Learn how to strike your attacker when facing a hand gun attack. This is step three in surviving a hand gun attack, following how not to get shot, and how to gain control of the weapon. Learn how to get inside the gun's danger circle using different strikes and stay in there. Also learn what to do against a two handed gun grip.

America is in danger, and our leading secret agent has come to Rob "Riki Tiki" Roy for help. He'll be giving her the B-51, B-52, B-53, and B-54. You will need Frangelico, Grand Marnier, Sambuca, Creme de Menthe, Kahlua and Irish Cream liqueur. Watch and follow along to learn how to mix up these potently alcoholic shots.

The move order 1.d4 d5 2.e3 Nf6 3.Bd3 e6 4.Nd2 c5 5.c3 Bd6 is very annoying because it discourages the key move f2-f4. Instead, White should play a different opening. He can enter a reversed Meran Defense with 6.dxc5, or a Colle System with 6.Ngf3.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

every christian must watch this video.and know the names to call the god in prayer or danger.1000 names are in bible to call god.i took only 10 top names.

Scrat is a saber-toothed squirrel who is obsessed with collecting acorns, constantly putting his life in danger to obtain and defend them. I hope you enjoyed watching this tutorial. how to draw Scrat from the Movie Ice Age 4 visit how to draw for more tutorials!

The narrator starts by asking the question, how do sumo wrestlers get so big. Most of his patients are seeking weight loss. Number one way to put on weigh is to sit breakfast. The reason behind this has got to do with you blood sugar levels. What sumos do is they wake up, skipping breakfast and that train for 5 hours. They then consume about 20,000 calories throughout the day and take naps in the afternoon. They then have a huge dinner. The sumo wrestler uses his metabolism to gain weigh. He ...

Basically, a "Kook" is the type of surfer everyone hates. Kooks put themselves and others in danger by their actions in the water. In this video, learn the rules of the ocean and avoid everyone staying far away from you at the beach.

When you're starting a garden, you need to be wary of what kind of dangers may be waiting for your plants. If you're growing veggies, this is especially important since certain things can kill them fairly quickly.

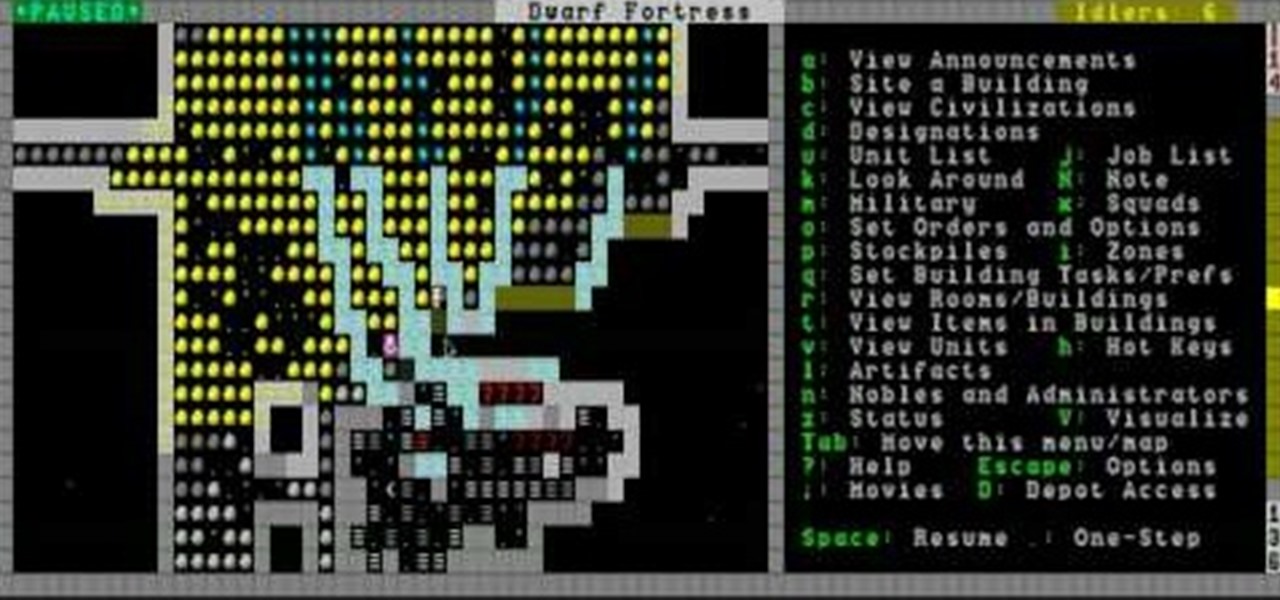
Adamantine is the best, most versatile metal in Dwarf Fortress, but discovering and using it bears great risk. This video will teach you all about adamantine and how you should react to ensure you survive what happens after you find it.

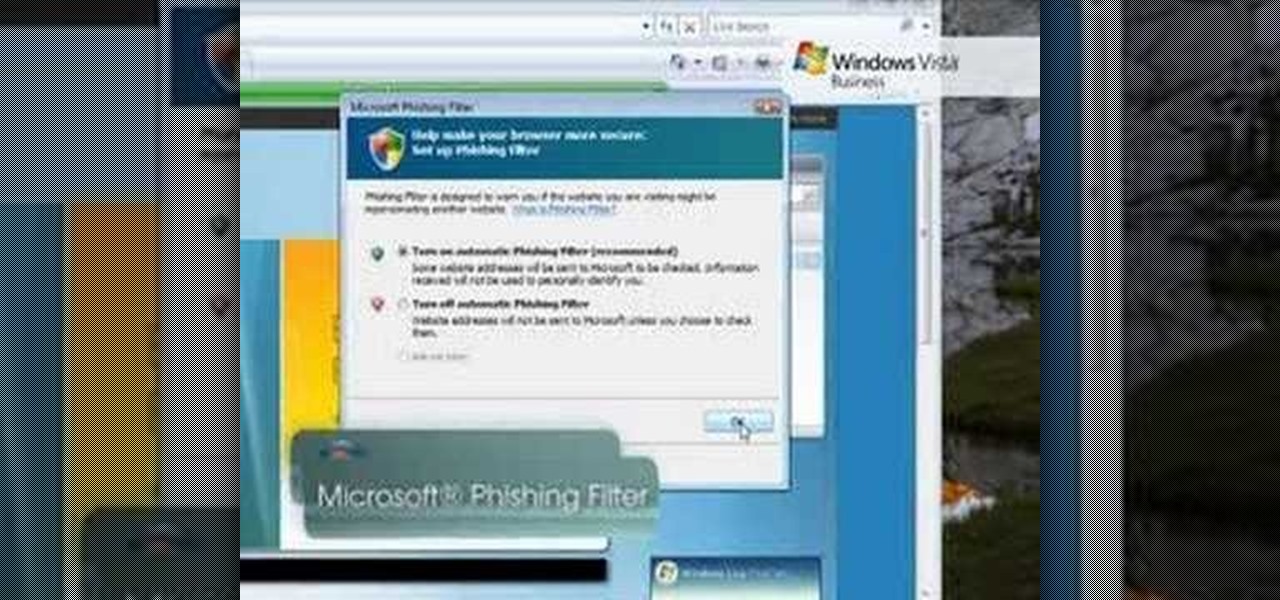
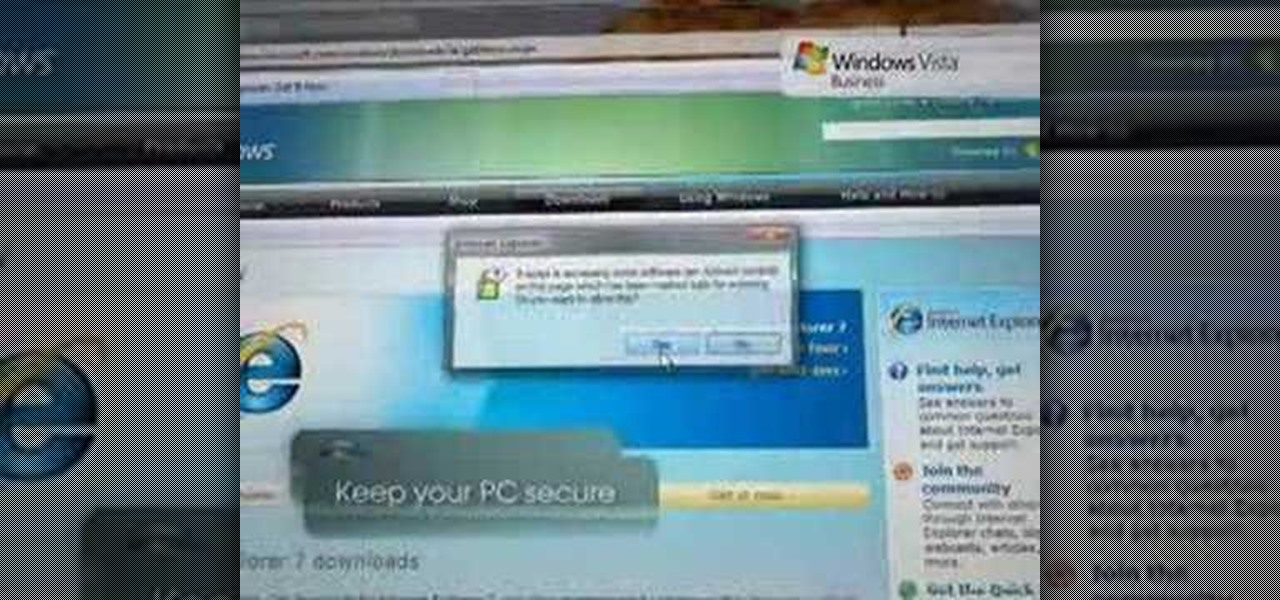
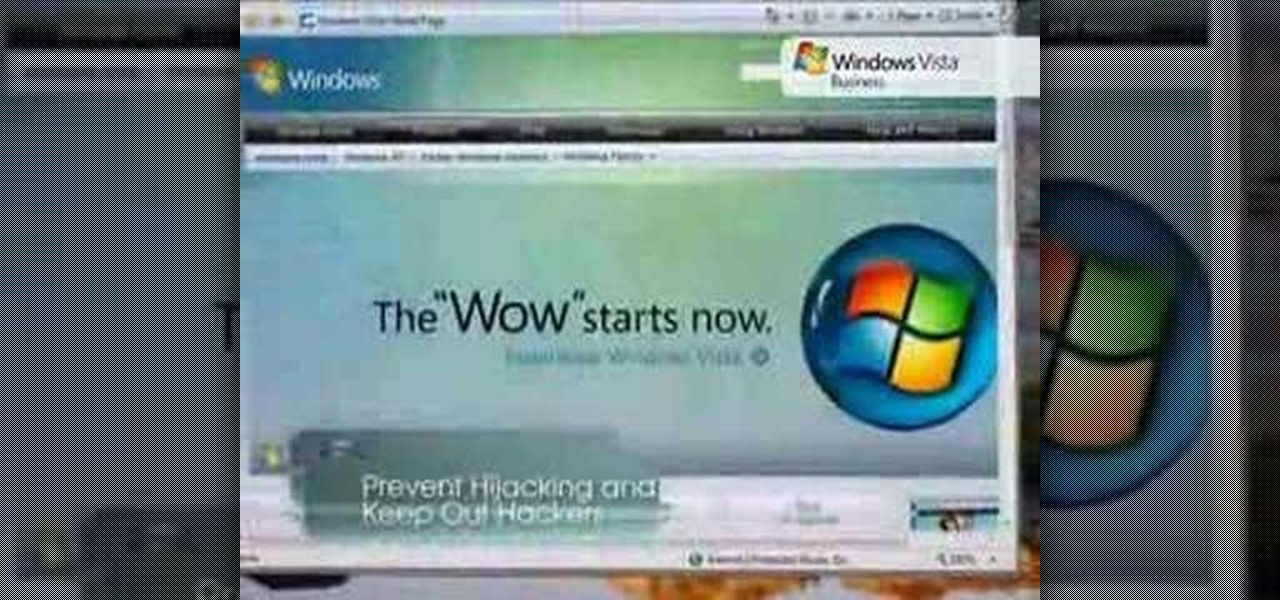
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

Black Friday is undeniably the biggest shopping day of the year. Black Friday, which occurs annually the day after Thanksgiving, is also the kickstart of the holiday shopping season, the big bang that leads swiftly to Christmas.

This video could very well apply to most bathroom exhaust fans, but this video specifically installs the Delta Electronics Breez Humidity Sensor Exhaust Fan, Model VFB25AEH (130 CFM). With this video, you'll learn the DIY approach to installing one of these exhaust fans in your bathroom, along with removing the old junk one. An upgraded bathroom fan can help eliminate the dangers of moisture, mildew and mold within your bathroom areas. Milan Rosan shows you the complete installation process. ...

In this Magic & Parlor Tricks video tutorial you will learn how to use normal playing cards as Tarot cards with Peter John. The diamond cards are used for money or finances in Tarot cards. Spades are known as swords in Tarot cards. Hearts are called cups, Clubs cards are recognized as business in Tarot cards. Hearts cards represent home, love, relationships and family. Spades are akin to problems, difficulties and dangers. The worst card is the 10 of spades. So, when you don't have Tarot card...

This speech from Duke University takes you through the basics of understanding the philosophy of metaphysics. One of the first lessons is the danger of religion without philosophy and how it can lead to a moral blank check. Learn about sacred space verses profane when talking about reality and how reality is multidimensional. You'll receive a beginners lesson on Rigveda and the beginning if Hinduism one of the oldest monotheistic religions in the world. Also, you'll get a lesson on human ener...

This 3-part video tutorial series will show you a very thorough way to skin a deer. This method of skinning of deer will provide the best shape and condition for your next step - brain tanning. Follow along with each step of the way, and make sure you're using an ultra sharp knife to eliminate the dangers of accidentally cutting yourself.

An associate from Garden Years discusses the danger frost poses to small, outdoor plants. Since you don't have a lot of control over the weather, there are a few tips you can follow to try an avoid any unwanted damage to existing plants. The host examines a peach tree to identify when a plant is blooming and thus very delicate. If a plant is fully blooming, then any temperature below freezing (32 f) can damage the blossoms. Aside from putting cloth over the plant, mulch is also very helpful i...

Finding yourself in the wilderness where there is no chance of possibly making a fire outside is pretty dangerous. But you can avoid the danger by making your very own cheap woodburning stove for the inside of you shelter. Enjoy!

In this boxing fitness video the instructor shows how to wrap hands for boxing training. If you are going to hit heavy bags or pads for fitness boxing, then you need to properly wrap your hands or you face the danger of injuring your knuckles or wrists. The instructor shows you how to wrap by wrapping a cloth around a woman's hand. Instead of wrapping the cloth on your hands yourself, it is always better to ask some one to wrap your wrists for you because they can work with both of their hand...

Have you ever wondered how sumo wrestlers are able to obtain and maintain such massive figures? Joseph Stickland, an applied clinical nutritionist, will explain to you exactly how a sumo wrestler is able to do this. Joseph will also explain the health detriments and the dangers to this type of lifestyle. Joseph explains that sumo wrestlers will skip breakfast, exercise, eat massive amounts of calories, (10,000 calories at least) for lunch, take a nap, and then have another mega calorie meal f...

Running low on power steering fluid could put you in real danger, causing hard steering, a sudden loss of control to the car and fatal car crashes, but here's a way to steer clear of that situation.

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Thawing frozen food on the countertop or in warm water may put your family at risk from food-borne bacteria. Keep them safe by following these methods.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

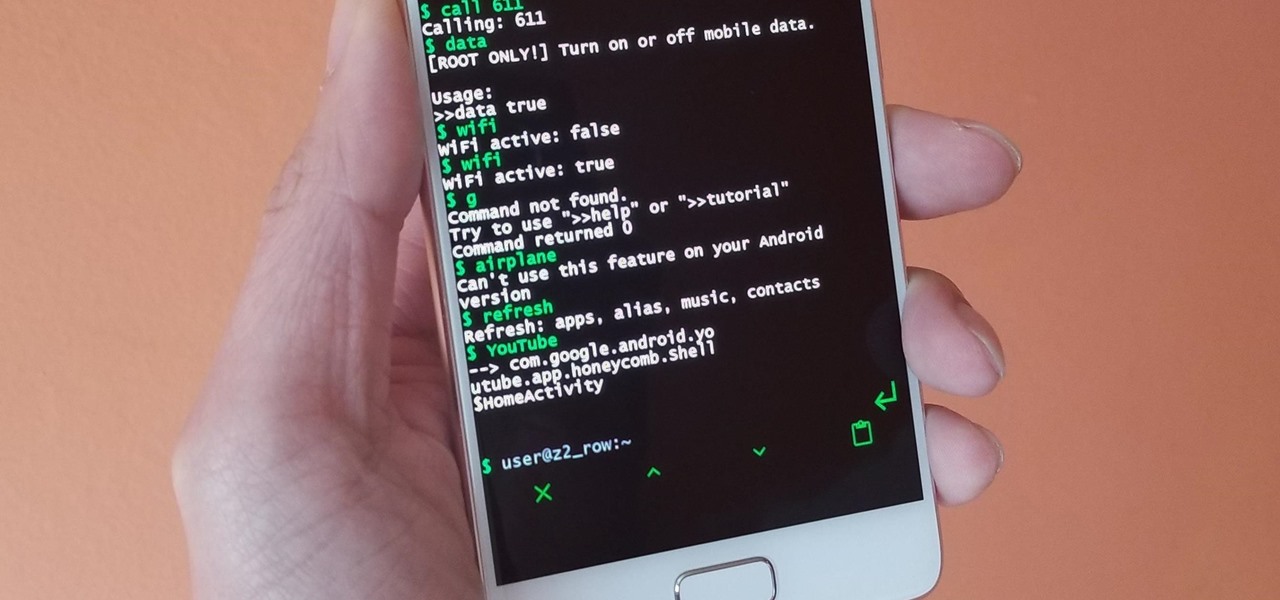
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

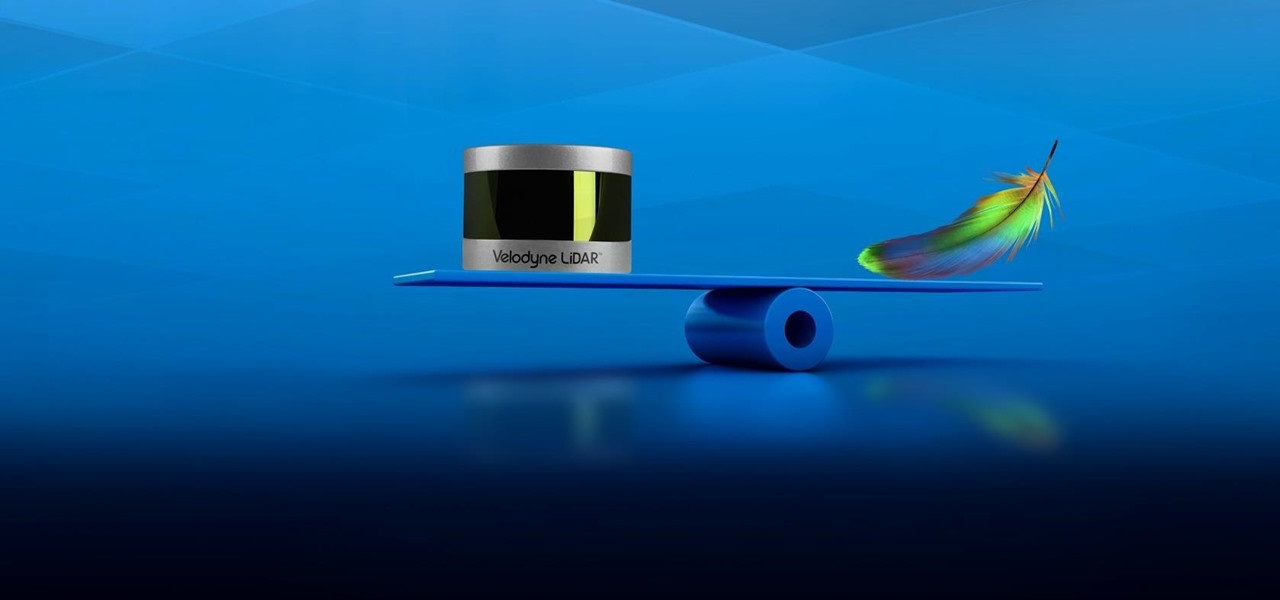
Velodyne wants to set the standard for the driverless industry when it comes to LiDAR. To do that, the Silicon Valley-based team just announced its next step — create a low-cost, fixed-laser sensor that can be embedded into a wide range of automotive and autonomous vehicles. That next step is named the Velarray. A sturdy, compact, and affordable LiDAR laser.

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Those going on crazy off-road adventures, taking their inspiration from various SUV commercials, are likely to encounter many unexpected, all-terrain dangers.

Video: . Steel wool fire Photography

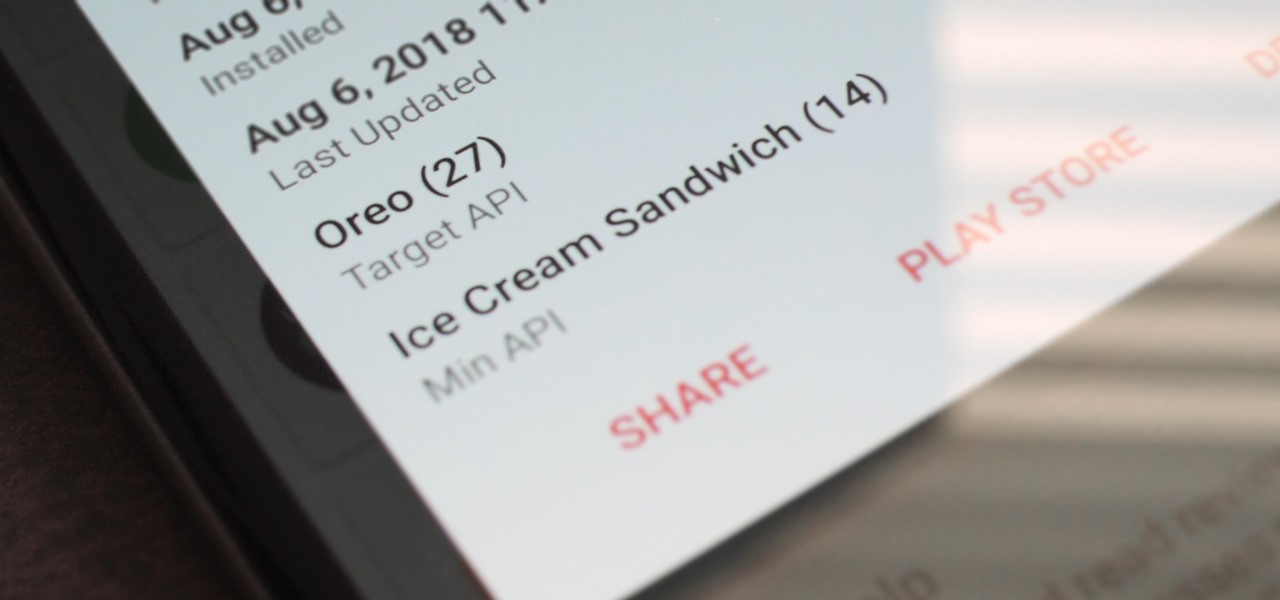
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

Every physician, medical student or resident, from emergency room doctors and nurses to anesthesiologists, need to know of the most fundamental skill sets: airway assessment and management. But before one can be proficient with this skill set, you need to know the tools of the trade.

Monitoring your blood glucose level is absolutely essential to your health if you suffer from diabetes. You need to keep track of your blood sugar or you could be in danger. This video tutorial will show you the proper way to use a blood glucose meter and give you helpful tips on getting the most out of them.

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

This is just a quick video to explain the dangers of working en pointe in ballet without any supervision.

"Foodborne illnesses are responsible for more than 75 million illnesses, more than 230,000 hospitalizations, and approximately 5000 deaths each year in the United States." In this six-part video lesson, learn about the basics of food safety in a commercial food enviornment. In the first video, three types of contamination are gone over as well as how improper handling can allow food to become dangerous to your patrons. In video two, learn about proper holding times and temperatures, and what ...

Twilight, that steamy, dreamy love story between teen Bella and heartthrob vampire, Edward Cullen. This love story is based on a series of vampire novels (Twilight, New Moon, Eclipse, and Breaking Dawn) by Stephenie Meyer. True love, handsome boy, and vampire danger = perfect teen love story. Who's your favorite Twilight character? This makeup tutorial demonstrates how to create Rosalie Hale's makeup, based on the actress Nikki Reed in the Twilight movie.

Twilight, that steamy, dreamy love story between teen Bella and heartthrob vampire, Edward Cullen. This love story is based on a series of vampire novels (Twilight, New Moon, Eclipse, and Breaking Dawn) by Stephenie Meyer. True love, handsome boy, and vampire danger = perfect teen love story. Who's your favorite Twilight character? This makeup tutorial demonstrates how to create Bella Swan's makeup, based on the actress Kristin Stewart in the Twilight movie.

Twilight, that steamy, dreamy love story between teen Bella and heartthrob vampire, Edward Cullen. This love story is based on a series of vampire novels (Twilight, New Moon, Eclipse, and Breaking Dawn) by Stephenie Meyer. True love, handsome boy, and vampire danger = perfect teen love story. Who's your favorite Twilight character? This makeup tutorial demonstrates how to create Alice Cullen's makeup, based on the actress Ashley Greene, in the Twilight movie.