Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.
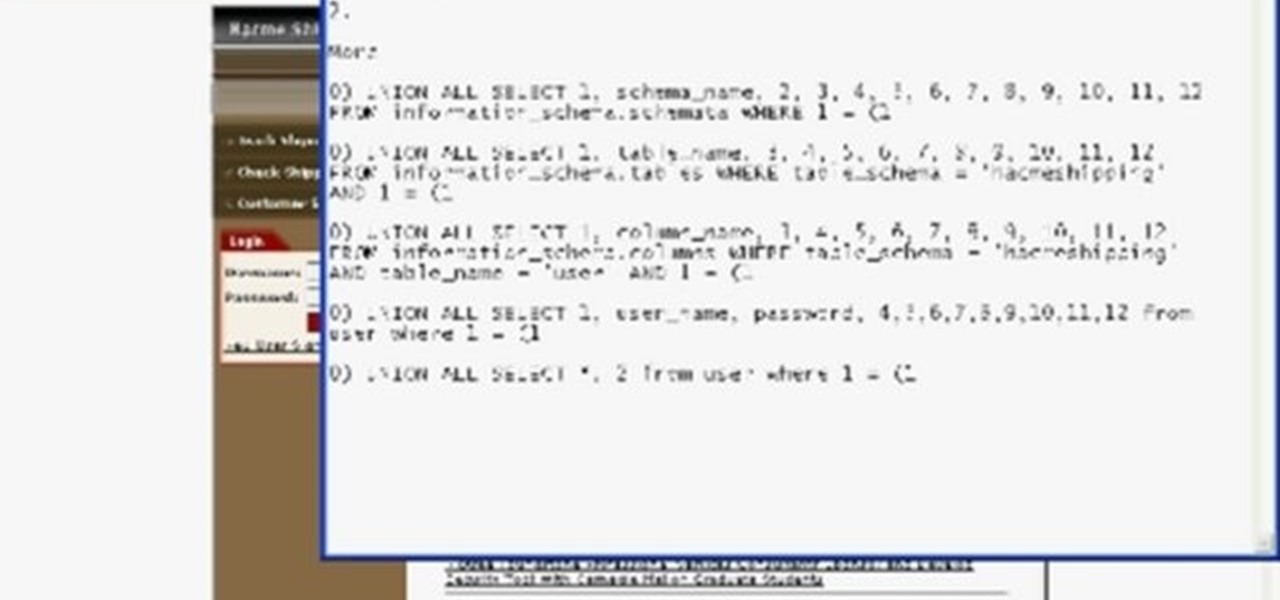
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

If you're a Firefox user and frequently use free image hosting services à la ImageShack & Photobucket, then you've no reason not to check out the ImageBot Firefox extension, which does quite a lot to streamline the picture uploading process.

This video tutorial is all about recovering the deleted files in Windows Vista. If you are using the Windows Vista and you have unknowingly deleted a file and emptied the recycle bin, then you can recover it. This can be done by using the Shadow Explorer. Shadow Explorer is a Vista program that accesses the Vista Volume Shadow Copy Service. In Vista, the shadow copy service is turned on by default. It creates backups of files on a regular basis. Shadow Explorer provides access to these backup...

As one of the world's largest and most powerful cloud computing platforms, Salesforce is used by countless companies to manage customer relations, deliver services, and innovate solutions to complex problems.

Many streaming services offer user profiles for different people in your household, some of which also include profile images. In most cases, you can set a custom profile image to better differentiate and personalize your account from the others, and HBO Max lets you do the same, albeit, with limited options.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

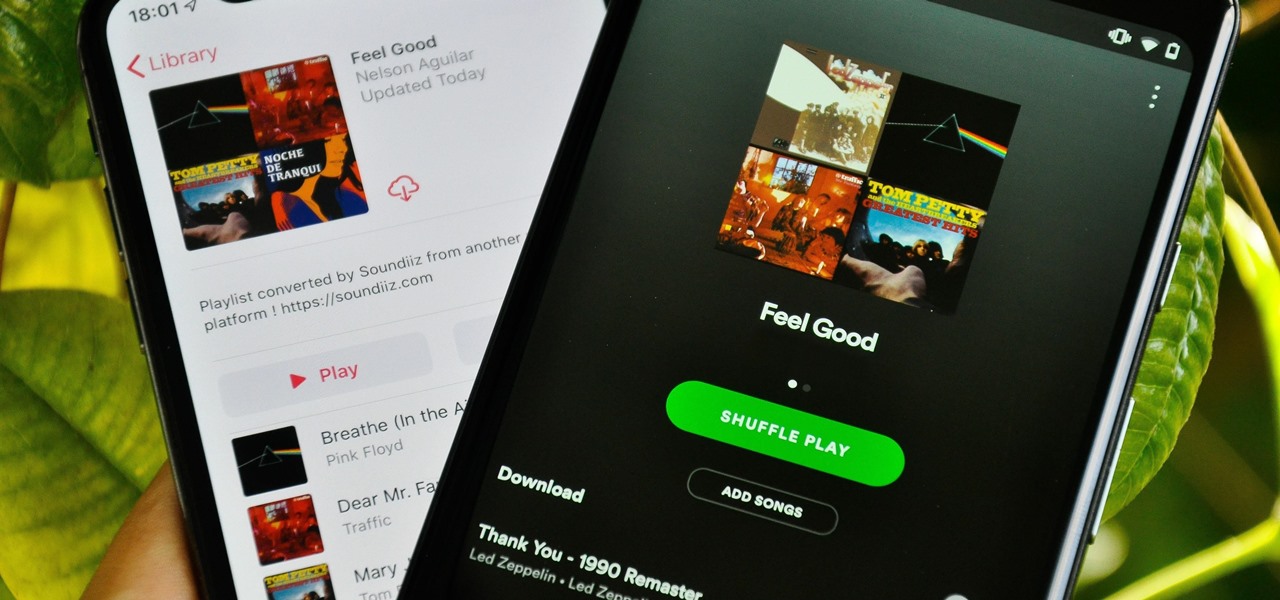
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luckily, if you're moving from Spotify to Apple Music, you can use a third-party app to take playlists with you.

The annual Augmented World Expo (AWE) typically packs the front page of Next Reality with new products and services from companies in the augmented reality industry.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

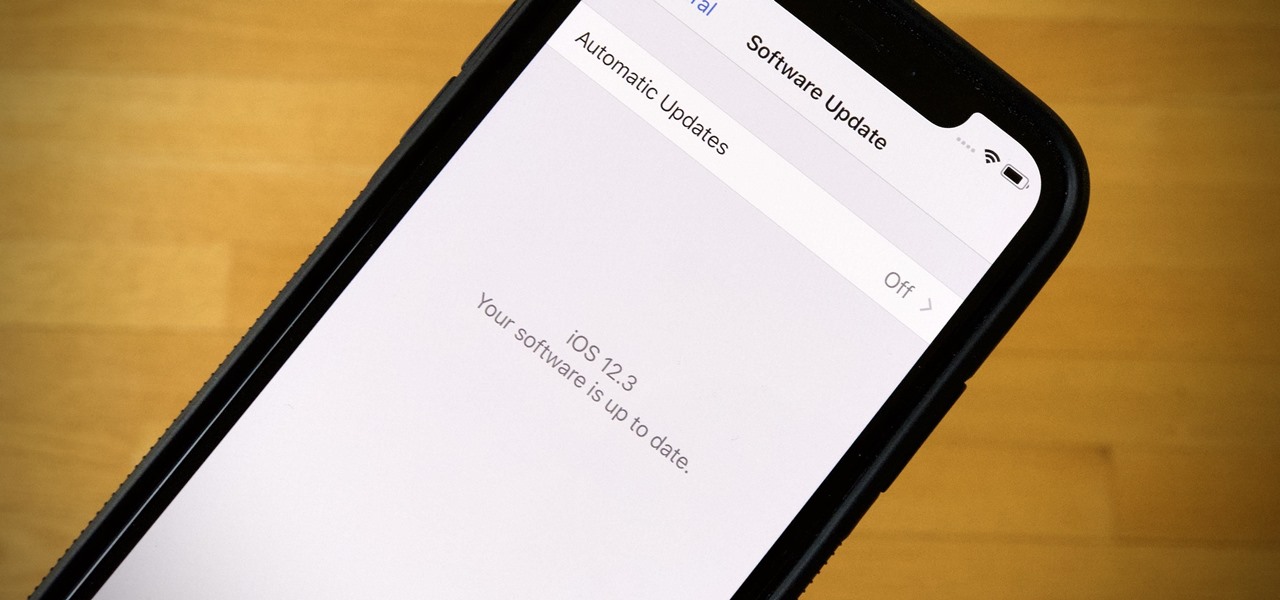
If you're a public beta tester, your Thursday just got awesome. Apple just released the first public beta for iOS 12.3 today, March 28. This update comes right on the heels of the first developer beta for 12.3, which itself released just one day ago. Thanks to that release, we know that this update contains a new TV app with updated layouts, Apple TV Channels subscriptions, a new logo, and more.

It's an exciting time to be an Apple fan. Monday saw not only a major announcement of new Apple services and subscriptions but also the official release of iOS 12.2. If you're a beta tester, you probably watched 12.2's evolution over the last two months. Well, get ready to do it all over again — Apple just released the first developer beta for iOS 12.3 today, Wednesday, March 27.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

With would-be unicorns Magic Leap and Niantic among its investments, Google is an active investor in augmented reality technology. This week, the search giant experienced both ends of the investment cycle, with an exit via Lyft's acquisition of Blue Vision Labs, and a funding round for Resolution Games.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.