If you want to become a food Instagram star, you may want to consider having babies. Well, to be more specific, you might need Mike Chau's two adorable children, Matthew and Samantha.

As iOS 10 makes its worldwide debut, many users are noticing that the promised iMessage effects feature in Messages is not working properly. Instead of seeing the actual effects, messages will come through like normal, but with text describing the effect they were sent with. On top of that, you can't send your own message effects if you're one of the affected users.

No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.
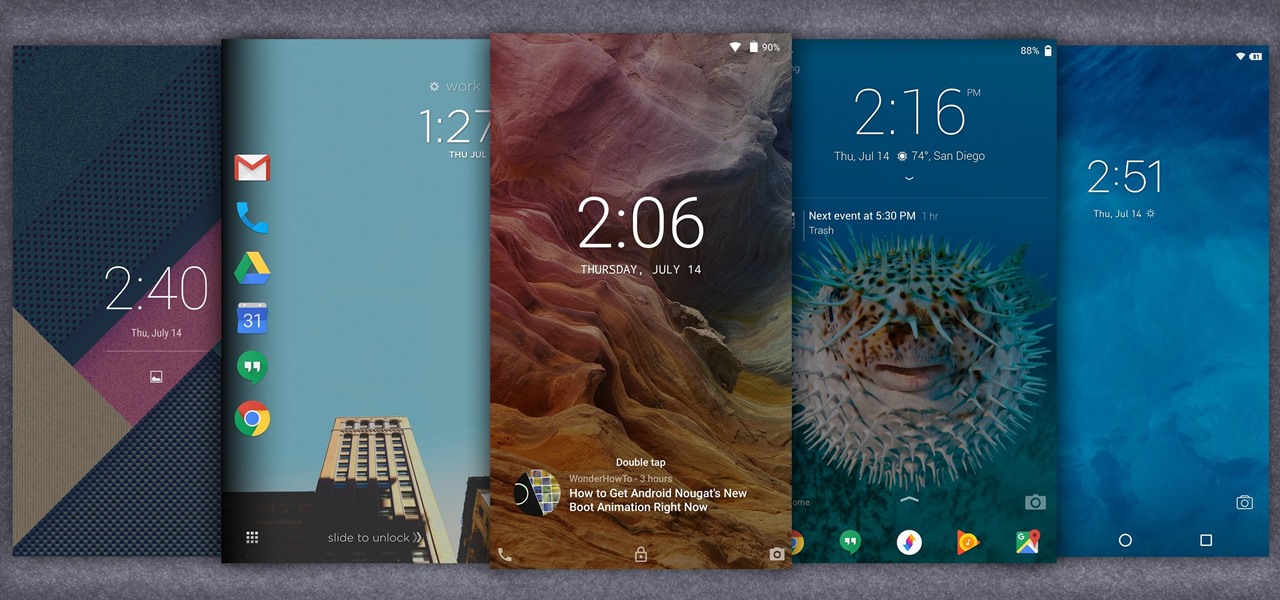
When it comes to customization, you just can't beat Android. Not only can you replace your home screen, switch your default apps, and apply icon packs, but you can even replace your entire lock screen by installing a simple app. Considering that the lock screen is the first interface you encounter when you pick up your phone, that last one might even be the biggest change you can make without root access.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

The Android Nougat preview build for Nexus devices comes packed to the brim with new functionality: multi-window mode, a dark theme, and a data-saver toggle, just to name a few. However, unless you have a Nexus device, it will be a while before you get these exciting new features by default.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

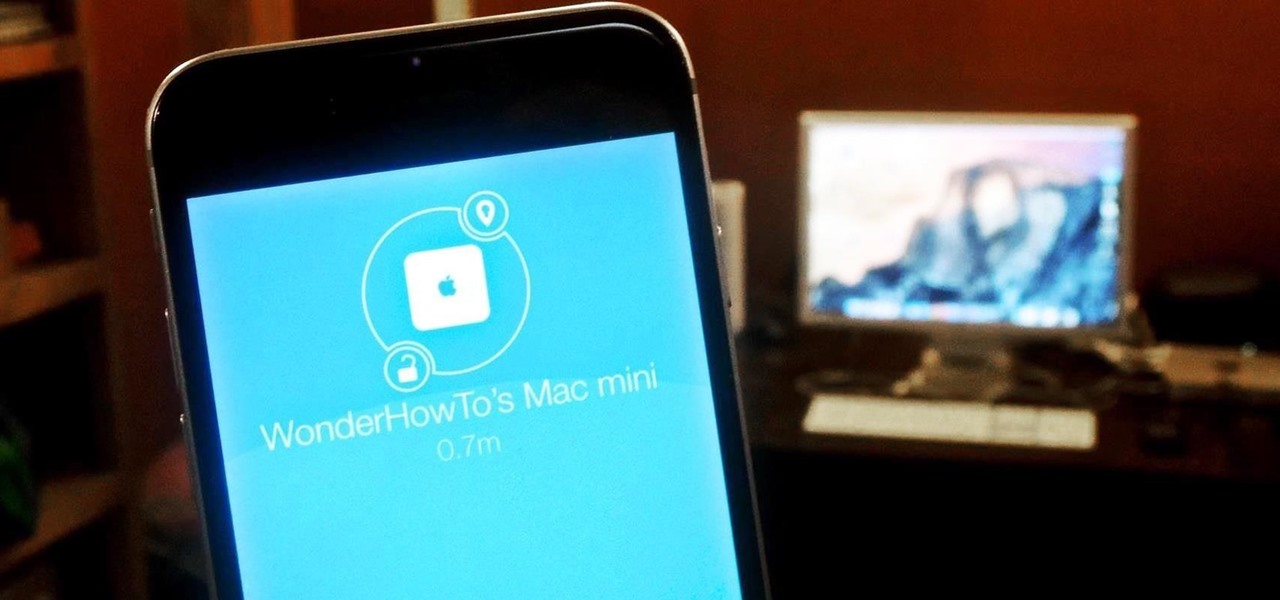
Leaving your computer unattended, whether at home, work, or a coffee shop, even for just a short while, is enough time for someone to steal it or look at your personal files. While there are ways to deter thieves, it's a little harder to keep snoops away.

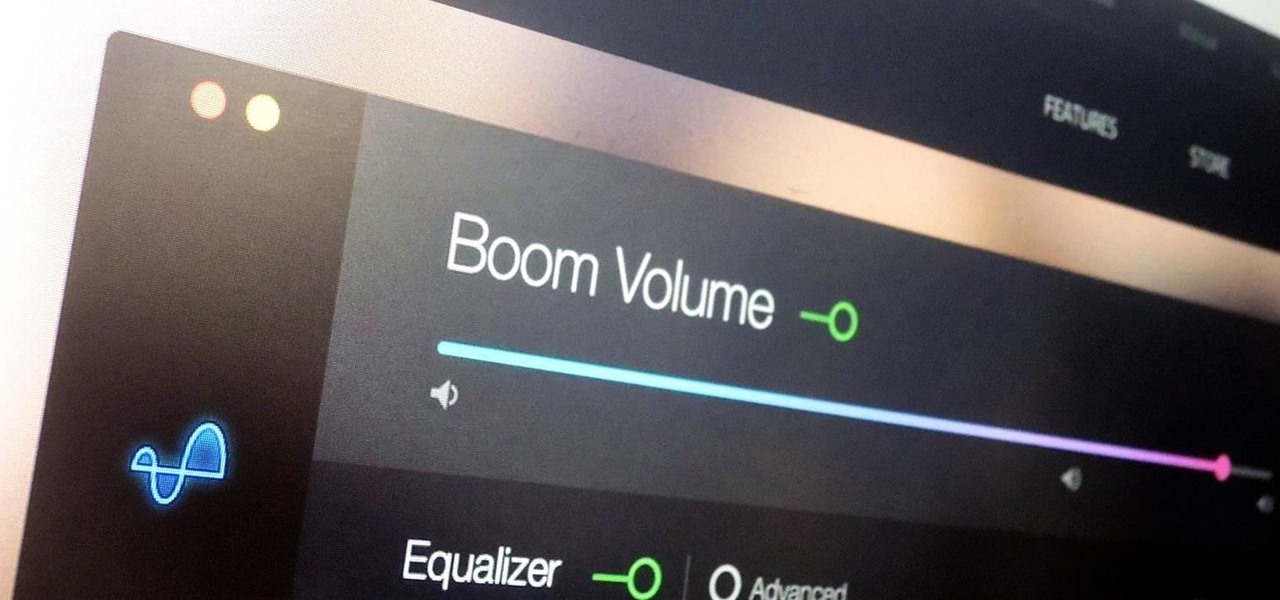
During a power outage at my apartment this year, I watched movies on my MacBook Pro instead of on my television. While I had no complaints about the screen size, I did have an issue with how low the audio coming from my speakers was. External speakers would help, but I don't want to buy them or lug them around every time I want to watch a movie.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Aside from its many high-end features, the camera on the LG G3 is up there with other heavy hitters like the Galaxy S5 and HTC One.

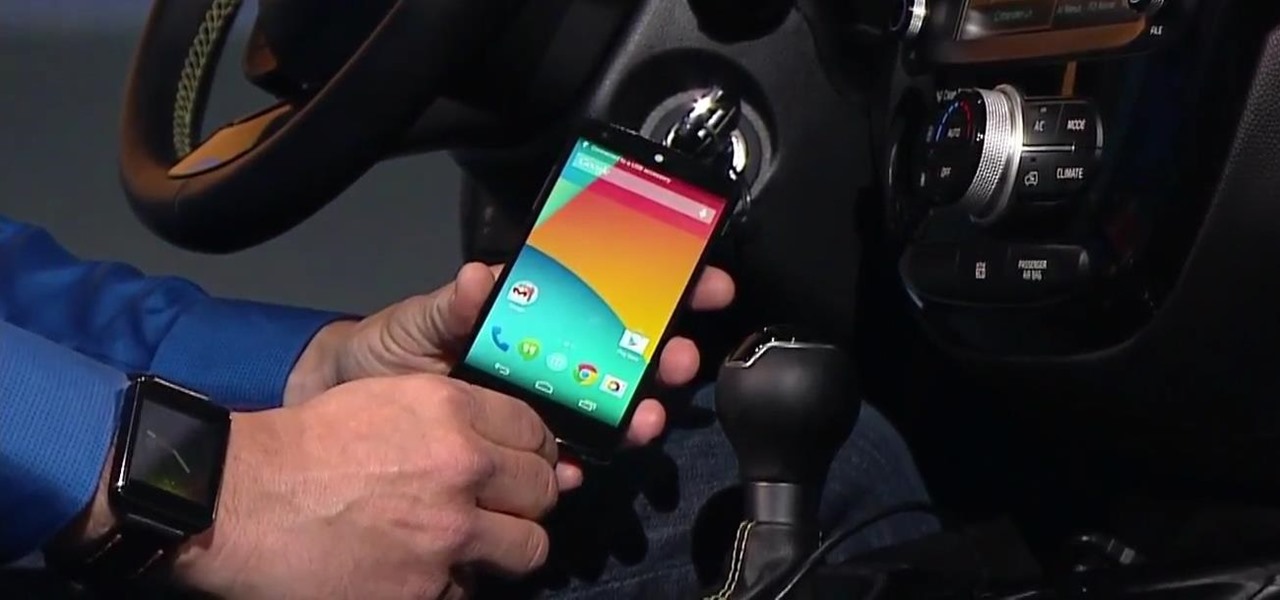
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

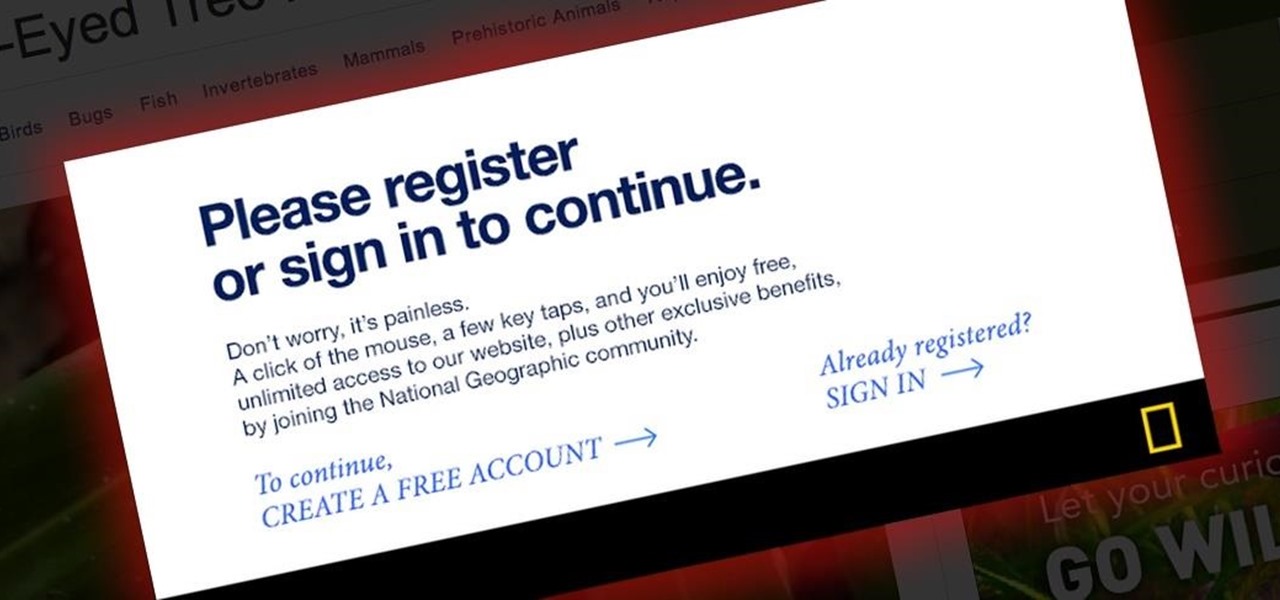
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

There are a lot of things your Samsung Galaxy Note 2 can do straight out of the box, but there's also a ton of things it can't, or simply could be better at. That's why most of us end up rooting—to enhance the mobile experience.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Artist Kate Bangs shows us how to improve old furniture with a shabby rose design. Take vanilla and fuchsia colored paint and mix them together as you paint them on the furniture to form the background. Let that background paint dry. With a watery brush paint the rest of the areas, including raised sections. It is shabby painting and so it does not have to be super neat. Load your brush with pink and white paint and make arches in a circle to form petals. Mix green, pink and white on your bru...

In these art lessons on video you'll learn how to create a watercolor painting. Our expert will show you what art supplies and materials you will need, especially the types of paints and brushes, as well as how to sketch out your painting, block in colors, and how to add darker colored paints to your watercolor.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.
How Do You Do A Business Plan? Part 1 of 5 (Series designed to discuss the parts of a business plan, what information is involved in each part, and why a business plan is needed.)

Your iPhone can do just about anything. It can even be a television remote. And a DVD player remote. Also, a CD player remote. You name it, it can be a remote for it. But it can't do it by itself, you need to use FLPR. It's a nice little piece of software that turns your iPhone into a universal remote. But it can be pricey. So what's the deal with FLPR? Best Buy has answers. The Best Buy Mobile team explains how simple it is to transform your Apple iPhone into a universal remote with FLPR.

One aspect of Android's interface that remains clunky is its gesture- or button-based navigation bar, mainly because app developers aren't fully utilizing the tools available to them. But a new feature Google is working on may finally make your nav bar more uniform across your apps.

Google always sets aside a few cool software features to remain exclusive to its Pixel phones. But that's the thing about Android: software features can be ported to other devices.

Night mode on the iPhone 11, 11 Pro, and 11 Pro Max is a godsend if you want clearer photographs in dimly lit environments. But if you want to keep the image dark or full of shadows as an effect of sorts, it's not immediately obvious how to disable Night mode, which turns on automatically when the app thinks you need it. But it can be turned off.

How much screen time is too much for a child? Should you let your children have a smartphone or tablet? What age is appropriate to introduce them to technology?

While Snapchat had a head start in making augmented camera effects popular on smartphones, Facebook has spent the past few years in hot pursuit, with no less than three apps offering mobile AR experiences, plus its Portal hardware lineup of smart home devices.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

Sometimes, we get stuck on a song so good we want the world to know about it. Sure, you could take the time to save the album art to your iPhone, then upload it to your Instagram or Facebook story, but why bother doing that when you can simply share the song to your story right from Apple Music?

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.

Alternate US history is the go-to move for hot new cable and streaming shows, from HBO's Watchmen to Hulu's The Handmaid's Tale, reimagining how things might have turned out is an endless well of narrative inspiration.