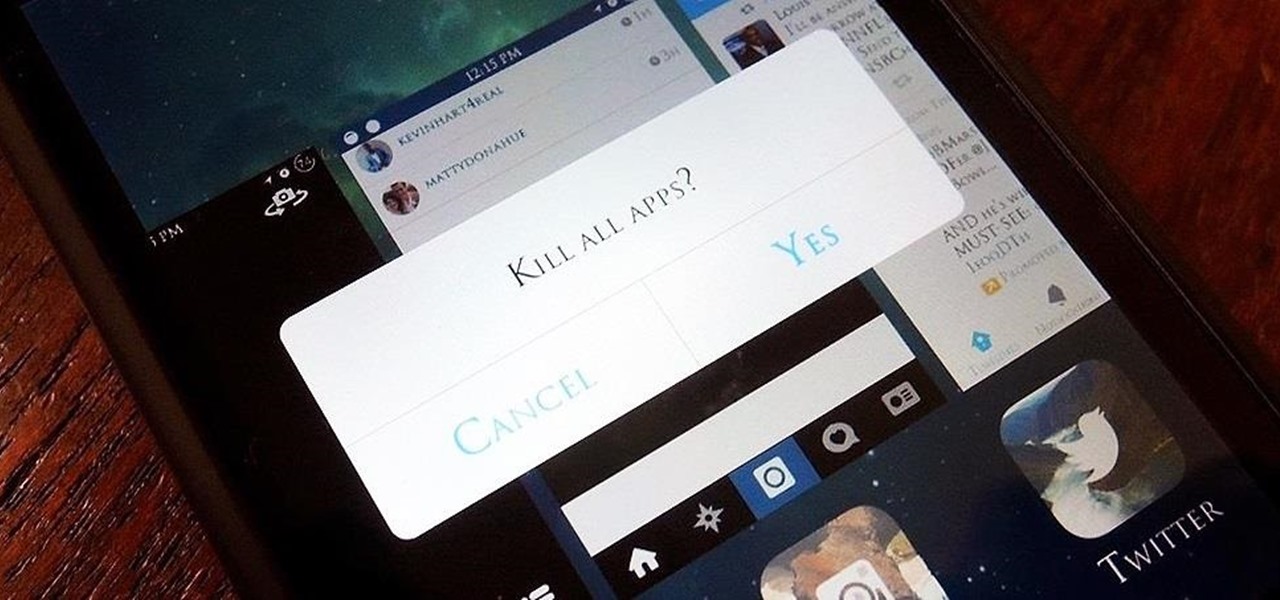
When lending our iPhone to our kids, siblings or friends, it's not uncommon to have it returned with what seems like a million apps open in the background. What's worse is being too lazy to close all those open apps, in turn having our battery drain much faster than normal.

Pinch-to-zoom has been a well-known feature in Google Maps, but one-finger zoom has always been a more practical way of navigating, especially for those of us using our phones with one hand.

Those of you using iOS 7 probably know by now that swiping down on an app's preview screen in the multitasking menu does absolutely nothing. Swiping up force closes the app, but down is useless—unless you're jailbroken.

Have you ever looked at your iPhone dock and wished you could place an extra, essential, or highly utilized app on there? Currently, with the basic settings you can only place four, but there's always that one that you wish could add to the mix.

How to make a wooden bench from reclaimed wood. Recycled wood projects, whether it's from pallet wood or old fence palings, the end result can be fantastic! In this video l am using reclaimed hardwood fence palings to build a rustic wooden bench seat. Rustic wood furniture has to be one of my favourites.

Having your phone ring loudly in a quiet environment could be potentially embarrassing for you, but also quite annoying for everyone else that didn't forget to put their smartphone on silent. Whether it's in class, at work during a meeting, at the library, or a movie screening—you can bet that someone's phone is going to ring loudly, pissing some people off. You don't really want to be that douchebag that interrupts a movie or the middle of a lecture with their annoying ringtone just because ...

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

Being lost sucks. There really is nothing worse than going to a huge event with a bunch of friends or family and then getting separated. Instead of partying with the bros, you get stuck next to this lame couple who keeps seriously making out every ten seconds. SMH.

Minesweeper is one of those games that everyone plays, but hardly anyone actually knows how to play. Most people just click random squares and see how far they can get.

Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.

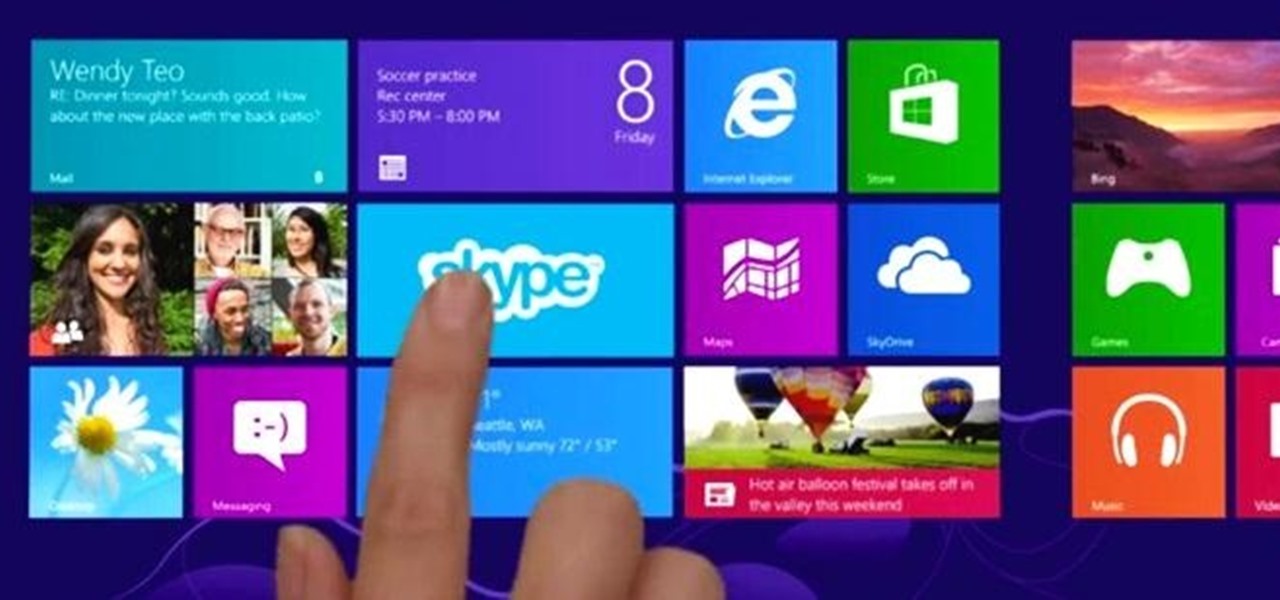
Windows 8 has been reimagined to take full advantage of touchscreen devices as the "future" of computing. A few years ago, touchscreen devices were super buggy and only played well with smartphones, but with the advent of the iPad and a ton of other tablets, touchscreen capabilities have spread to full-sized desktops and even televisions.

Before my time, people used to listen to music recorded on these things... I didn't really know what this thing was until my parents clarified and told me that they were called cassette tapes. These "cassette tapes" were utilized to store sound recordings on either side of the tape, which could usually hold between 30 to 45 minutes. I laughed at that information as I took out my iPhone 5 (roughly the same size), which can store roughly 40,000 minutes worth of music.

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

This tutorial for Sony Vegas 7 helps you utilize keyframes and create even better masterpieces!

Learn how to utilize this ankle bounce exercise as a part of your ladder training workout, geared at improving your athletic ability.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a Times Square billboard in Photoshop.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Traditionally, incorporating loops and grooves can translate into hours of hard work just to get the loop to fit your song's tempo and timing. Help is on the way from the Propellerhead's ReCycle which gives you full creative control over utilizing your looped material. Join electronic recording artist David Alexander as he shows you how ReCycle has revolutionized using sampled loops. In this episode, David shows us how to Chop Up A Complex Loop.

Analog reel-to-reel tape is some of the most in-demand recording equipment today. Learn how to use a reel-to-reel tape machine in this free video series that will allow you to utilize this piece of musical recording equipment.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.