
How To: The Five Phases of Hacking
Five Phases of Hacking:- The five phases of Hacking are as follow:


Five Phases of Hacking:- The five phases of Hacking are as follow:
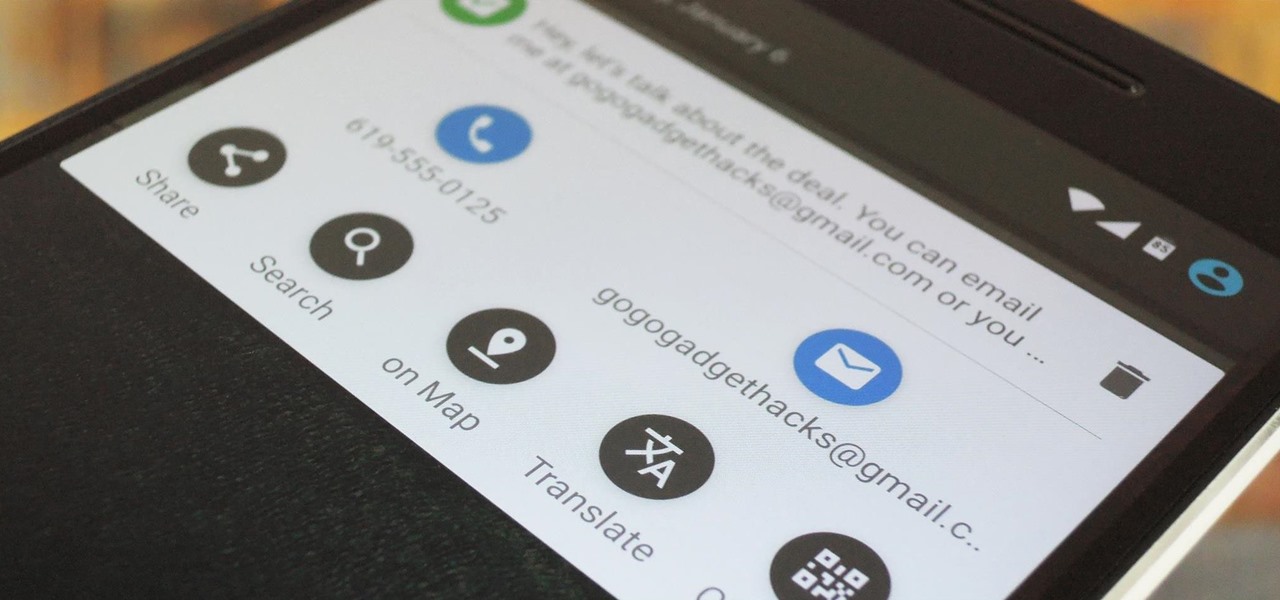
Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.
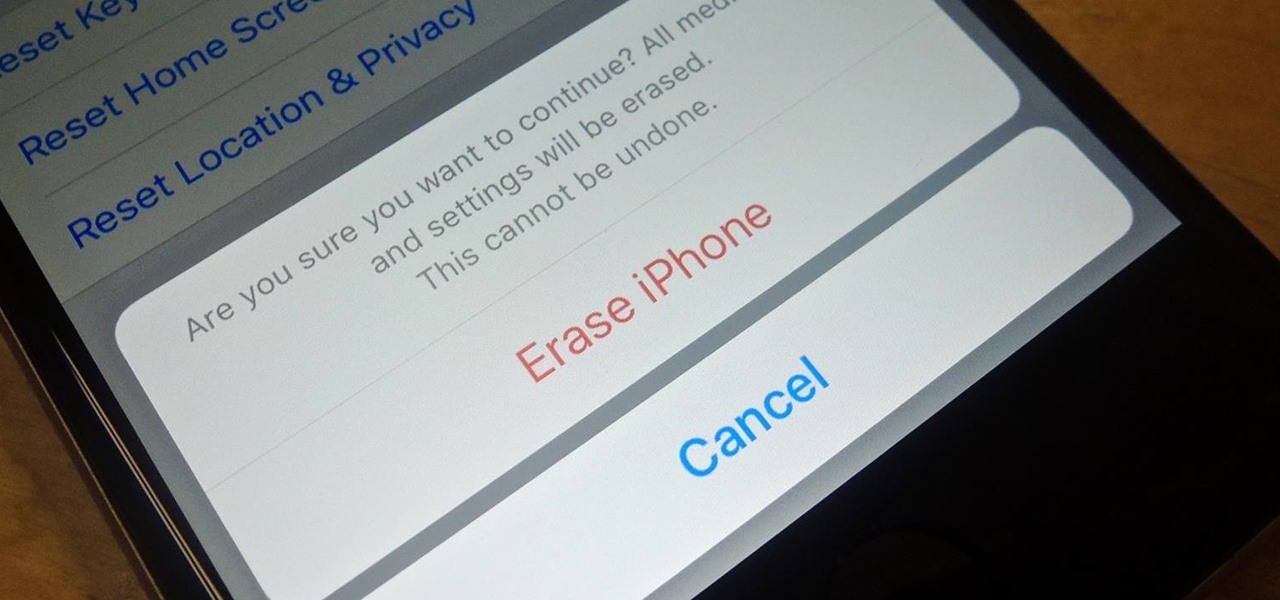
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when they are ready.

If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.
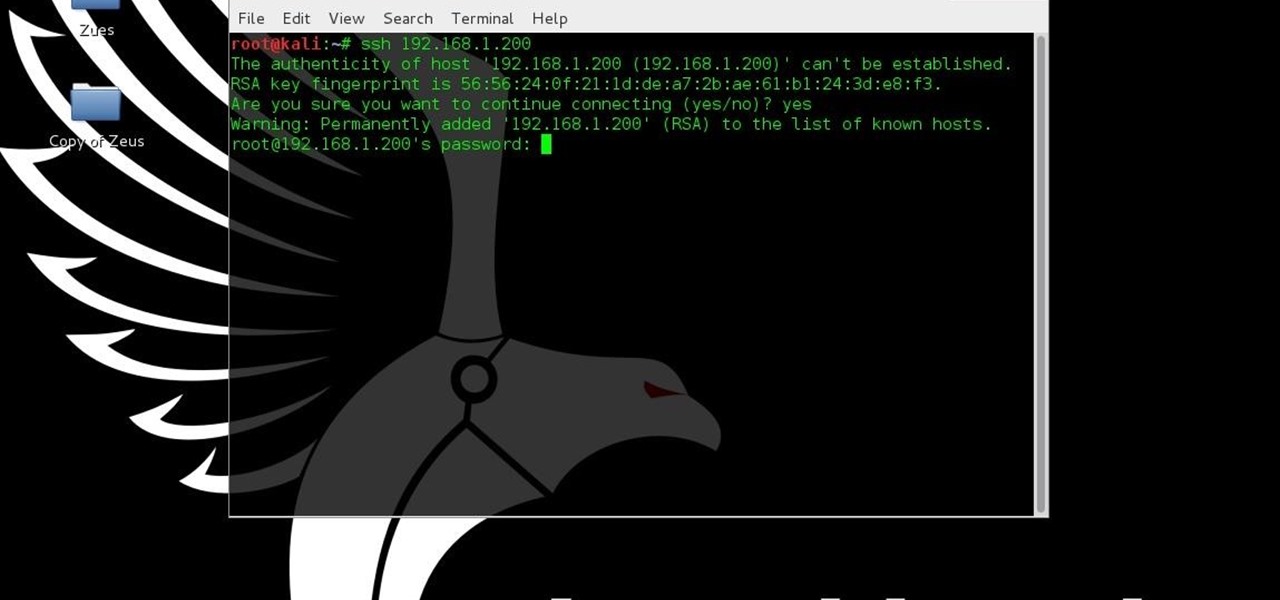
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.
Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Android Lollipop, introduced an array of new features and aesthetics that pleased many loyal users. One of those additions being the new heads-up notifications. Taking subtle inspiration from iOS, these notifications are visually appealing and can be easily dismissed or expanded, but they do require that you take an action before they go away immediately. Of course, you can always wait 10 seconds for them to disappear, but that can be really annoying if you're in the middle of a game or editi...
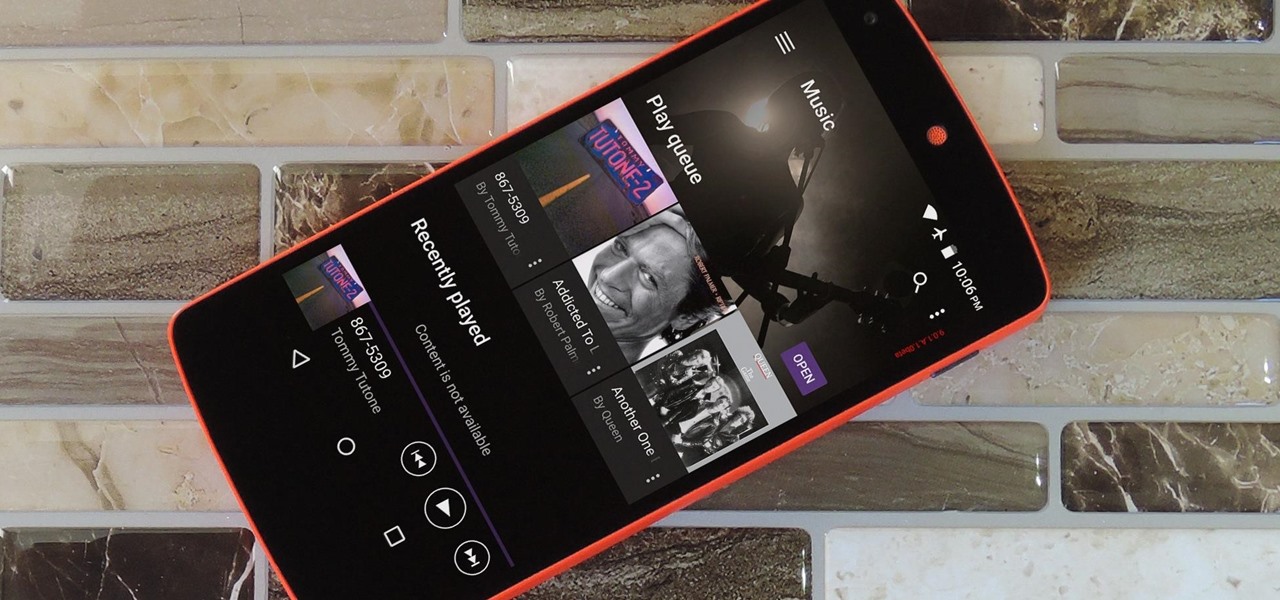
Sony's Xperia line of smartphones are beautifully crafted and have many great features. But considering the fact that Sony has evolved into a media company over the last two decades, it's their media-related apps that stand out the most.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.
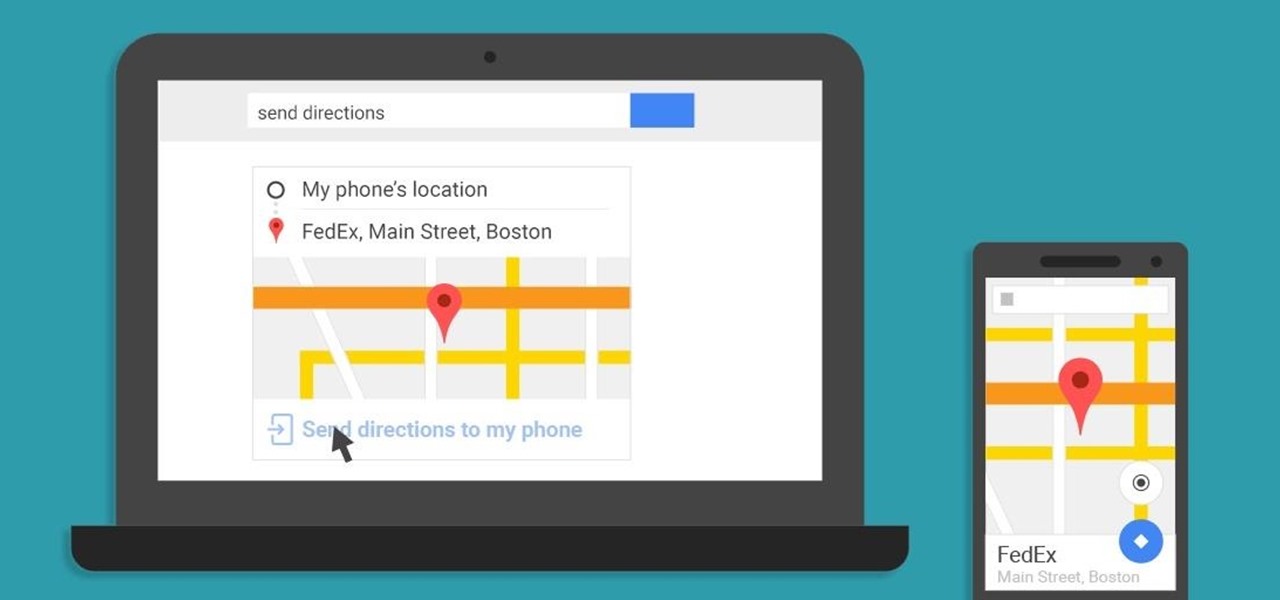
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Resources for finding new music are at our disposal in all corners of the internet; the only problem is deciding which one is the best for you. Spotify, Pandora, and Rdio all have options to discover new music on your smartphone, but they tend to expose mostly established artists, making the process of finding lesser-known but good music a game of trial and error.

In the shadow of Facebook's announcement for third-party app development on Messenger, the company has announced the release of a whole new application called Riff, a creative tool for making videos with friends.
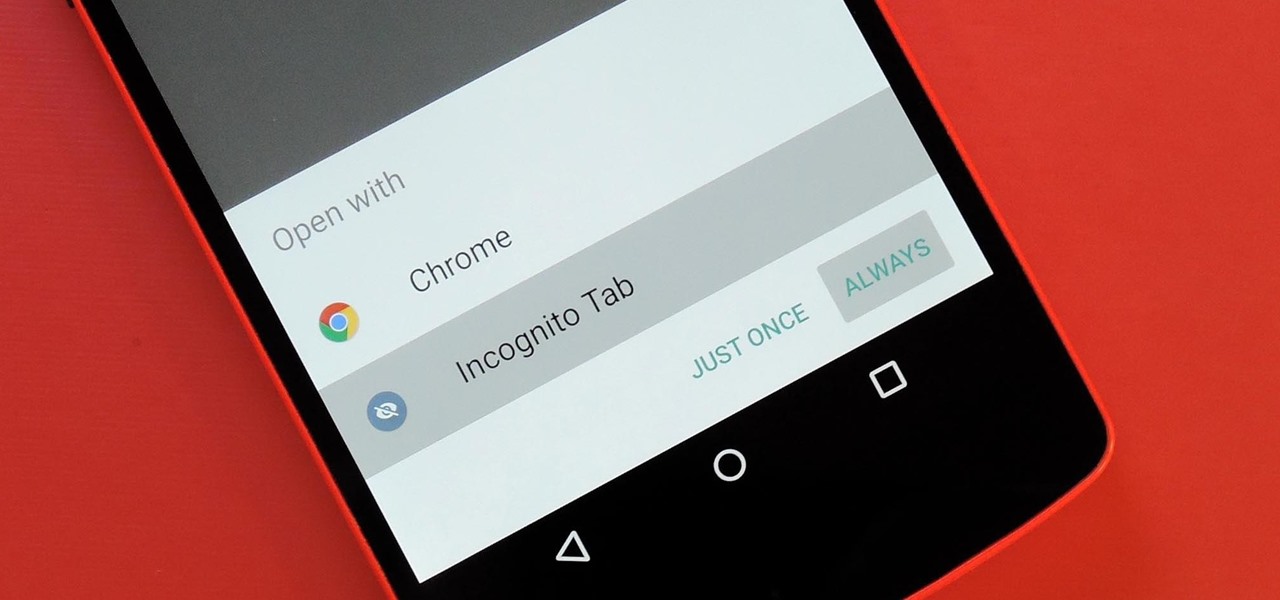
Chrome's Incognito Mode is a great feature for folks that don't want their browsing history tracked. When it's enabled, Incognito Mode makes sure that all cookies and cache that are saved while you're browsing are deleted as soon as you leave a webpage.
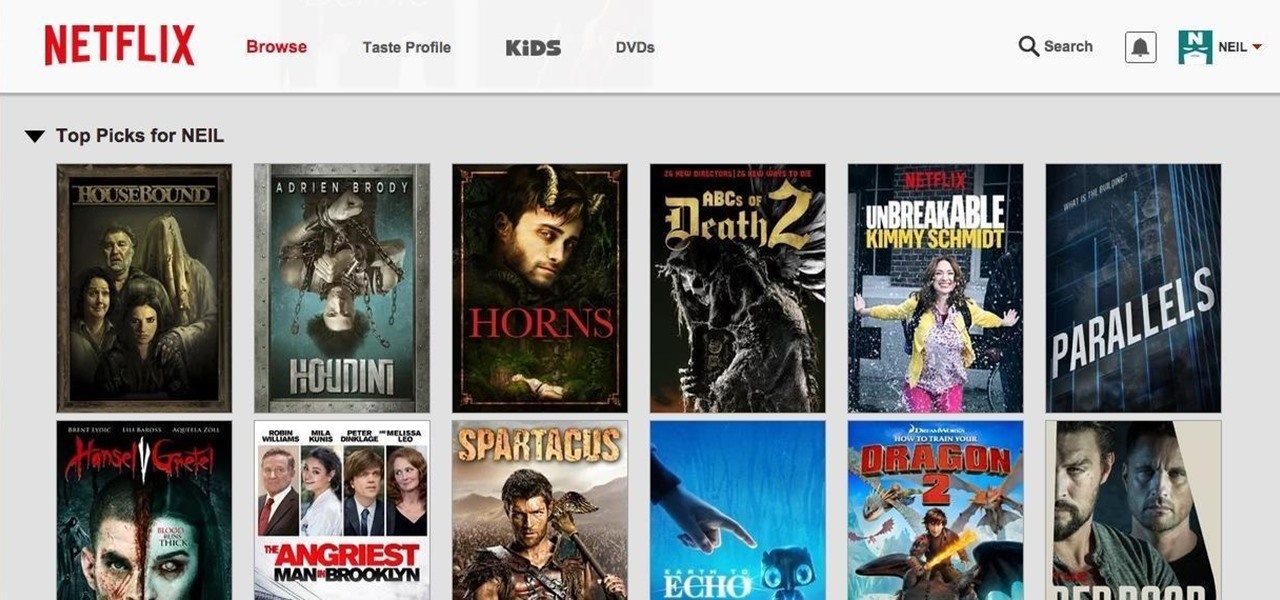
Netflix was my proverbial gateway drug to cord-cutting, as I'm sure it was for many others. Yet as much as I truly love Netflix and its service, there are some annoyances I have with the interface of the desktop web version.
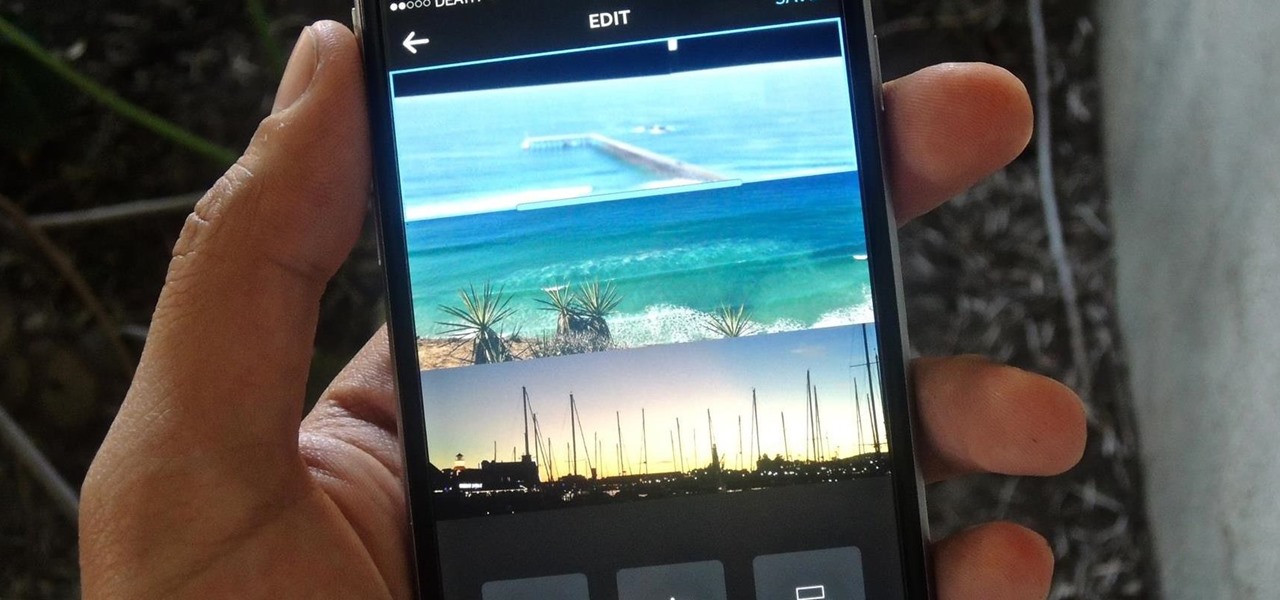
If you're one of the many that likes to upload collages to Instagram, the Facebook company has a new tool for you. Instagram released a brand new app in March called Layout to help facilitate the process of creating photo layouts to post onto social media or just share with friends.

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).
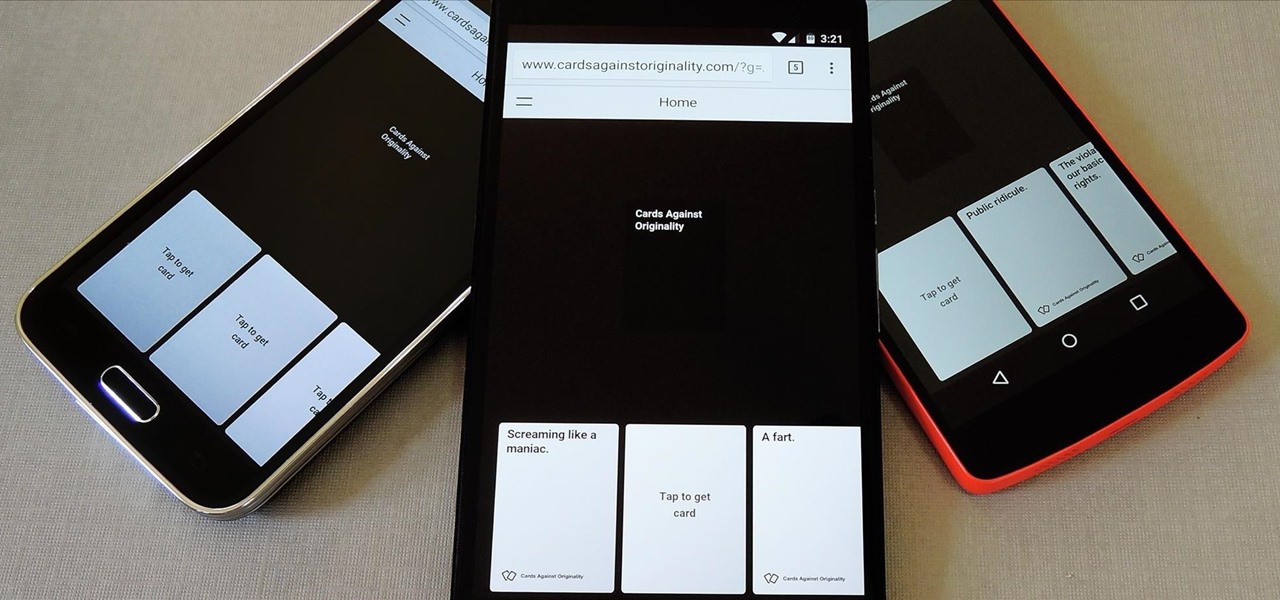
Cards Against Humanity is a popular party game with good old-fashioned raunchy adult themes that go quite well with a few alcoholic beverages. Up until now, though, you had to either print out a set of cards or order the official deck to play—unless, of course, all players happened to have devices that sported the same operating system.
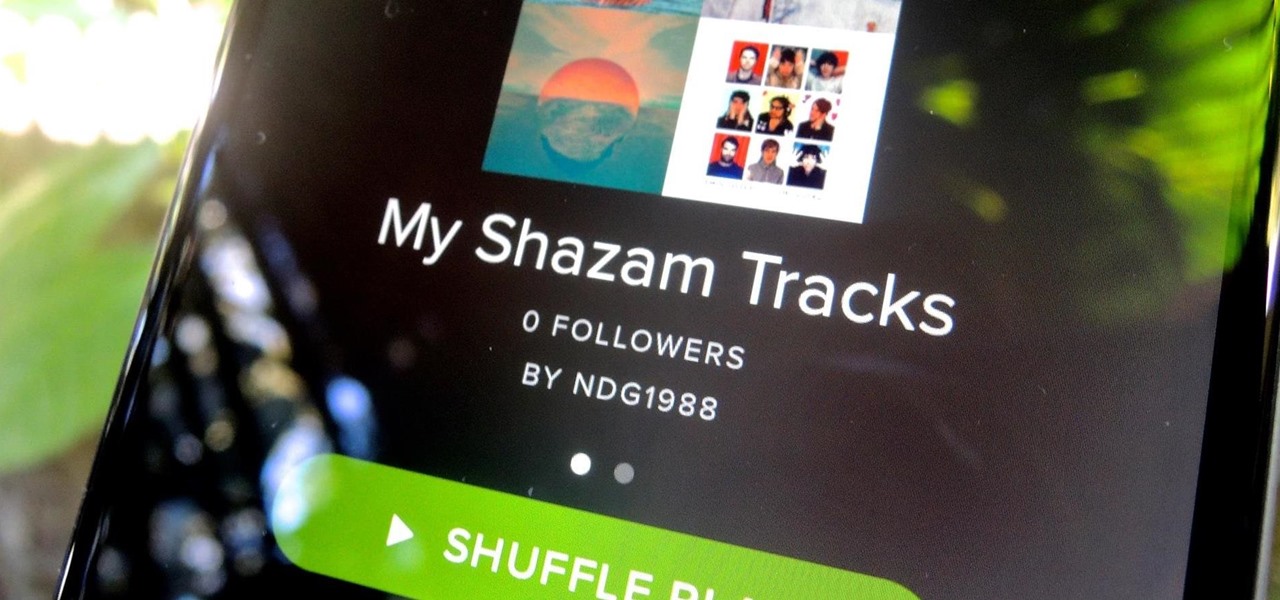
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."

These days, we truly have a world of knowledge at our fingertips. Trouble is, a large portion of that information is not something you'd want your five-year-old learning about quite yet.
Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.
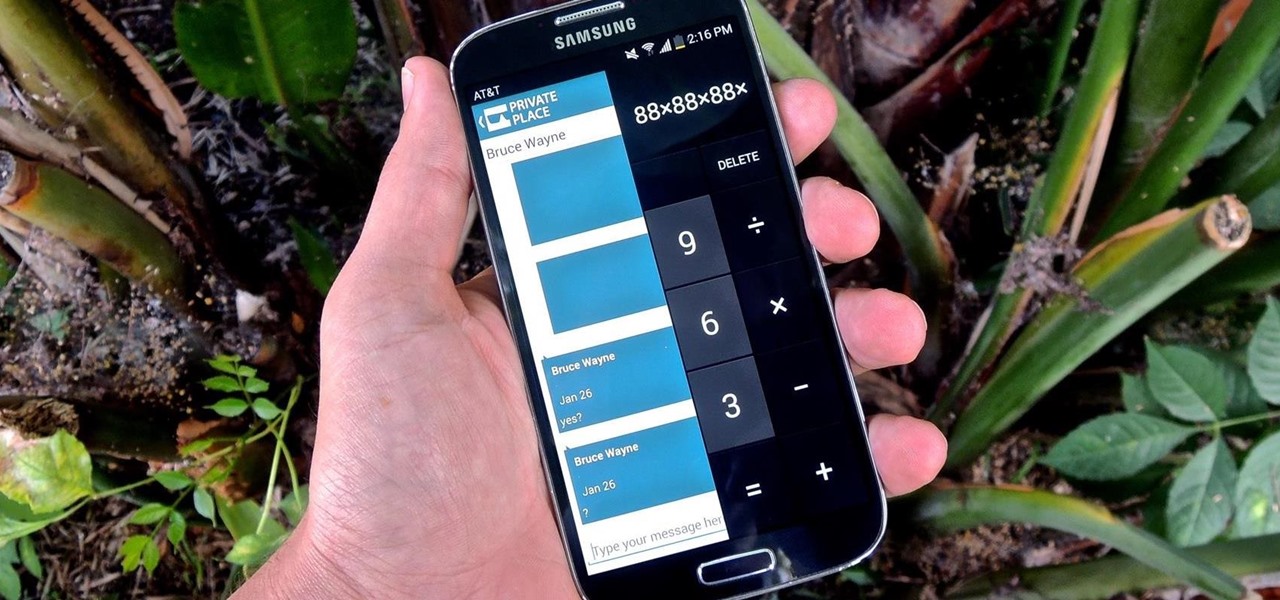
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

You don't need a study to tell you how beneficial music is to helping you fall asleep. Most of you probably have your soothing playlist and SleepPhones queued up and ready to go before you get into bed and count those Zs.
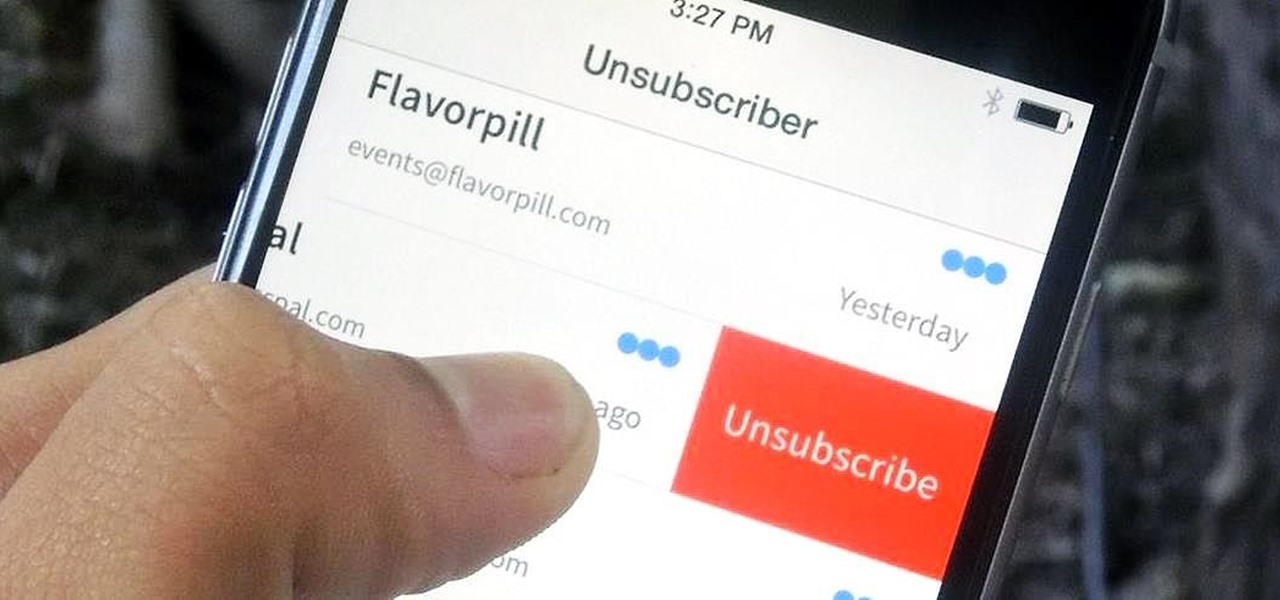
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.
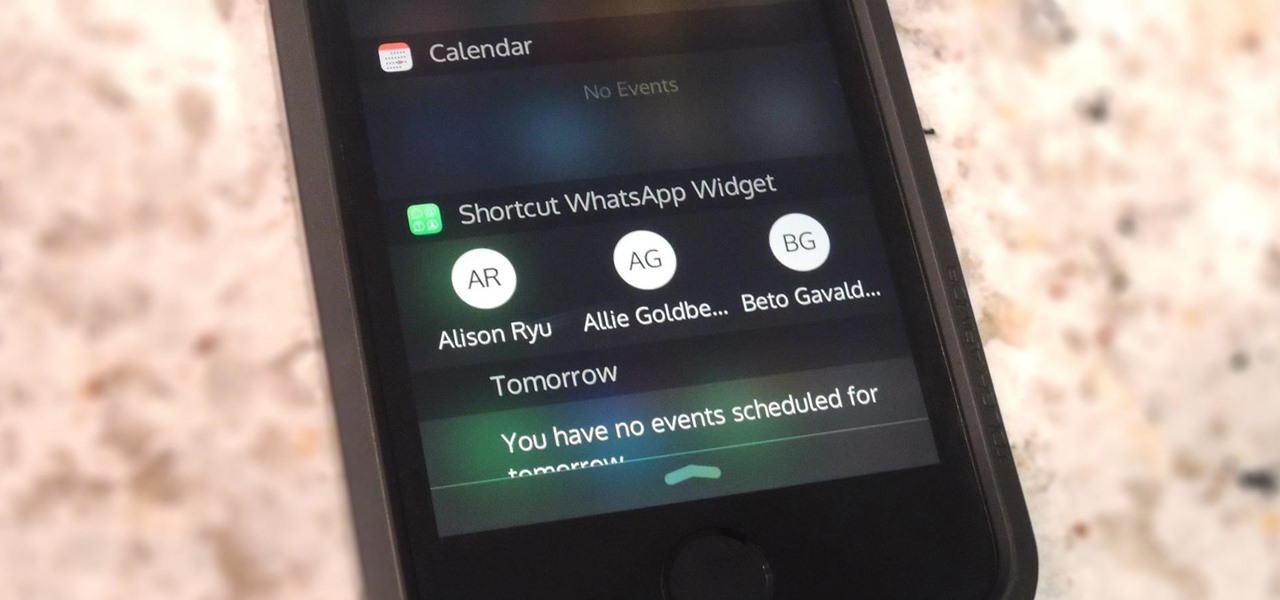
WhatsApp is the go-to application for sending a message (or 100) to friends at home and abroad. And the best thing is, the service has remained true to its roots after Facebook acquired the company for $19 billion.

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

One of the more talked-about features of Android Lollipop is a new Priority Mode that allows you to mute all notifications except for those coming from starred contacts. As simple as that sounds, this can still be a bit confusing—or at least lead to some unwanted interruptions.