Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.
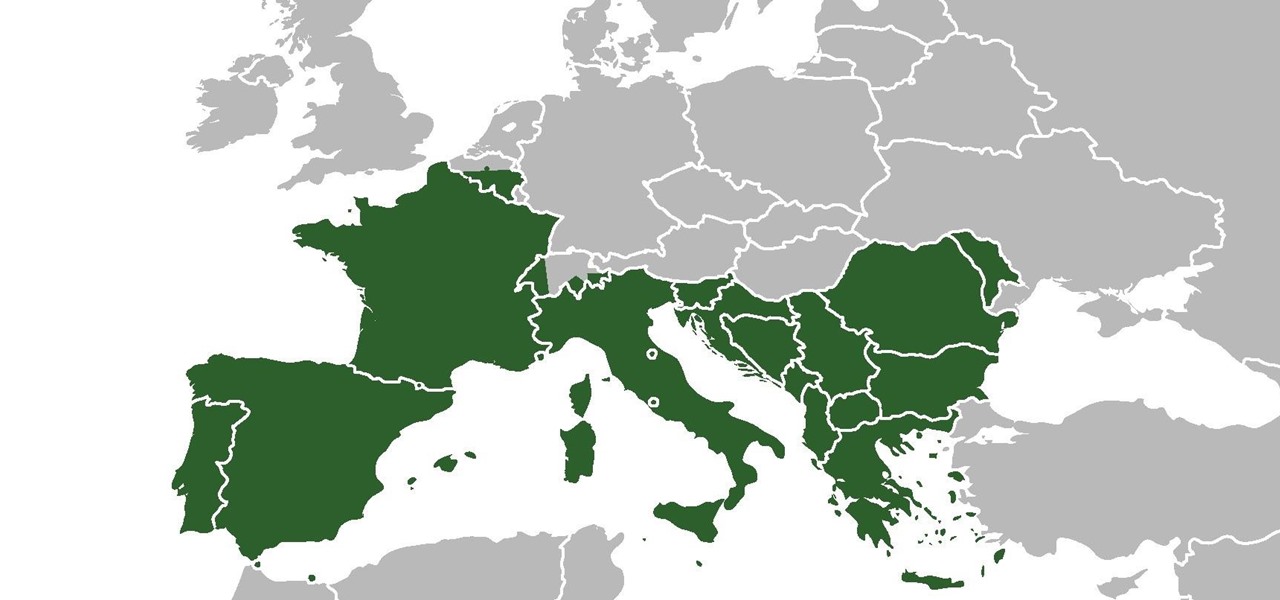
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Ok, here's the deal.. you take a video camera and just record about 5 minutes of a view similar to the pic (like where you would place a surveillance camera in a room). This bathroom has to be at a location where everybody will be gathered around watching TV etc... Sooo, when someone goes to the restroom, you playback the video you recorded earlier (hiding all playback equipment, obviously), and after the person is in the bathroom, and the tape is rolling, have everyone in the room start laug...

It's Monday, which means once again, it's time to highlight some of the recent community submissions posted to the Math Craft corkboard. In this post, we'll also make a flexagon, which is a type of transformable object.

Google+ is the greatest social network to emerge since Facebook annoyed everyone into joining, but that doesn't necessarily mean that our relationship with it is all rosy. Although Google+ has amazing innovations, like hangouts and circles, users are spending a lot of time begging for core features that take what seems to be an eternity to emerge.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to WonderHowTo's first Weekly Community Roundup! Each week we will be featuring the best projects from the community, as well as ongoing challenges and activities you can partake in. WonderHowTo is made up niche communities called Worlds, so if you've yet to join one, get a taste of what's been happening this week in the highlighted Worlds below...

The Tokyo Game Show (TGS) is the biggest video game expo in the most game crazy country on Earth. It is kind of a big deal. As such, their "indie" game showcase/contest Sense of Wonder Night (SOWN) is a major opportunity for developers of all shapes and sizes to showcase their work to important industry leaders and expo attendees. 2011 will be SOWN's fourth year, and it began accepting submissions yesterday.

Real-time strategy (RTS) was the most popular genre in PC games at one time. It put Blizzard on the map—one of the biggest game developers in the world. And it buried the once venerable turn-based strategy genre, the only survivor being the Civilization series. But like hair metal in the late ‘80s, RTS reached its saturation point. Many bands (games) were too similar and used ornamentation over innovation. Suddenly, the fans left. From ’95 to ’03, Command & Conquer releases were more like new...

In the past 25 years, there have been five generations of home video games systems. Since Nintendo changed the world by releasing the NES in 1987, there has always been at least two consoles competing for dominance in the wild west of the games industry. This competition— coupled with rapid advancements in technology—has led to a new generation of battling systems coming out every five years, like clockwork.

On a Wednesday evening when friends are going to a movie or out to dinner, you’re at the dojo training.

The much-hyped Apple event is now history, and we finally know what the Cupertino tech giant had up its sleeve: new iPhones.

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

If you've been reading, watching or listening to the news, you sure know about the Trayvon Martin case. If you visit this site often, you may also have noticed that I've not put up any news on this case. I have my reasons. And this post will describe why.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

After a postponement of the Summer Olympics for a year due to the COVID-19 pandemic, Tokyo is set to host the games this summer, despite a surge in cases in the city.

The recent release of the Looking Glass Portrait has gotten the public excited about personal displays that simulate 3D visuals, but in the public display marketing space, this is an area that has already received a lot of attention.

The electric vehicle space is where a lot of the most cutting-edge technology is used to push vehicles forward (the best example being Tesla).

In recent years, the tech innovation space has been dominated by the US and Asia, with Europe weighing in, but still being mostly lauded for its art history and architecture.

The year 2020 sparked a trend of people moving out of big cities, with some opting to buy mobile homes and vans to travel rather than be cooped up in a tiny apartment during quarantine.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

At first glance, it may not sound like there's much value in doing a crossword puzzle in augmented reality, but The New York Times has managed to revamp the pastime as an immersive game.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.