"What is dead may never die." That's easily one of the best lines (and episode title) from HBO's Game of Thrones series. While the saying may ring true for the Ironborn, it's not quite as catchy when it comes to batteries.

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

As we all use our smartphones for more and more things, we constantly want to share and view those items on a larger screen, especially when it comes to media. While phones like the Samsung Galaxy Note 2 and tablets like the iPad do make watching Netflix on a portable device pretty legit, bigger is always better. Newer iPhones may have Retina displays, but watching Avatar on your phone is like being forced to drink a delicious mango tango smoothie with a coffee straw. Plus, if you want to sho...
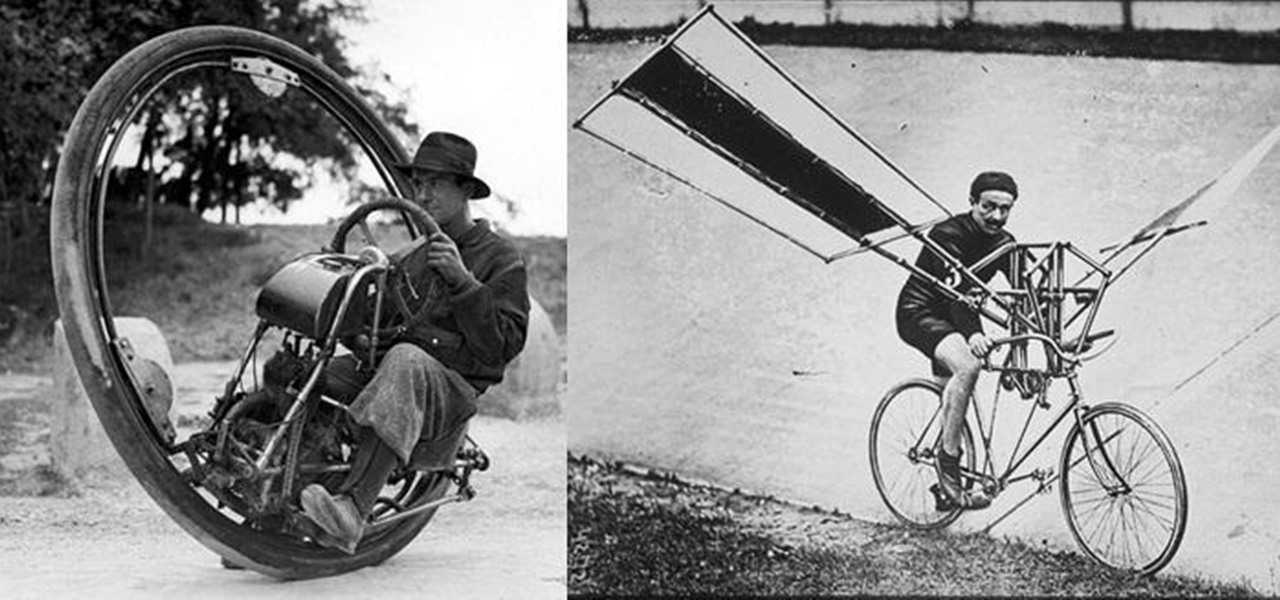
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

The reasons for donating surpass much more than the direct and obvious benefits (ahem...taxes). Charitable donations are a direct reflection of your values and perspectives, not only improving your self worth, but can bring about unintended advantages.

If you haven't walked into a department store or seen one of those millions of jewelry commercials airing over the last month, you might not know that February 14th is Valentine's Day.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

The holiday season is creeping up fast, and if you're shopping for a Steampunk, it could be almost impossible to find anything for them unless you know exactly where to look. Luckily for you, some of us have done all of the work you'll need. Whether you're Steampunk shopping for Christmas, Hanukkah, Chrismukkah (yes, that's real), Kwanzaa, or Festivus, you're sure to find something for that special lady or gentleman in your life by taking a stroll down this list!

Winter is coming... and if you don't get that Game of Thrones reference, it's okay, you're still cool in my book.

Syncing your Google and Facebook friends to your smartphone gets your contacts list up-to-date quickly, so you'll never have a problem finding someone's number.

Believe it or not, the 2012 Presidential Election is (finally) almost over. While most of us are breathing a collective sigh of relief (no more political ads!), it still seems like it hasn't been that long since the last election results were announced. This time, though, one of the biggest differences is how people will watch. Since traditional cable is on its way out, and mobile devices are getting more popular every day, a lot of people will be watching this year's election results online ...

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

Redbox recently announced a partnership with Verizon to bring a new streaming video service called Redbox Instant to an already crowded table. No prices have been released yet for the service, but with Netflix, Hulu, Amazon, YouTube, iTunes, and many others all attempting to get a hold of your dollars, what are currently your best options? Subscriptions Services

As I said before in my earlier post on how to make a two-tone doorbell, sound is more than just music. Note blocks can create a wide variety of notes and sounds, and those can be used for more than just making a stirring rendition of "Still Alive" from Portal.

Omniscience is not required to make some really cool shit happen. Yes, it took a while, but we can make fuel from the Sun! Solar panels are basically our answer to God. And now that we can make solar electricity, finding the most efficient way to harvest it is tricky.

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

Learn tips for using the Celtx free screenwriting software, including project library, production schedule, editors, and online services in this free screenwriting video series.

In this online German recipe video series, learn from gourmet chef Rainer Wickel how to prepare German potato pancakes, wienerschnitzel, and a German sauerkraut casserole. This expert chef will teach you about traditional German cooking, what wienerschnitzel is, what German potato pancakes are, what a sauerkraut casserole is, and the ingredients and utensils needed to create these traditional German dishes.

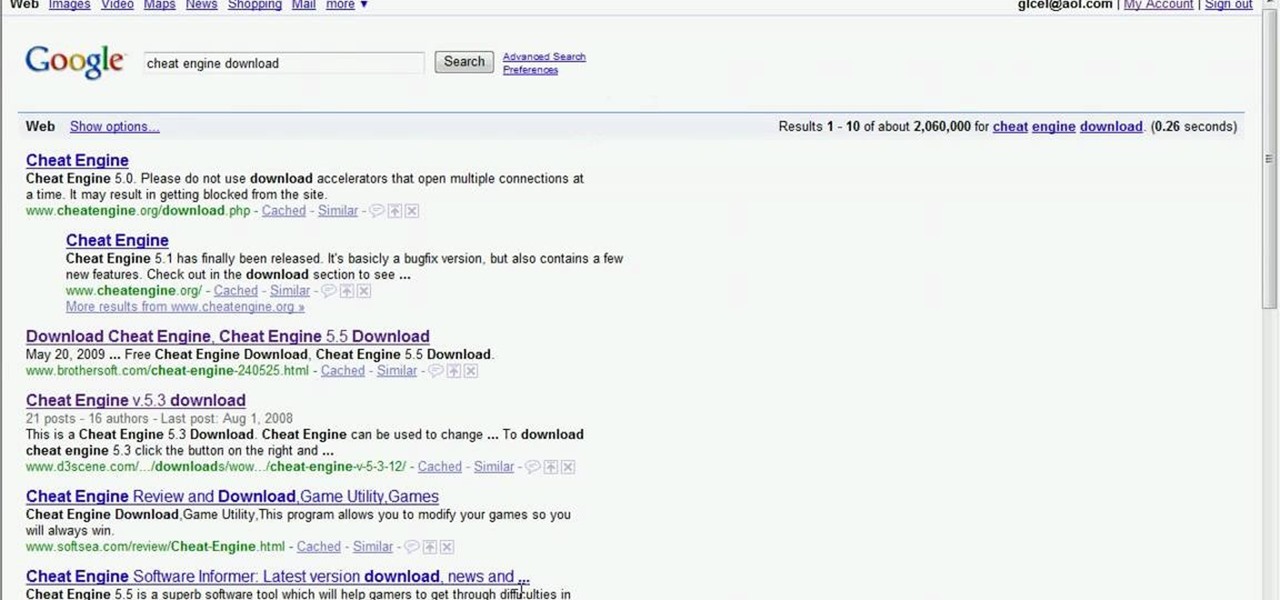
This video tutorial will show you the one thing everybody wants to know… where's the Cheat Engine 5.5 download at? There's nothing to getting Cheat Engine on your computer. Once you have it, you can start hacking and cheating all of the flash games you play on Facebook and MySpace and every other site with online games. So, to download Cheat Engine 5.5, you just need to Google it and you'll find it in the first result. Or you can just go to http://www.cheatengine.org or the download page for ...

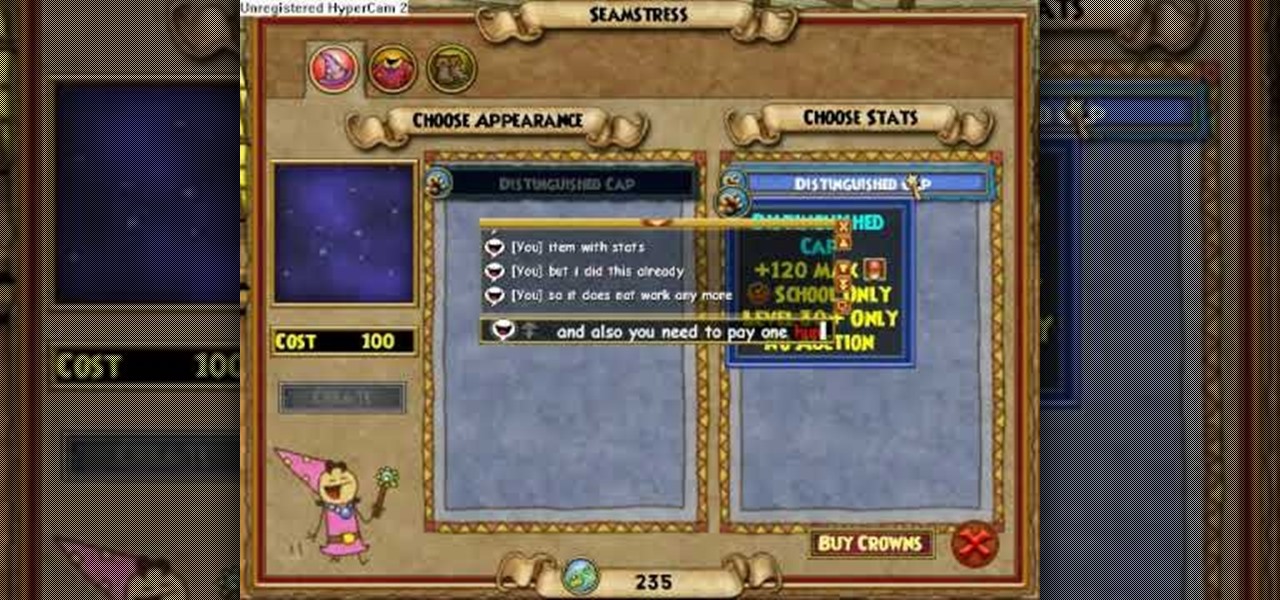
Hemming and stitching in Wizard101? Yep, learn how to stitch itms together and make an awesome wizard-like costume.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get into Nightside without beating streets in Wizard101. You don't have to beat all of the streets to get to Nightside in Wizard City.

IMVU is a 3D avatar chat, instant messenger, and dress up game. Get help with all of your IMVU avatar needs with these IMVU tips and tricks! Watch this video tutorial to learn how to earn credits easily on IMVU (09/28/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09).

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to hack Evony (09/17/09).

Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to cross-dress on Meez.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get heroes and troops in Evony.

In this video series, watch as accountant Joseph Salazar teaches how to operate an accounting calculator. Get tips on how to calculate sales tax, how calculate finance charges, and how to find the installment buying amount. Use these step by step online tutorials to continue your accounting career.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

If you actually had to look up what "DS" stands for in Nintendo DS, that probably means you weren't a huge fan of the portable game system. To be honest, I never was. It's fairly bulky and has two tiny displays.

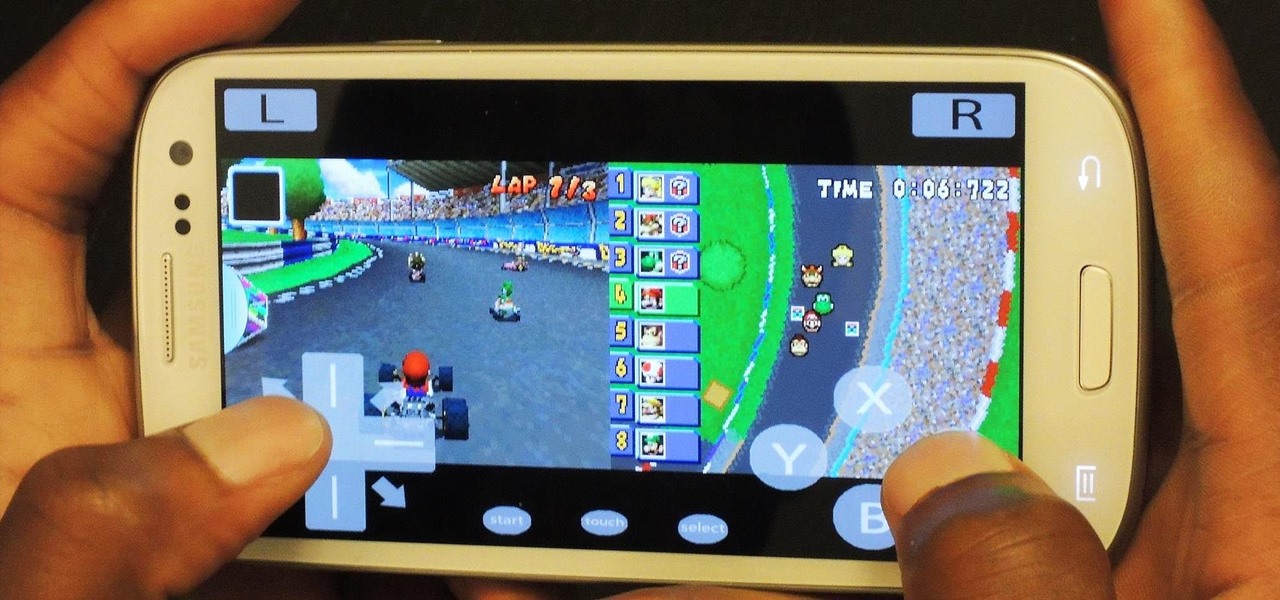
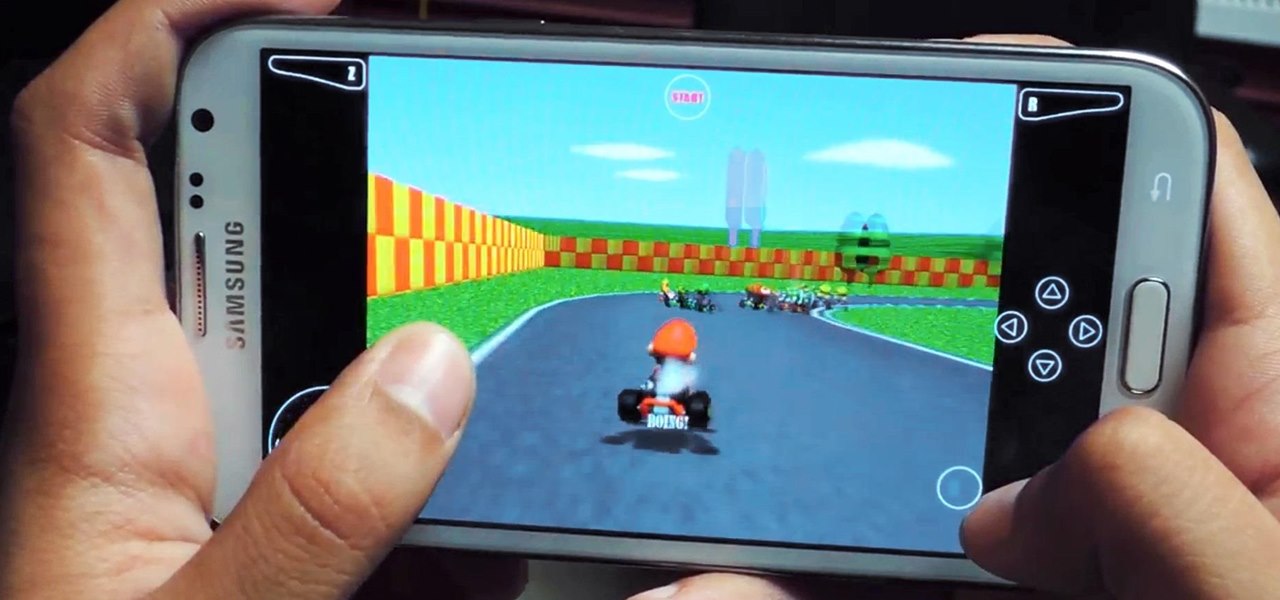
Nothing can beat a portable system designed specifically for gaming. There are tons of emulators available on Google Play, but most have awkward controls, large game files, resolution issues, and hardware compatibility problems. The list could go on...

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Katarina is one of the champions you can use in League of Legends, being able to both deal out damage and handle taking it herself. Here's a quick overview of what she can do, and the best way to incorporate this champion into a team game on the Fields of Justice.