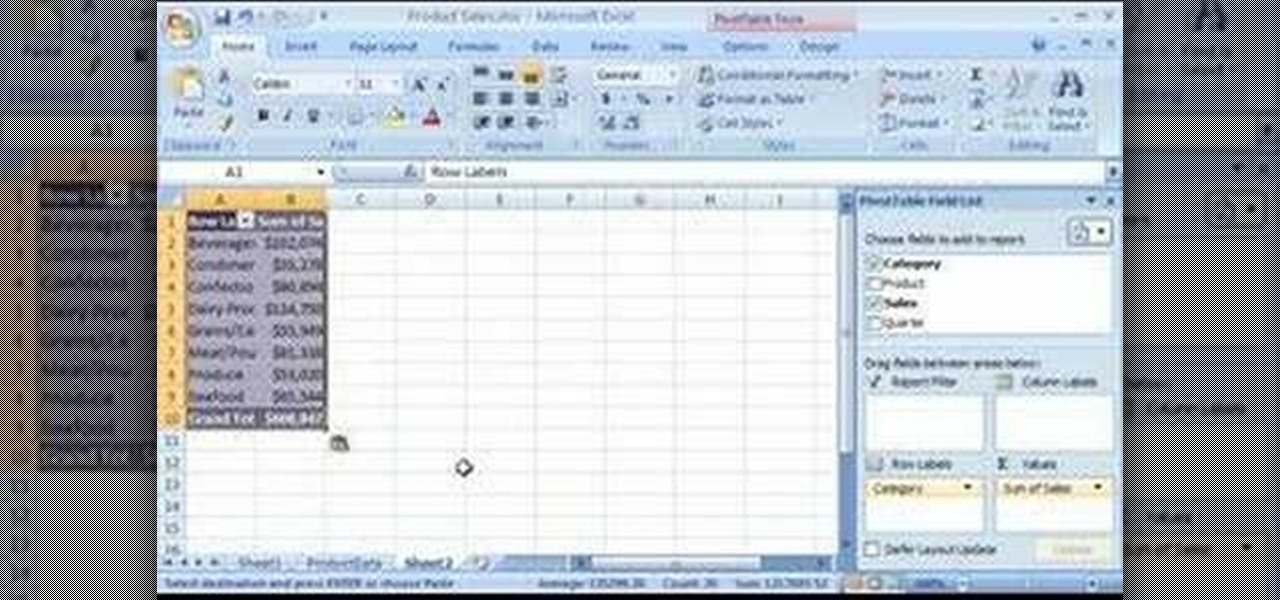
With PivotTable reports in Microsoft Office Excel 2007, your sales report will sparkle with power, flair, and functionality. Take a look at this instructional video to learn how to show the big picture, show all the details, or show anything in between. Easily create multiple worksheets to switch back and forth between the various versions of your report. Sort, filter, and summarize your data any way you like. Show the details of any summary value in your report.
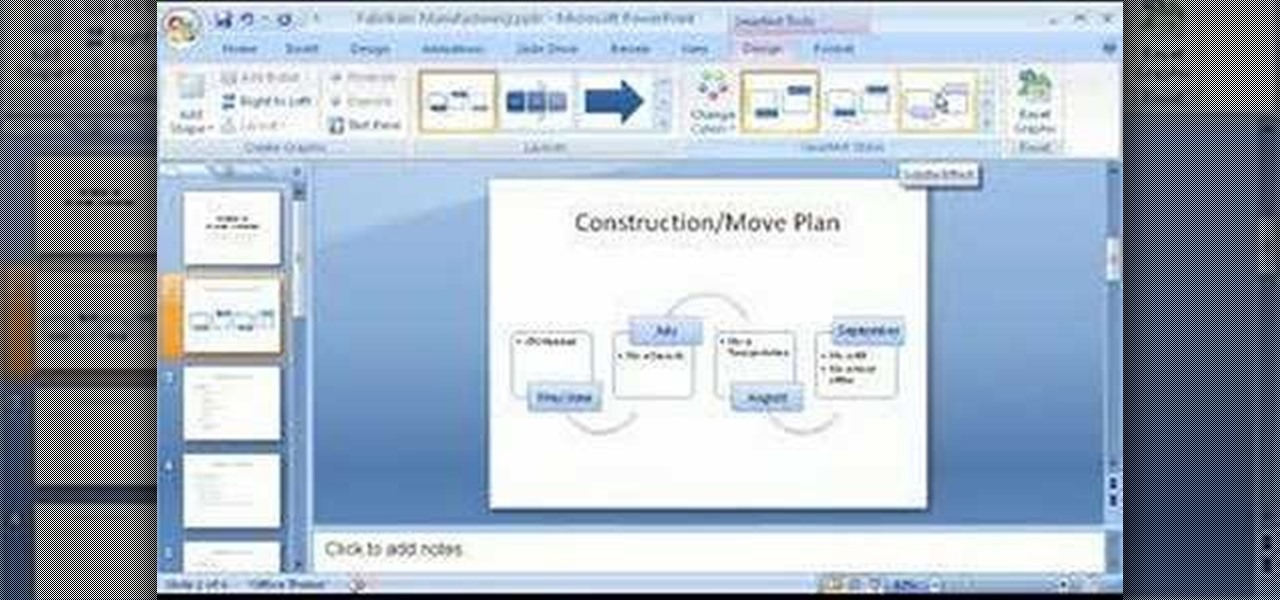
Learn how to add color, shape, and emphasis to your text and data in Microsoft SmartArt graphics in this tutorial. See which one works best for getting your point across. An organization chart? A time line? A process with sequential tasks? Non-sequential items? Pick one, and optionally customize it with colors, animation, effects such as shadows, bevels, and glows, and more.
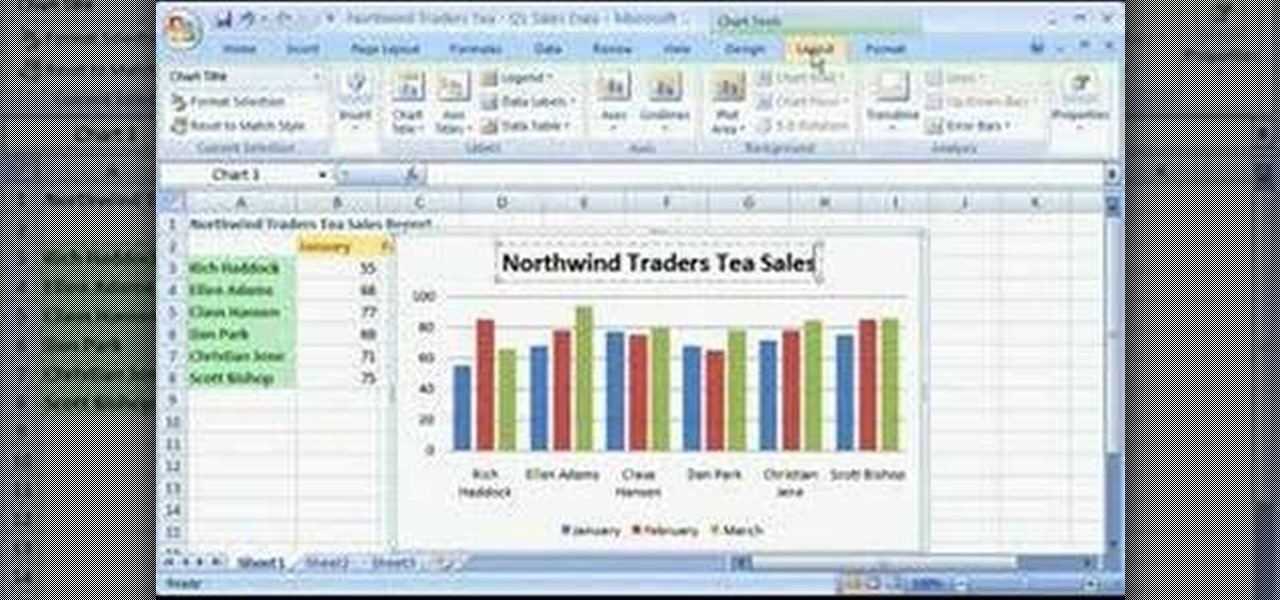
Check out this tutorial and learn how to create chars in Excel 2007. In Office Excel 2007, you just select data in your worksheet, choose a chart type that best suits your purpose, and click. Want to try a different chart type? Just click again and select a new chart type from a huge range of possibilities. Then work with the new Chart Tools to customize the design, layout, and formatting of your chart. You can see how various options would look just by pointing at them.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...
In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...
To unlock Toon Link first go to Subspace Emissary, make sure you've completed it, if not you will not be able to unlock him until you have done so. Go to Subspace Emissary and click on the completed data with the crown and load it. Next go to "The Forest" and choose any difficulty and any characters. Now go forward and fight whatever you by until you reach a door and enter it. Now you'll see Toon Link and fight him and win. After winning you'll unlock him.

In this hands-on workshop, Googlers Mano Marks and Pamela Fox show how to use tools within Google Maps, Google Earth, and Google Spreadsheets to create, import, and edit KML. They also show a quick integration of KML in the Maps API, and briefly mention geo search and indexing. This talk is useful for developers who haven't had a chance to play with the Maps or Earth creation tools yet, and are looking for quick ways to create and share geo-data.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

Discover how After Effects redesigned Motion Tracker (After Effects Professional only) gives you more power to synchronize motion between two elements in a composited scene. Learn how Motion Tracker works by analyzing the moving pixels in each frame and then using that data to control the motion of a new layer. Set as many tracking points as you like or choose from a list of defaults. Also see how Motion Tracker's interface and controls have been simplified to be faster and easier to use.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

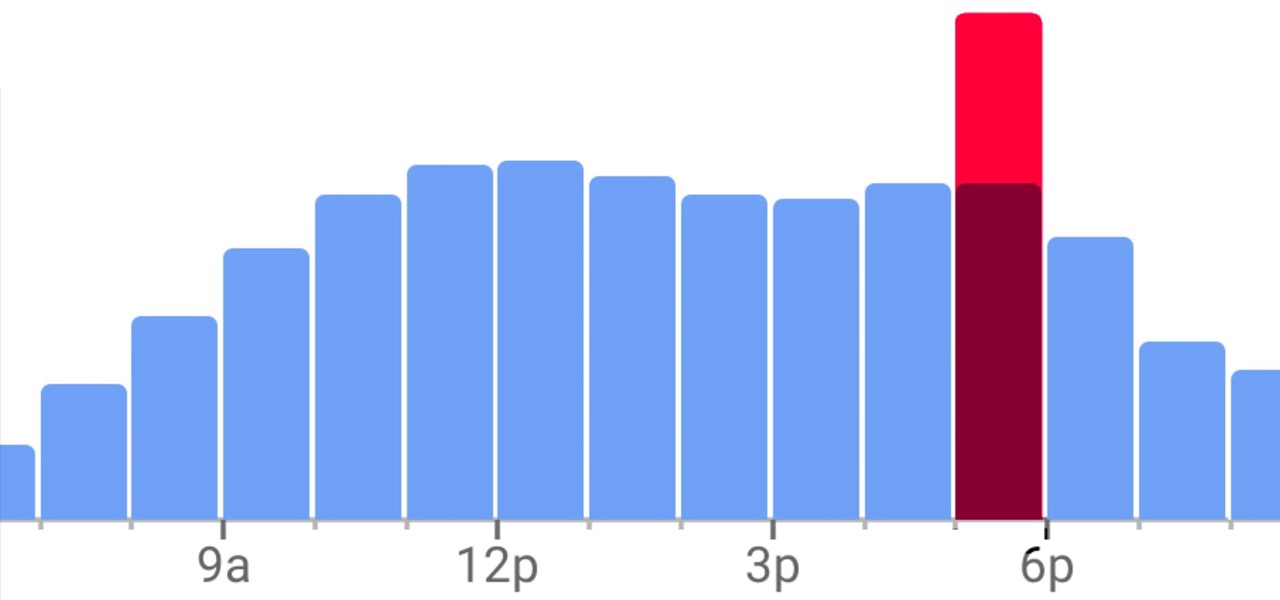
Unlike Apple Maps, Google Maps can tell you when a restaurant, bar, club, or other business you're thinking of visiting is busy. It's extremely helpful if you want to avoid peak times or wait for the place to be empty. If you can't pry yourself away from using Apple Maps, there's an easy alternative to see the popular times of most businesses.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

Fresh software updates can be amazing or a nightmare, but they're mostly the former since new and updated features can give your iPhone improved functionality. There are over 200 benefits in iOS 14 alone, and hopping on the iOS 14.2 beta includes new emojis and fresh wallpapers. For the longest time, however, being away from Wi-Fi meant no update for you. That is, until now, thanks to 5G.

We're living in a world that runs on Big Data. As the driving force behind everything from self-driving cars and Google algorithms to the latest medical technology and financial platforms, massive sets of increasingly complex data lie at the heart of today's most exciting and important innovations.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

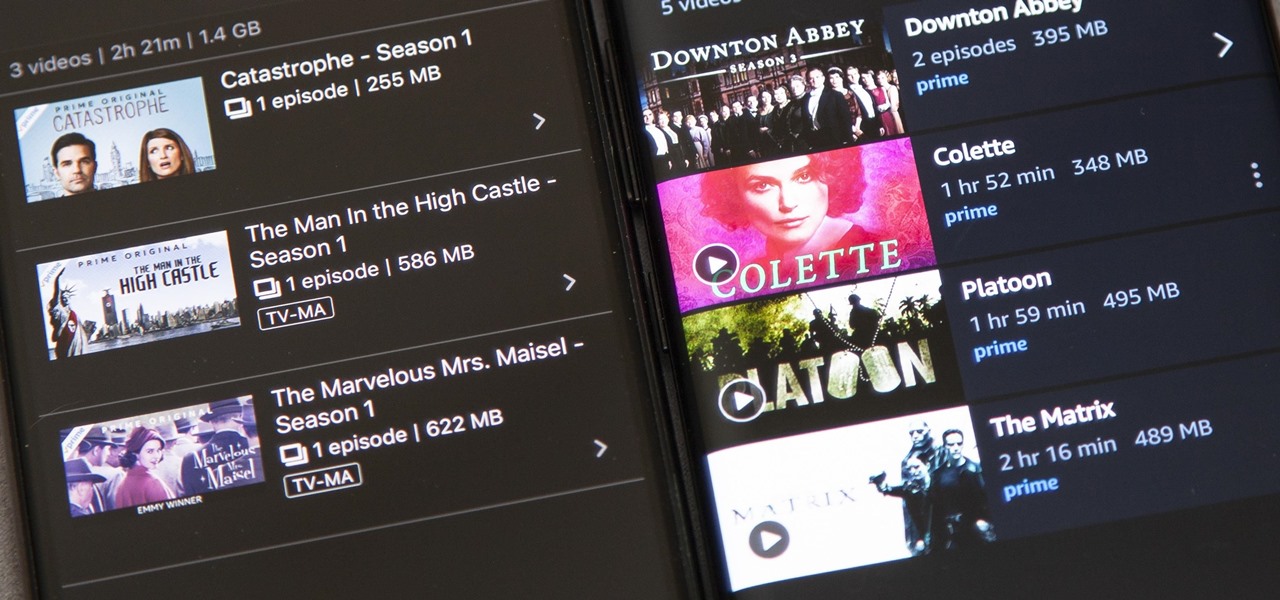
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

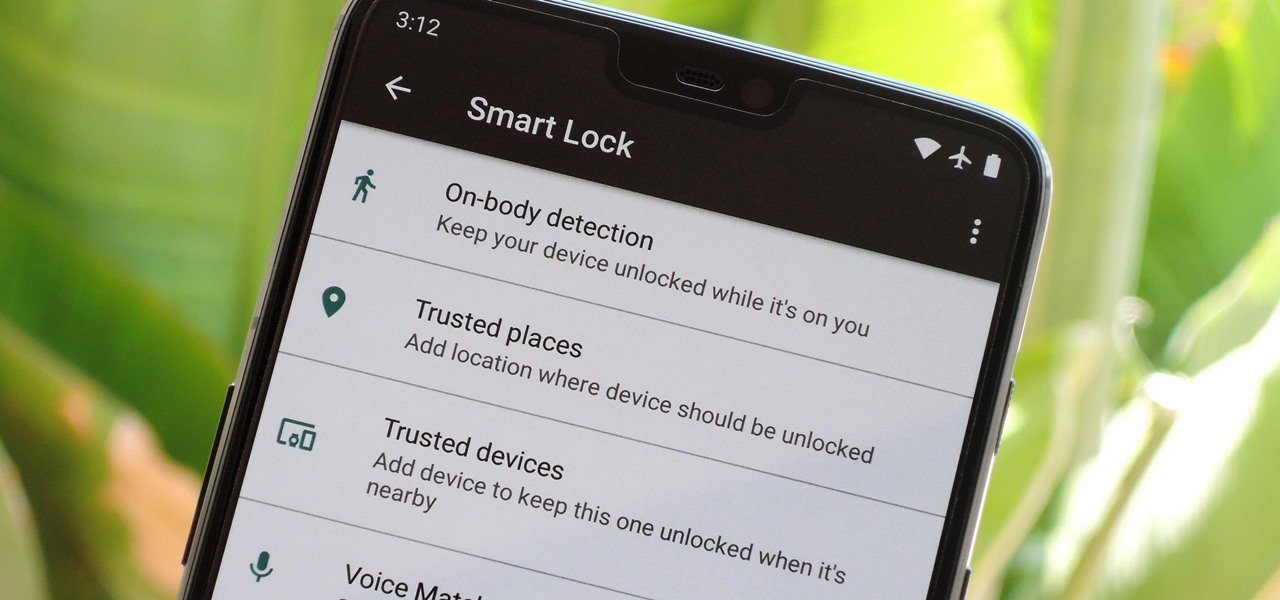
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

The new iOS 11 was just released by Apple, and you can install it right now. Overall, it's got some great features, but how does it fare battery-wise on your iPhone? And how can you increase daily battery life for more juice and less charging every day?

One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught unaware.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Whether it's spotty data coverage, bad customer service, or a high monthly bill, at some point many of us consider changing carriers. The problem is, we often don't want or need to change our devices. Since it's now legal to unlock devices to bring to new carriers, getting devices switched over is doable, but it's pain going into carrier stores and dealing with their constant upselling.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Sometimes data is lost on your hard drive by accidental deletion from recycle bin, or due to reformat or other reasons. In this video the instructor shows how to recover data even after a reformat. Contrary to popular belief that data is completely lost after a permanent deletion or reformat, it is possible to retrieve the lost data using some tools. It is only that windows cannot locate the data after deletion which is still present in the lower levels of you hard disk and to retrieve this y...

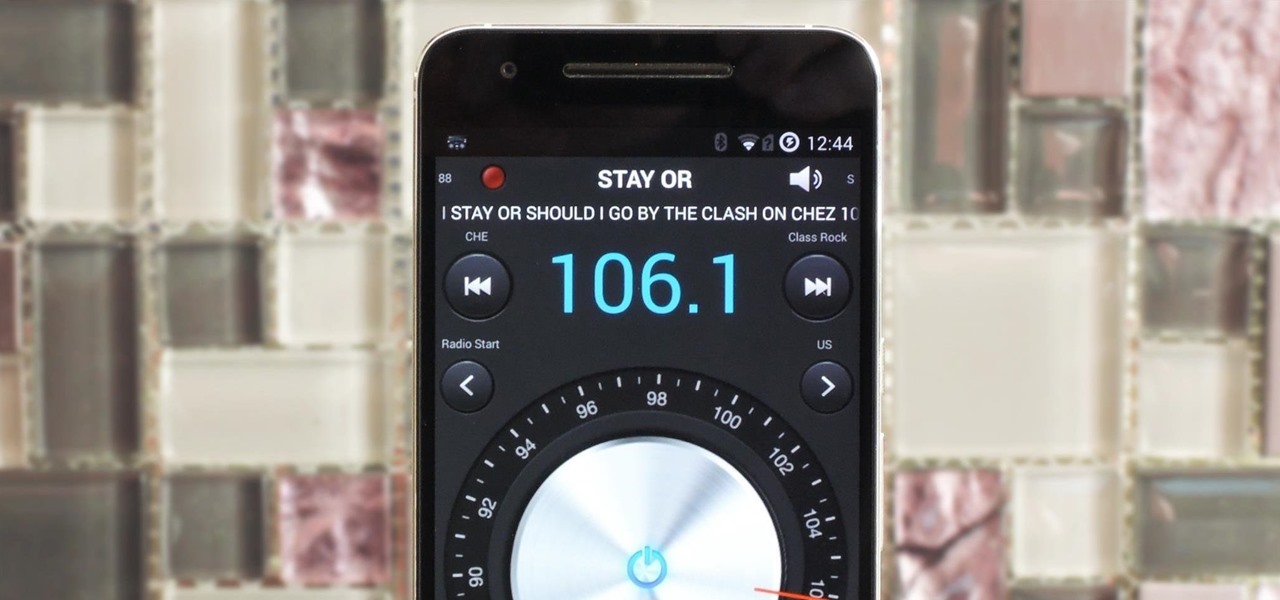
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?