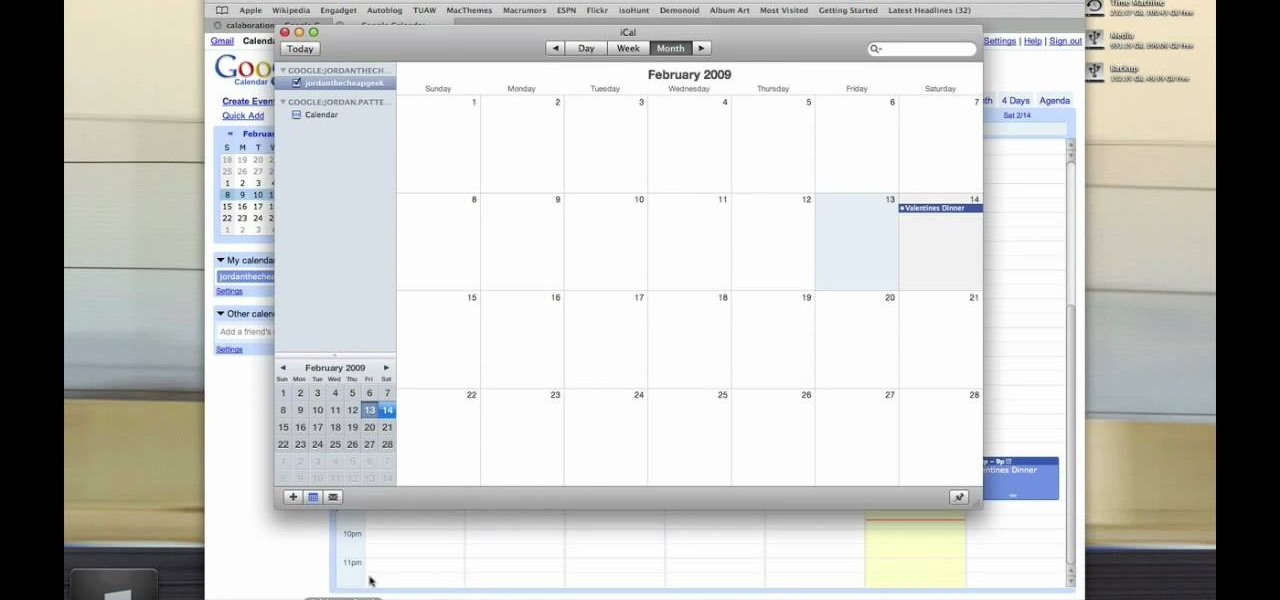
Jordan Patterson the Cheap Geek has made a video showing you the steps to sync your contacts and calendars on three mobile devices together, the iPhone, a laptop running Windows, and a Mac running OS X utilizing a few downloaded programs and Google Calendar. First he shows you how to sync calendars on the Apple computer, by downloading a program from Google code called collaboration code, and then running it. After putting in his g-mail account information, he tells the program which calendar...
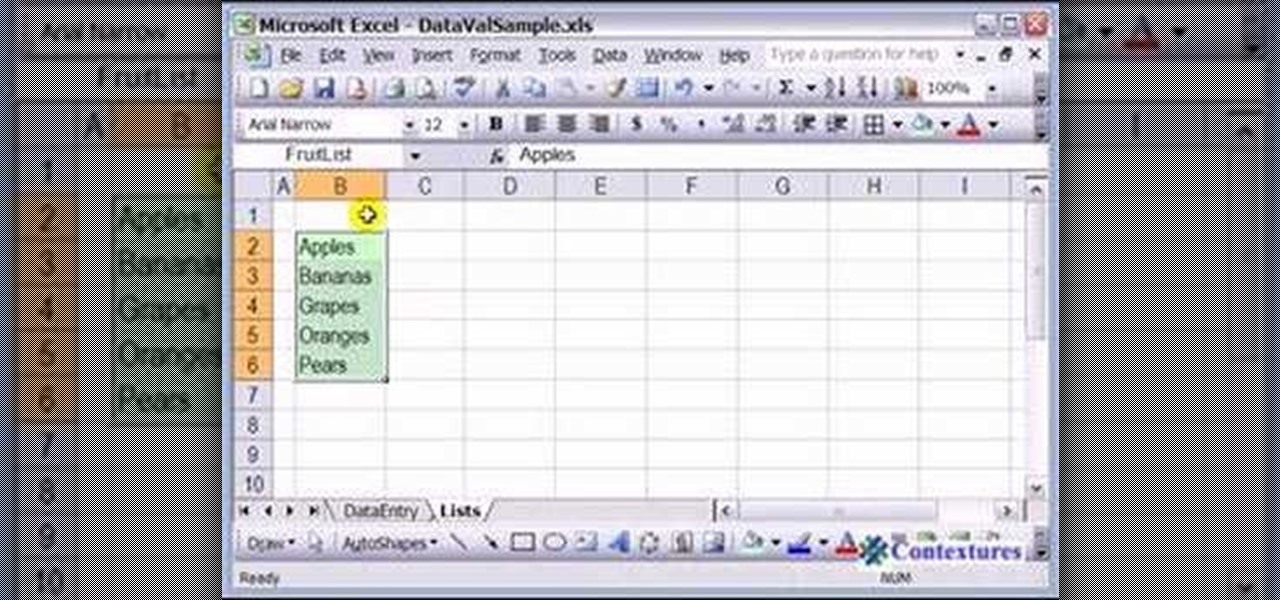
This how to video shows you how to use drop down lists in Microsoft Excel. This will be useful for stores and avoiding people ordering items that are not available. First, type the items in a column. Select them and then click in the name box. Type the name of the list. Note that it must be one word. Now, go back to the order sheet. Select the cell where you want the list to be placed. Go to data and select validation. On the settings tab, choose list and type in = and list name. You can pres...
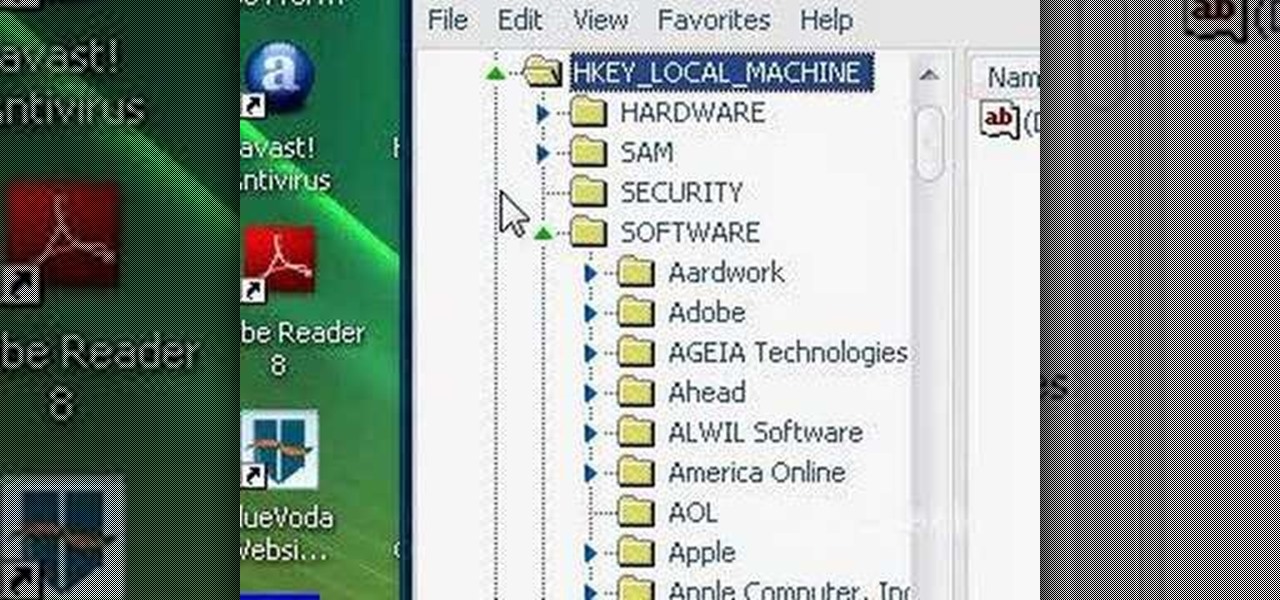
This how to video shows you how to change your computer registration on a computer. First, go to the start menu and select my computer. Right click it and choose properties. You will notice a registered to name. This is what we are going to change. First, go to start and select run. Type in Regedit and click okay. This program will open. Go to HKEY_LOCAL_MACHINE and Software. Scroll down and find Microsoft. From there, scroll down and find Windows NT. Open it and select Current Version. On th...
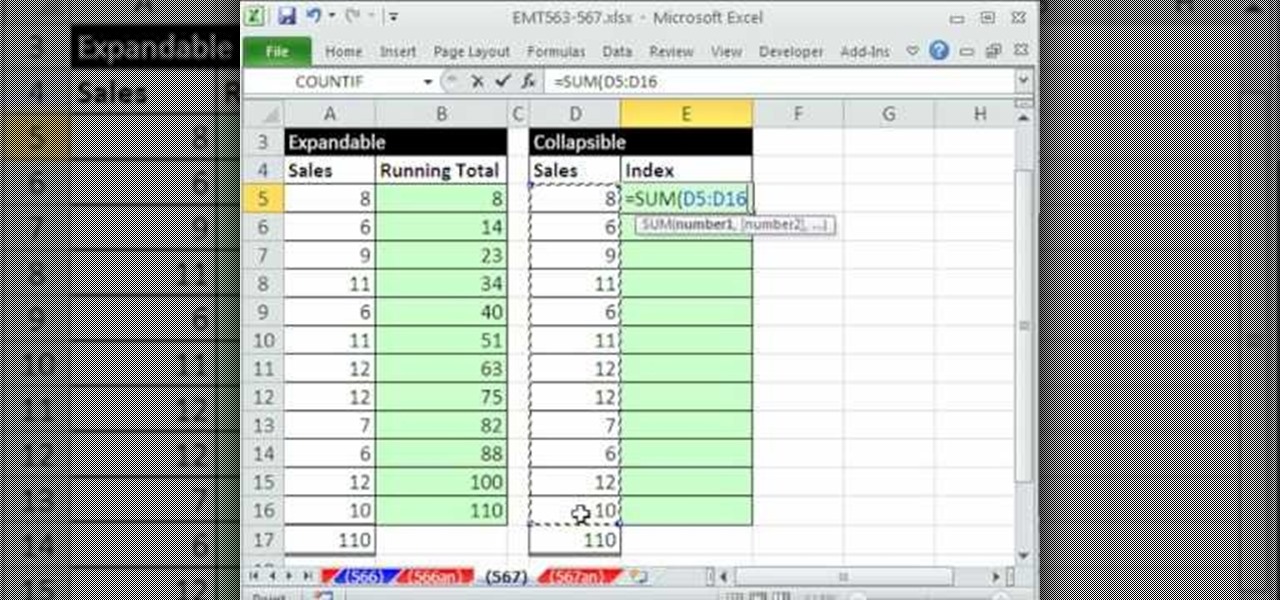
This video demonstrates how to create collapsible and expandable cell ranges in Excel. The first thing that you will have to is to prepare your Excel worksheet that contains the data which you need to be expandable and collapsible. On the first cell under your Running Total column, type in the function, "=SUM". Select the Sales cell corresponding to that cell then type in Shift+Colon. Click on the first value and hit the F4 key to lock your row reference. The result will automatically show. Y...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.
How to sync your iPod to more than one computer

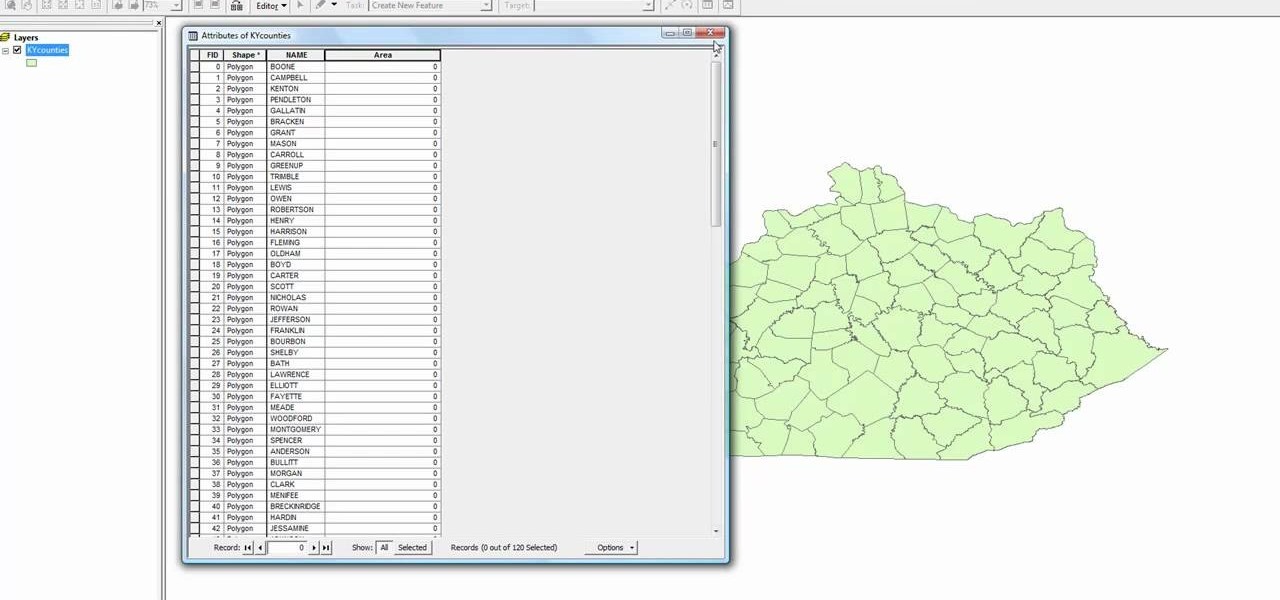
In this how to video, you will learn how to calculate the polygon area in ArcMap. First, open the program ArcMap. Next, go to the left column and right click it. Select attribute table. From here, go to options and click add field. Type in Area and click double. Next, right click area at the top and select calculate geometry. Next, select area disabled. Exit the windows. Next, click the red icon at the top and select data management tools. From here, select project. At the top drop down menu,...

For creating a custom avatar first you need to go to the website FACE YOUR MANGA. There you can find an option named click create to start. Then you click on the create button. Then select male or female. Then you will get a default dude. you can see options like face, nose, eyes, mouth, ears etc on the right side. You can give colours according to your wish. And make whatever changes you want. Once you are done click finish and you will find a pop up box saying that yu are about to download ...

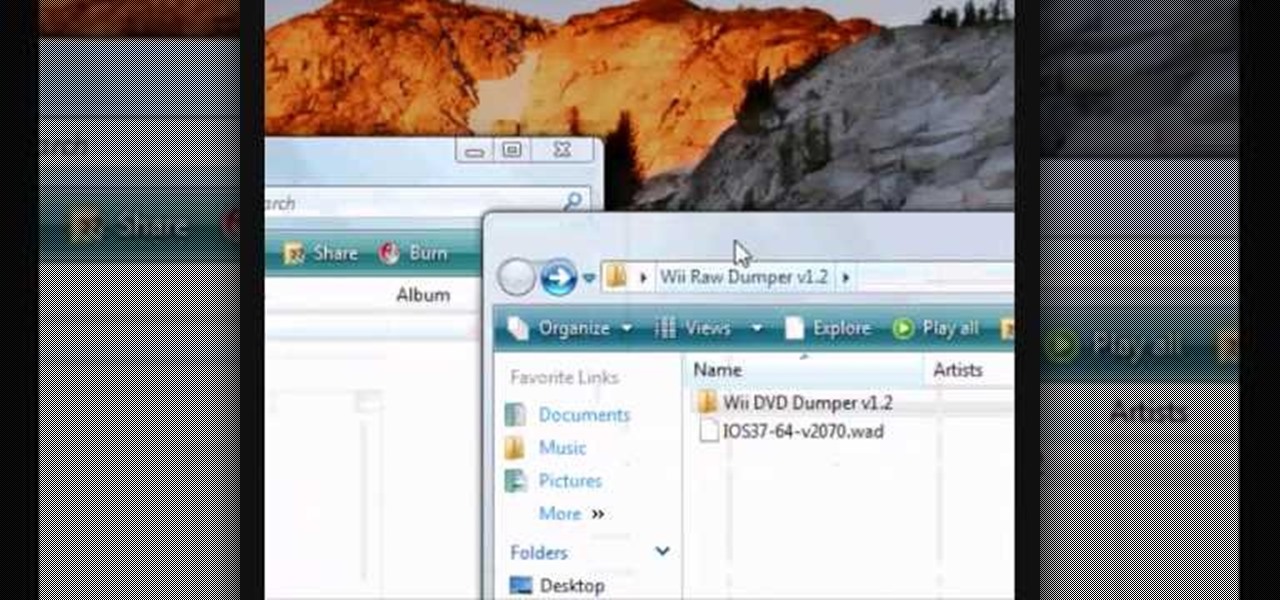
This video tutorial from noxad presents how to backup and burn games for Nintendo Wii game console.To setup game transfer from computer to your console you'll need any type of SD memory card. In this tutorial it's Lexor 1 GB SD card.Insert SD card into your computer card reader. Autoplay window will open, asking what action you want to perform. Select Open folder to view files.You can open SD card manually from My Computer window. (Start button-Computer).Make sure your SD card has folder name...

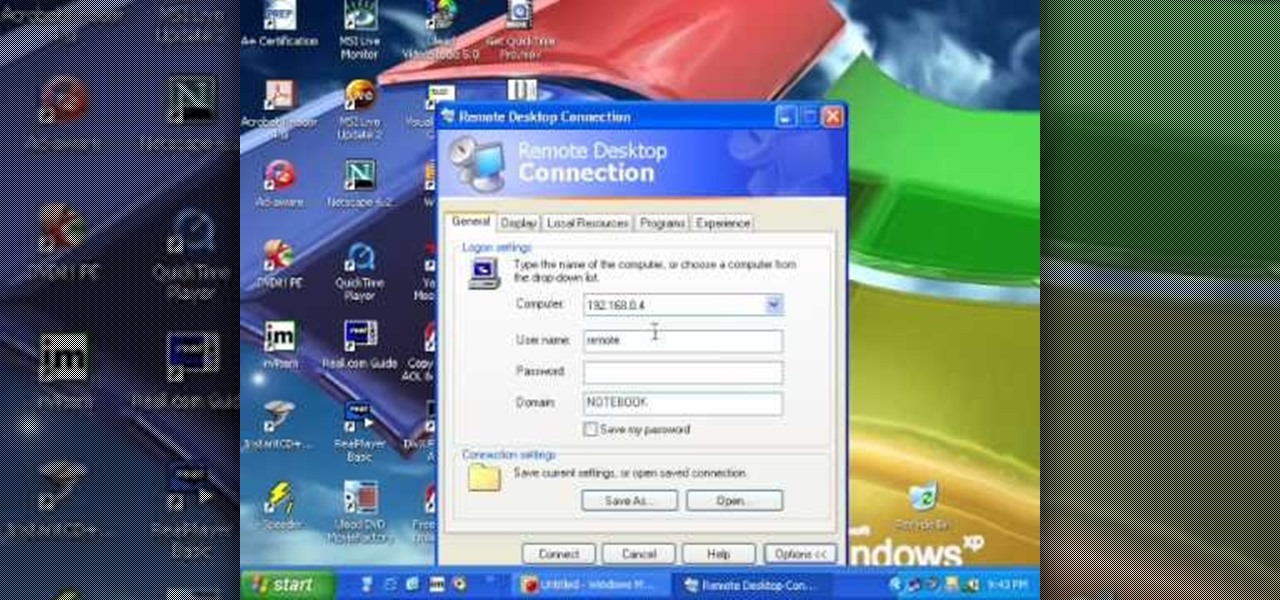
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

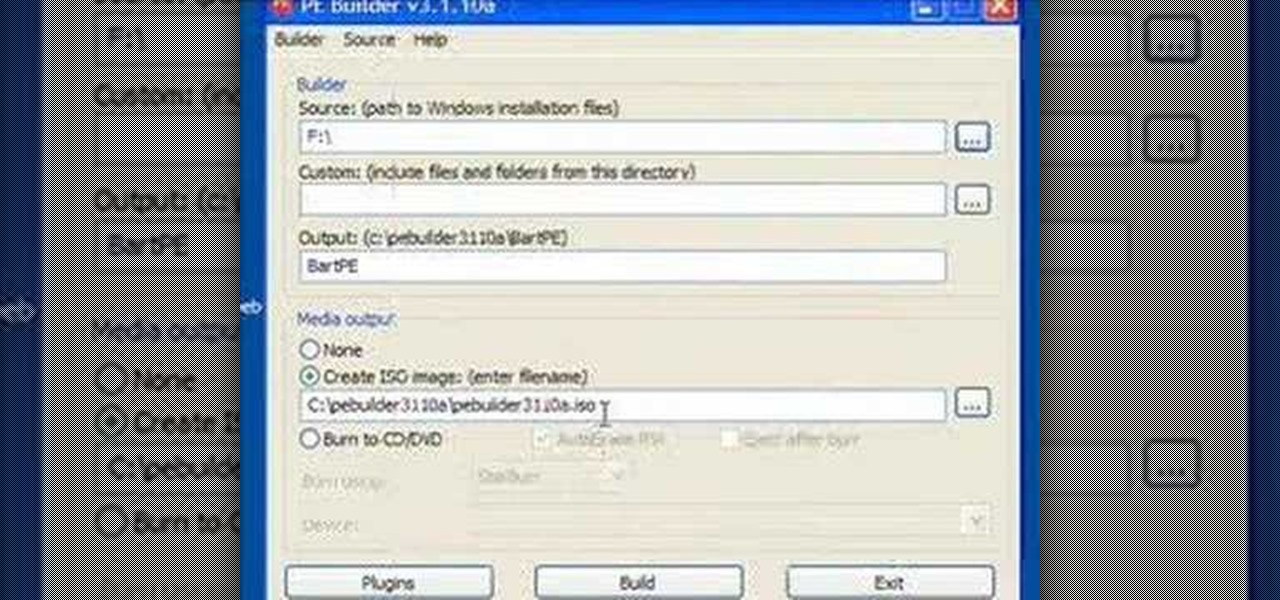
Steve Lee Ignacio explains the procedure to be followed to build a Bart PE Professional Rescue CD. He says that the basic requirements for completing this process is a Windows XP Pro or Home CD, a Bart PE builder, a Windows Computer, a program to burn .ISO files and a CD burner. He then explains the various steps involved in building the Bart PE CD, the first of which is to download latest version of Bart PE Builder using a search engine like Google. Then he explains the second step which is ...

In this video you will learn how to manually white balance a Nikon camera using the Ba-lens. Paul Franklin explains in a few simple steps. First take the lens cap of the appropriate size and put it on the lens. Then go to the camera and set the meter to spot meter he says its important because it measure the amount of light going through the little dome as he shows. Once you've set it all you need to find the white balance button. Then scroll through the icons until you reach preset. Then hol...

Video demonstrates tutorial of how to hide the logical drive icons in Windows. In the demonstration there is two partitions C and D and also there is a DVD drive, DVD Rom and DVD Writer. Here drives C, D and F from My computer is going to be hidden with help of utility called “No Drives Manager”. If you don’t want your young ones to access some of your important data you can hide it. It will just be hidden. This means if go to the address bar and types the name of the drive you can go to that...

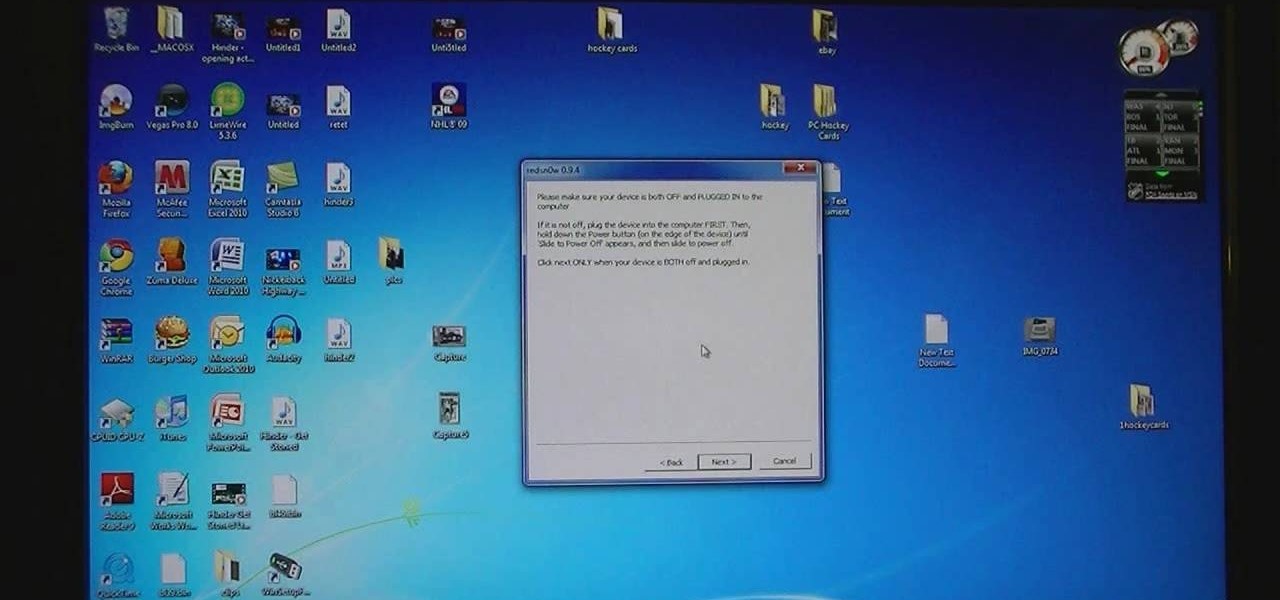
The video describes how to Jailbreak & Unlock your 1st generation iPhone 2G version 3.1.3 and Jail breaking iPhone 3G on version 3.1.3 using Redsnow. The person says that the first and foremost thing to do is to update or restore your iPhone to 3.1.3 version and also remove the SIM from the iPhone. Then you have to download two files from the video description, then launch Redsnow. Then you have to browse the 3.1.2 file that was downloaded already and click on open and then on the next button...

In this beginners video, the instructor shows how to use Word 2007 by opening, closing, and saving documents. When you open the Microsoft Word software with out any documents, the window looks gray indicating the same. There is an office button present in the top left corner of the window through which you can access various options. Click on it, and select the open button which brings up the open dialog box. Now, you can browse through your computer and select any Word document to be opened....

This video shows us how to burn files to a disc using Windows Vista. Insert the blank disc in your computer's recordable disk drive. Autoplay will automatically appear. Choose "Burn Files to disc using Windows". Click next when "Burn a disc" dialog box appears. Empty folder window appears. Choose files that you want to copy and drag them to the window. For example, if you want to copy a photo, click Start menu and open the Pictures folder. Select photos and drag them to the window. Photos are...

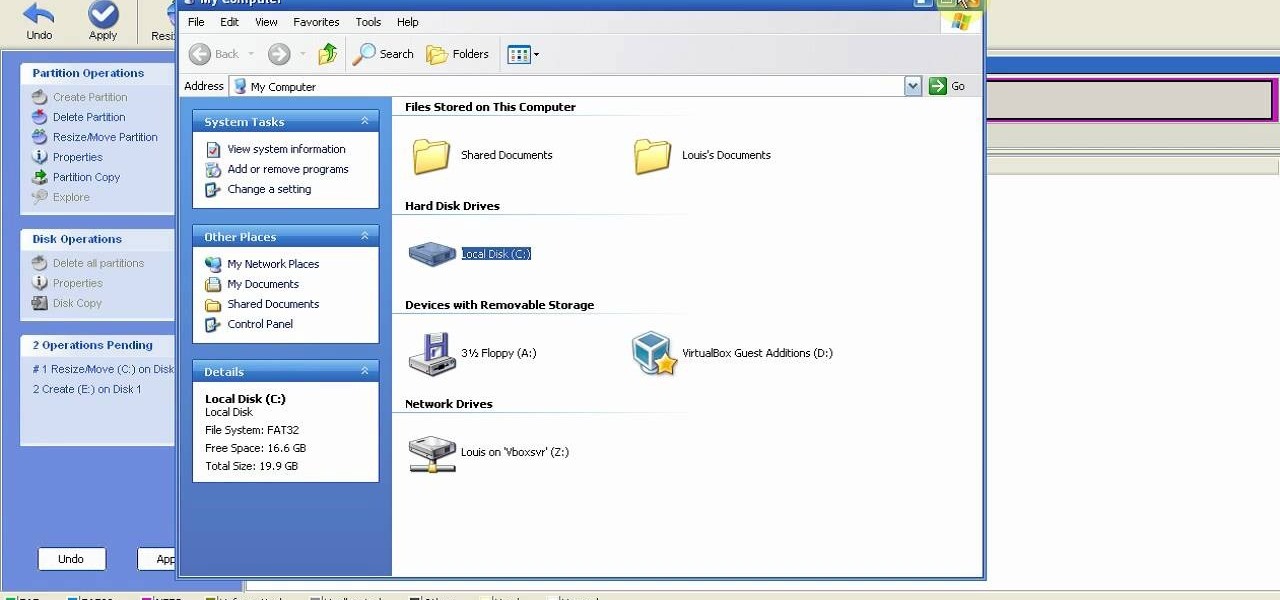
This is a step by step tutorial how to Partition & resize your hard drive with EASEUS. To resize hard drive Open EASEUS Partition Manager. Click on the drive you want to resize. Then click Resize/Move. Go to the end and left-click with your mouse dragging in the direction you want to go. In the display you can see the size that's being created. When you have the size drives you want, just stop and click OK. If you shrunk one drive you can now create a new drive using the unallocated space. Th...

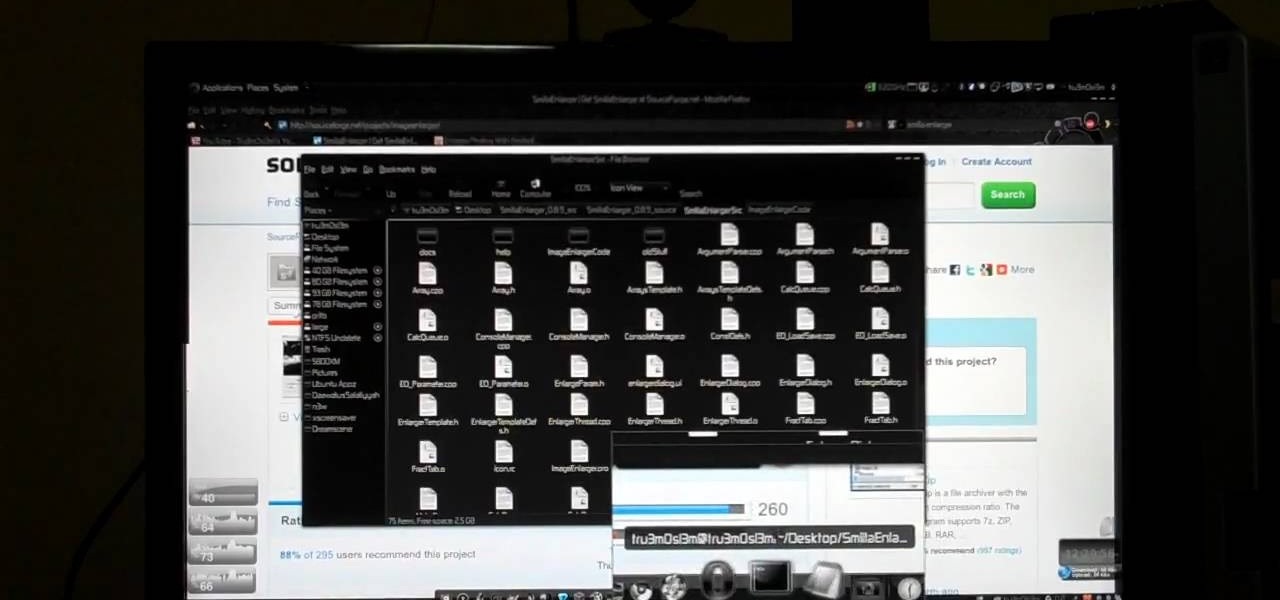
Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

Wearing a seat belt while in a car can save your life. Do you know how to adjust and properly use it? Learn how to drive safe and use seat belts properly (Ford DSFL). A professional driver explains how to fasten your seat belt properly.

What do you know about braking in an emergency situation? If you're not even sure what kind of brakes you have on your car or truck, then you need to do some research. Learn how to drive safe and deal with emergency stops (Ford DSFL). A professional driver explains the differences between braking with Antilock Braking Systems (ABS) and standard braking systems.

Driving a vehicle is a big responsibility and road safety is paramount. Improve your driving skills by using your most important tool -- your EYES! Learn how to drive safe and always look ahead (Ford DSFL). A professional driver explains why it's important to look where you want to go, not at an obstacle, when you're driving.

When you're on the road, you want to be in control of your vehicle. The only way to be in control and improve your driving skills is by having good hand positions and correct and comfortable seating position. Learn how to drive safe with a good hand and seat position (Ford DSFL). A professional driver gives this important tip about seating position.

Did you loose a CD jewel case somewhere in life? Do you have enormous amounts of data cds lying around and have no place to put them? You can make a CD or DVD case out of a simple piece of paper in a few easy steps.

It's easy to restore lost browser bookmarks from a backup copy. Here are step-by-step instructions for Internet Explorer and Firefox.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

Microsoft Excel is one of the most useful tools you can bring into your professional life. However, as useful as Excel is, it can also be difficult to learn on your own. The All-In-One Microsoft Excel Certification Training Bundle is an incredible tool that will take you from Excel beginner to Master for $33.99, on sale for 98% off.

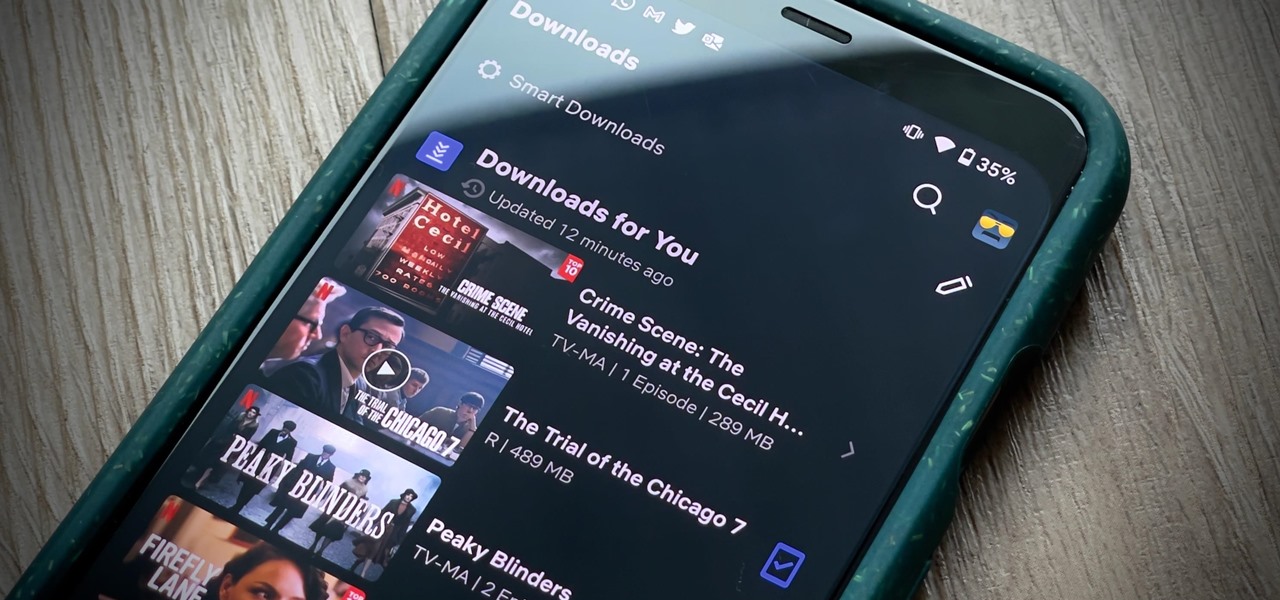
These days, there's more content than ever, and the sheer amount of titles out there can make picking something to watch seem near impossible. Netflix does provide suggestions based on content you've already viewed, which helps, and the company believes so much in its algorithms that it now gives you the option to auto-download videos on your devices based on your interests, no decisions required.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

It's no secret that more and more talented computer science gurus and programmers are turning toward high-paying careers in engineering. Today's engineers stand at the forefront of some of the world's most important and exciting technological innovations — ranging from self-driving cars and surgical robots to large-scale construction projects and even space exploration—and our reliance on these talented data-driven professionals is only going to grow in the coming years.

It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

In the not-so-distant past, cloud computing was thought of primarily in terms of online storage platforms. Now, however, massive cloud infrastructures are used by virtually every major business to reach clients, manage data, and deliver services.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Since its original release as a spreadsheet program called Multiplan in 1982, Microsoft Excel has become the world's premier business software. If you think that it's only good for spreadsheets, you haven't been paying enough attention.

Whatever industry you're in, there's a decent chance you've had to work with Excel — that number-crunching powerhouse that drives the accounting departments of countless corporations across the globe.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.