When conducting mobile convert surveillance, you will be following someone and it is important to dress appropriately for the environment and carry your surveillance equipment in a bag that will fit into the scene.

When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

If you are law enforcement or find yourself in an emergency situation you may need to know how to properly conduct surveillance in a rural area. You will have to gather information without being scene and will need different techniques when out in the wilderness.

You can use surveillance skills to pursue a career as an investigator or to spy on whoever you like. You will need to have a mobile means of making observation and this might include things like pen and paper, camcorder or camera.

This walkthrough shows you how to beat the Temple Surveillance mission (level 10) on Perfect Dark Zero for the XBox 360.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

Innovation is a lightning bolt that every company would like to bottle. Doing so in a corporate environment is nearly impossible. This video features a business expert outlining some tips for managing innovation and innovative ideas in your business, nurturing those ideas into profitable new services or products that your business can offer. It includes defining roles for different people involved in the innovation process and what steps to take in the innovation process.

This Photoshop tutorial will show you how to turn a photo into a surveillance camera screenshot.

No City would be a pretty awesome name for just about anything. Rock album, memoir, celebrity child, even a Yu-Gi-Oh! card / deck. This video will teach you how to make an awesomely powerful No City deck for Yu-Gi-Oh! and kick some ass with it.

Don’t let cyber bullies push you around, being nasty and spreading rumors about you online. Learn how to fight back against tormenters who hide behind a computer screen. Internet harassment is just as damaging and hurtful as any other form, and proper action needs to be taken to keep the victim safe. Watch this video tutorial and learn how to protect yourself or someone else from cyber bullies,internet harassment, or online rumors.

Remember how the bad guys in Scooby Doo would always use cut-out portraits to spy on people through walls? Well, unless your landlord is super cool, you probably shouldn't start cutting holes in your wall just yet, but you can make a higher tech version, thanks to NASA employee Mark Rober. Mark used a cheap picture frame and a portrait with the eyes cut out to make the "Scoob Cam," which also doubles as a surveillance device. He used an iPhone and an iPad to start a FaceTime chat, then taped ...

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

This video shows how to setup and use your DynaSpy wireless video surveillance camera.

There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're not the one that's supposed to be eavesdropping with them.

Keep warm and stay cute this winter! Make your own pair of trendy cyber fluffies! All you need is some faux fur in a color and style you like, thick elastic, plus a few basic sewing supplies (like a measuring tape and sewing machines).

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

As a multitasker, I've embraced the hustle and bustle that has filled my life. I'm constantly doing several things at a time, while looking for shortcuts to finish all of these things quicker than before. I brush my teeth with my cell phone in hand and drive to work with breakfast in mouth—I spare no time. Well, now there's an application for the Mac users among us that can help take some of the stress out of doing a thousand things at once.
New York (CNN) -- New York City police didn't violate New Jersey state laws when they carried out surveillance programs of Muslim-owned business, mosques and university student groups, according to a Thursday statement from the New Jersey attorney general's office.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

A former decorated undercover FBI agent, Mike German, explains how the national security state, in league with local law enforcement, is secretly targeting Americans for political views and activities perceived as a threat to the political establishment. » Former FBI Agent: Surveillance State Trashing Constitutional Protections Alex Jones' Infowars: There's a war on for your mind!.

The NYPD says it will launch an all-seeing "Domain Awareness System" that combines several streams of information to track both criminals and potential terrorists.

Google Instant is one of Google's many search innovations, this one causing search results to emerge continuously below the search bar as you type. This can allow you to find more search results faster, and this video wills show you how it works, including how to turn it off if you decide you want Google to wait until you're finished typing before searching.

Dying to try online dating, but worried that the guy that you're digitally winking at is really a cyber stalker? Then watch this Dating Advice how-to video to learn how to date and decode online dating profiles. With this online dating translator you are sure to keep all the cyber stalkers out of the running.

Knitting when you're sitting at your table is usually a cinch, since you can rest your elbows on the table when you're tired and also place your knitting needles and yarns closeby within reach. But staying in one place all day long can be boring.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Sexy Playboy Cyber Girl Dana Dicillo has some advice for you in making your audition video for Holly's 55th Anniversary Playmate Search reality show. If you ever wanted to be in Playboy, you need to watch this.

Yu-Gi-Oh! represented the third wave of collectible card gaming, taking the mantel from Pokemon and Magic and bringing the style of game to a new generation of kids. This video will teach you how to build three awesome decks for one of the video game versions of the game, Yu-Gi-Oh-Gx! Tag Force 2! They are called Cyber End, God, and Blue Eyes respectively.

Most gals put on makeup to fit into the norm: You know, to look professional and "put together" for work or to look desirable on a date or when clubbing with the girls.

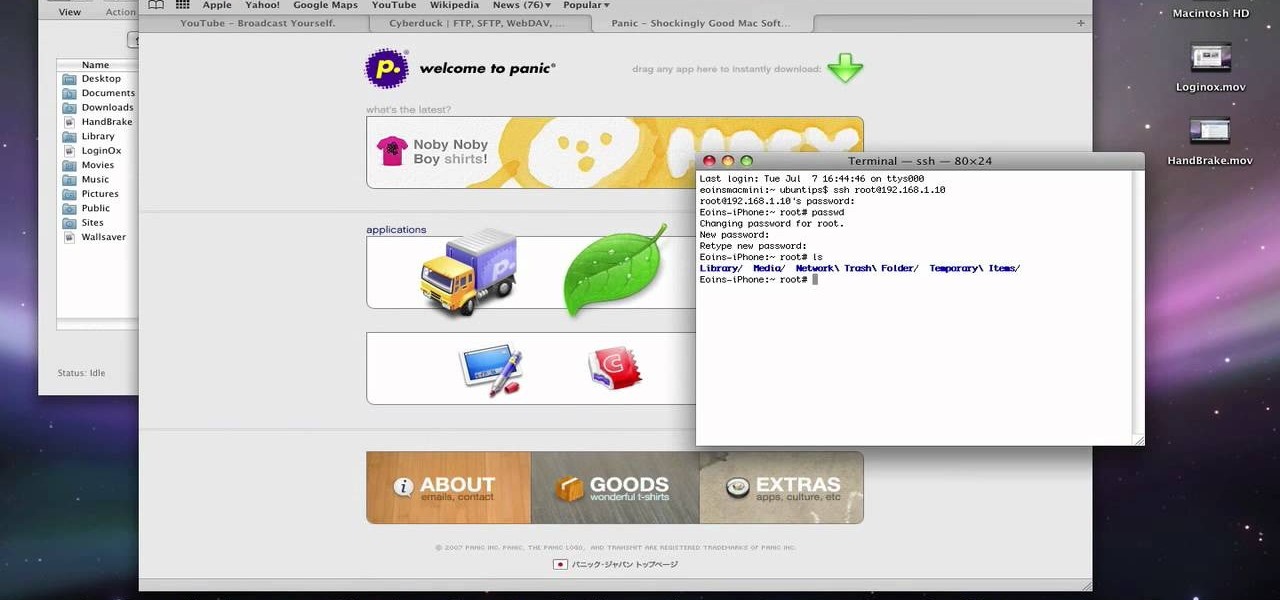
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

This is a video walkthrough of the "Prologue: Financial District" level in Mirror's Edge for the Xbox 360.

This is a video walkthrough for Chapter 1: Flight (PT. 1/2) in Mirror's Edge for the Xbox 360. The game has a realistic, brightly-colored style and differs from most other first-person perspective video games in allowing for a wider range of actions—such as sliding under barriers, tumbling, wall-running, and shimmying across ledges—and greater freedom of movement, in having no HUD, and in allowing the legs, arms, and torso of the character to be visible on-screen.