Check out this video from Berkleemusic.com and take your recording in a new direction and change the key of a certain section or the pitch of a note using the Transpose options in Digital Performer music software.

The existing uninstall routine for the Mozilla Firefox web browser may leave profile data and a Program Files folder behind. This is how to remove it.

For Mac OS users who want to try Linux without erasing all of their other data - a step by step tutorial on how to install Ubuntu on a Mac using Parallels.

Kipkay details how to surf the web secretly and leave no trace behind on your computer. Many websites collect personal data without you knowing it and you should surf anonymously.
Find the biggest files on your computer ordered by size. Learn to order folder by filesize so you can find the ones harboring the most diskspace terrorists. Learn to clear up your private data automatically and wipe it clean from being undeleted.

How to make an instant, in-cell bar graph in a Microsoft Excel spreadsheet to make comparing data instantly visible.

A new feature in Google Maps, Mapplets, places data overlays onto your map - like movie times, crime rates and real estate prices. Learn how to combine multiple overlays for a one-stop view of what you need to know.

Learn how to better organize and convey your data to colleagues- create your own professional-looking charts in Microsoft Publisher.

Learn how to use the sum and autosum functions in Microsoft Excel and you'll appreciate the efficiency of spreadsheets for dealing with data lists. You'll never use a calculator again!

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Less than a month after launching its augmented reality Swim Goggles, wearables startup Form is preparing to add a major new feature for aquatic athletes.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

The photos and videos you take with your iPhone contain bits of information, known as metadata, including the location where they were taken. This metadata makes it easier for Photos to organize your media, but put these photos and videos in the wrong hands and anyone can find out where you live or work. Luckily, iOS 13 makes it easy to wipe the geotag from images and videos before sharing.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

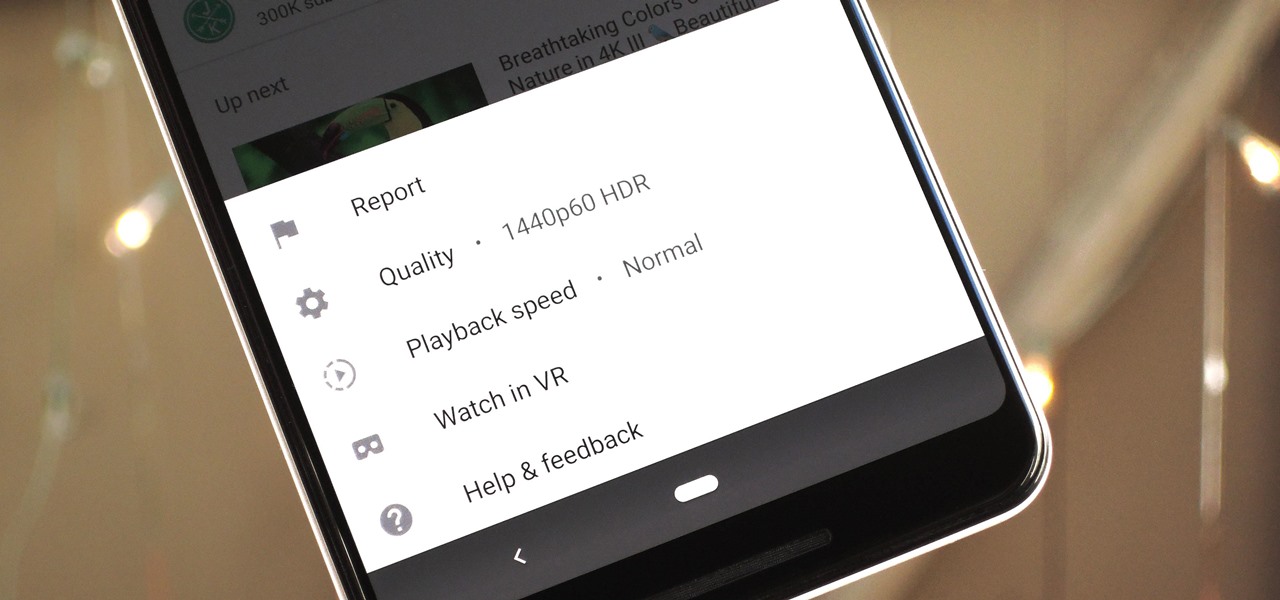
The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

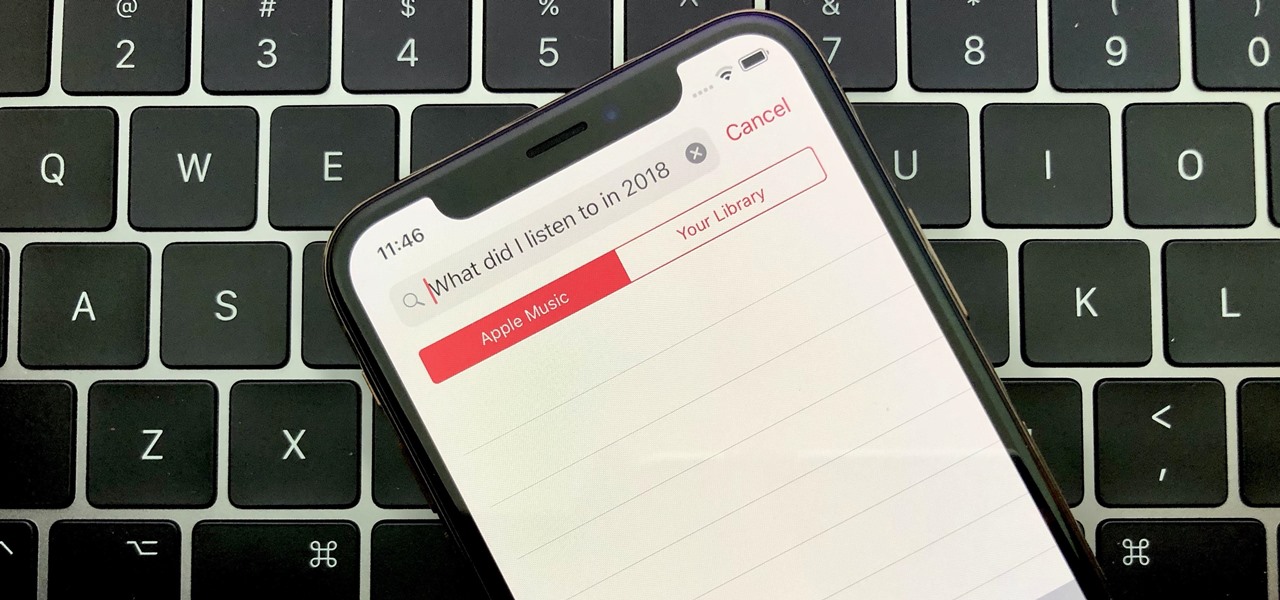
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

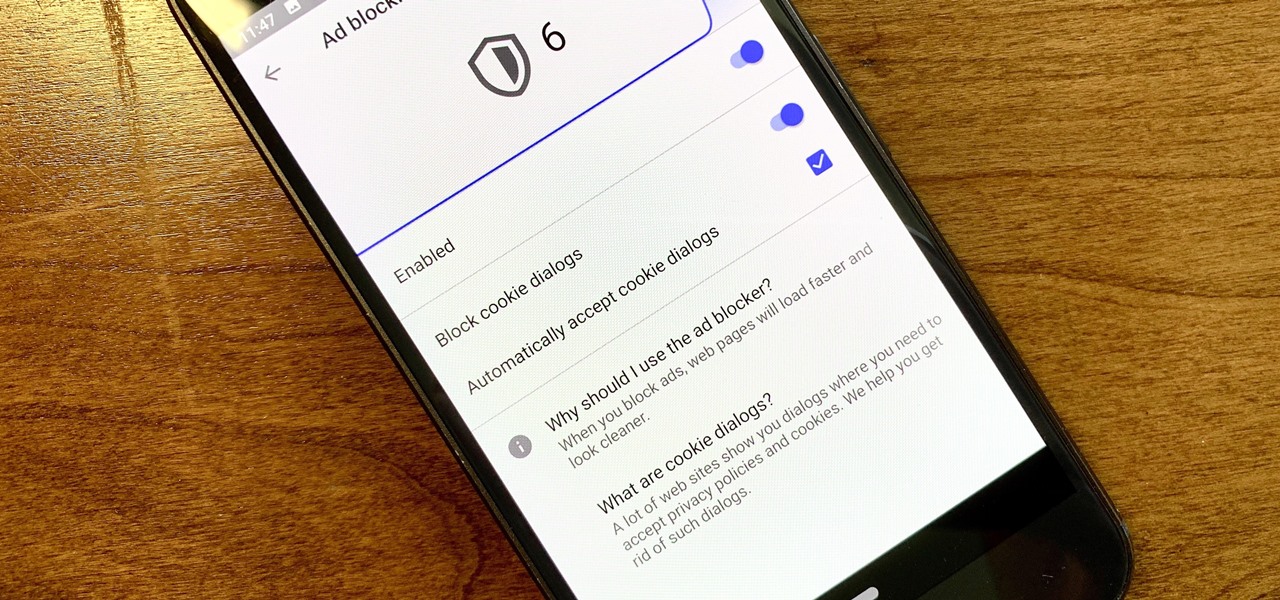
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

While having no internet connection is definitely a bad thing when you need it, you can at least bide your time until you're back online with a hidden Easter egg inside of the Google Chrome browser. This gem unlocks a secret side-scrolling game that can keep you busy during your downtime.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Beijing- and Seattle-based DataMesh have announced the release of a new enterprise geared mixed reality middleware — MeshExpert. This solution for collaborative interaction with dynamic data is made up of two primary components: MeshExpert Live!, a 4K mixed reality capture system built off of the Microsoft Spectator View, and MeshExpert DataMix, which offers the ability to blend different types of data with XR and mobile hardware.

Apple Maps. For years now, its reputation has been that of a punchline. Although Apple and Google battle for supremacy in most hardware and software categories, in the map game there's no question who has the superior app. But the news of the day shows Apple expanding the cities it plans on collecting street data from, opening up speculation that they're not ready to throw in the towel on Apple Maps.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.