After testing the waters with a few pop-up stores along the West Coast earlier this year, North is bringing its smartglasses to more cities across the US and Canada.

Location-based AR game Ghostbusters World is creeping closer to launch, and developer FourThirtyThree has released some new gameplay footage and a trailer to capture the interest of the living.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

Kitten Planet, a spin-off company that grew up in Samsung's C-Lab incubator, has developed a connected toothbrush that teaches and motivates children to brush their teeth better via augmented reality while tracking their performance.

Live theater doesn't typically benefit from the kind of computer-generated special effects that big-budget Hollywood blockbusters deploy, but that could change soon thanks to Microsoft's HoloLens.

New York City may not be the friendliest city, but with the apps Via and Curb now letting users ride-share in the city's yellow taxis, New Yorkers can expect to snuggle up close in the back of a cab next to complete strangers. That's right, get ready to feel the love.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!)

We at Food Hacks Daily freakin' love Halloween—it's the perfect time for weird and creepy food. The gruesomer, the better.

Ah, ginger. From stir fry to smoothies, ginger is a reliably sharp and refreshing flavor that adds zing to everything it touches. It may be a pain in the ass to remove the skin from ginger (or not), but the zest it brings to food is well worth the trouble. Don't Miss: How to Brew Your Own Ginger Beer Like a Boss

It's fall—so whether or not it's cold in your part of the world, it's time for apples and anything apple-related. (Please, don't get me started on pumpkin things. Seriously.)

A whole grilled pineapple is the perfect party dessert. It's beautiful, provides a natural centerpiece before you eat it, and can be sliced right on the spot and served with a dollop of ice cream. (Fresh mint leaves and a splash of liqueur on top taste pretty good, too.)

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

Pain is, for the most part, unavoidable when you stub your toe, break your arm, or cut your finger open. It's instantaneous and, in some cases, long-lasting, but it only feels as bad as you want it to. Yes, that's right—that pain is all in your head.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.

We're living through the technological revolution, and while devices like the iPhone 6 or Galaxy S5 have made life easier and more entertaining, it's possible that sometimes our smartphone usage can become uncomfortably excessive. In your own experience, think about how anxious and off you feel when you leave your phone at home—Cell Phone Separation Anxiety or Phantom Phone Vibrations shouldn't be a real thing that we deal with.

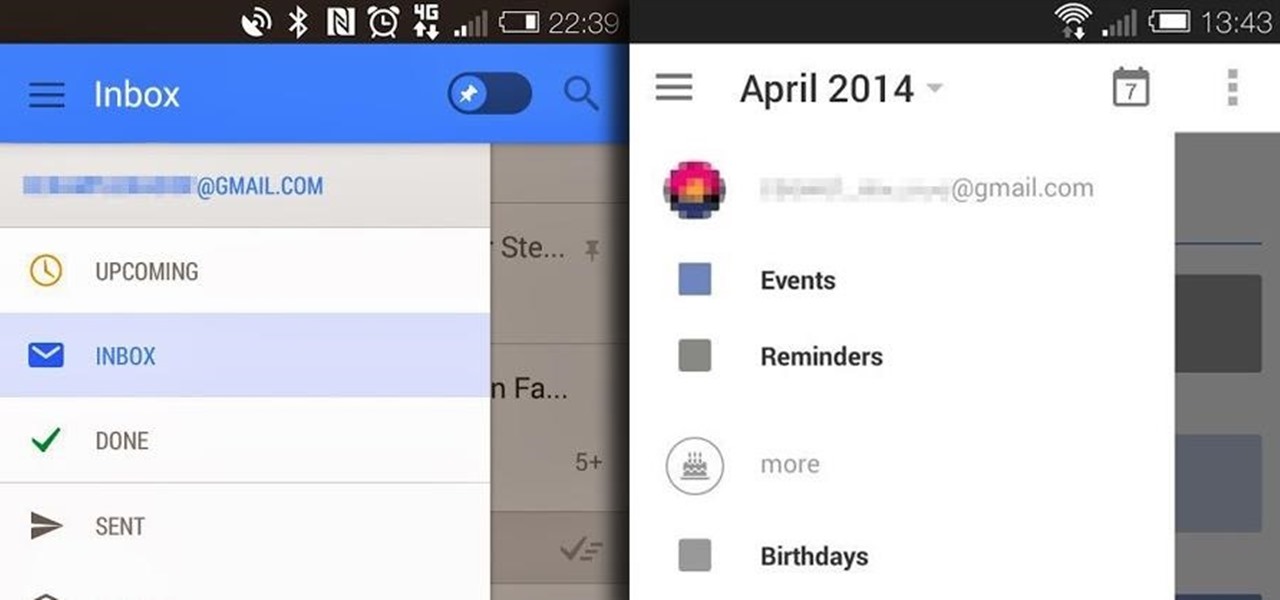
Google I/O may still be a couple of months away, and although we don't expect anything groundbreaking—no new Android versions, just fixes to KitKat—we could be treated to some new apps. No, not Pokémon inspired Maps, rather new versions of Google's Calendar and Gmail apps.

The first thing I do when I wake up in the morning is run to the kitchen to make coffee, and I know I'm not the only one. According to a survey by the National Coffee Association (yes, there's such a thing), 83% of Americans drink coffee, and I'd bet most of that consumption happens in the morning.

Applications, features, and software running in the background of your Samsung Galaxy Note 2 can drain a significant amount of battery power, even when your smartphone isn't being used. For this reason, smartphone carriers and developers suggest that you turn off Bluetooth, Wi-Fi, and other battery hogging features when they're not being used.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Even though I am not cool enough to use Instagram on a daily basis, I still try to stay in the loop. I did take photography in high school, so I know a thing or two about picture taking. I just can't seem to find the motivation to take a picture of random crap during my daily routine, but I guess that's why I'm Instalame.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

The Motorola Droid is the reigning king of the Android family, but it's getting a little old and you're probably looking for a way to improve your phone's performance if you own one. Why not root the dang thing and install a custom ROM on it so it'll at least be organized the way you want it to be! This video will show you how to install custom ROM's (basically phone UI's) on a rooted Motorola Droid phone, allowing you nearly limitless customization options for your awesome phone. The ROM in ...

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

What do you do when your favorite new car is still two years away from hitting the road? Look to augmented reality, of course.

Augmented reality as a storytelling medium can do some extraordinary things words and images alone can't convey -- such as transporting readers 400 years into the past.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Researchers at Disney have demonstrated the ability to render virtual characters in augmented reality that are able interact autonomously with its surrounding physical environment.

It's fitting that students at the University of Washington can catch a glimpse of the new, 135,000 square-foot computer science building in augmented reality before construction is completed.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

According to Dr. Lindsey Fitzharris of The Chirurgeon's Apprentice, hospitals during the first half of the nineteenth century were known as "Houses of Death."

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.