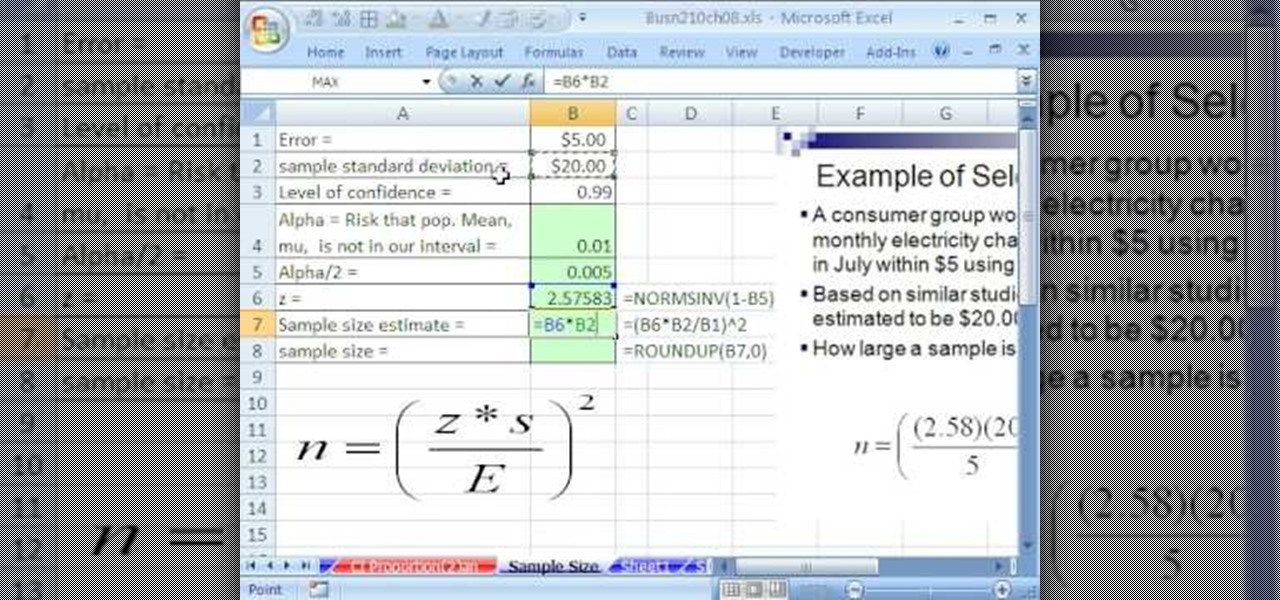
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 87th installment in his "Excel Statistics" series of free video lessons, you'll learn how to calculate sample size (n) for confidence intervals.
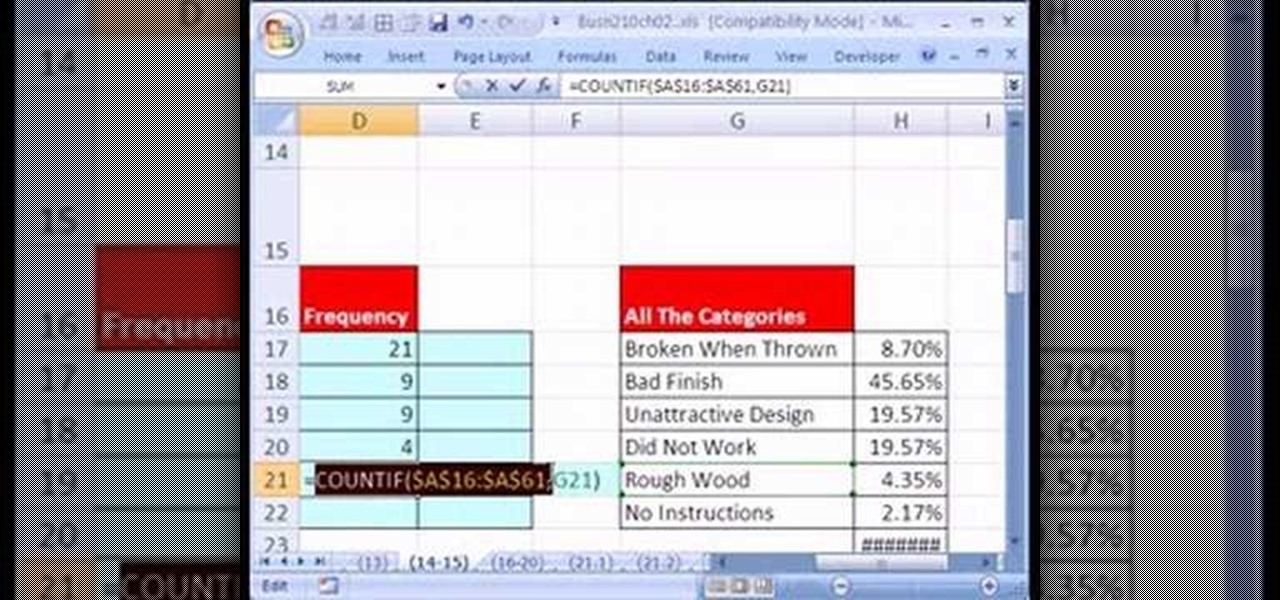
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 19th installment in his "Excel Statistics" series of free video lessons, you'll learn how to group categories in a frequency distribution with a formula (2 COUNTIF) and the pivot table (PivotTable) grouping fea...
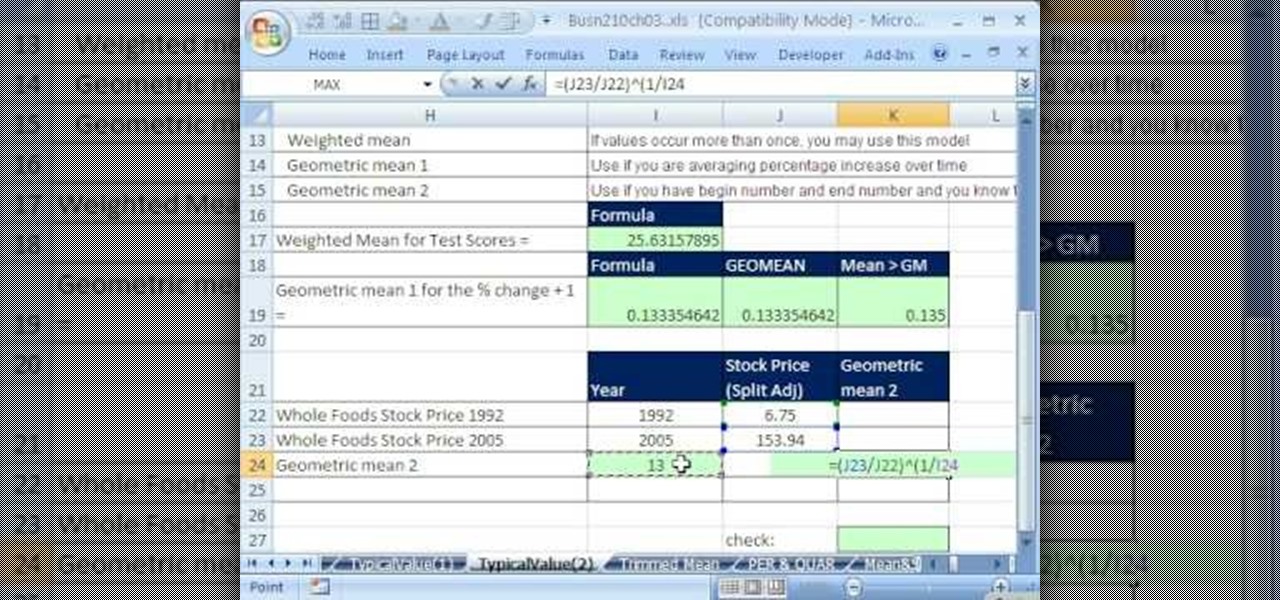
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 35th installment in his "Excel Statistics" series of free video lessons, you'll learn how to calculate weighted and geometric means and see how to use the GEOMEAN function.
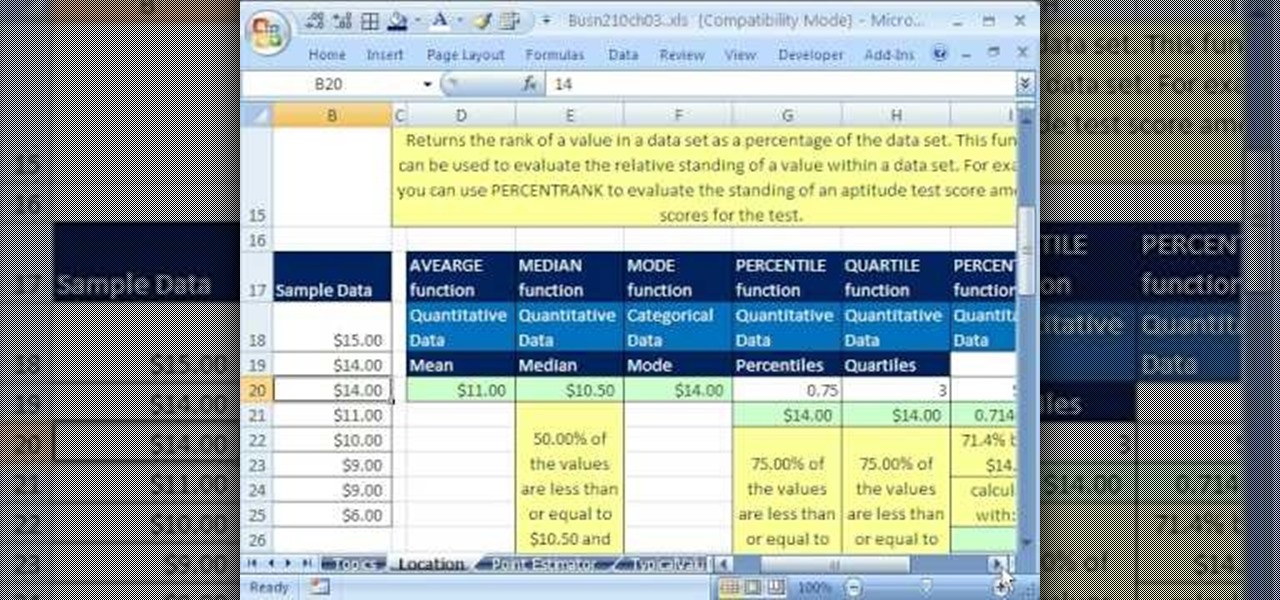
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 33rd installment in his "Excel Statistics" series of free video lessons, you'll learn how to use the AVEARGE, MEDIAN, MODE, PERCENTILE, QUARTILE and PERCENTILERANK functions to measure location.
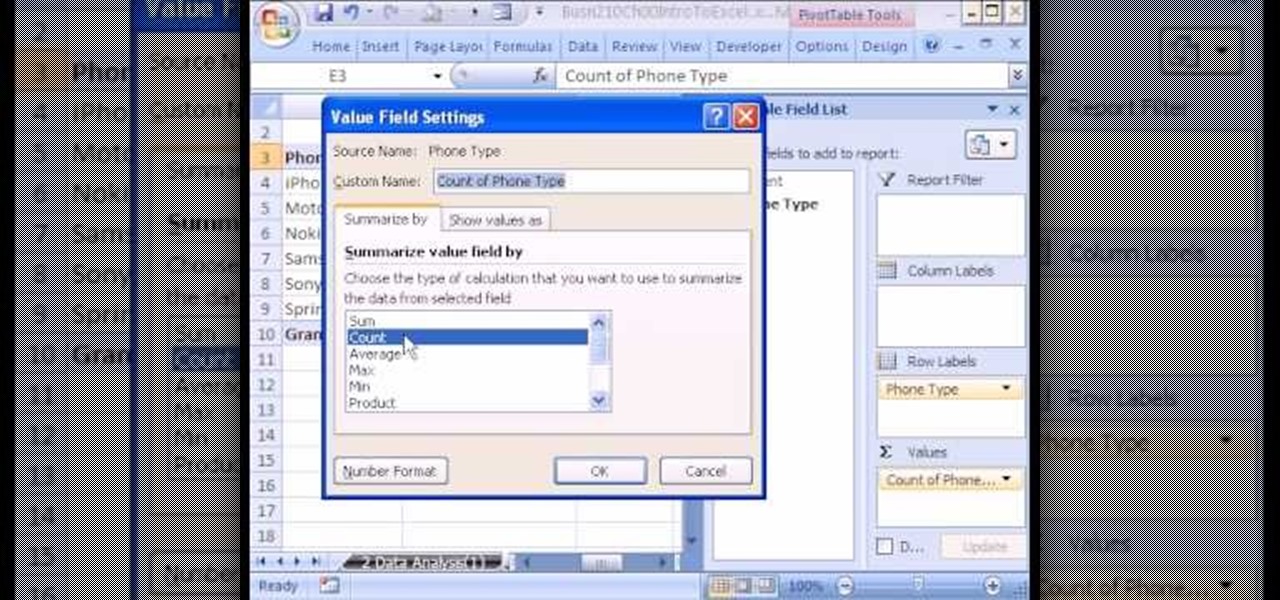
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 4th installment in his "Excel Statistics" series of free video lessons, you'll learn how to create a frequency table and percentage frequency table using a Pivot Table (PivotTable).
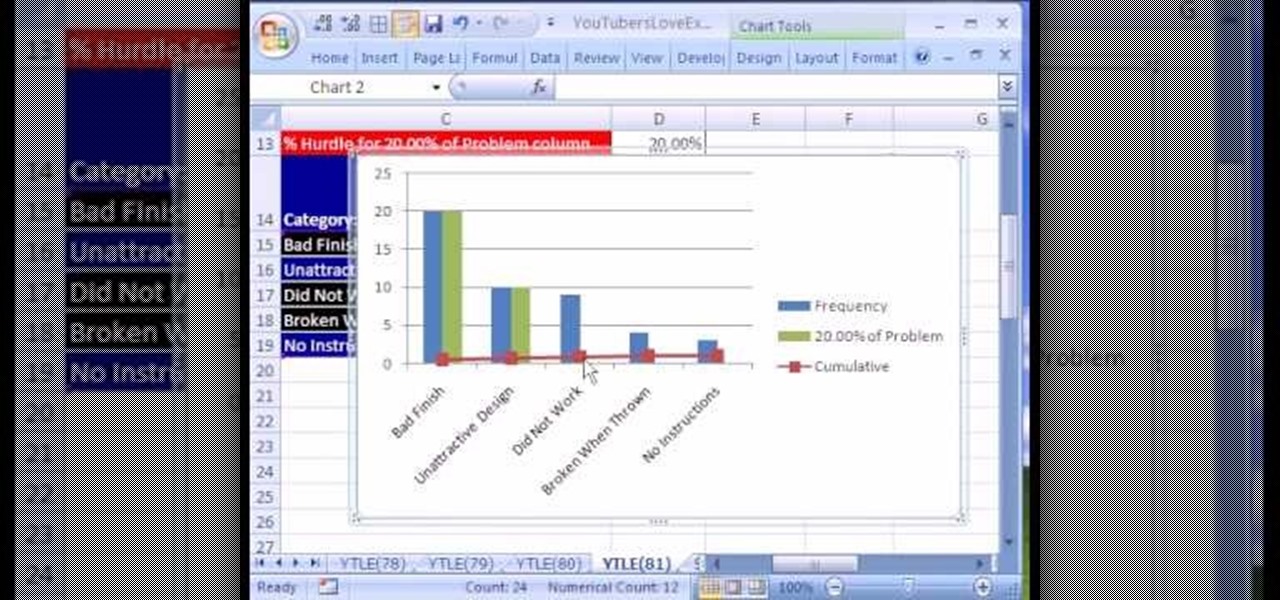
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 81st installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to add conditional formatting to a chart by creating a new column of data with a formula.

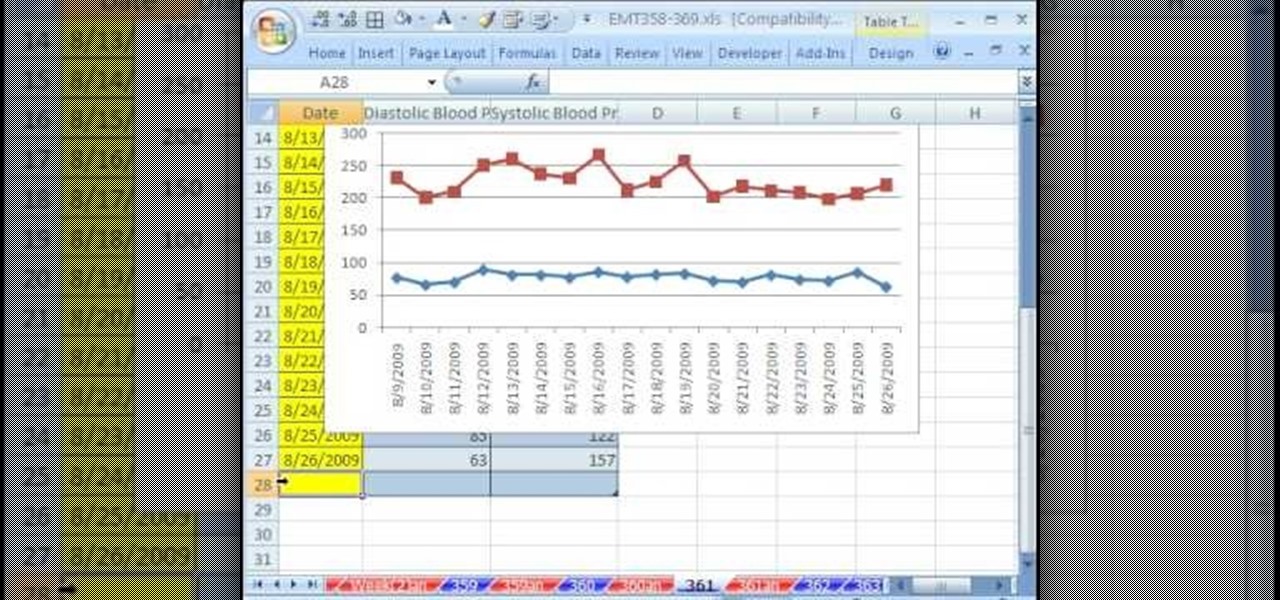
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 361st installment in their series of digital spreadsheet magic tricks, you'll learn how to create a dynamic two data series line chart for blood pressures.

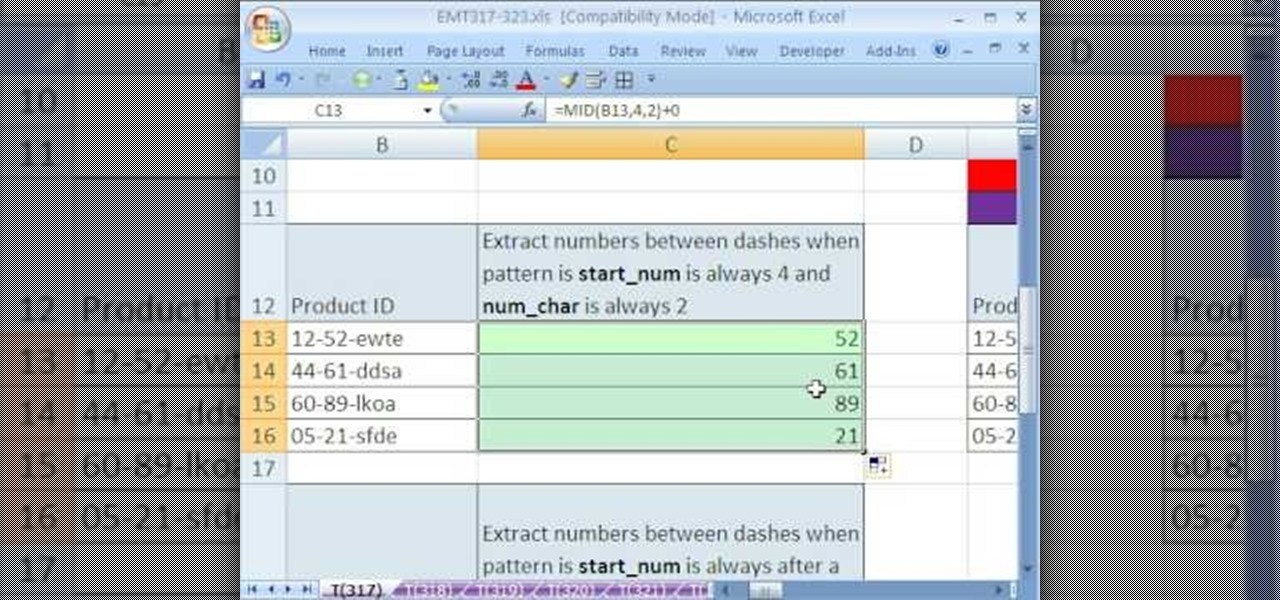
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 317th installment in their series of digital spreadsheet magic tricks, you'll learn how to extract data (specifically, a substring from string) using the MID Function.

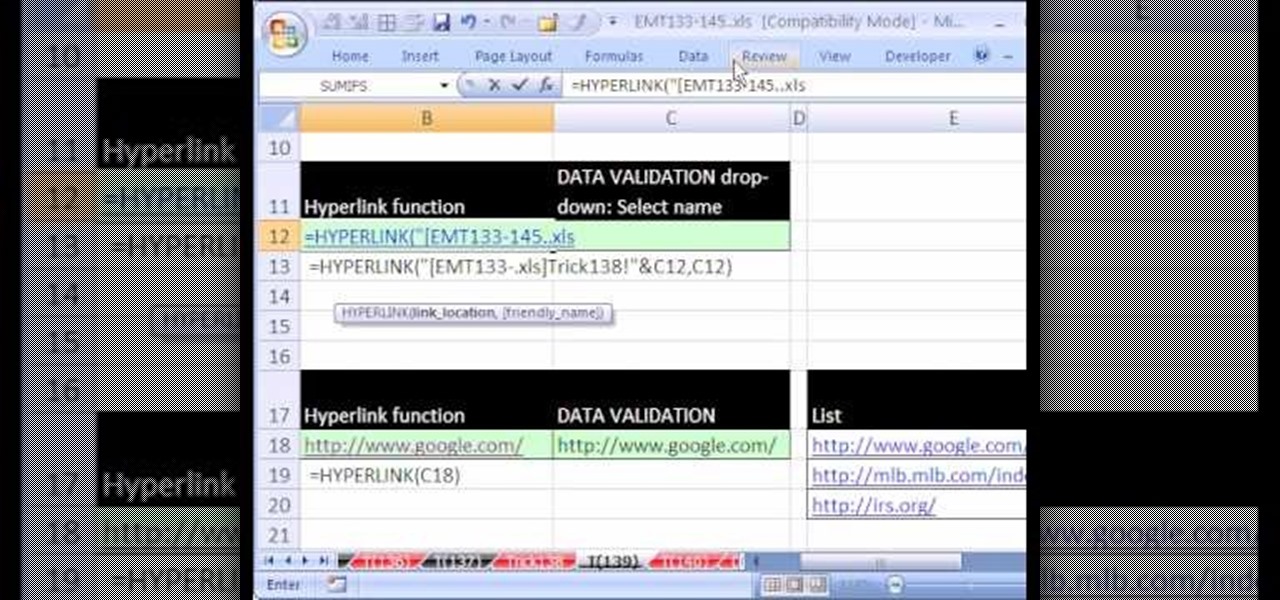
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 139th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a data validation list drop-down and the hyperlink function to create a list of links.

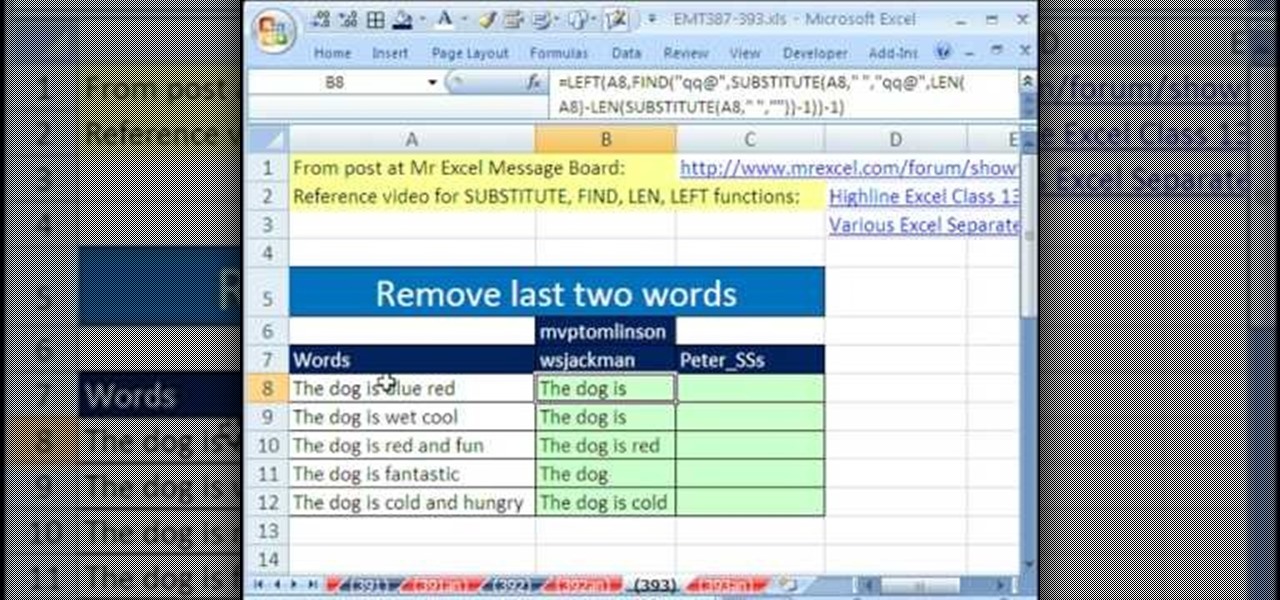
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. With this video tutorial from ExcelIsFun, the 393rd installment in their series of digital spreadsheet video tutorials, you'll learn how to remove the last two words from column of data with the LEN, SUBSTITUTE, FIND, REPT, RIGHT and TRIM functions.

Before you sell your Blackberry on eBay you may want to erase all personal data on the device. This video will show you exactly how to reset your Blackberry and erase all personal information.

A lag switch allows you to cheat in online games or on XBOX LIVE by disabling the flow of data to your console or PC. We will show you how to build one.

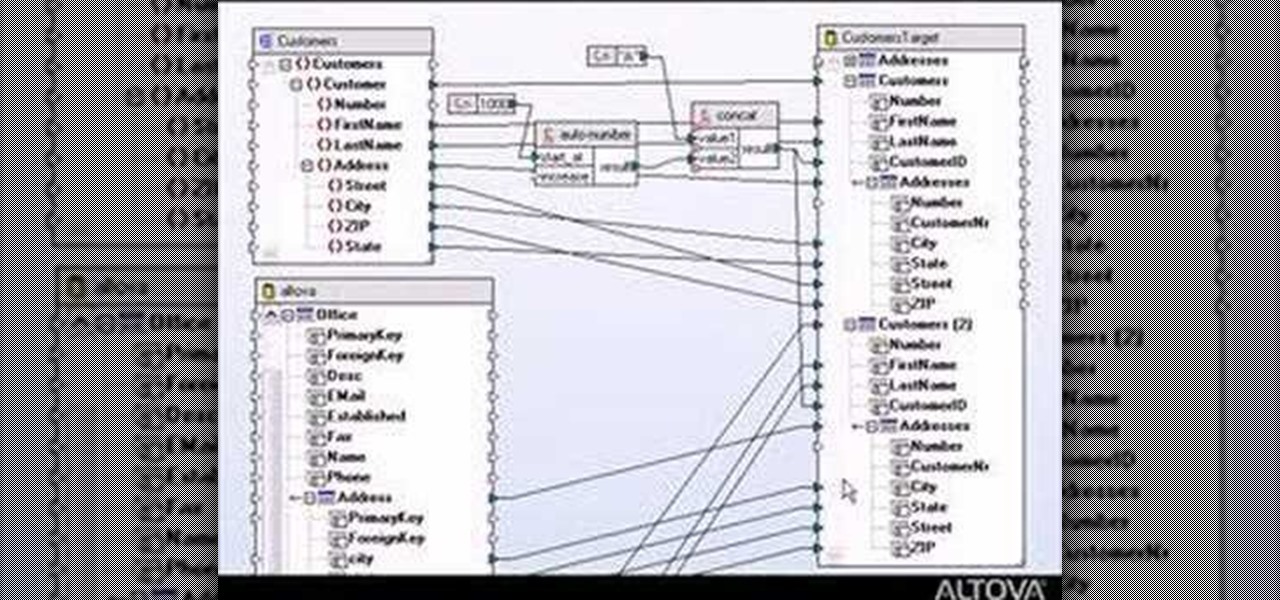
Designing a data mapping project in MapForce? The output functions in MapForce let you preview textual or XML output, save it to disk, or look at SQL statements for database output before committing them to the database server. Learn how in this tutorial.

While you cannot directly open a Microsoft Access database file in OpenOffice Base, it is possible to connect Base to an Access database, and manipulate the data contained within it.

Databases allow you to store data in a systematic and organized format, making it easy for you to search, sort and edit.

To use your iPod to move your music, you must sync your library to your iPod as data into a folder.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

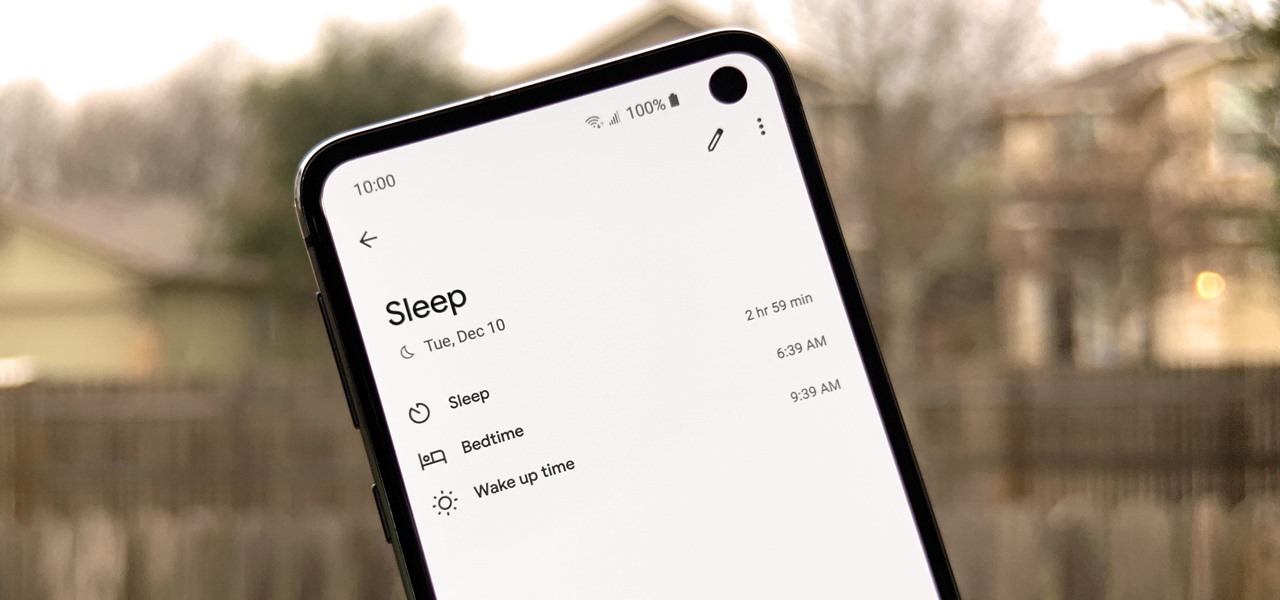
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

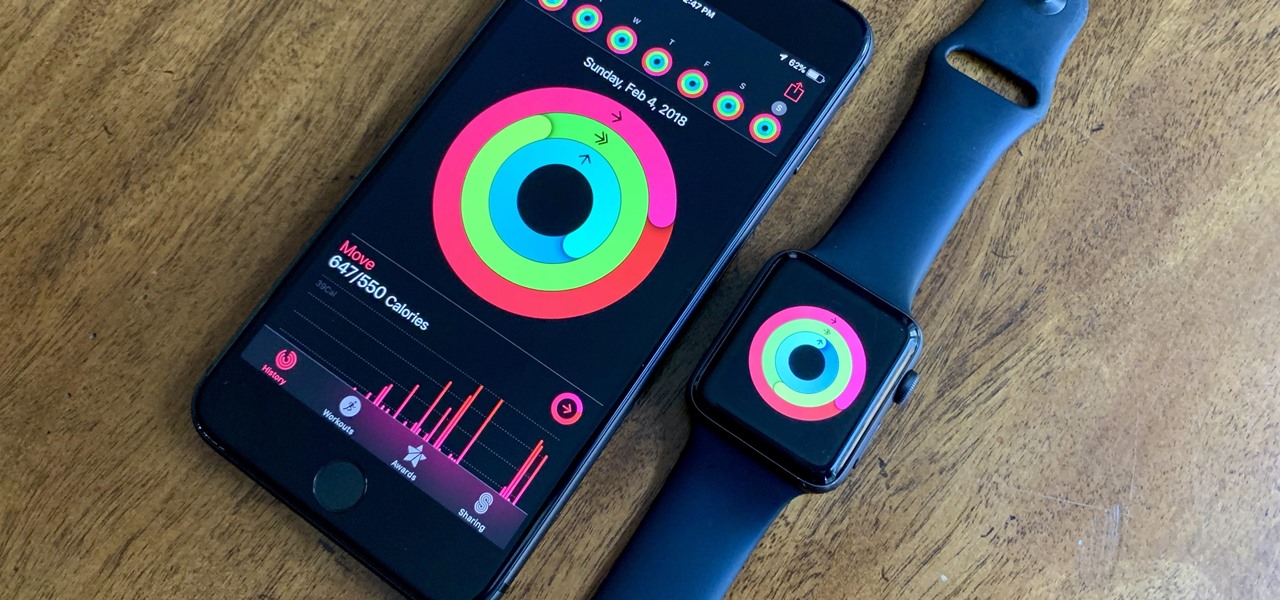
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

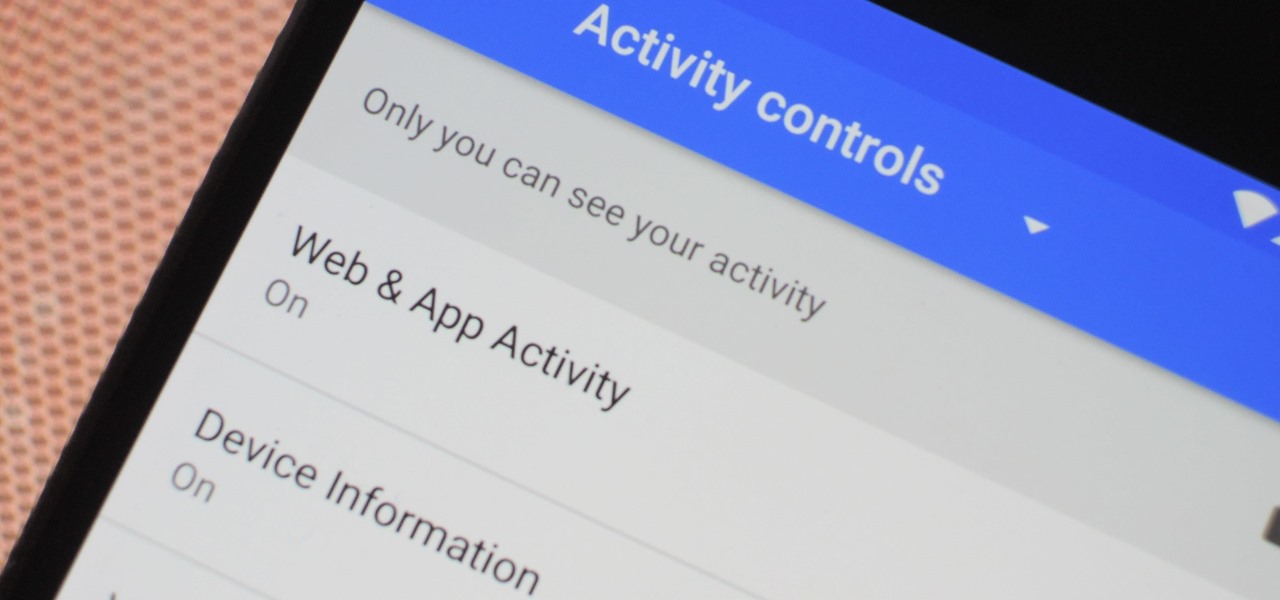
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

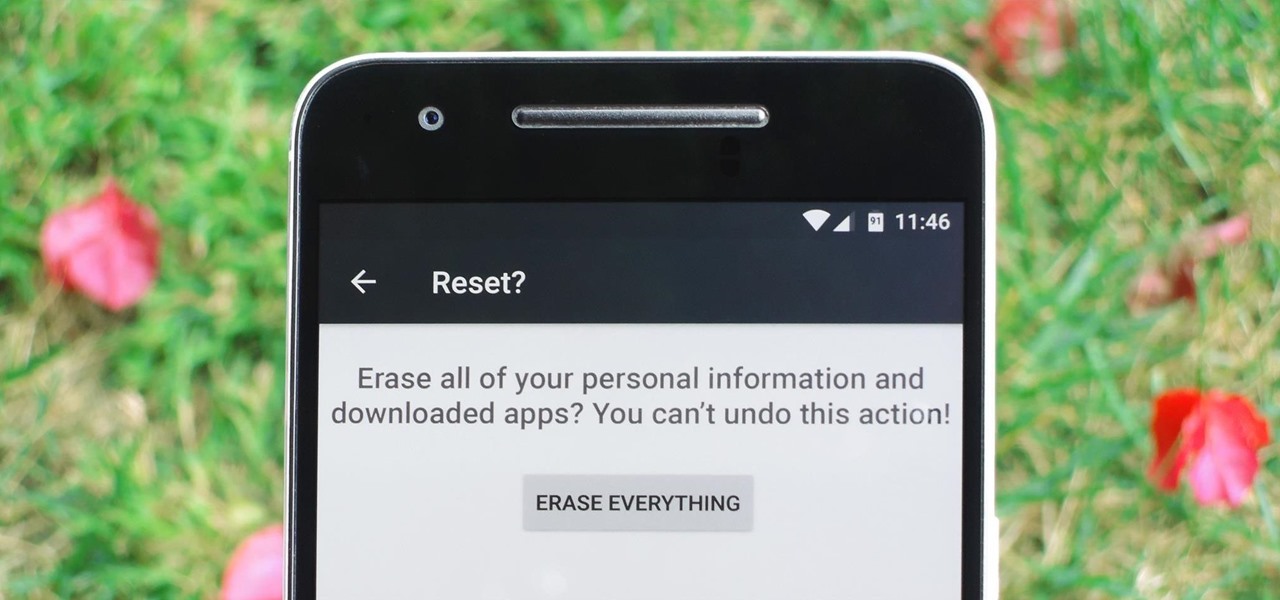
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.