Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.
While it may not serve much of a purpose here in sunny Los Angeles, it's still a good idea to keep constant tabs on the weather forecast, because you don't want anything to rain on your parade.

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless.

A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.

If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

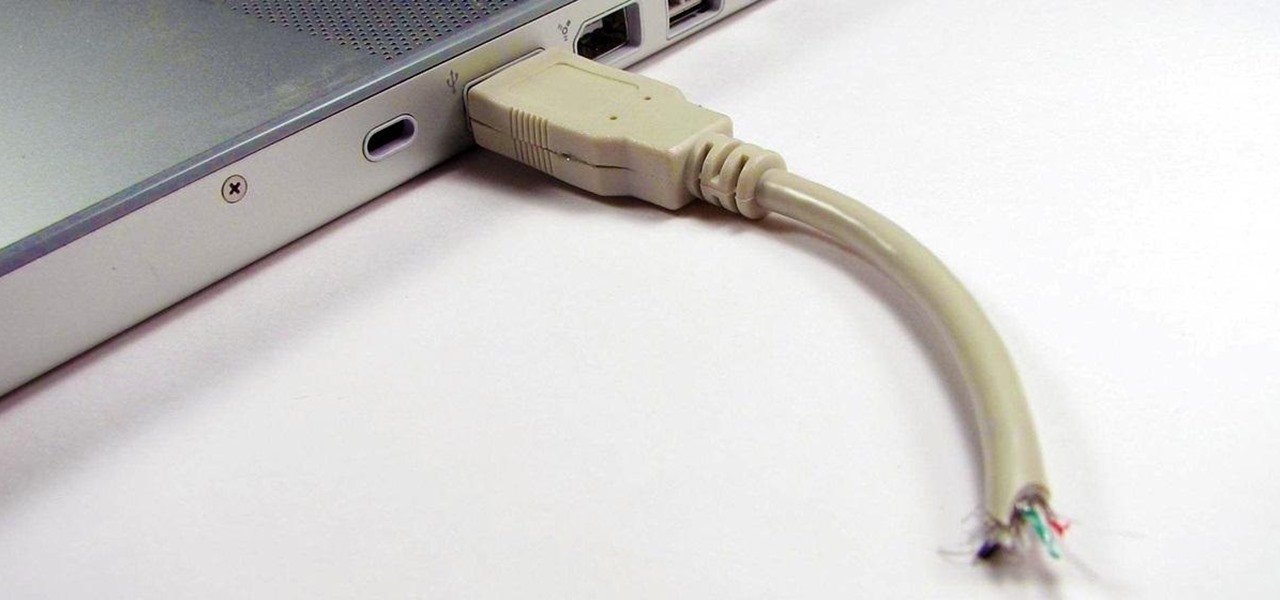
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...

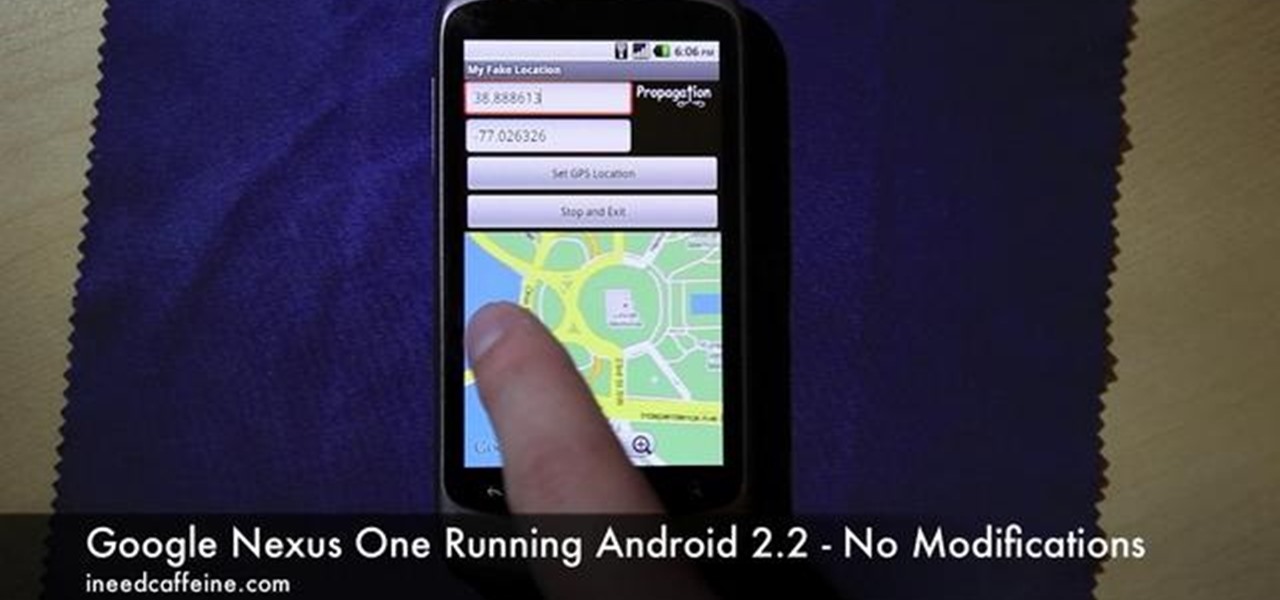
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, even Android mobile devices.

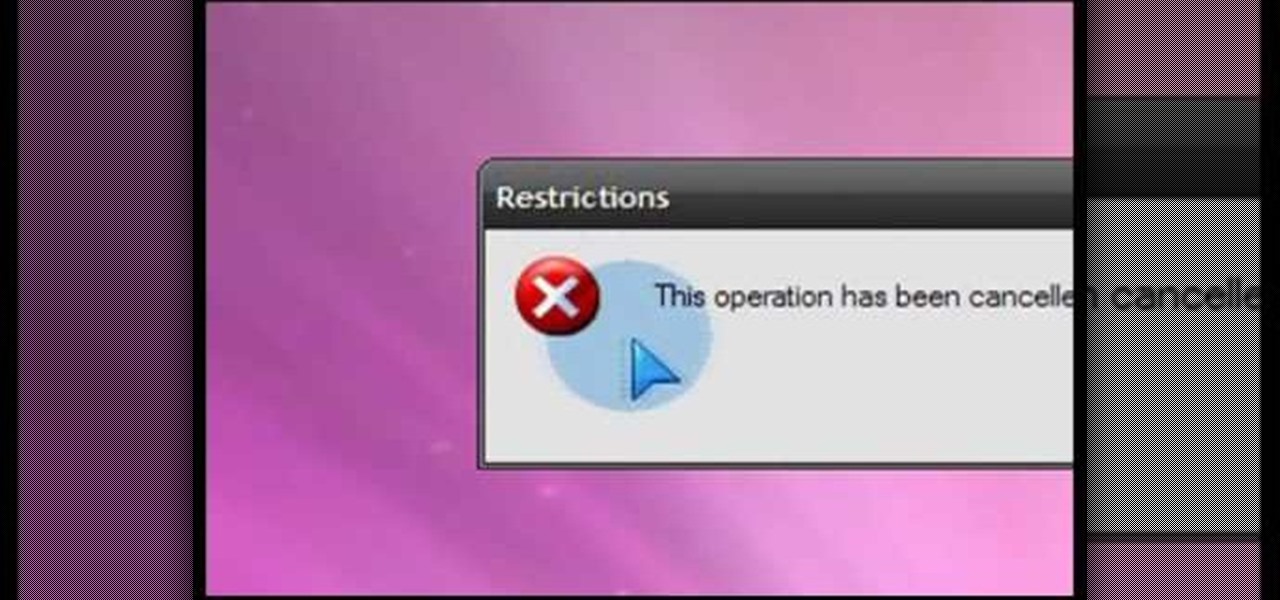
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."

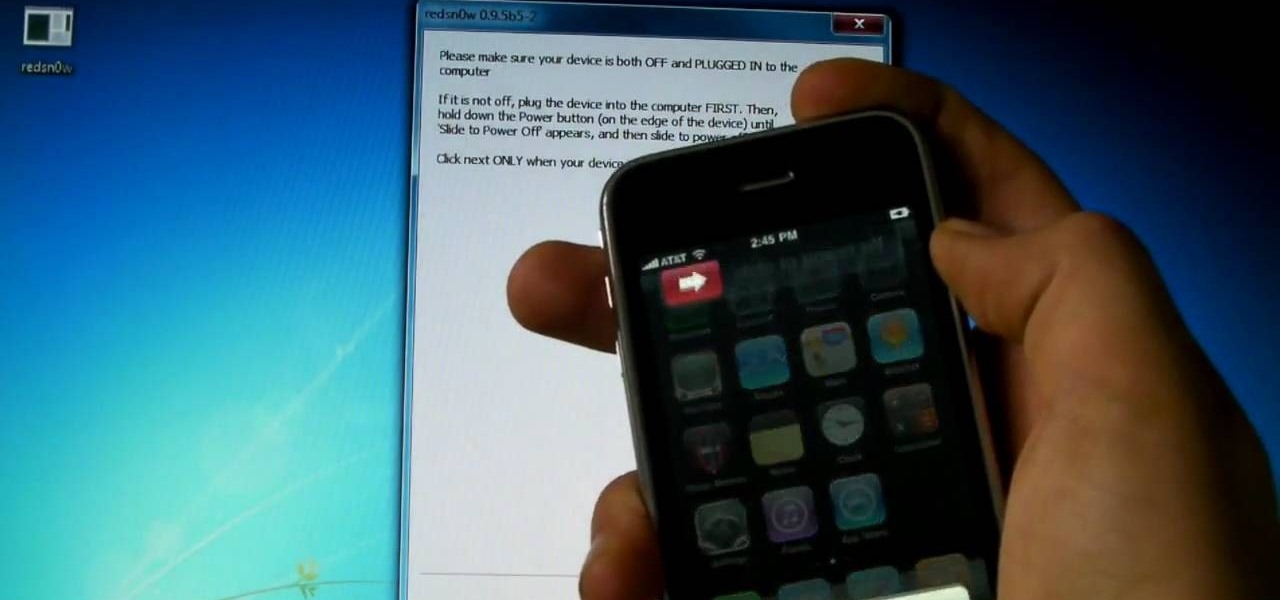
As of today, there are no legal barriers standing between you and jailbreaking your iPhone, iPad, or other mobile device. Hooray! If you were afraid of Apple coming to your house at night if you jailbroke your phone, you can finally let go of the fear and make your iDevice the beast it should have been all along! This video will show you how to jailbreak a iPhone 3G or iTouch 2G with iOS version 4.0 or 4.0.1 using Redsn0w. Now you can fully enjoy your Apple device.

In this how-to video, you will learn how to replace a hard drive in a 2008 Macbook Pro. Make sure you use the proper anti-static precautions before replacing the device. You will need a T6 screwdriver and a Phillips screwdriver. Make sure you transfer your data from the old drive to the new one before installing. Shut down the computer, close the lid and turn the laptop over. Remove the battery cover and battery. The hard drive is held by a plastic retaining bar. Loosen the screw holding the ...

To install a hard drive in a 13" (13 inch) Macbook Pro laptop computer released in 2009 you will make sure to first transfer all data off the drive then discharge any static electricity from your hands making sure your are in a static free work environment. Next you will remove the old hard drive, to do this flip over the laptop and remove the 10 screws around the edge of the device with a #00 Phillips screwdriver starting with the three longer screws on the top right. Next, lift off the bott...

In this how-to video, you will learn how to install a hard drive into a 17" Macbook Pro. Make sure you use the proper anti-static precautions before going on with this procedure. You will need a pry tool, a Phillips screwdriver, and a T6 screwdriver. Make sure you transfer your old data into the new drive before installing. Shut down the computer and flip the laptop over. Unscrew the ten screws around the bottom. Now, remove the cover. You will see the hard drive at the lower right. Loosen th...

In this video from MacOSG we learn how to install a hard drive in a 15" Macbook Pro from around 2009. For this you need a #00 Phillips head screwdriver and a T6 Torx screwdriver. Make sure you use proper anti-static precautions with this. Transfer your data to the new drive before installing. To remove the hard drive, flip over your Macbook. Use your Phillips to remove the 10 screws. Remove the 3 at the right which are longer than the other screws. Then remove the left most screw which is the...

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

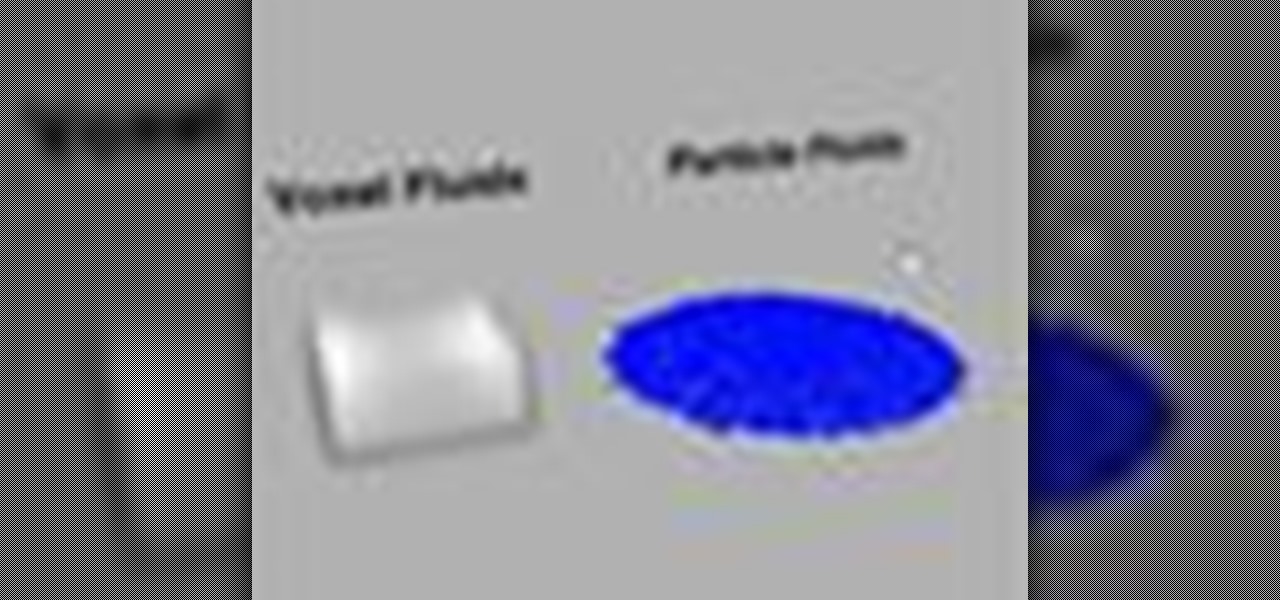
Created by Houdini Product Specialist Stephen Tucker, this crash course series focuses on the concept of fluid dynamics and how they work within Houdini. These videos on Voxel Fluids should help any artist get up in running with the foundation tools available for creating fluid effects in Houdini 9.5. Topics range from how to create a container to how to gain access to fluid attributes for shading, and even passing data from volumes to particles.

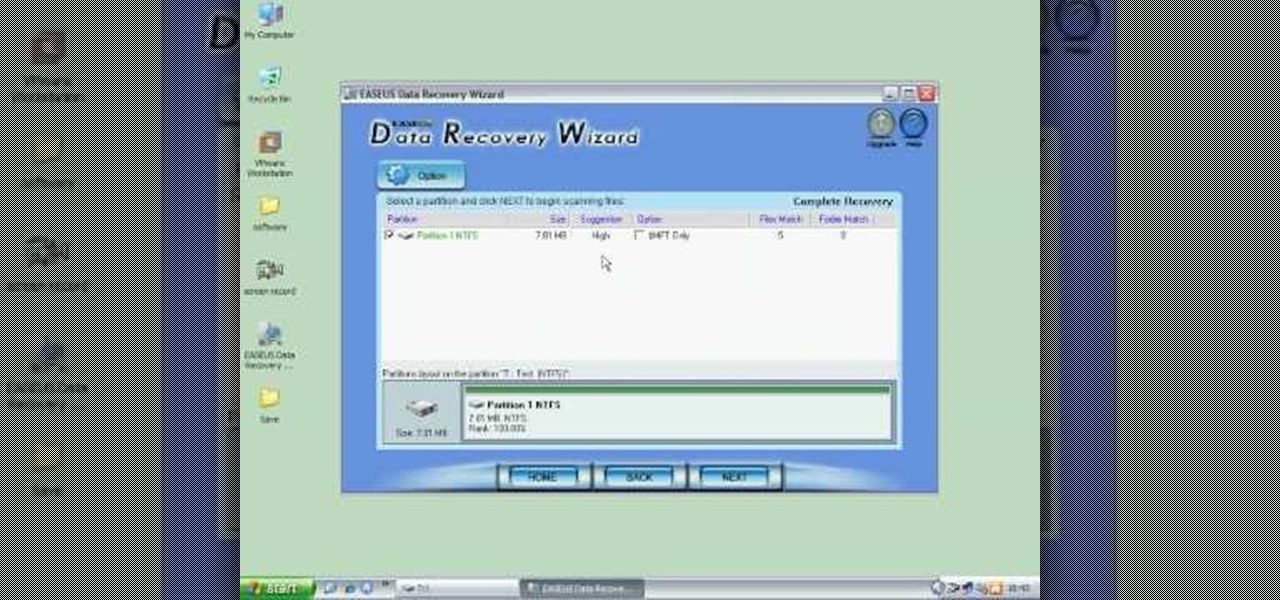
In this video the instructor shows how to restore lost data. When you delete your files you can restore them from the recycle bin. But if a hard drive is formatted all the data is lost and you can not even recover it from recycle bin. In such cases you will need to use data recovery tools to recover that lost data. In this video the instructor uses the Data Recovery Wizard software to recover the data. Start the Data Recovery Wizard. In that there are three options by which you can recover yo...

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

If you're new to DreamCoder for Oracle, one of the very first features with which you'll want to acquaint yourself is the data table browser, which will permit you to display entries in a given Oracle database. For a detailed walkthrough of this feature, take a look at this video tutorial.

This video tutorial will walk you, step by step, through the process of importing data directly from an Excel document to a MySQL database server using the smart copy feature available in the DreamCoder for MySQL. For more information, press play!

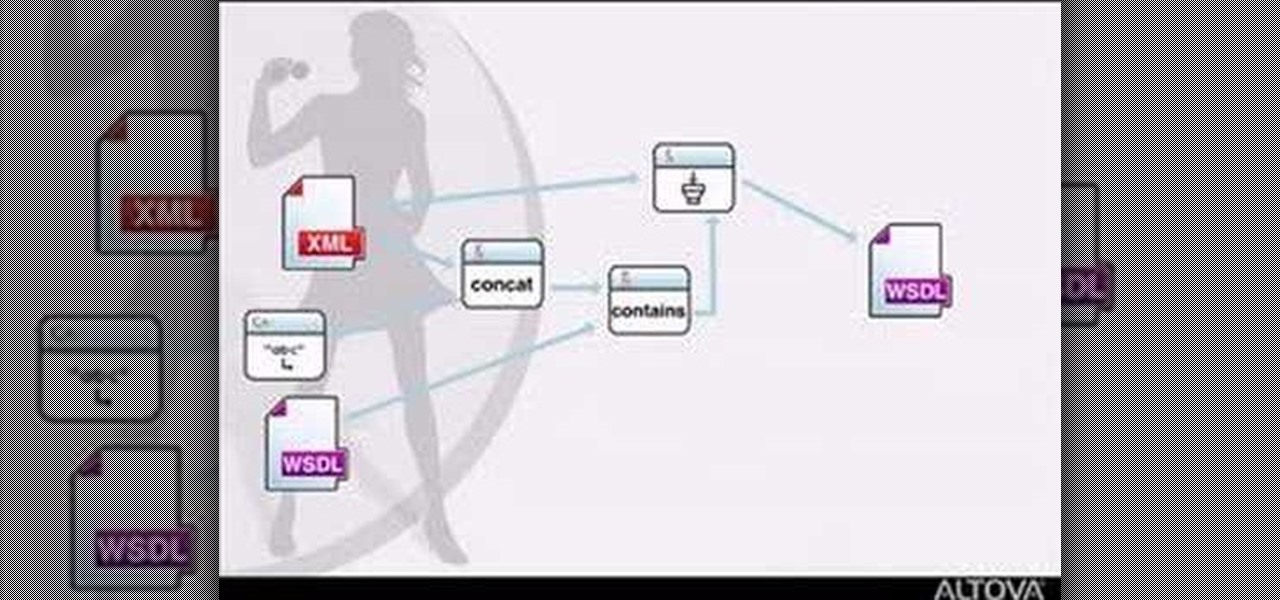
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.