Despite Android's flexibility in regards to customization, the options available in stock Android are pretty barebones. It is only with the help of third-party apps that we can entirely transform sections of the UI to our liking. And thanks to a new app, we can modify another part of the OS, the status bar.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.
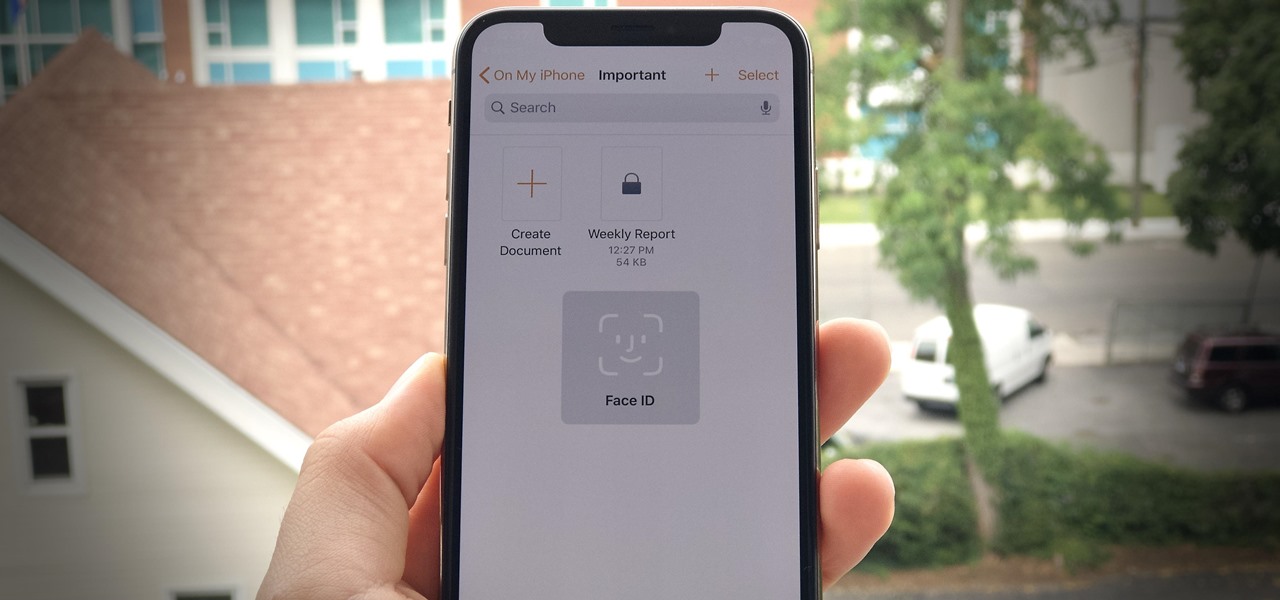
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Newer businesses, or older businesses looking for more traffic and sales, often offer enticing deals to attract customers. On Yelp, any business has the option to provide a deal to users, which is essentially a Groupon-like coupon. But how do you find these deals in the Yelp app for Android or iOS?

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

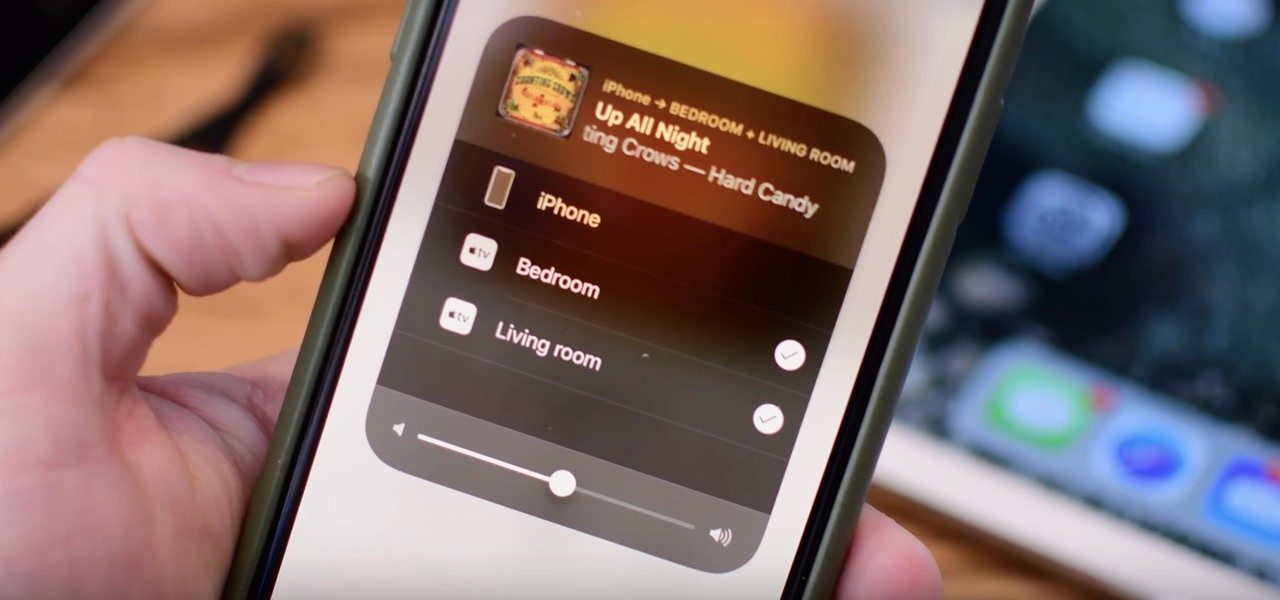
Back in June 2017, Apple promised us AirPlay 2, a simple way to connect and control multiple speakers together via an iPhone or other Apple device. While the feature was included in early iOS betas, by iOS 11's official release, AirPlay 2 was nowhere to be found. After all the numerous subsequent iOS 11 updates, it's finally here in iOS 11.4.

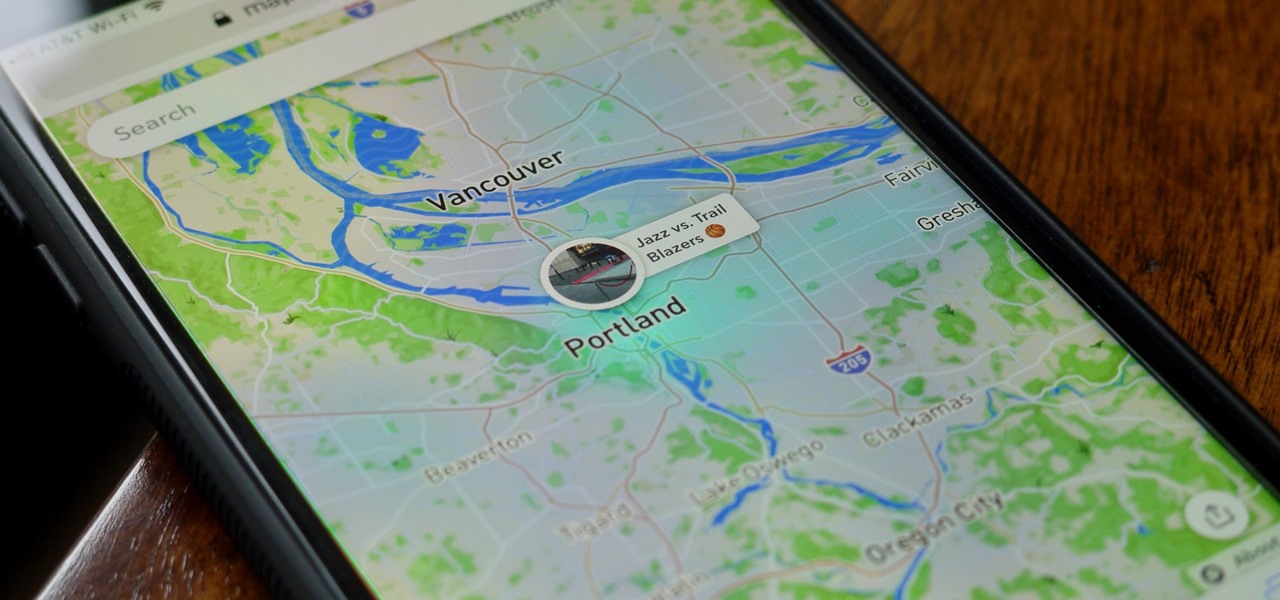
Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

You can't go scrub-a-dub in the tub - at least not comfortably so - if your shower faucet is leaking, or if your current tub valve is stuck and not letting any shower water come through. If your shower is broken beyond repair then your best plan of action is to take the whole thing out and reinstall your shower stall. We know this big - and potentially disasterous - procedure has been parodied many a time on popular TV sitcoms, but it's actually realizable if you're careful and follow the ste...

In this video from DavidWygant he teaches about using the ultimate opening line with women. He talks about approach anxiety and how you can talk to women about that very thing. He also talks about the 10 PM rule. Talk to the girls before 10 pm because by around 10 she will be so annoyed by being hit on all night. You can even approach her early in the night and discuss about maybe who she is meeting up with. Make a joke about your phones! Maybe you both receive text messages from your friends...

In this video the instructor shows how to check if your computer has a home group setup or setup one if required. Home group is Microsoft's new way of making networking easier with computers. They allow you to share documents, pictures, videos and all kinds of media between computers that are a part of a home group. Go to the start menu and go to Control Panel. In the Control Panel select the Network and Internet link. Now in the Network and Internet window select the Home group. In this page...

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

Purchase a silver XBox 360 faceplate from your local gaming retailer. You can also remove the faceplate currently on your XBox 360.

This video is about how to tattoo. Once you make your choice of design, the tattoo artist traces the image. Next, he places the image on carbon paper and traces the image again to create a reverse image. He cleans the persons skin then firmly presses on the blueprint. Now its time to construct the needles. One is for outlining and the other is for coloring. The finished needles go in a machine to be cleaned. He places the needle in a Coil. When an electric current runs through the coil, it ma...

pbj746 is here to teach you on how to create a glossy rainbow effect using Adobe Photoshop CS4. This can be easily done in a matter of minutes and you can try experimenting with other colors and effects to get variant number of sassy backgrounds.

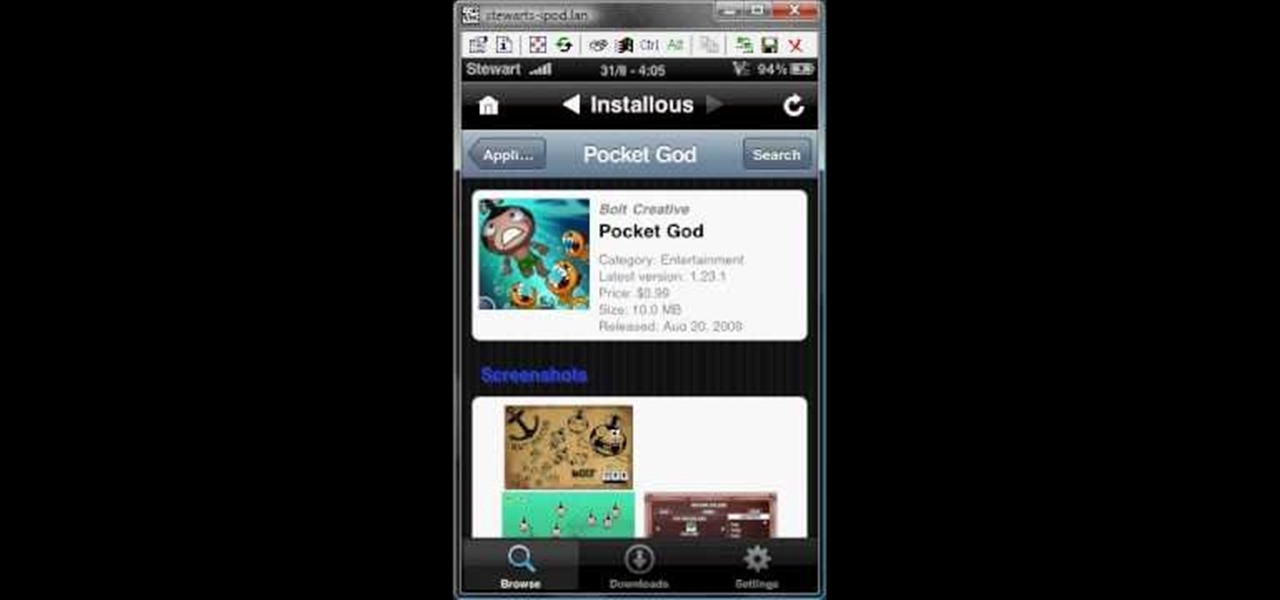
Use installous properly on your iPhone

At one time or another, every parent has thought about taking off the belt, but that's frowned upon in our current society, perhaps even illegal. Even using you hand could be too harsh for the child's sake, but there are ways to get your unruly tot under control. Toddlers are often headed for trouble, but you can steer them in the right direction without spanking.

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.

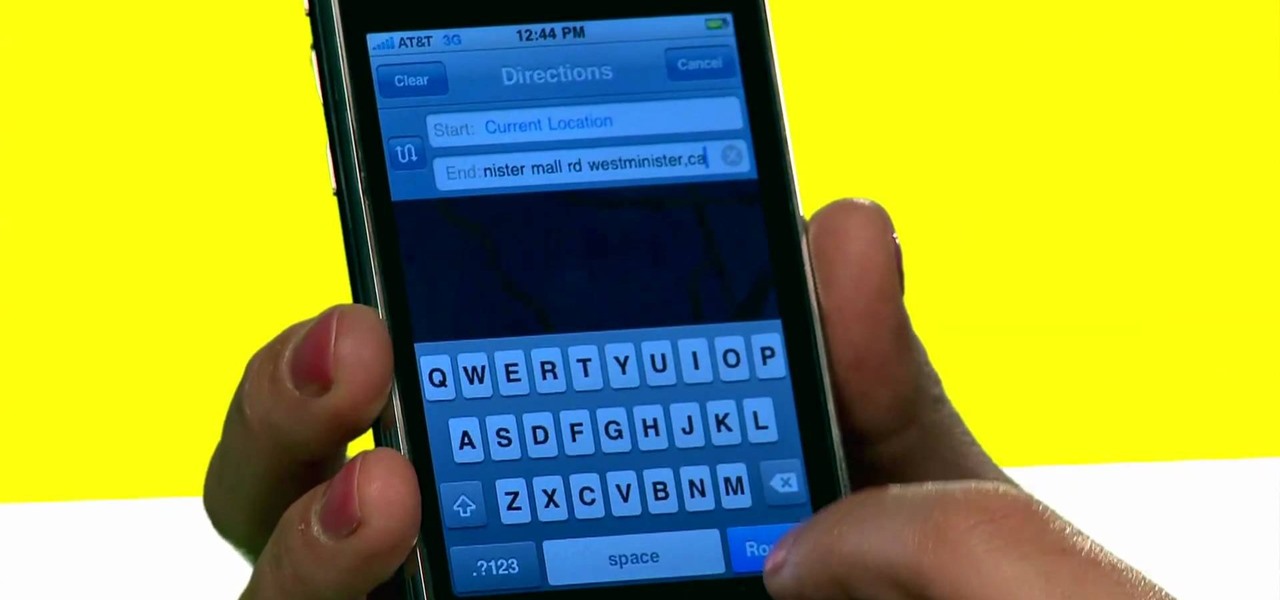
The iPhone is great. And so is Google Maps. And together, they define mobility. They go together perfectly. Like yin and yang. But how do you get the most out of Google Maps on the iPhone? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use Google Maps on your Apple iPhone for directions.

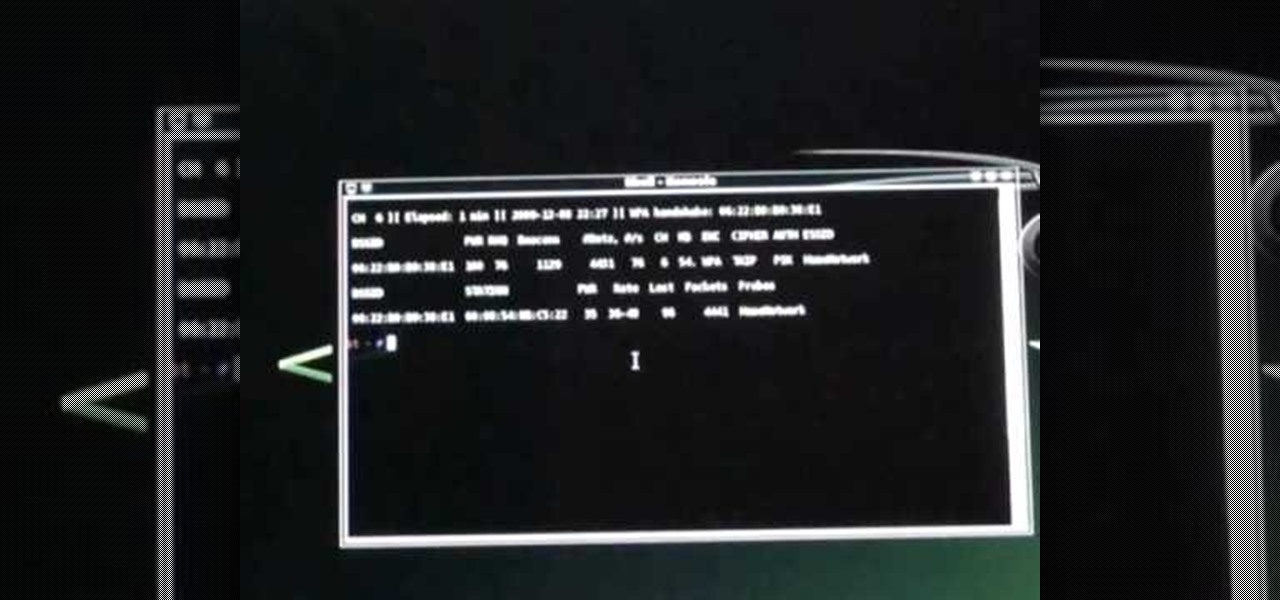
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

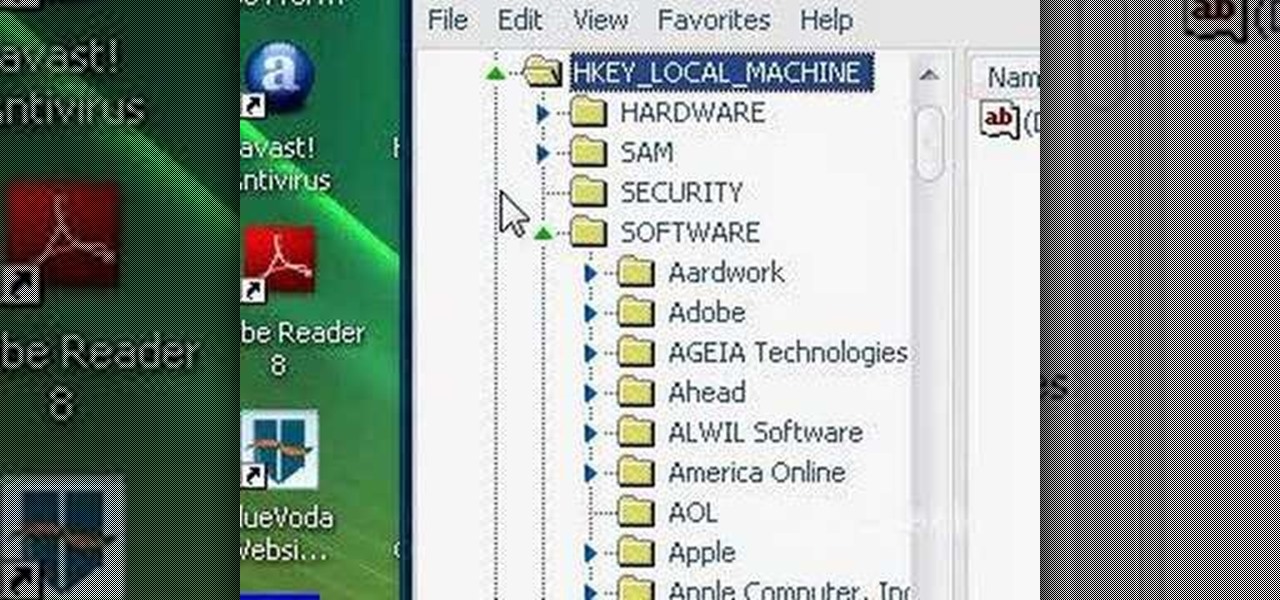
This how to video shows you how to change your computer registration on a computer. First, go to the start menu and select my computer. Right click it and choose properties. You will notice a registered to name. This is what we are going to change. First, go to start and select run. Type in Regedit and click okay. This program will open. Go to HKEY_LOCAL_MACHINE and Software. Scroll down and find Microsoft. From there, scroll down and find Windows NT. Open it and select Current Version. On th...

1. First of all you need to have a folder containing stock of various photos downloaded from the internet. The width of these images is ‘780’ and you need to resize them to ‘550’.

This is a video on how to weave in ends on kniting. First take two ends at a time, tie the new color and a half not around the current working color, and tie them. The thread the end onto the yarn needle, and go througha few of the yarn stitches. Next give it a little pull to make sure nothings coming loose. Go up to the next yarn ends, and do the same thing. What you have to make sure you do is weave the yarn through light colors. Also make sure the knots are secure, and are not going to com...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

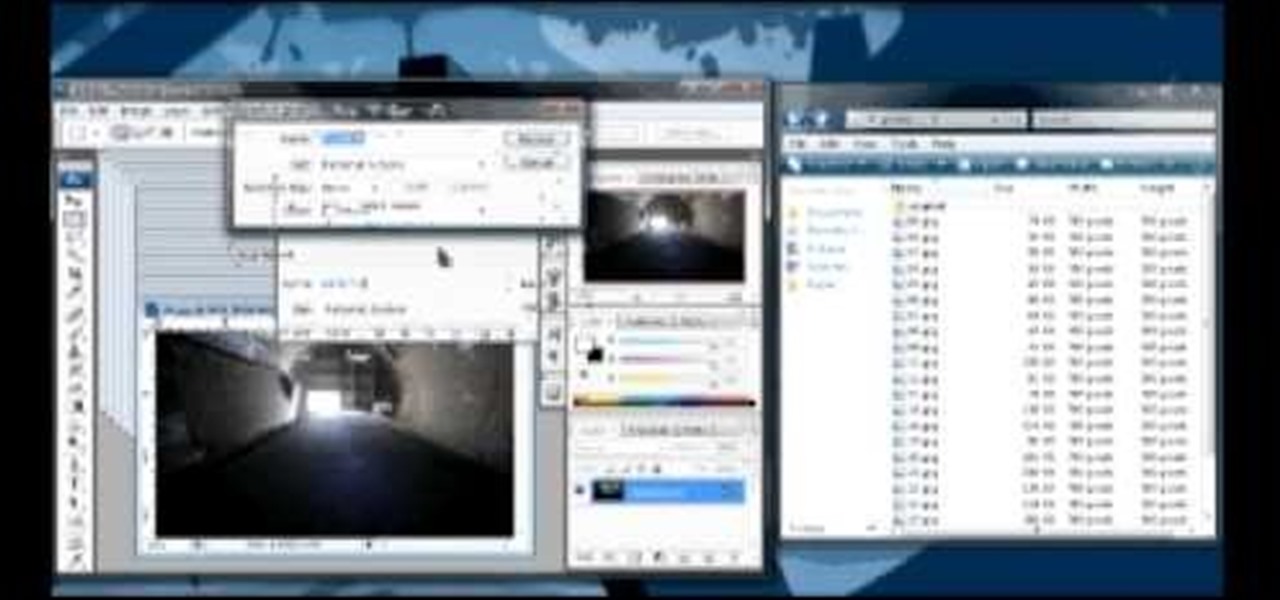
In this how to video, you will learn how to re-size any image in Photoshop to submit to Alamy. You will need the file to be 48 megabytes and uncompressed. First, open the image in Photoshop. At the bottom, you will see the current image's file size. Now go to image and image size. Increase the size by two or by five percent. Make sure re-sample image and constrain proportions are selected. Make sure bicubic smother is selected at the bottom of the window. At the top of this window, you will s...