Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

If you missed out on Black Friday this year, you've got a second chance at saving some big bucks on apps, mobile devices, HDTVs, and other tech. See below for all of the hot Cyber Monday deals from Amazon, Apple, Google, Microsoft, and other online retailers. This list will be continuously updated throughout the day, so bookmark it to stay up to date on all the of Cyber Monday discounts.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Get your holiday shopping done early with these deals on software, e-learning classes, and gadgets. These Cyber Monday goodies include something for everyone at a can't-miss additional 20–70% off sale prices.

Although all signs points to Microsoft releasing a new HoloLens in the coming days, the company is nevertheless looking to distribute its augmented reality apps to other operating systems.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

After watching Samsung's exploding phone fiasco this past year, I took comfort knowing that the likelihood my iPhone would suddenly combust was slim. However, after hearing about a recent incident in Wisconsin, iPhone owners may have reason to worry.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

I record close-cropped videos and take macro still shots with my smartphones on a daily basis, so as you would expect, I spend a lot of time cleaning these devices. Over the course of a couple years, I've fine-tuned my cleaning regimen, and at this point, it's down to a near-science.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

Google largely helped to pioneer the concept of a steering wheel- and pedal-free self-driving experience when it began testing its Firefly pod-like vehicles a few years ago.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Thanksgiving.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.
Welcome back Hackers\Newbies!

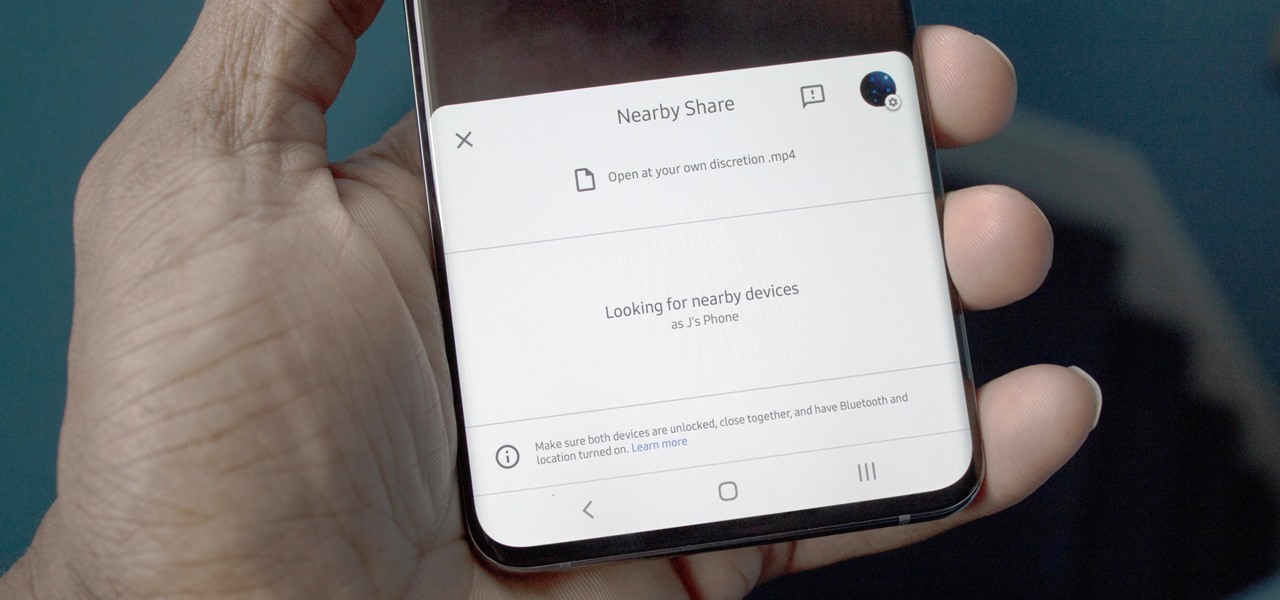
Android has finally got a proper alternative to Apple's AirDrop. With a few touches, Nearby Share lets you send files, links, and even tweets to Android, Windows, macOS, ChromeOS, or Linux. But AirDrop has not been without its share of issues, and thankfully, Google has learned from them.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.