In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

There are a lot of programs which allow opening archives. Alas, most of them are rather complicated to use. The process of the archive opening often takes much time. Hopefully, there are some programs which are simpler to use for regular users.

There are a lot of programs which allow opening archives. Alas, most of them are rather complicated to use. The process of opening of the archive often takes much time. Hopefully, there are some applications which are simpler to use for regular uers.

Many people are unhappy with their current height and want to get taller. There are some natural ways to increase your height, but remember, it takes time and a lot of patience and you won't grow 2 inches in a week.

If you've been struggling to get ChickHEN R2 installed and running on a PSP 3000, check out this video.
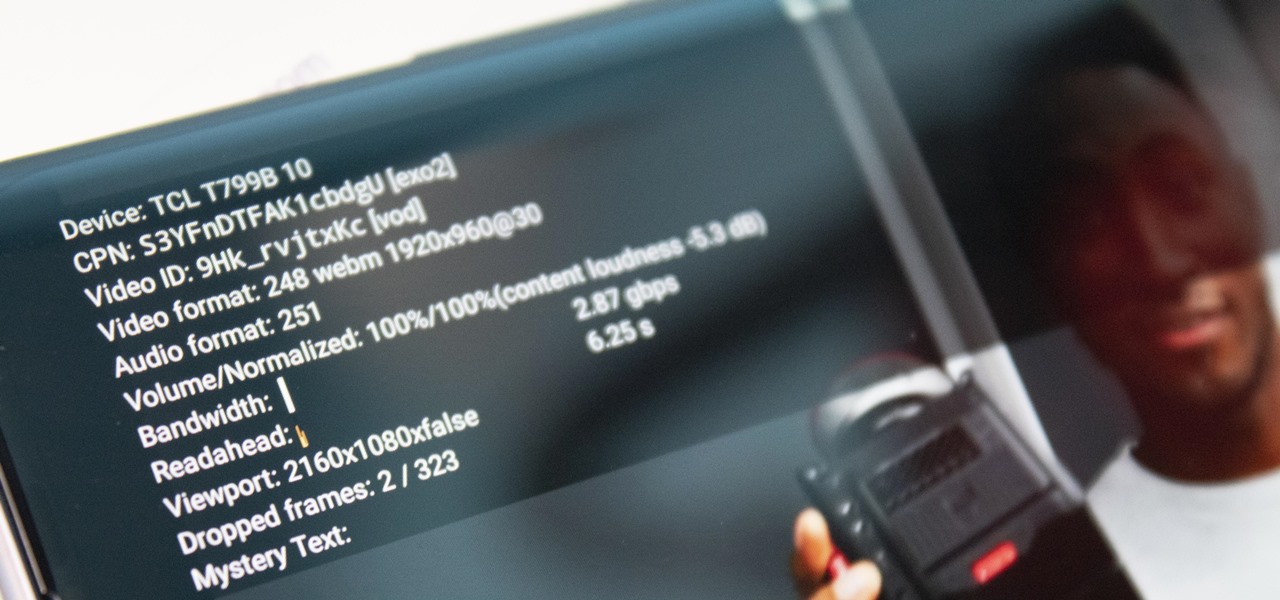
Most streaming platforms have seen a huge viewership increase in the past few months. As a result, wireless carriers and ISPs are struggling to provide the necessary bandwidth for everyone, resulting in some customers being limited to DVD quality. The same applies to YouTube, YouTube Music, and YouTube TV, but you can see the resolution being used and change it to something better.

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

In this tutorial, we learn how to resize thumbnails in Windows XP. First, close all the windows on your computer, then go to your start menu. Next, type in "regedit" under "run" and then click "enter". Now you will see a registry editor, find your current user path when you get to this page. Now, go under the software folder, then the Microsoft folder, and then the Windows folder. Next, go under "explorer" and create a new "DWORD" value called "thumbnailsize" and set a value between 32-256. A...

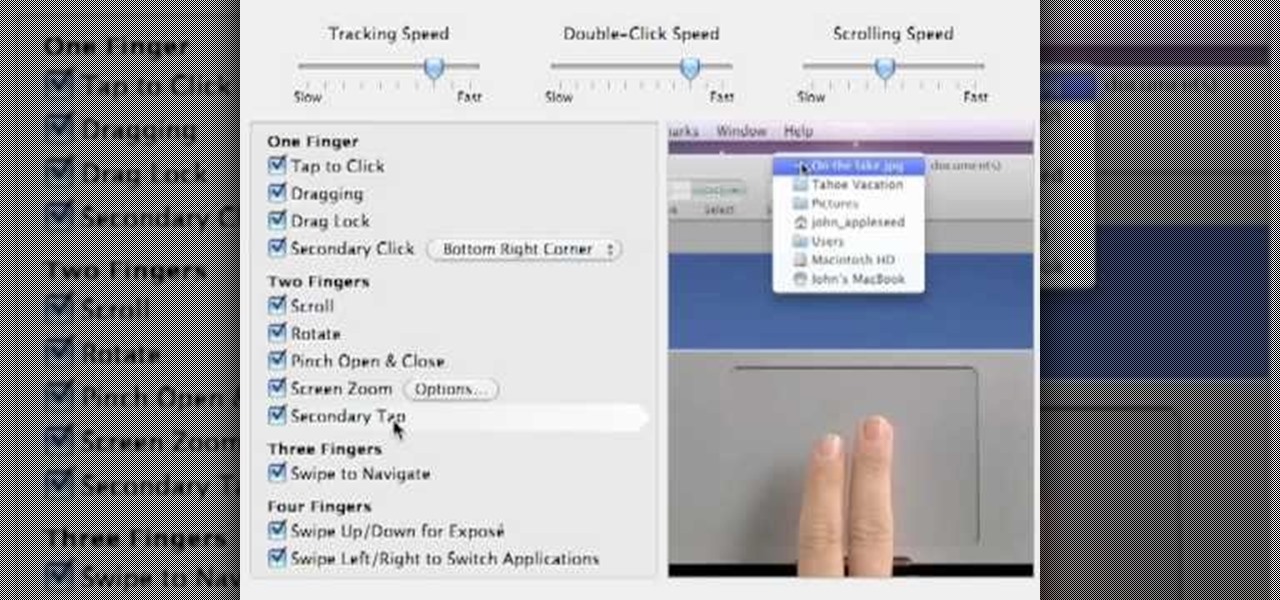
While the Macbook Pro track pad is a dream to use, it may not be immediately apparent on how to access the secondary, or "right click" menu. This video gives you a visual demonstration on how to right click using the two finger tap method. Note, it is important you check your System Preferences > Track pad preference pane to ensure secondary tap is the selected option. You can access the System Preferences by clicking on the Apple in the very top left hand corner of your screen and selecting ...

One of the basics of electronics is knowing how an electrical current works. For this video, you will need a 1.2V battery, a lightbulb, and 2 copper wires. First, take the wires and attach one end of each wire to opposite sides of the battery. Have a friend hold the wires there, or tape the wires down. Then, take the unattached ends of the wires. Take one wire and touch it to the upper part of the base of the lightbulb. Take the other wire, and touch it to the bottom. The lightbulb should now...

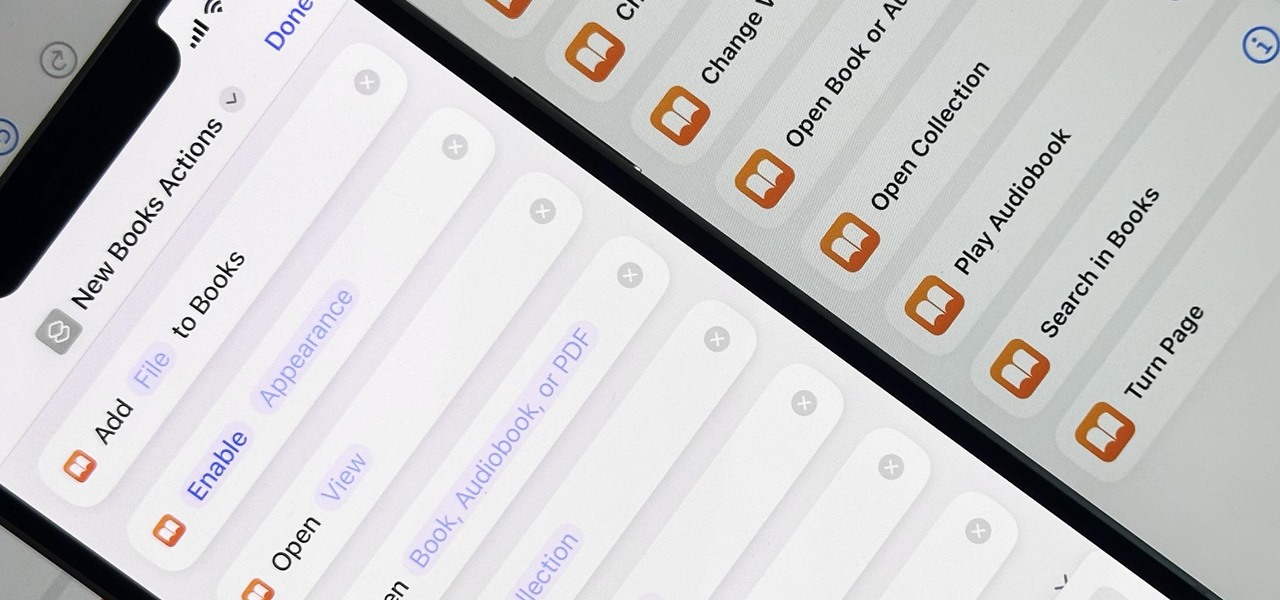
When iOS 16.0 was still in early beta testing, Apple teased us with a slew of new Books actions in the Shortcuts app, but none of them materialized in iOS 16.0 or 16.1. That changes with Apple's latest software update for iPhone.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

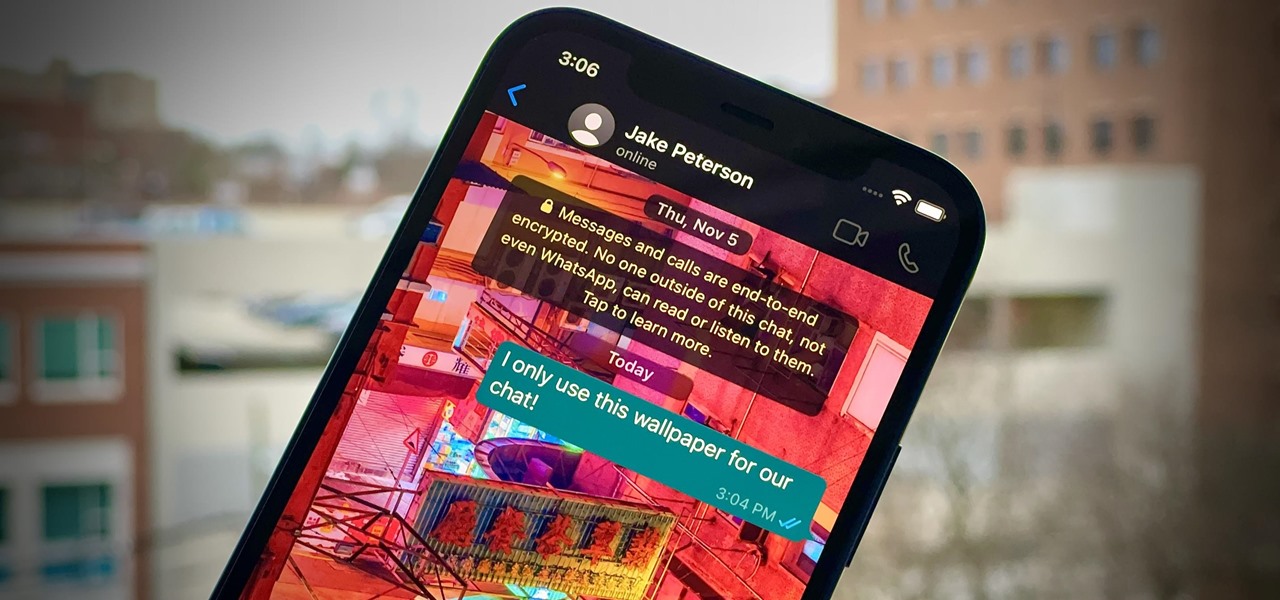
One of WhatsApp's best features is being able to change the default wallpaper for all chats. There's no reason to stick to the default WhatsApp backgrounds when you can be texting over an image of literally anything. In a newer WhatsApp update, you can go a step beyond that by setting custom wallpapers for individual chats, personalizing every text thread you have.

It should be simple to select and copy all text on a webpage in Safari, but it won't work as it does in other apps. Usually, you can press-and-hold down anywhere on a page and choose "Select All" from the edit menu, but that functionality is disabled in Safari and WebKit-based browsers by default — including in the latest iOS 14 version. Luckily, there is a workaround to getting a "Select All" button back.

Home Screen widgets come in various sizes on iOS 14 and later, and which size you choose will depend on how much content or data you actually want to see. But what happens when you pick the wrong widget size? In a perfect world, you would just edit the current widget's settings, but Apple didn't make it that easy.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

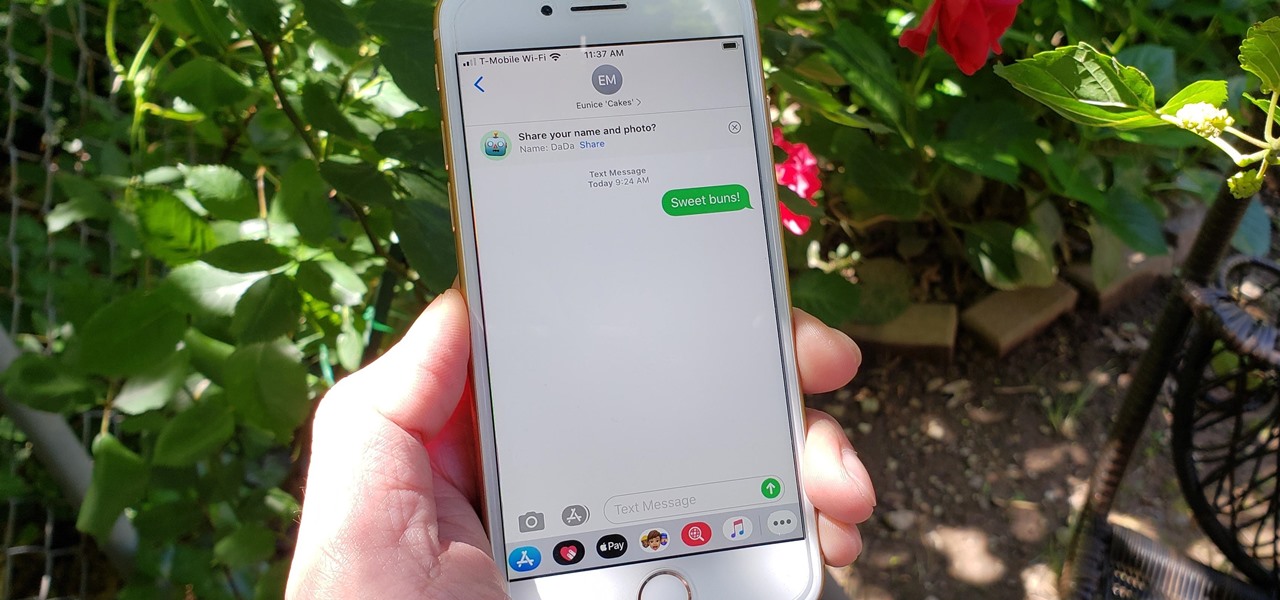
For quite some time, popular messaging apps such WhatsApp and Skype have let you set a profile picture along with a display name to make you more instantly identifiable to loved ones and colleagues. Apple has finally caught up with this fad in iOS 13. That means you can set a custom name and profile image within iMessage so others can quickly view who's messaging them at a glance.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

In recent years, many software publishers have tried to sell the business community on remote meetings via VR, but if social media chatter is any indication, it hasn't taken off in a big way just yet. However, for some, the notion of holding remote meetings using augmented reality, a medium in which you're still directly tied to the real world and not closed off in a blindfold-style VR headset, might be the better solution.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.