If you're Apple computer needs a little cleaning, not the hardware, but the software, then MacKeeper is the way to go. This application will help protect your hard drive from junk and other useless data, freeing up much needed space on your Mac. Also, you can recover files, hide private files, clean up your login items, apps and plugins, and more! Watch this video to see how to use MacKeeper.

In this Software video tutorial you will learn how to install & use CDBurnerXP: Free CD/DVD burning software. It is compatible with Windows XP and Vista. Open up a browser and go to CDBurner. Click on downloads, download and install the file. Open it up and select your language. Then the main menu will pop up. Here you can choose exactly what you want to do. After you select your action, say Data disc, click OK. On the next screen you get to select the files. Just drag and drop them in to the...

If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 92nd installment in his "Excel Statistics" series of free video lessons, you'll learn how to use the TINV and TDIST functions to test a hypothesis.
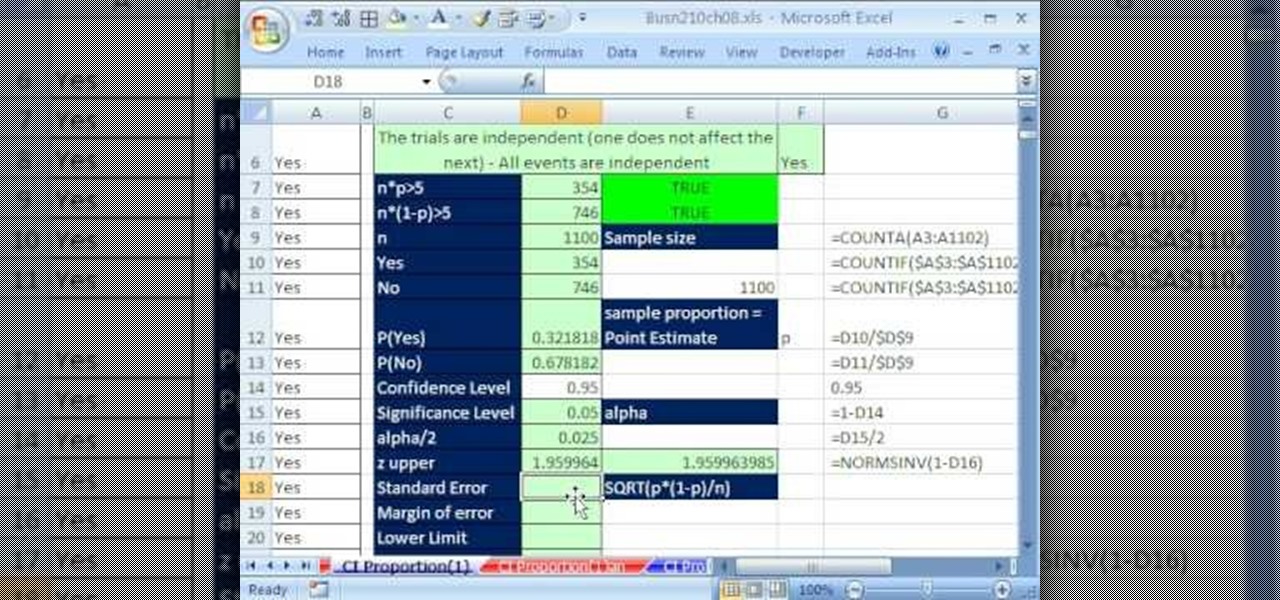
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 85th installment in his "Excel Statistics" series of free video lessons, you'll learn how to construct confidence intervals for proportions using NORMSINV function and other formulas.

This video will show you how to install custom firmware onto your PSP (Playstation Portable). Being able to install your own firmware will allow you to change the way your PSP operates. Follow these instructions, but be careful! It's always a good idea to back-up your PSP to prevent data loss.
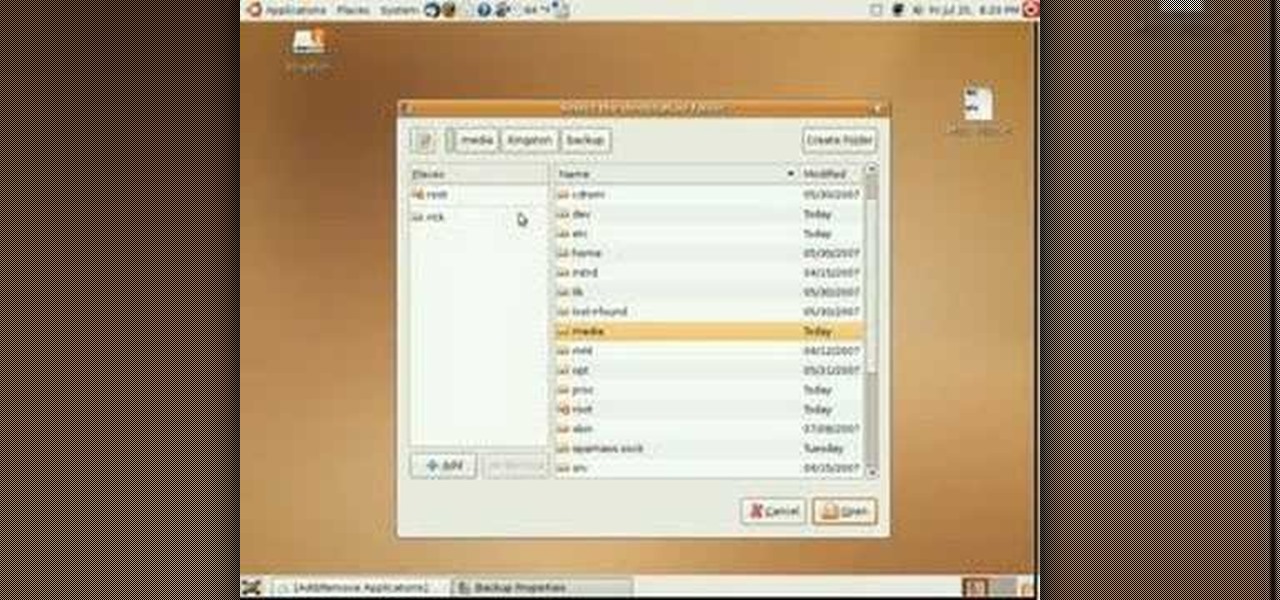
In this video tutorial, users of the Ubuntu Linux operating system will learn how to use the Simple Backup application to either manually or automatically back important data. For more, or to get started using Simple Backup on your own Ubuntu Linux system, watch this handy how-to.

Outlook is one of those applications that has 100 ways to do the same task. Today I’m going to show you how to automatically extract data from an email and have it populate fields in various modules in outlook (Contacts, Tasks, Calendar)

Watch this software tutorial video to learn how to use HijackThis to find malware hiding in the alternate data stream. This how-to video will make finding hidden malware easy and help you protect your computer.

Look at this video tutorial to see how to remove viruses from your computer if you live in Charlotte, or anywhere else in the world. This will help you remove viruses from your computer yourself, without paying mega bucks to get it fixed. You'll see how to get a free virus scanner, for virus removal. This could take up to an hour or two, depending upon the data information on your PC.

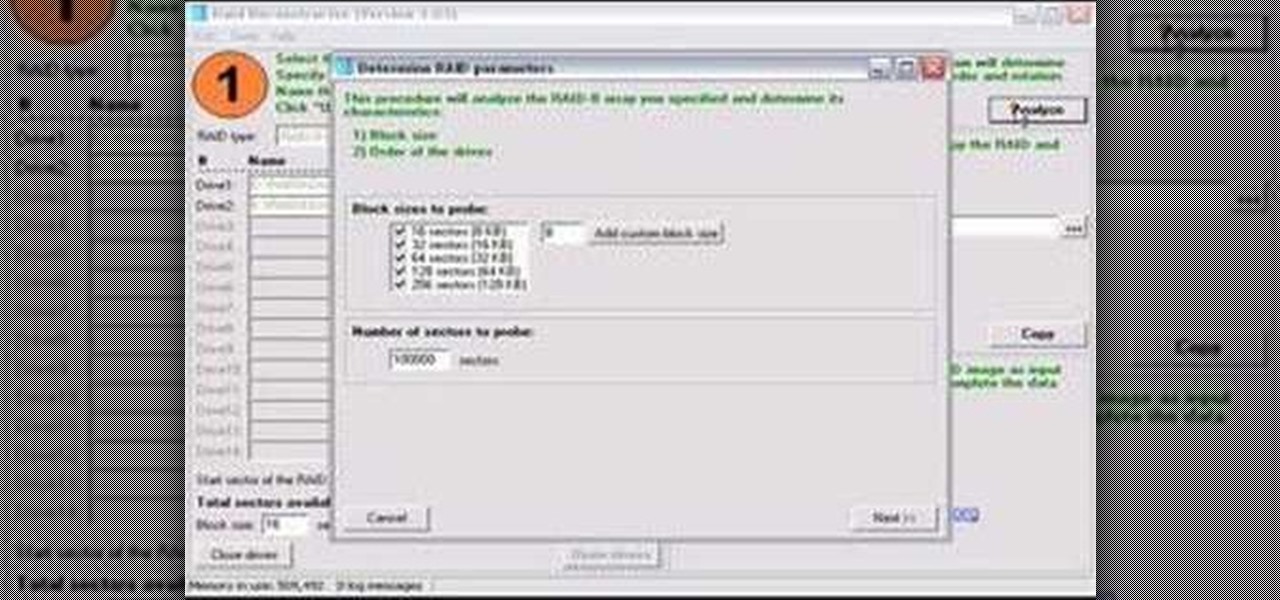
Check out this video tutorial on how to use the Runtime RAID Reconstructor software to create a destriped image with a two drive RAID 0. So, get your data back with this copy of your RAID to have recovery options for your computer. This program will collect, sector by sector.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

In this episode I show you a few of the innumerable uses of Quicksilver. Quicksilver is an unified, extensible interface for working with applications, contacts, music, and other data. The possibilities are endless. These are just a few of the ways that I use Quicksilver on a daily basis.

How to change the alignment of headings in Open Office Calc to fit all your data onto one page.

Larry Jordan explains the advantages and trade-offs of various external drive solutions, compares data rates or FireWire drives vs. SATA drives, what solutions work the best and how to avoid clogging your Final Cut Pro workflow.

Cells in Numbers '08 are the same as in Excel. Basically, they are where you store your data. This tutorial will show you how to use the different functions of cells.

A spreadsheet software wouldn't be much good if you couldn't use formulas and functions on your data. This tutorial goes over how to use them in Numbers '08.

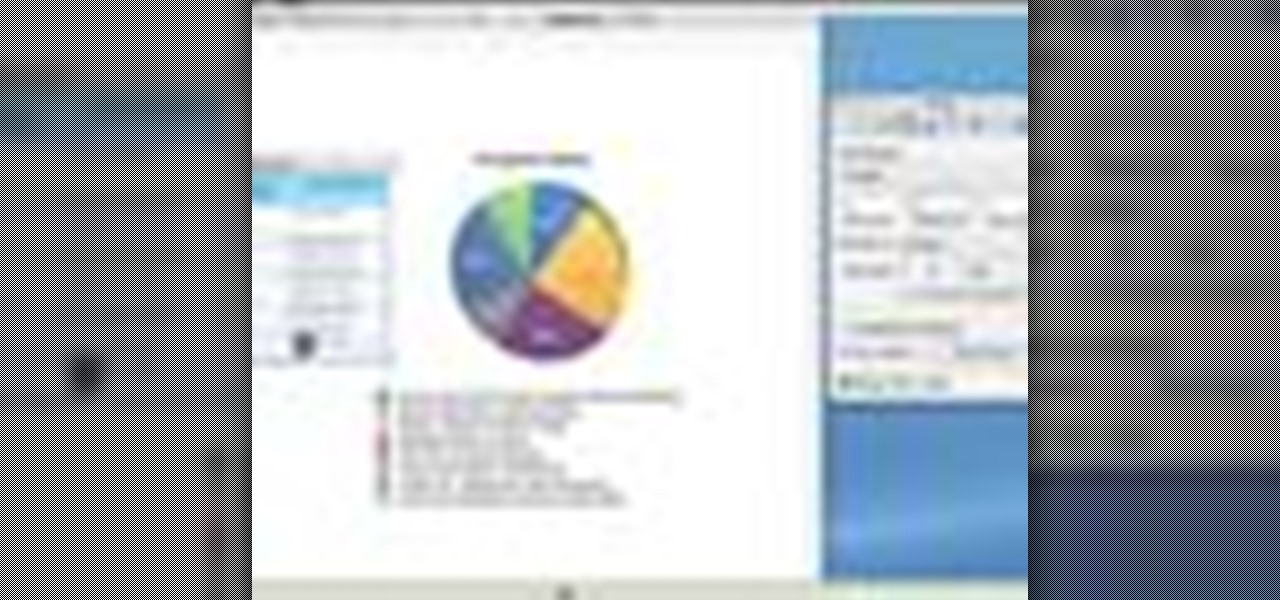
It's often best to use a graphical representation of the data you've assembled or calculated. This tutorial shows you how to create charts to visually show your results.

In Numbers '08 you can enter data dynamically with interactive buttons and sliders known as cell controls. This tutorial goes over using check boxes and sliders.

If you can't access your iCloud data such as emails, contacts, calendars, photos, notes, reminders, files, and other documents via a web browser on untrusted devices, like one at a library or friend's house, there's an easy way to regain access.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

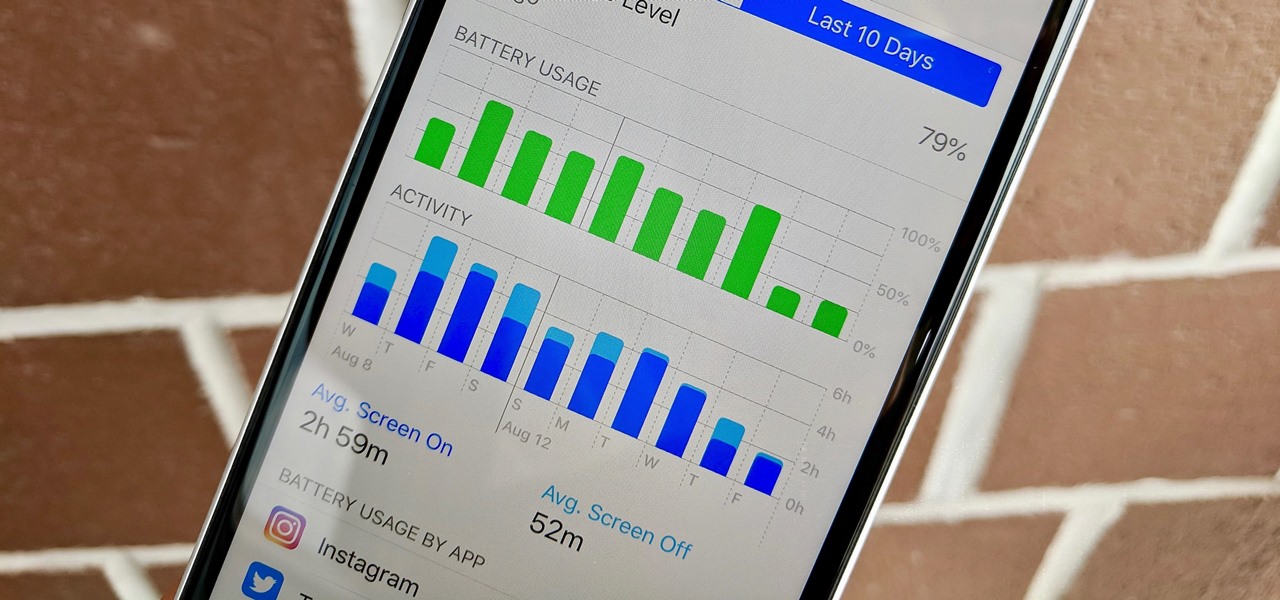
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Apple took a giant step forward in terms of user customization with the new Control Center in iOS 11. With an improved design, buttons you can pick and choose from, and even a new default Cellular Data toggle, it's definitely a better iPhone experience. However, Apple also took a giant step backward with the confusing Bluetooth and Wi-Fi toggles.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.