While Black Friday shoppers found countless deals on all kinds of smartphones, one device was overtly left out of the price cuts — the iPhone X. Walmart was the only store to offer a promotion on the newest Apple device, and even then, it was difficult to find. Cyber Week appears to have repeated recent history, with only one store offering a special on the iPhone X, but it's not Walmart this time.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Cuphead may have taken the indie gaming scene by storm, but its "introduction" to the iOS App Store is what everyone in the smartphone world is talking about. There is no official Cuphead game available for iPhone, and that's what is so surprising — a fake version was approved and released for iOS devices, and at this scale, incidents like this just don't happen for Apple.

Watch this video to learn about screen writing and story structure in order to make your own movie. The "Inciting Incident" is explained— the moment in the first act that propels the rest of the story into motion. As an introduction into creative storytelling: Don't ever allow the inciting incident to be boring.

If you're like me, you probably have a wishlist of Android games you'd love to buy, except the high price tags keep you away. A few bucks can feel like a fortune in the Google Play Store — you just can't bring yourself to pay that much. Well, lucky for you, Google Play has some serious discounts this Cyber Monday. There won't be a better time to buy these games, until next year, of course.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.

Zabernism. What exactly is it? It's a term that originated in 1912, during an incident involving an overzealous soldier who killed a cobbler for smiling at him is Saverne, a small town in Alsace in north-eastern France. The said event ultimately triggered an intervention from the army who took over the power from local authorities.

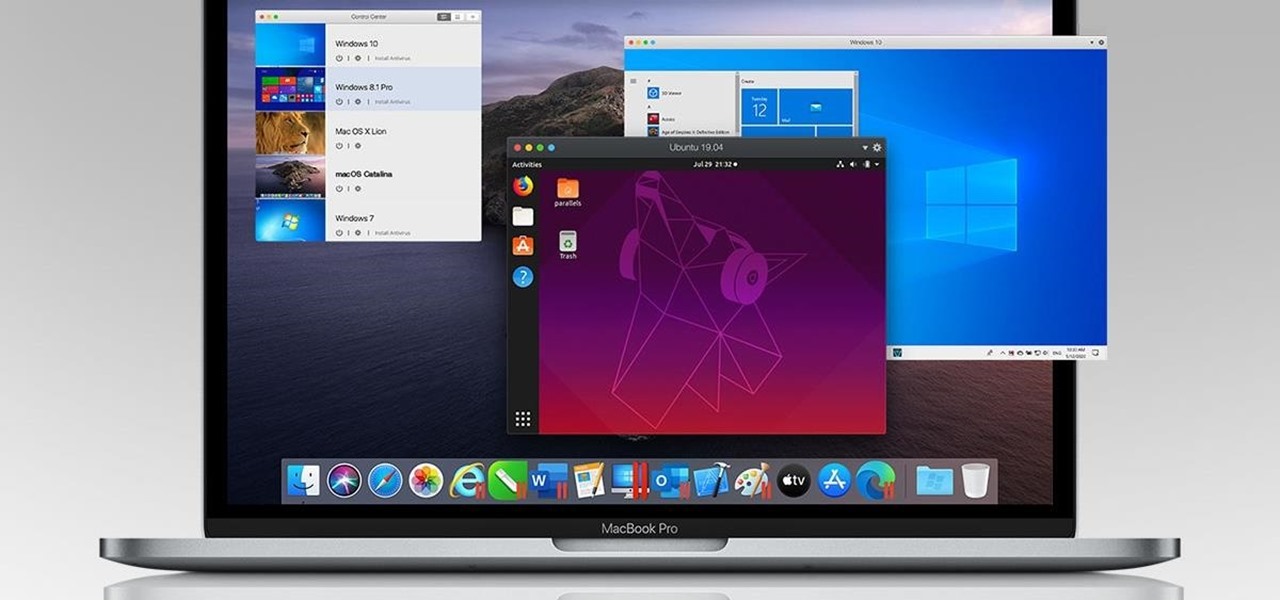
You're on your computer a lot, so it only makes sense that you download the best apps and software for it. The Official Cyber Monday Mac Bundle Ft. Parallels Pro & Luminar 4 is available for only three weeks at an additional 40% off the sale price of $69.99. Just use the promo code CMSAVE40 at checkout.

Apple continues to build its augmented reality hardware and software team in stealth mode. The latest addition comes via the hiring of a former DAQRI user experience designer and VR app developer.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

This how-to video is not for church-going makeup; the makeup look demonstrated is based on the deadly sin of wrath, and is as intensely theatrical as it sounds. The cosmetic products used to create this look are MAC's Full Coverage Foundation, Select Moisture Cover Concealer, Blot Powder, & Peach Invisible Set, Bat Black Cream Color Base, Black Black Pigment, Bat Black Cream Color Base, Dark Soul, & Softwash Grey Pigments, Burnt Burgundy, & Black Black Pigments, Boot Black Liquid Liner, Bat B...

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

This most recent school shooting, one of the worst in history, has devastated our country. That such an act can be performed not by a begrudged child, but by one or more adults, is nearly unthinkable.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Do you love a good mystery? Were you a huge fan of "The X Files" or any other freaky movie or TV show? If you are daring and not afraid of the unexplained, Paranormal Investigator may be the job for you. Check out this video to see if you qualify and exactly how you can get into this spooky field.

In this video, you will be walked through the game Foreign Creature. There are human characters in this one, with word clouds, in an office setting with bulletin board, desks, rolling shelves, and tack boards. In another scene of the game, you will see a hospital setting with nurses, surgery table, patient, medical equipment, and doctors. In this setting, the patient is a foreign creature who blacks out the medical staff and proceeds to stalk the hospital. Police try to capture the humanoid-l...

The end of year surprises keep on flowing from the Plantation, Florida offices of Magic Leap. This time, it's yet another game from the company's old partner Insomniac Games, and it's called Strangelets.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

A 5-year-old girl was injured after the battery in another Samsung phone exploded in China. The Samsung Note 4 was reportedly charging next to the sleeping girl when it blew up in her Guizhou-based home.

CyberTimez and the Wounded Warrior Program, using the Vuzix M300 monocular smartglasses, are teaming up to help supply veterans with little to no sight. The overarching goal here is helping these injured service members to find a new level of independence in a sight driven world.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.

In a world where augmented reality is becoming the hero of the movie marketing, Universal Studios has decided to use the technology to reinvent the traditional movie trailer, a time-tested tactic of film promotion, in support of the forthcoming Robert Zemeckis film, Welcome to Marwen.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

If you live in New York City and are itching to sell your Yeezys, you're at risk of falling victim to thieves. A devious duo is searching Facebook to find people selling the popular sneakers and then robbing them at gunpoint when they meet up in person.

What companies do you think have a unique and compelling take on social media? Wendy's is certainly confident, to say the least. But Lufthansa Airlines is taking a different approach than most — and it seems to be working — as they give passengers a look behind the scenes through Snapchat Stories.

Oh, Waze—you know, that Google-owned traffic navigation app that tempts drivers into stopping at local food joints like Dunkin' Donuts and Taco Bell? Well, now you can even order a large iced coffee through the app before you even arrive at a fast food hotspot.

Welcome back, my hacker novitiates!