If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

When temperatures drop and hit new lows during the cold, winter months, it's hard not to crank the heat up. That means increased energy bills each month, no matter if you rely on gas, electric, or another fuel for heating.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

There are countless methods and cleaners aimed at eliminating stubborn stains from everything to clothing, carpet, and furniture. But completely removing every last trace of a stain doesn't require an arsenal of chemical cleaners and repeated cycles in the washing machine. Most stains can disappear in a matter of minutes with a dose of alcohol.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

Whether you drop your iPhone into a toilet or your dog's water bowl or regularly take it into the shower or pool, water will likely become nestled inside its speaker grilles. Water exposure causes audio playback through the speakers to soften and sound muffled, and getting that water out is no easy task. Luckily, there's an app for that.

The last few weeks were fairly busy in the realm of augmented reality and remote meetings developments. Most of that activity was generated by some mammoth announcements from Snap and its Spectacles AR smartglasses, and Google, with its Project Starline experimental holographic video conferencing system.

If you're getting or already have a new iPhone 12 or 12 Pro, its big-ticket feature is MagSafe, something you'll definitely want to explore. While the technology is new to iPhone, Apple used the MagSafe name for its magnetic charging connectors on older MacBook models until USB-C replaced it. Apple's reenvisioning of MagSafe for iPhone is completely different and much more useful.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.

The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Being able to sleep deeply and fully is one of the foundations for real health. When you go without it, you feel subhuman and incapable of dealing with the world—just ask a student who's had to pull an all-nighter or the parents of a newborn. In fact, many studies have shown that lack of sleep or irregular sleep is linked to acne, weight gain, and depression.

Thought I would cross-post a piece I did a while ago.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

Now that Vision Pro, Apple's mixed reality headset, has been announced, Apple can free up some R&D resources to commit to its upcoming foldable iPhone, which has been rumored for just as long as Vision Pro has. Will it be a flip-style or a larger foldable? Let's see what all the industry experts and Apple leakers have to say.

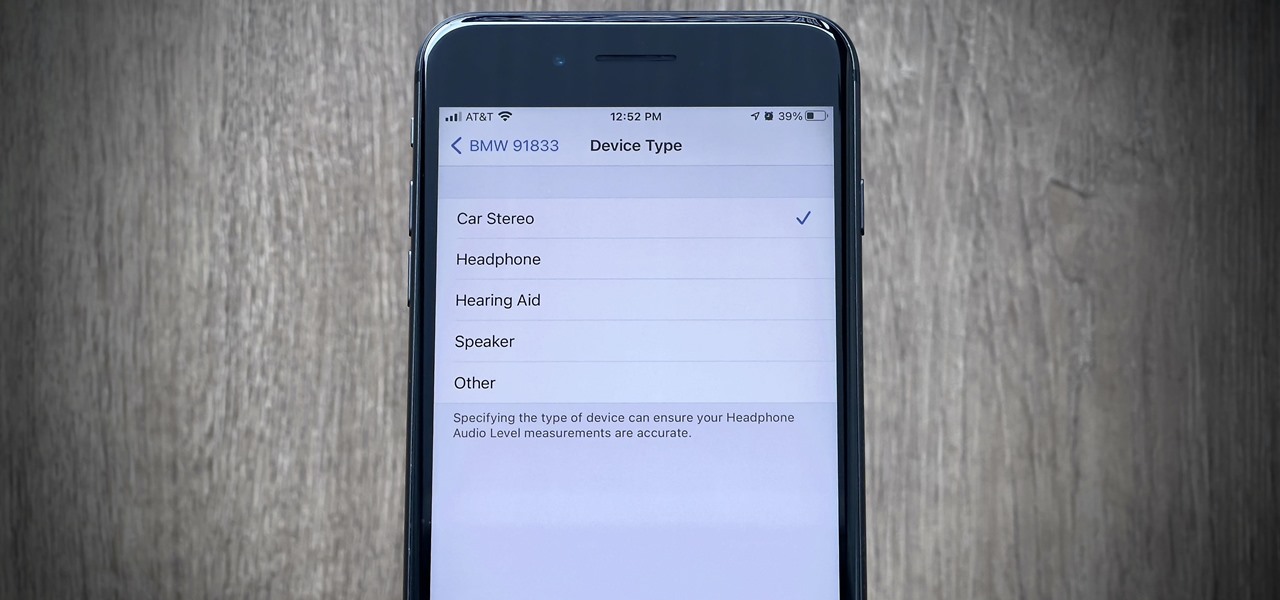
Remember when water and iPhones couldn't mix? Pools, tubs, and toilets would suck down the working iPhones of clumsy and careless owners and spit out expensive paperweights like they were nothing. Times have changed, however, and the newest iPhones can take a swim without fear of certain death. But a dip in liquid can still cause muffled music and audio from the speakers.

Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to your iPhone the next time it happens.

Outside of iPhone releases, software updates are arguably the most exciting aspects of iOS life. It's like Christmas morning when your iPhone installs an update, as you dive through your device to find all the new features and changes Apple thought to include. With iOS 14.4, there are at least 10 such new additions just waiting for you to explore.

The new iPhone 12, 12 mini, 12 Pro, and 12 Pro Max may seem like minor updates to the iPhone 11 lineup, but there are quite a few features that make them worth the upgrade. Apple has done a good job of highlighting all of those features, but some didn't get all of the love they deserved.

Making the jump from an older iPhone, or even an Android phone, to the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max can be a big one. It's not just the change of a new smartphone — it may have had a huge impact on your wallet too. So whenever the device goes berserk, is unresponsive, or won't turn on, it's understandable to be worried. But DFU mode can help whenever you're in a dire situation.

Social media apps like Instagram, Snapchat, and TikTok have plenty of editing tools that go beyond the basics, but there are still a lot of things they can't do. So if you want to apply interesting, unique effects to your photos and videos for social media, you'll need to add some other apps to your iPhone's arsenal of tools.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

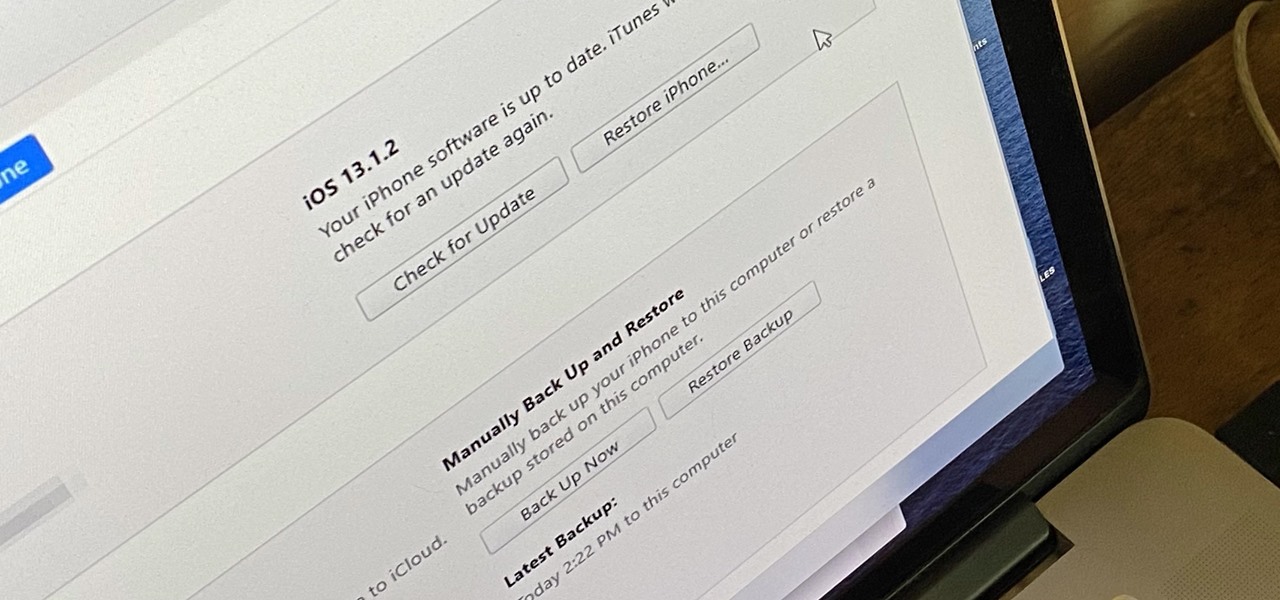
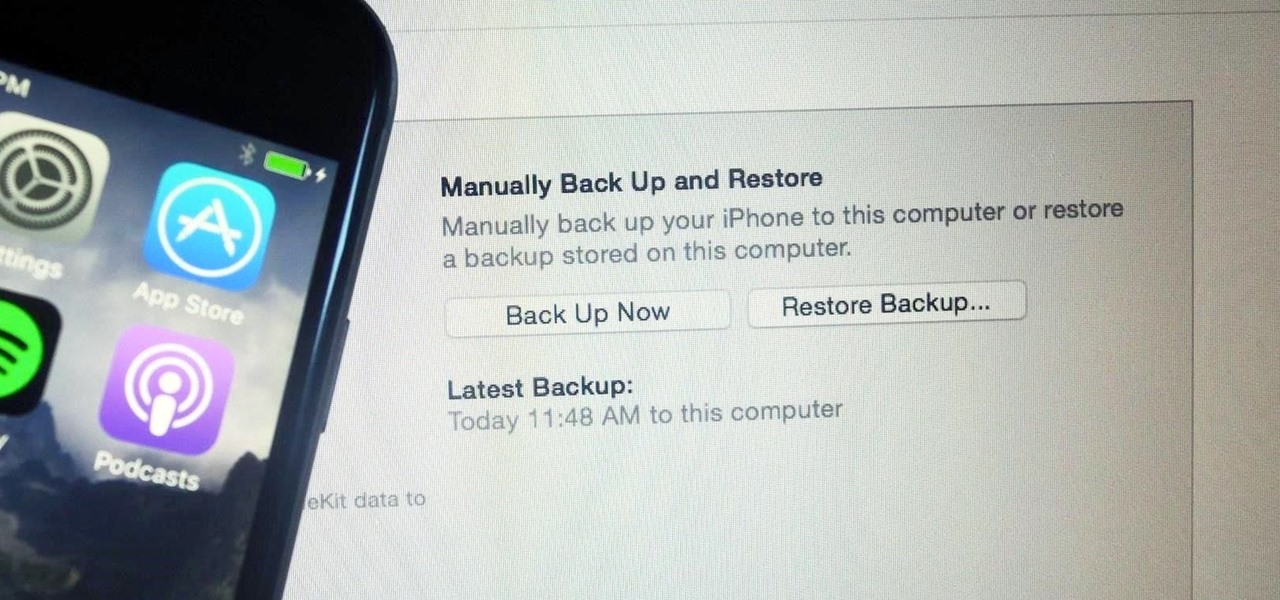
Whenever something goes wrong with your iPhone, or whenever you want to downgrade from an iOS beta back to the regular iOS release, you can restore your iPhone to your last saved state. Restoring to an iCloud backup is great but won't work in all situations. Plus, if you saved a backup on your computer, that may be the best route to take to get back all of your data.

It's easy to back up and restore your iOS devices using iCloud, but there are a few downsides to encrypted iCloud backups. For one, Apple holds the key to decrypt all the data. Plus, you're limited to only 5 GB of data for free before you have to upgrade your storage to 50 GB, 200 GB, or 2 TB.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

So, someone on your shopping list has an iPhone. Lucky for you, Apple's line of smartphones are practically made for accessories. From AirPods to adapters, there's something for every iPhone user in your life. Are you feeling overwhelmed by the options? You've come to the right place.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.