Summer cookouts and barbecues come with a lot of delicious foods, but to me, there's nothing better than dishes heaped with avocados. From guacamole to simply eating an avocado right out of its skin, I devour this fruit constantly—but it's one that can be tricky to find perfectly ripe.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

If you've noticed a tiny discolored spot on your computer screen that just doesn't seem to go away, chances are you have a stuck pixel. With modern LCD and OLED screens, there are millions of incredibly small dots (pixels) that make up all of the contents of your display—and within these pixels, there is a set of red, green and blue subpixels. These mix together at various levels to create all of the different colors you see.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Previously, the only way to see files in iCloud Drive on an iPad or iPhone in iOS 8 was to view them in Safari, which was pretty messy overall. To make iCloud Drive a little less confusing for the average consumer, Apple has included a dedicated app in iOS 9, allowing you to conveniently view all your stored cloud-based files right from your home screen.

Since the new Mac OS X 10.11 El Capitan is brand new, I recommend installing it on a separate partition on your hard drive. This will keep your current Yosemite system safe from harm, and will let you easily switch back to it should El Capitan become unusable for any reason.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

Spotlight, Apple's selection-based search system, received a major facelift on Mac OS X Yosemite. Packed with dozens of new features, such as a central search window and increased app suggestions, the reworked Spotlight was a breath of fresh air.

Samsung is known for its added features, but occasionally, these can cross the line between functionality and bloat. For many users, this is the case with the "S Finder" and "Quick connect" buttons that are hard-coded into the notification tray on most Galaxy S6 and S6 Edge variants.

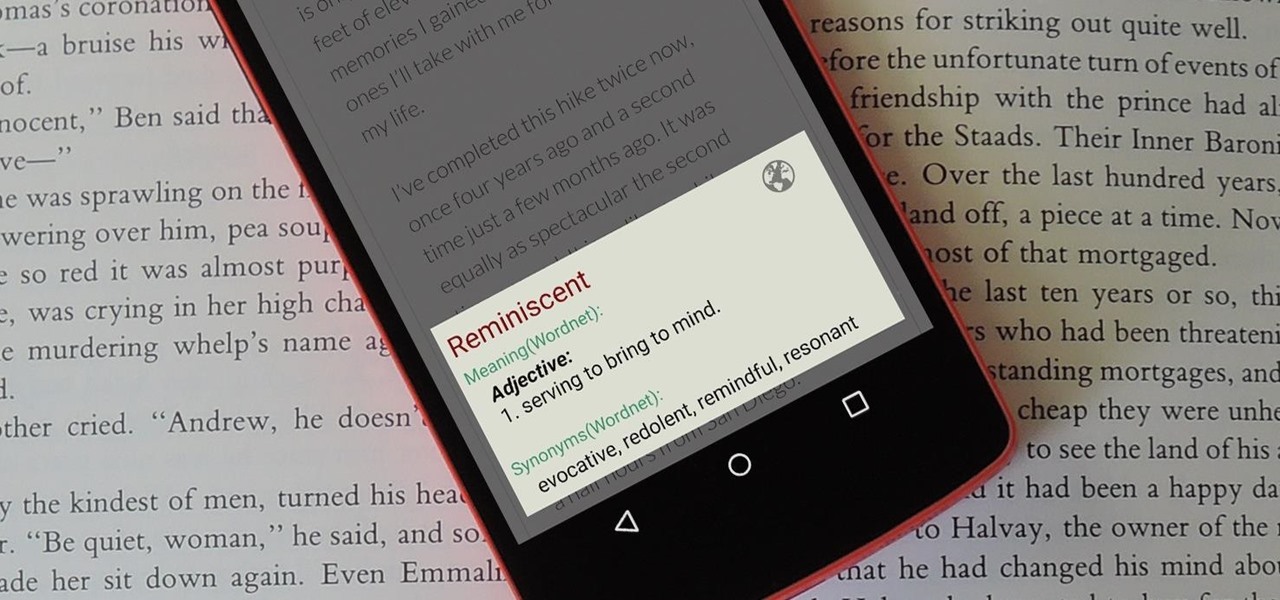
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Google Play Music is an awesome app—even if you don't subscribe to their $9.99/month All Access service, you can still use it to store and stream up to 50,000 of your own songs for free. Add to that the fact that it's a pre-installed app on most Android devices, and there aren't many reasons not to be using Play Music.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

If you don't like watching YouTube videos on your computer with your hand glued to your mouse, the next best thing is using keyboard shortcuts. They may not seem any easier than clicking, but once you get them down it's a whole other story. Plus, there are some features you might not otherwise use (I'm looking at you, speed control) unless the shortcuts existed.

Aside from the fact that it was the only game available on my cell phone at the time, I was really good at Snake. I still occasionally play it on my smartphone, but I've never been able to duplicate the same level of achievement as I once did.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

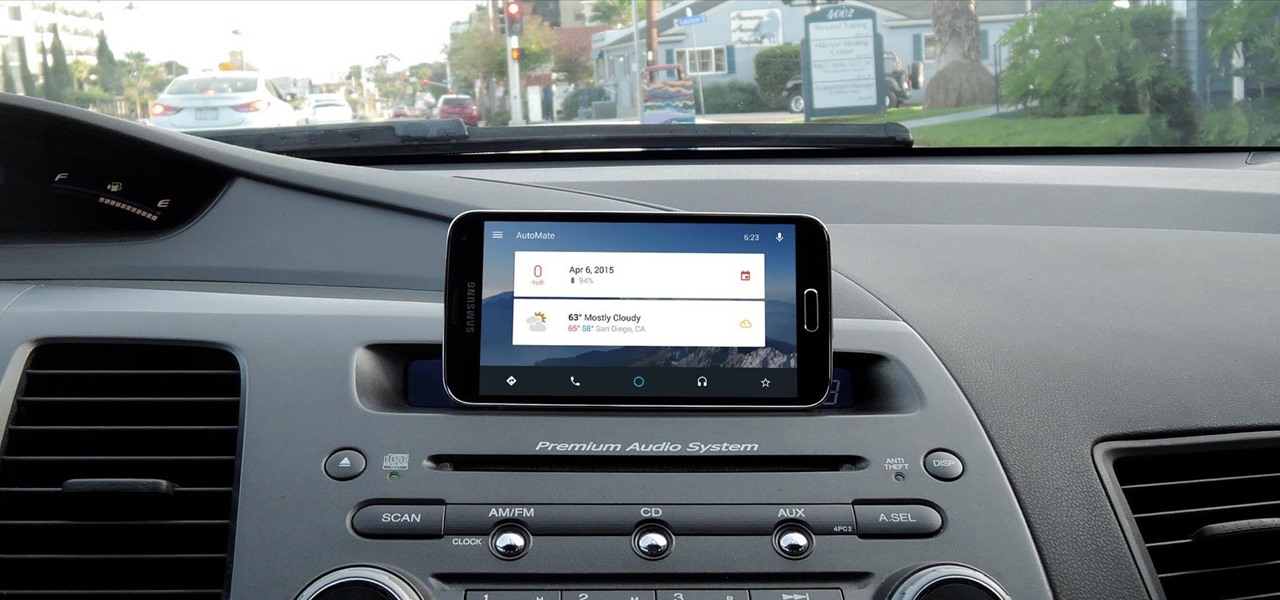
Auto manufacturers are slowly starting to debut models with Google's new Android Auto software baked into the dashboard console. Starting with the 2016 model year, we should see vehicles from Honda, Ford, Chevrolet, and many others sporting the new software.

Using the overview screen (aka recent apps) is a simple way to jump back to a previous task to continue where you left off, but as you use more and more apps, jumping back to that initial task isn't really that "recent" with all of those new tasks stacked on top of it. Now, thanks to developer PhinxApps, we can redefine what "recent" truly means using PinTasking. With this app, you can pin any app or webpage you're currently using onto your device's screen in the form of a Facebook-like chat-...

All across the web, countless users and critics have already decided that Periscope, the Twitter-owned live video-streaming app, has killed (or is on the verge of killing) Meerkat off for good.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

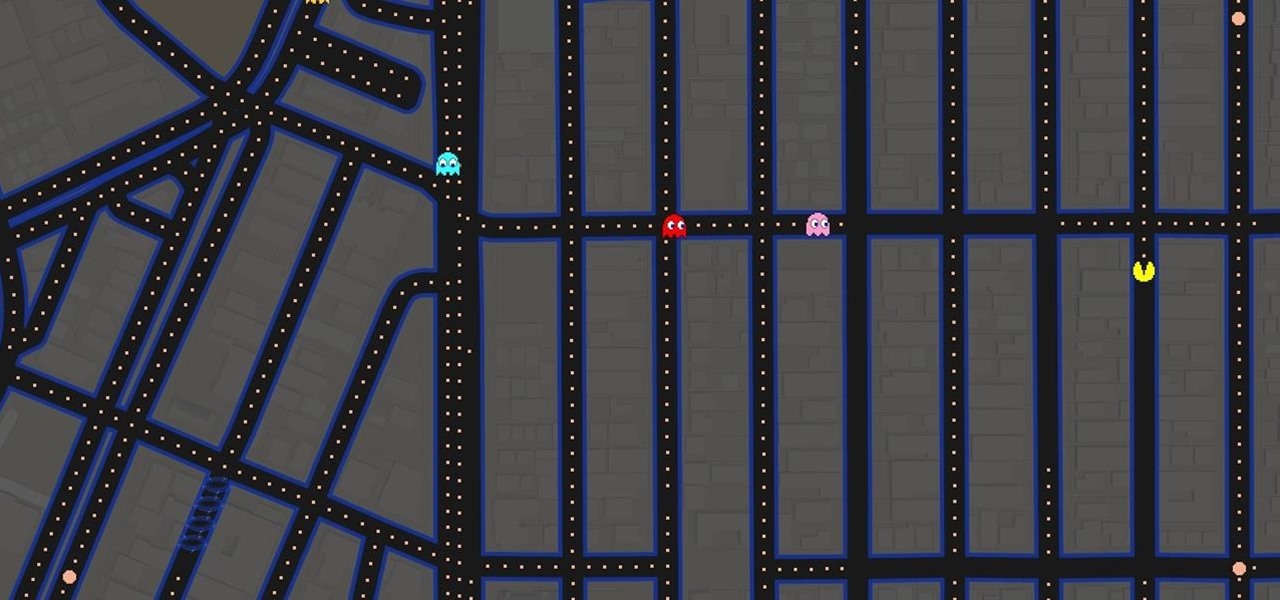
It's that time of year again. Each spring, Google likes to have a bit of fun with April Fool's Day. Pranks have ranged from a fake email printing service called Gmail Paper to a search engine for smells. It's all fun and games, but this year, they've taken that mantra rather seriously with a Pac-Man game baked right into Google Maps.

Yes, emojis are the [insert poop emoji here]. They can help improve your love life and even let you portray emotions in a more diverse and well-rounded way now. But combining emojis with GIFs? Well, that's some next-level [insert poop emoji here] right there, and with a new iOS keyboard from Puppy Ventures, that next level is finally here.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

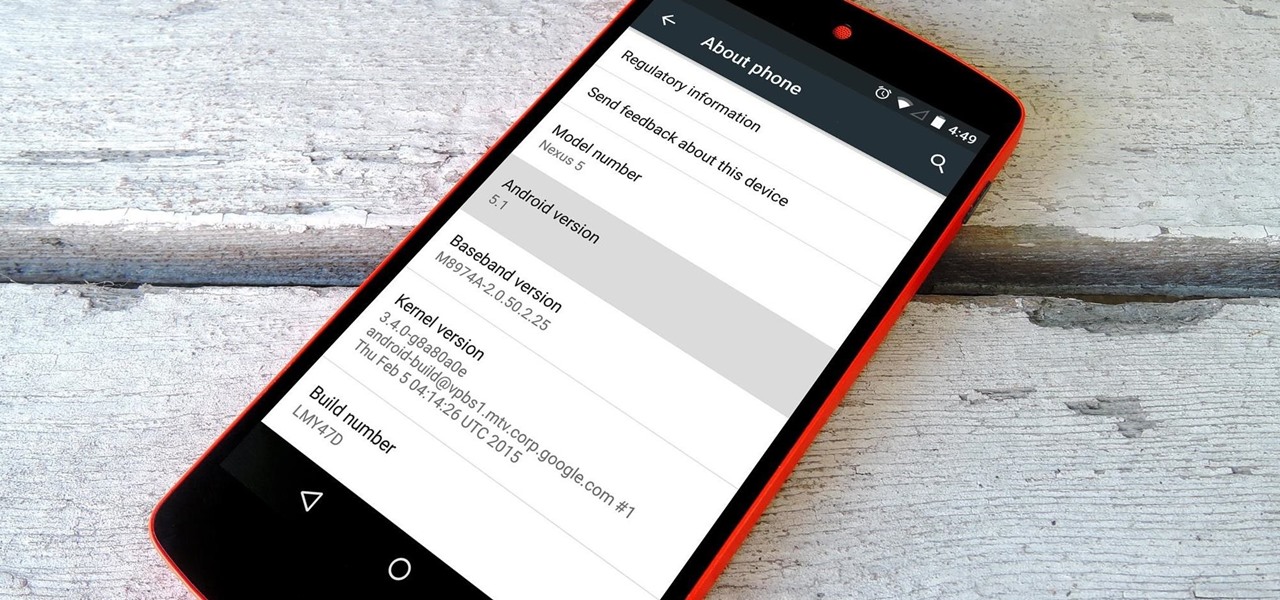
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

I hate flying for two reasons. Firstly, I'm afraid of heights and turbulence is absolutely hellish. Secondly, I hate overspending on airfare. Flying can be unnecessarily expensive, especially if you don't plan ahead or must deal with inclement weather. Nevertheless, the travel season is almost here and we're always looking for the cheapest, most convenient flight. But what service actually provides you with exactly that?

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.

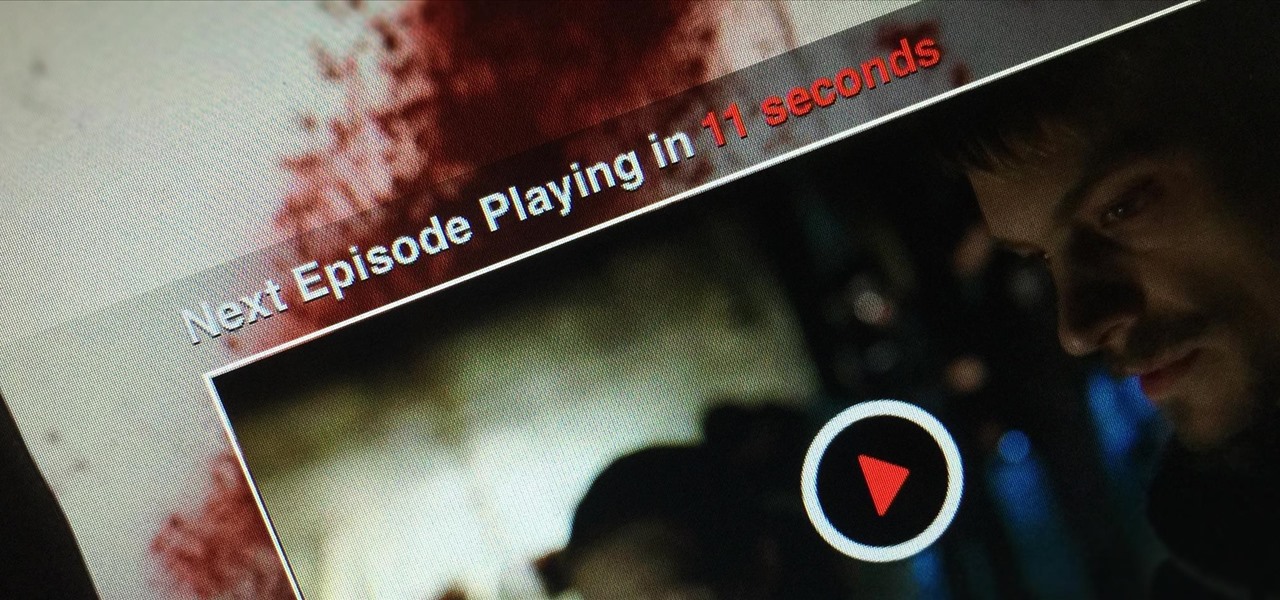
Netflix is an enabler. It creates a joy around binge-watching and couch potato-ness, and the major contributor to this epidemic is its built-in "Post-Play" feature.

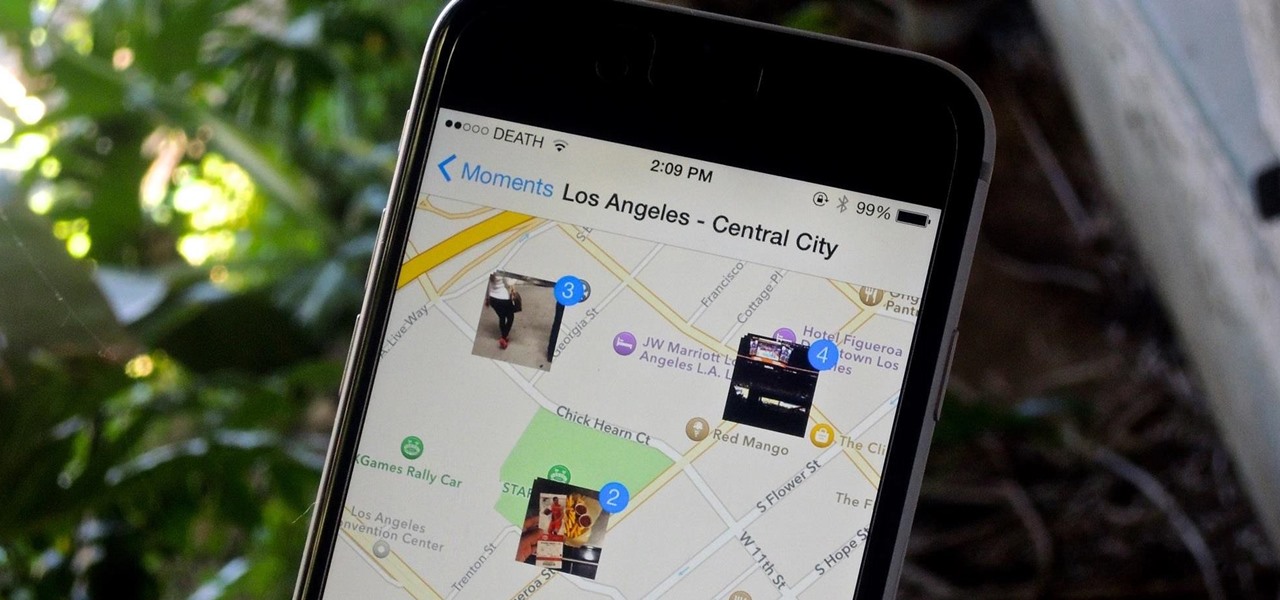
Location Services, a native feature on iPhones since iOS 6, is used to pinpoint your approximate location using a combination of GPS, Bluetooth, Wi-Fi, and cell tower information. Apple uses this on their smartphones for many useful reasons: so that you can tag locations in Instagram, get better directions in Maps, and check for matches based on your location in Tinder.

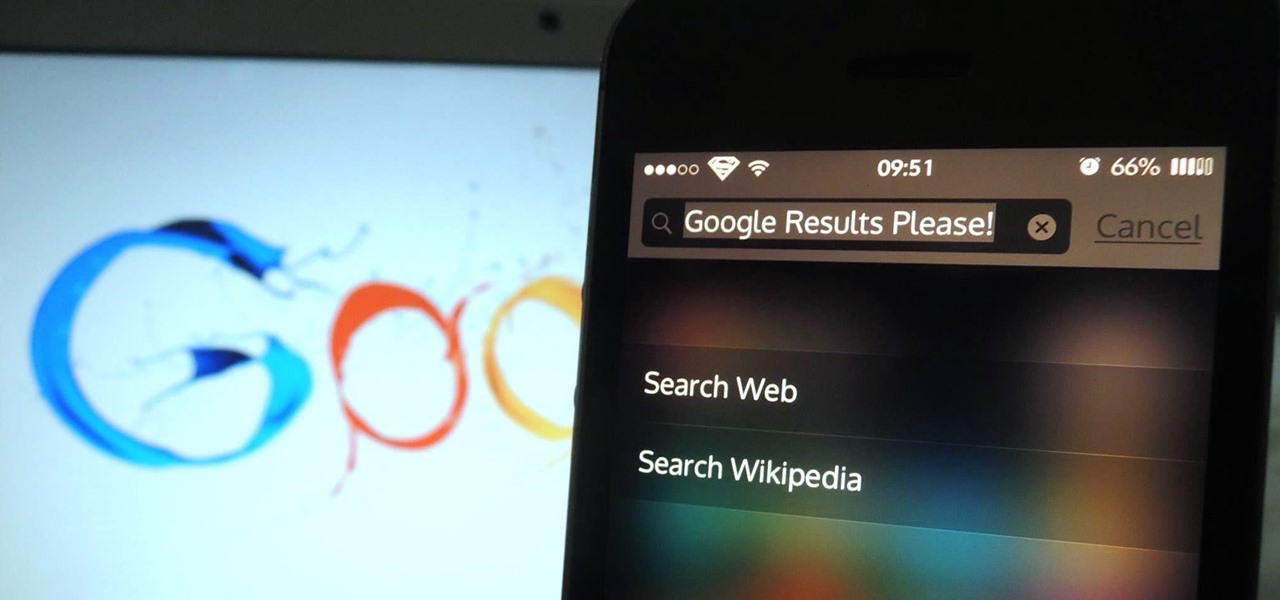
Spotlight makes finding apps, contacts, emails, songs, and old messages extremely easy on an iPad, iPhone, or iPod touch. You can even search for Wikipedia articles online, as well as perform general web searches.

Macs, like pretty much all Apple products, are notorious for not having a highly customizable UI. They do this to keep a consistent look and feel across all of their devices, but I've grown bored of it over the years.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

During class or while at work, it can take an immense amount of self-control to resist navigating over to Reddit. The link-aggregator and meme-warehouse makes it too easy to kill time... most of which you should be spending on various other tasks.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

CyanogenMod has always been on the forefront of ROM customization, and its newest release, CyanogenMod 12, is no exception. In the newest nightlies, they have included an updated version of their Theme Engine, which allows you to effortlessly change the way your entire system looks.

When surfing the web in Safari, you can double-tap the status bar to quickly scroll back up to the top any webpage. In other iOS apps that have the shortcut enabled, you can get the job done even faster by tapping the status bar only once. The only bad thing about this feature is that there's no shortcut for scrolling all of the way back down or to the middle.

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

When my Nexus 5 received the Lollipop update, one of the first things I noticed was how subtle and quiet the new lock and unlock sounds were. Sure, this is a minor quibble, but it's also an easy fix.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...