As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Mark Wallace explains how to use a light meter, how it works (incident and reflective meters), and what type to purchase. Use this for still or motion cameras.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

In this Fine Art video tutorial you will learn how to use a Polaris incident light meter. The meter has a power, mode, ISO control and a multi flash exposure buttons. On the side you have the up / down and the trigger buttons. Power on the light meter. Select the mode, say ambient light and then set the ISO by pressing the ISO button and the up/down button. Now using only the up/down button, set the shutter speed. Then place the meter under your chin to meter the light on your face. Press the...

No City would be a pretty awesome name for just about anything. Rock album, memoir, celebrity child, even a Yu-Gi-Oh! card / deck. This video will teach you how to make an awesomely powerful No City deck for Yu-Gi-Oh! and kick some ass with it.

Don’t let cyber bullies push you around, being nasty and spreading rumors about you online. Learn how to fight back against tormenters who hide behind a computer screen. Internet harassment is just as damaging and hurtful as any other form, and proper action needs to be taken to keep the victim safe. Watch this video tutorial and learn how to protect yourself or someone else from cyber bullies,internet harassment, or online rumors.

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Bed-wetting is a part of childhood for most children, and cleaning up after it is pain for parents everywhere. Watch this video for tips on how to clean up the stains from a bed-wetting incident, restoring the normal pee-free ambiance of your home.

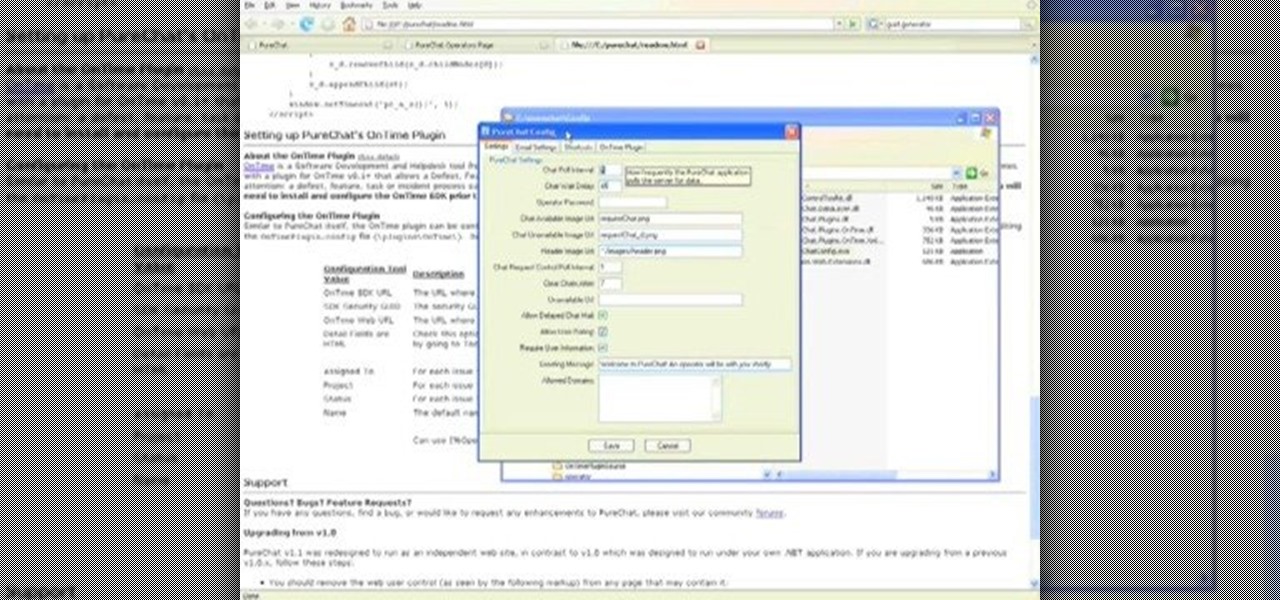
PureChat 2008 ships with an OnTime plug-in that allows you to quickly turn live web chat conversations into defects, feature requests, incidents or tasks in OnTime -- with just a few mouse clicks!

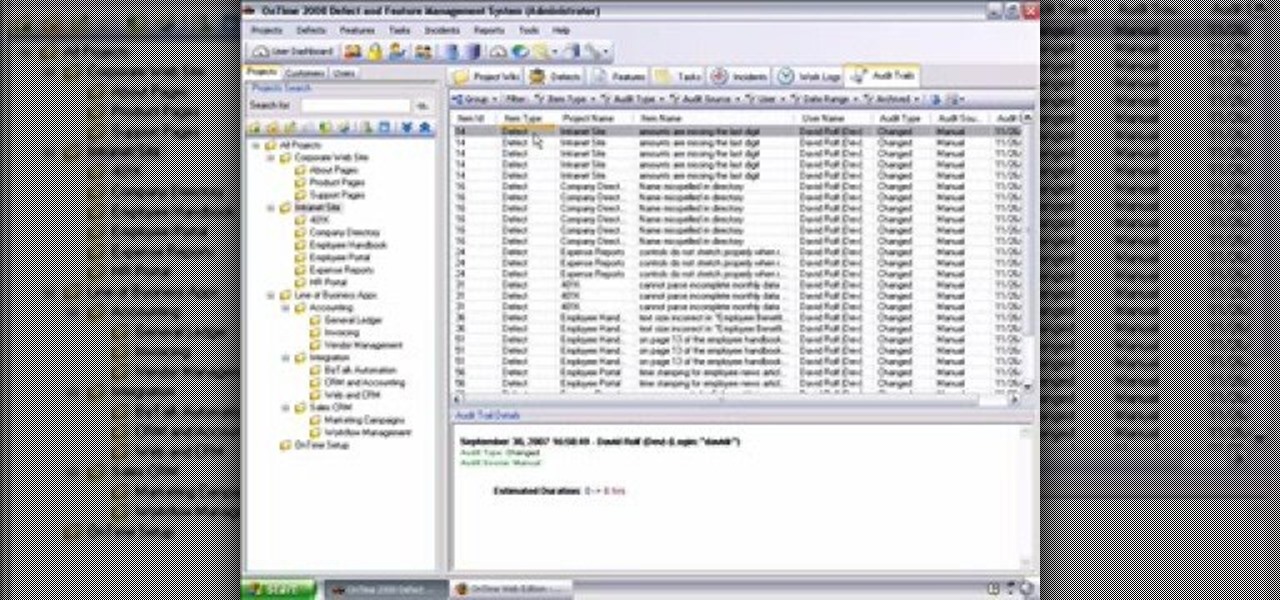
This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite focuses on how you can see the history of your defects, features, tasks, and incidents, as well as project wiki pages. For more information, as well as to get started using the history and audit trails features in Axosoft OnTime 2008, take a look.

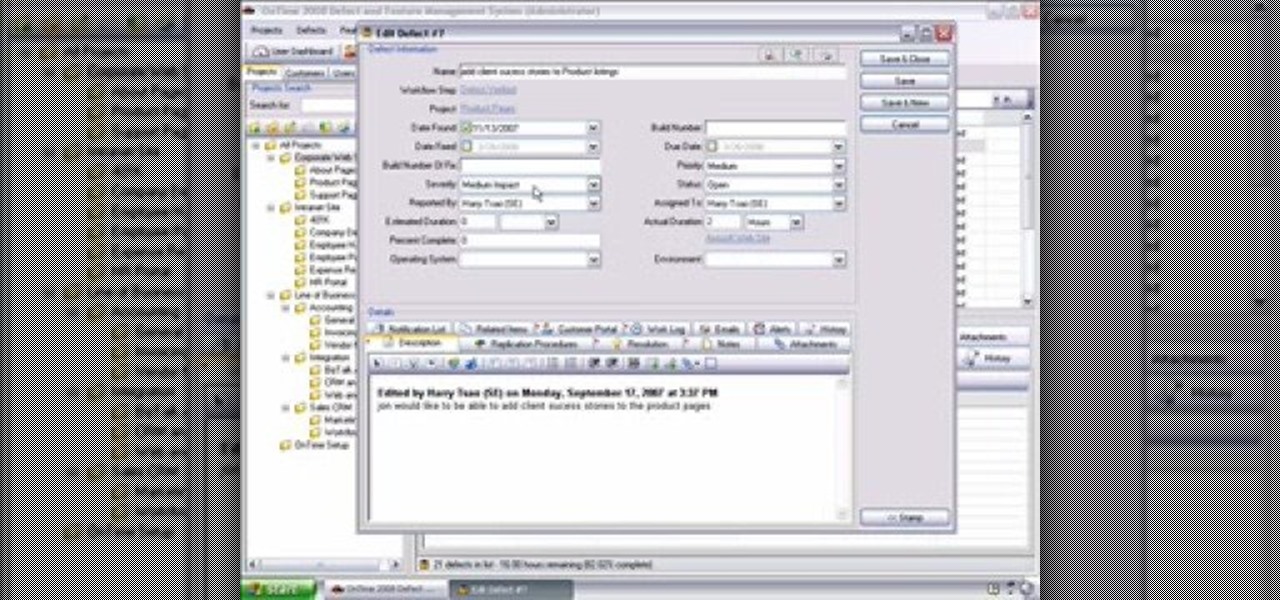
The User Dashboard in OnTime is a great way to look at items across types and edit them. See how to view and search through data regardless of its type (Defect, Feature, Task, Incident) by taking advantage of the User Dashboard. For detailed instructions on using the dashboard, watch this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite.

Worklogs are the time sheets of OnTime. They help track the time your developers spend working on bugs and features, or the time that tech support staff work on incidents. There are several ways to interact with worklogs and this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers them in detail.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

Privacy is important. Whether its a telemarketer or a crazy ex, sometimes you may need to block someone from contacting you. With this tutorial, learn how to get rid of those pesky callers.

Keep warm and stay cute this winter! Make your own pair of trendy cyber fluffies! All you need is some faux fur in a color and style you like, thick elastic, plus a few basic sewing supplies (like a measuring tape and sewing machines).

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Dying to try online dating, but worried that the guy that you're digitally winking at is really a cyber stalker? Then watch this Dating Advice how-to video to learn how to date and decode online dating profiles. With this online dating translator you are sure to keep all the cyber stalkers out of the running.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Sexy Playboy Cyber Girl Dana Dicillo has some advice for you in making your audition video for Holly's 55th Anniversary Playmate Search reality show. If you ever wanted to be in Playboy, you need to watch this.

Yu-Gi-Oh! represented the third wave of collectible card gaming, taking the mantel from Pokemon and Magic and bringing the style of game to a new generation of kids. This video will teach you how to build three awesome decks for one of the video game versions of the game, Yu-Gi-Oh-Gx! Tag Force 2! They are called Cyber End, God, and Blue Eyes respectively.

Most gals put on makeup to fit into the norm: You know, to look professional and "put together" for work or to look desirable on a date or when clubbing with the girls.

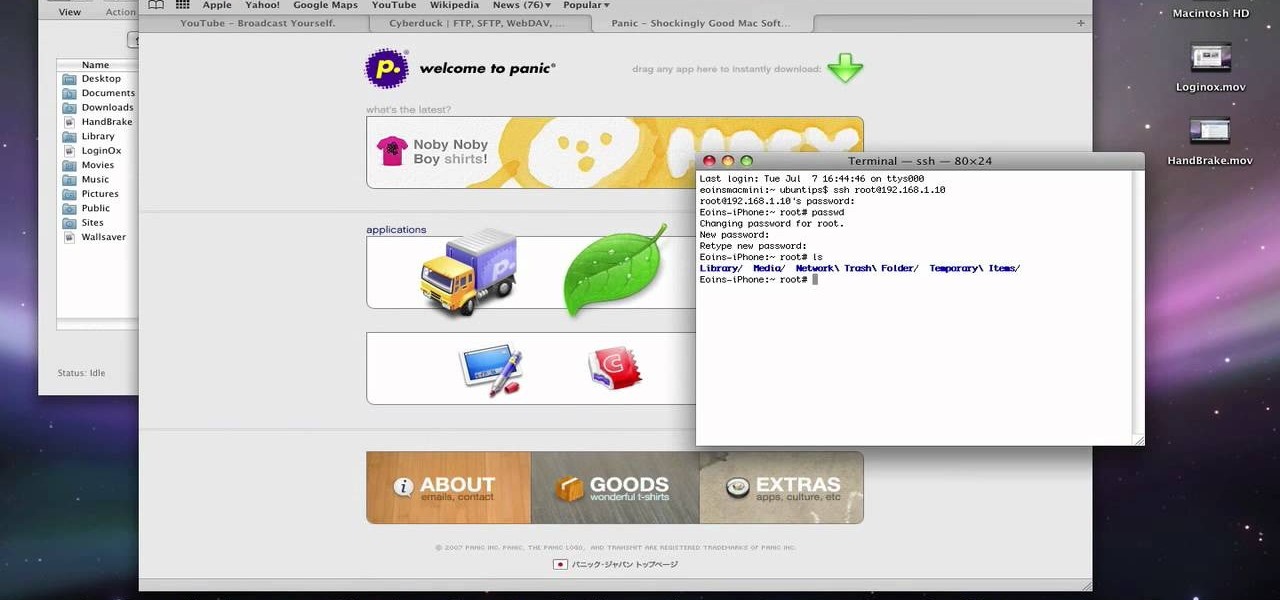
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

Like all famous artists, Frida Kahlo had a very colorful life. Raised in a small town outside Mexico City, she lived through the Mexican Revolution and was struck by a bus as a teenager, an incident which caused a broken spinal column, broken collarbone, broken pelvis, fractures, and a punctured uterus which led to infertility problems later on.

Okay, so the shutter shade trend sort of rode the wave of Kanye West's popularity after he wore it for his video for "Stronger," and then decreased in fan enthusiasm after the Taylor Swift music video incident (your ego is more than your "imaginary friend," Kanye).

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

They say that behind every joke is a half-truth. If that adage itself contains a grain of verity, the Daily Show's satirical Glass piece should raise a few eyebrows amongst the Glass Explorer community.

In this Love Birds tutorial, the counselor, Roger Gil tells how to apologize to a woman. He says that we can apologize to women to reestablish some level of connection that has been damaged due to some incidents. He says that guys should not feel that apologizing is like surrendering. He says this can be an obstacle in the relationship. He says that the first step is to acknowledge the wrong action that we may have done. He says its not worth it to hurt a woman's feelings, and we should immed...

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my rookie hackers!

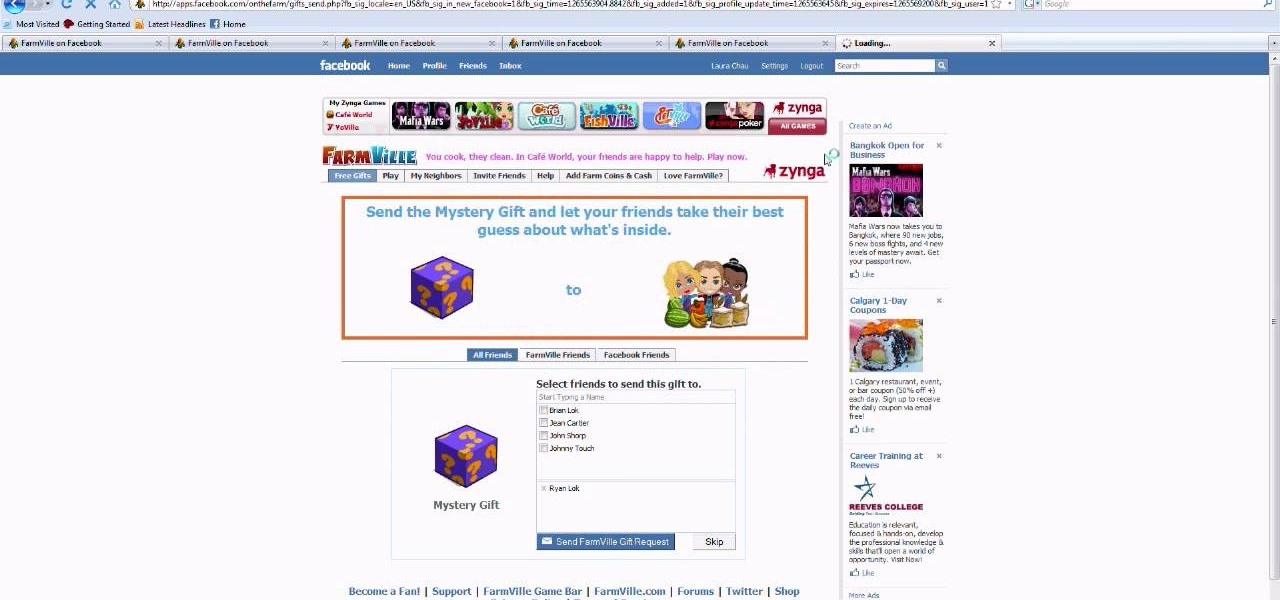
In Zynga's uber popular web game Farmville, you really do receive as much as you give out. Being a good neighbor to your cyber friends means you score lots of loot - via Farmville "gifts" - but you gotta send a few, too.

If you wait for the newspaper to come out with all the Black Friday deals, you'll have lost out on several hours of valuable shopping time! The best way to stay updated this Black Friday and Cyber Monday is by using smartphone apps!

Who likes to buy apps? The answer is no one, of course. Unfortunately, as in life, the best apps and games don't come free. That's why it makes sense to wait until those apps go on sale before handing over your hard-earned cash. And what better day to find discounts in the iOS App Store than Cyber Monday?

The Essential Phone didn't have a hot start when it was released back in August. A delayed release, poor camera performance, and high price tag led many to avoid the otherwise well-received device. But after a few software updates and price drops, it's now a steal of a deal.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...