Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Welcome back, my greenhorn hackers! I've been writing these Linux tutorials in an attempt to fill the void in the education of some aspiring hackers into the Linux operating system. There is a lot to know, and in this tutorial, we'll look at Linux file permissions. Step 1: Checking Permissions

Despite what we all argued in school, math does come up in daily life. When those dreaded fractions are staring you in the face remember these steps and you will be multiplying in no time. Practice always helps.

One can easily get rid of acne scars without surgery by means of following steps. Identify the type of acne scars you have. See a dermatologist who can tell the difference between types of scars. For example, scars may be classified as ice pick, boxing, rolling or hypertrophy scars. Not every nonsurgical removal techniques will work with each type of scar. Get a chemical peel. A solution is applied to the skin which causes the top layer to peel off. This encourages new skin growth. Peels are ...

The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

There are a variety of ways to speed up your body’s ability to heal. Things like keeping the incision clean, resting, nutritious foods and physical therapy will get you feeling strong quickly. Avoid negativity, as it may actually slow down your recovery. No one likes to be laid up in bed after surgery. Follow the advice on your “get well soon” card and be back to your old self in no time.

Staccato is Italian for articulated distinctly, with a separation between notes. In this tutorial you will learn how to play the staccato bowing technique on violin. Start slowly with a nice "pop" or collé sound at the beginning of each up bow stroke. Build up your speed faster every day and track your progress daily in the Practice Journal. The stacatto bow technique improves control over the entire bow and prepares you for pieces that use staccato. Pull to the tip on each down bow stroke. U...

Apple's newest software update, iOS 17.5 includes one killer new feature for people who like word games: another lexical challenge to complement the crossword puzzles that Apple News already has.

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.

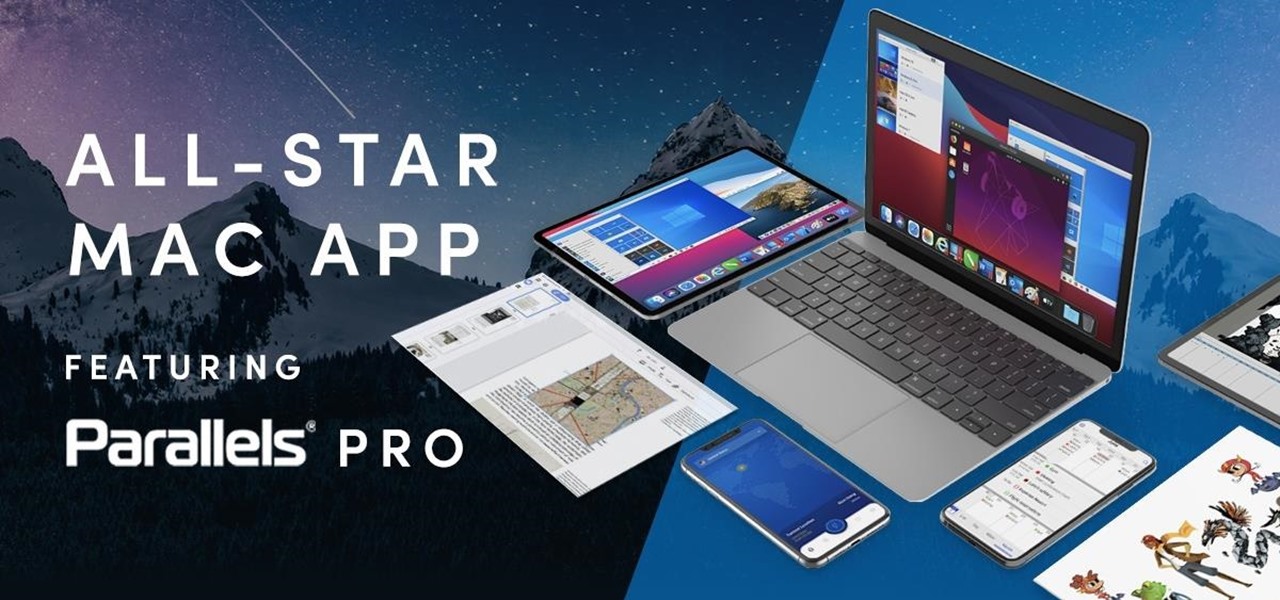
As great as Macs are, they're often limited by the apps you have installed. Your computer might have the processing power to render a 4-hour movie in the time it takes you to have lunch, but if you don't have the right apps, you're not putting all that power to use. The All-Star Mac Bundle Ft. Parallels Pro gives you access to programs that will put your Mac to use and give you the best functionality out of it, and right now this whole bundle is on sale for $49.99.

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

If you want to quickly pick up a new skill over the holidays, learning to build your own Apple apps is one of the most impressive ones you can work on. This complete course bundle on SwiftUI and iOS 14 will have you submitting your own iOS apps to the App Store in just two weeks. Right now, The iOS 14 & SwiftUI Bootcamp Bundle is on sale at 95% off, for just $24.99 (regular price $600).

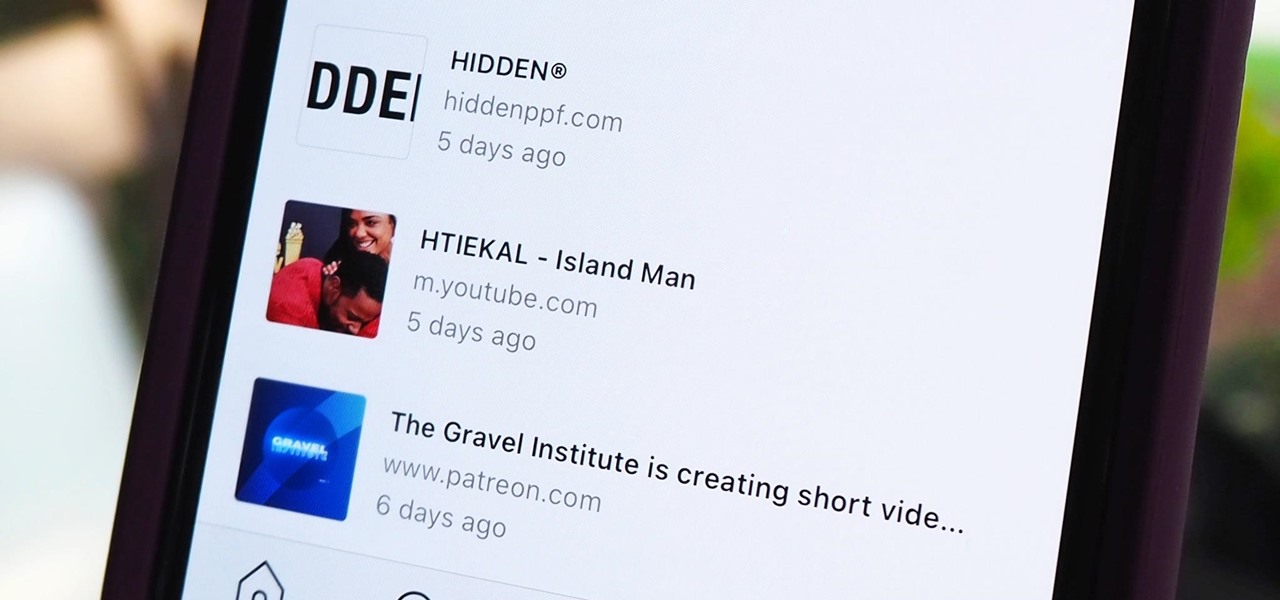
Instagram isn't as link-friendly as other social media platforms like Twitter and Facebook. Still, when you do find and open a link, whether it's for a petition or a product, you may want to find it again later. That's why Instagram keeps track of every link you've ever opened. That way, if you ever need to revisit a webpage, you don't have to find the original post or account from last time.

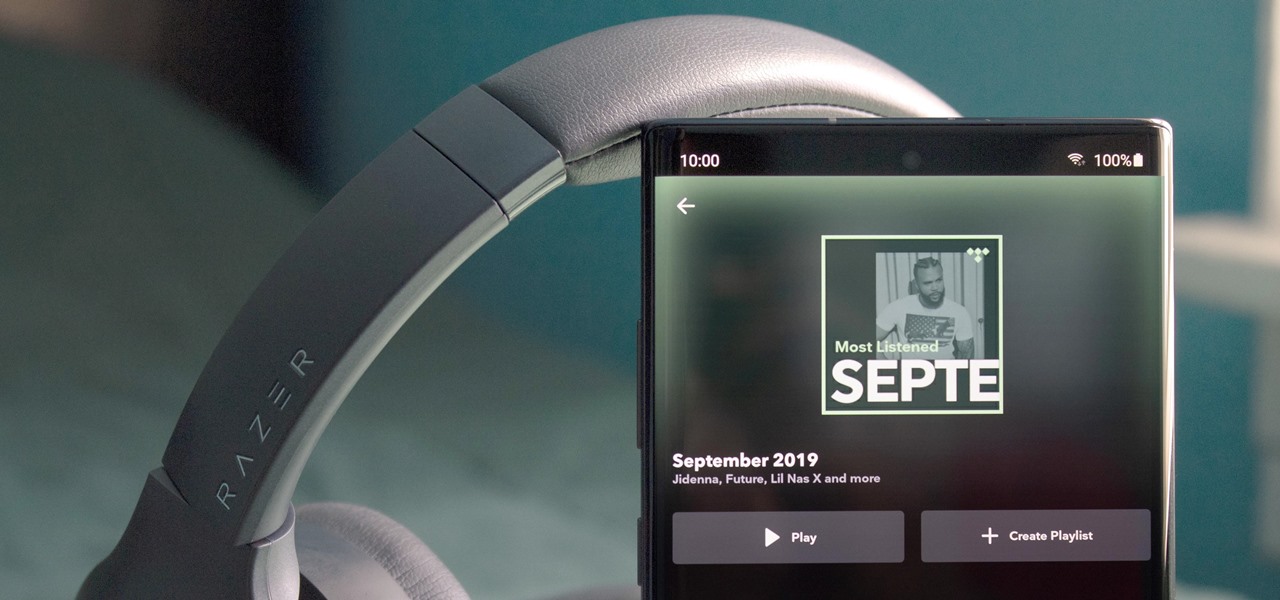
It is surreal how your playlists change over time. A song you loved in January will be forgotten about in May. With hundreds of singles from different artists coming out daily, it is easy to get distracted. Tidal understood this problem and created a solution called "History Mix."

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.

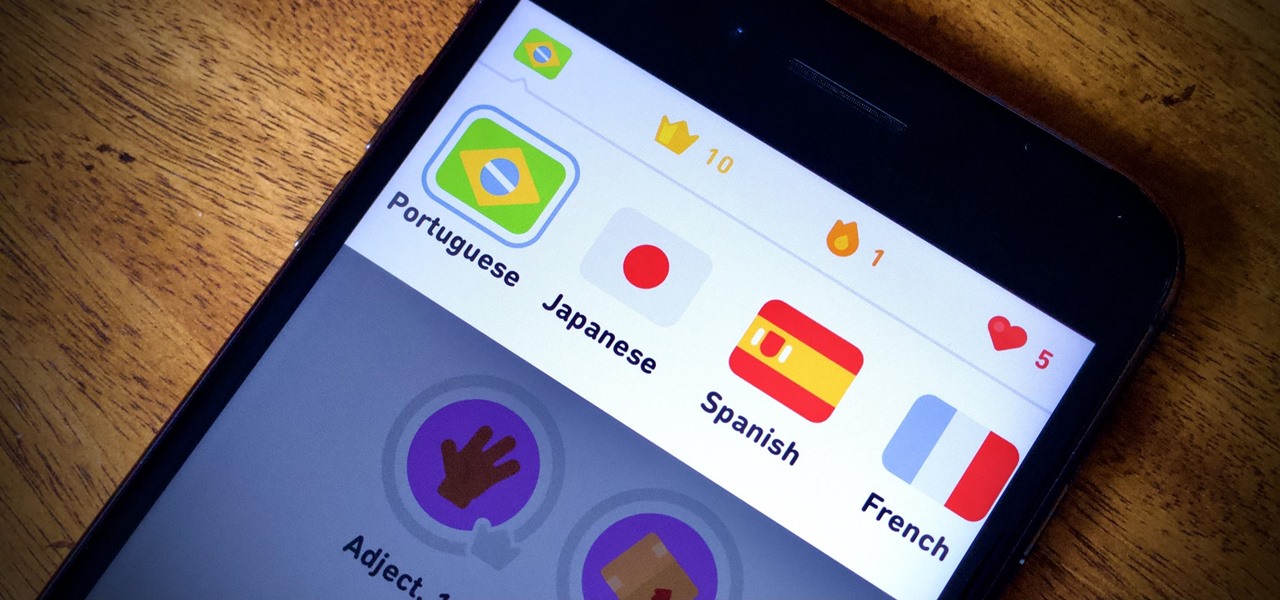
There's only so much Netflix and TikTok a person can take in quarantine before they've had enough. We've only just started our stay-at-home lifestyle, but already TV and movies are getting old. The COVID-19 lockdown doesn't just have to be a mindless watch party, so why not take the time to learn a new language?

Spotify launched an experimental feature in early-2018 called Spotify Voice, a voice assistant that lives right in the app. It lets you speak to quickly find and play your favorite songs, albums, artists, videos, and podcasts on the music streaming service. Although the feature was initially only available on iOS, it's been ported over to Android so that anyone can take advantage of it.

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

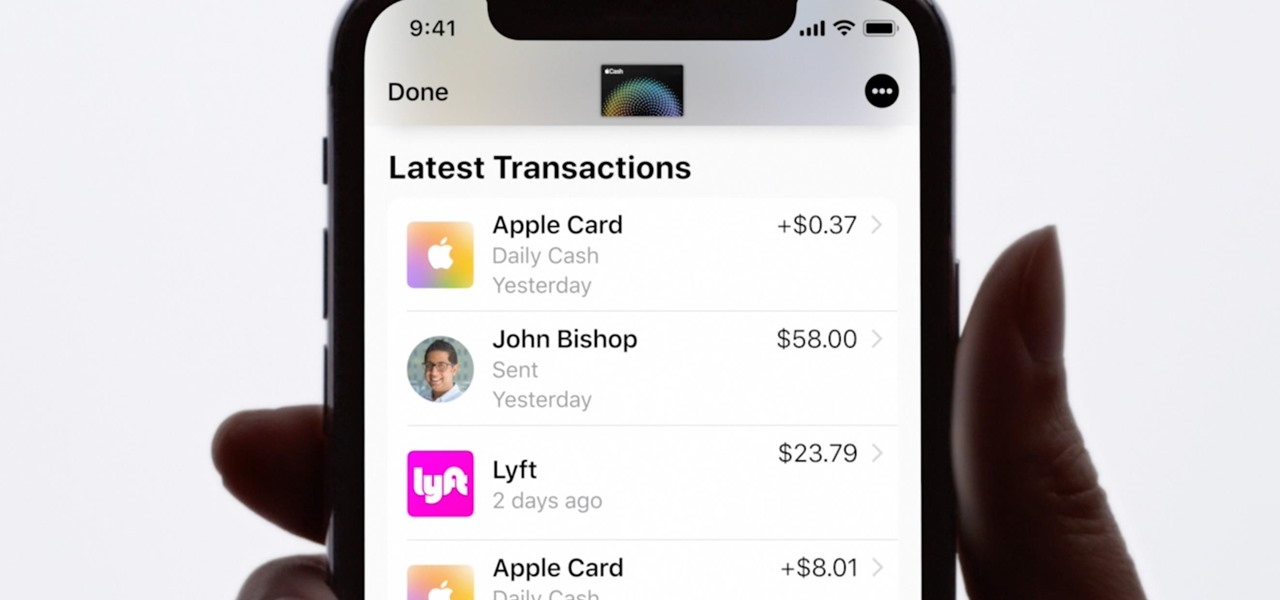
Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.