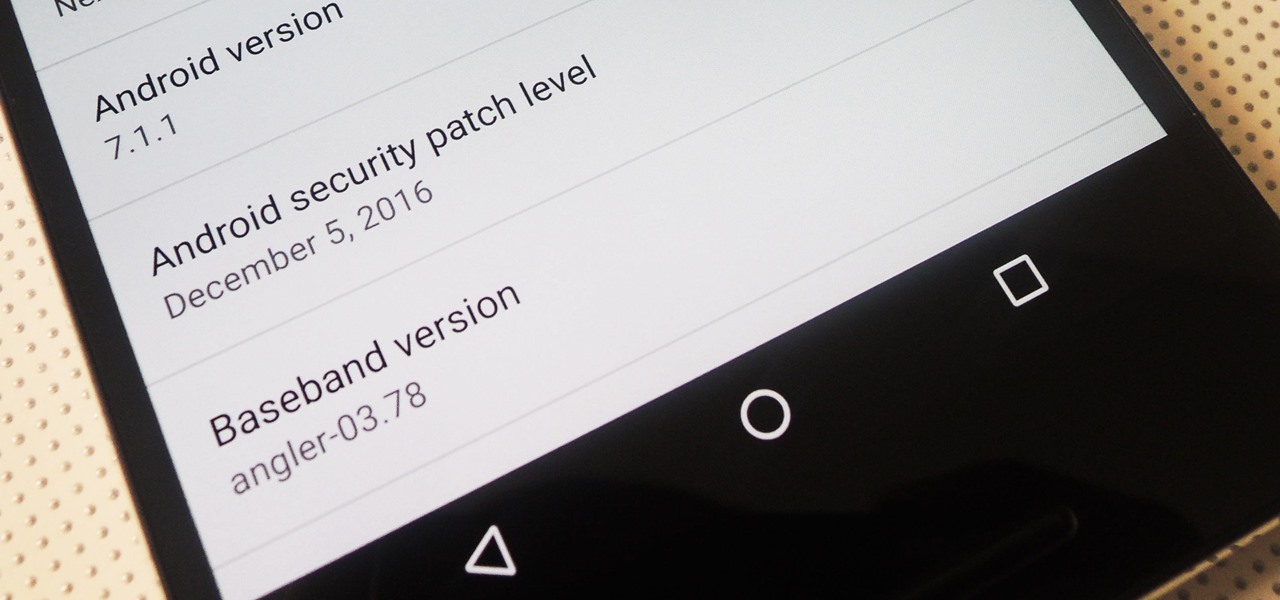
Android 7.1.1 stock images for the Nexus 6P were released last week on December 5, 2016. However, Verizon users seem to have been excluded from the update. Google's factory image page states "All carriers except Verizon" next to version number NMF26F. This doesn't seem fair, especially since Verizon Nexus 5X users received the latest Android Nougat update.

When you're sitting at your desk trying to get some work done, your Android device can be a big distraction. If a text comes in, you have to pick up your phone, unlock it, then respond with the clumsy touch screen keyboard—and by then, you've probably forgotten what you were doing on your computer.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.
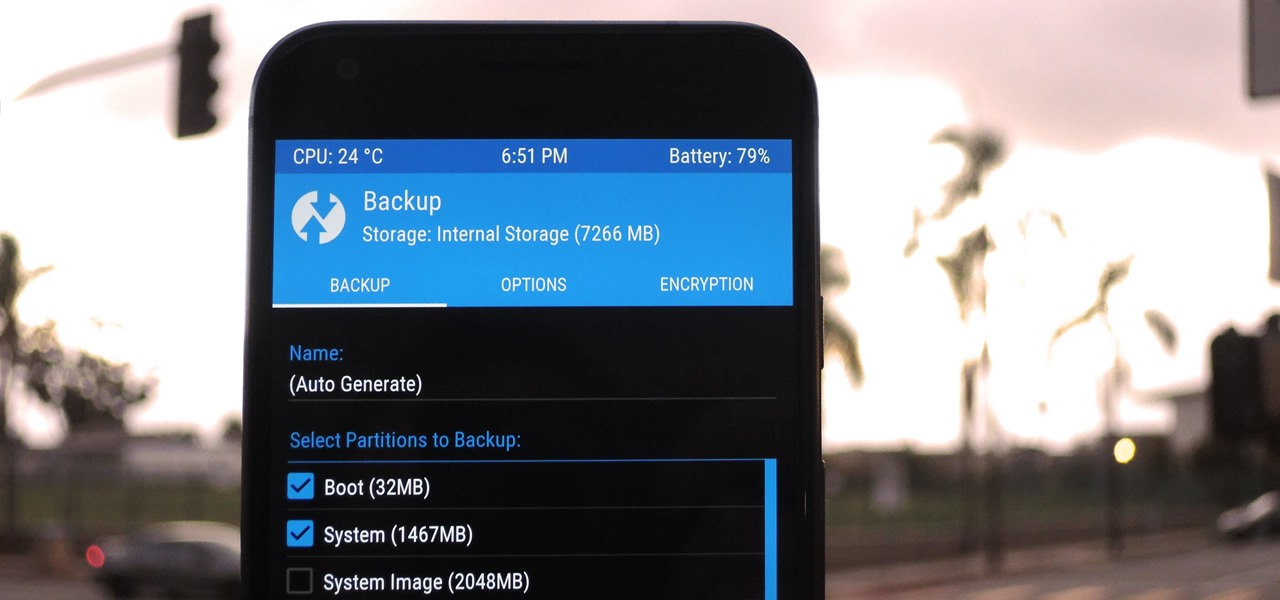
A custom recovery is a very powerful tool. You can flash ZIPs that modify your Android device in ways that not even root can accomplish, and of course you can use it to install custom ROMs. But when you're applying all of these cool mods, there's always a chance that something could go wrong, and you might even end up bricking your device.
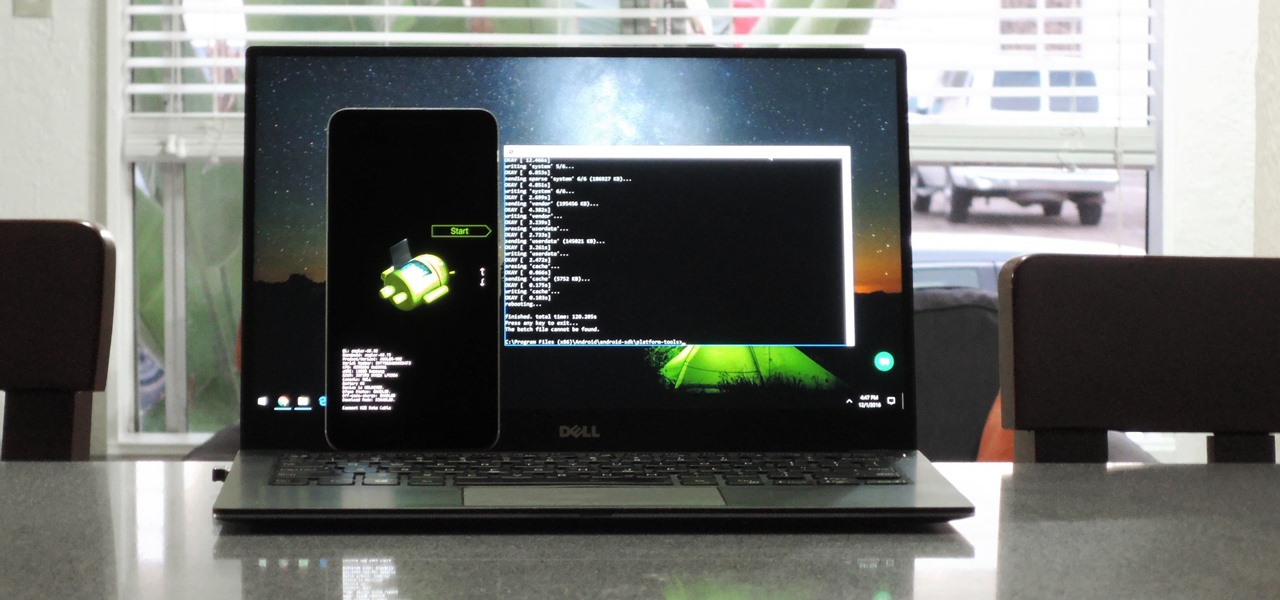
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

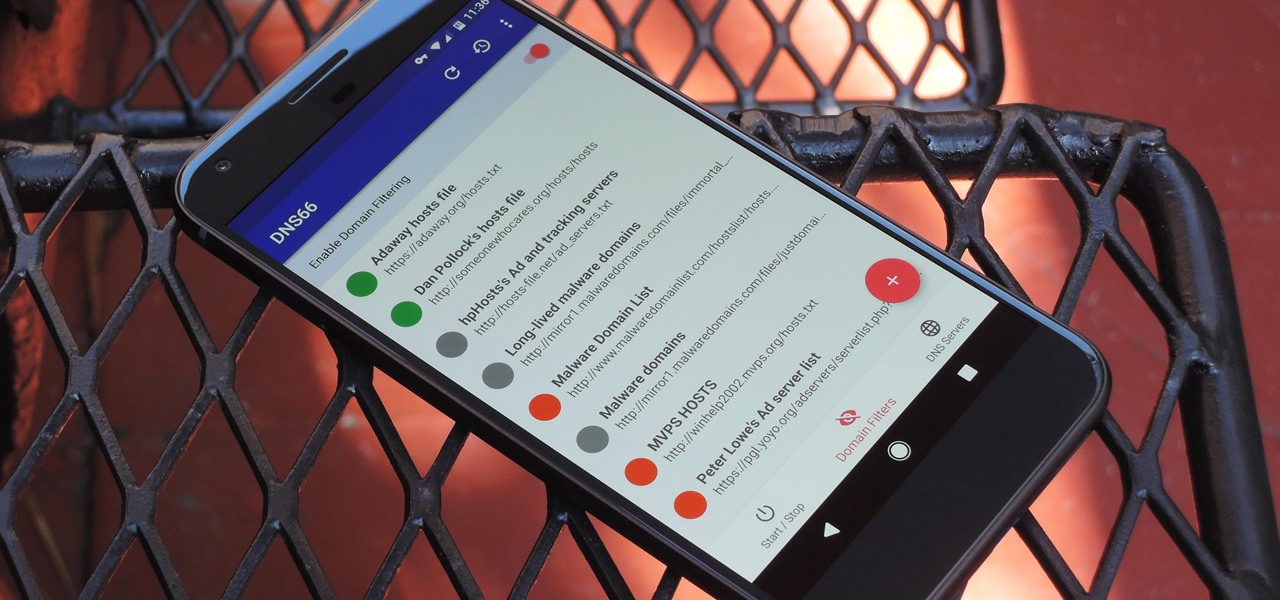
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

Tricking your eyes into seeing 3D images isn't all that hard in movies or even in virtual reality, but when you start projecting holograms into the physical world, you run into some difficult problems. Microsoft obviously figured them out with their HoloLens, but how? The process is pretty amazing.

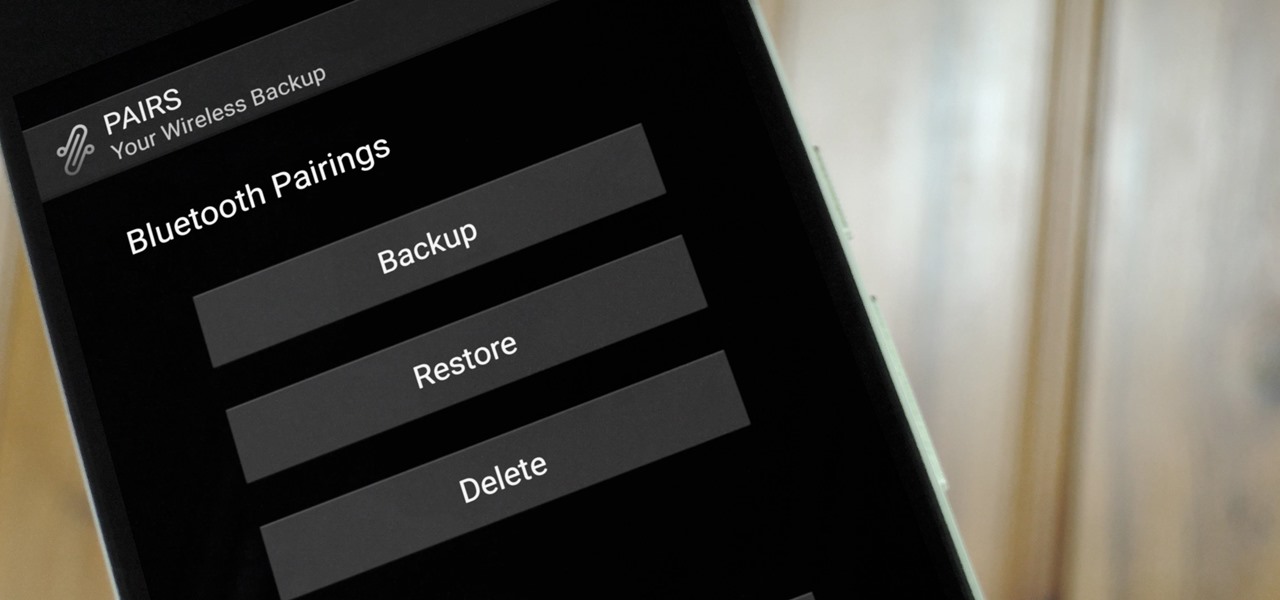
If you enjoy modding your Android device with root utilities, custom ROMs, and Xposed modules, then there's a good chance you've had to factory reset your phone when something went awry. Plus, when you're switching ROMs, it's always recommended that you wipe all data, so us modders spend a lot of time restoring and tweaking various settings.

Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

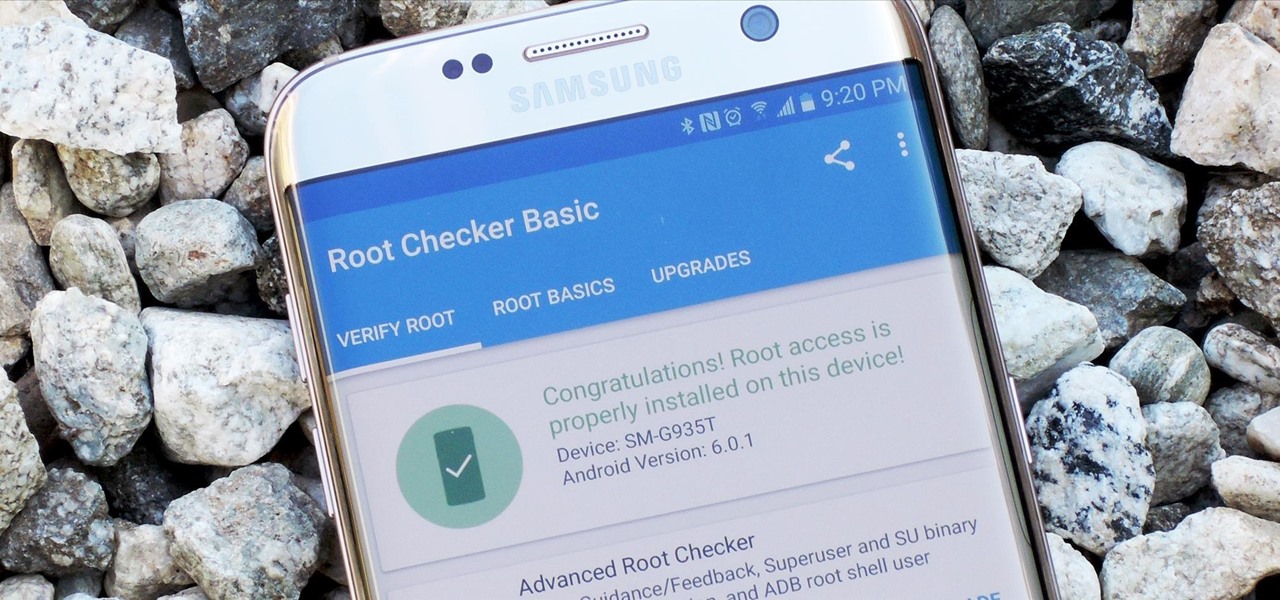
Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

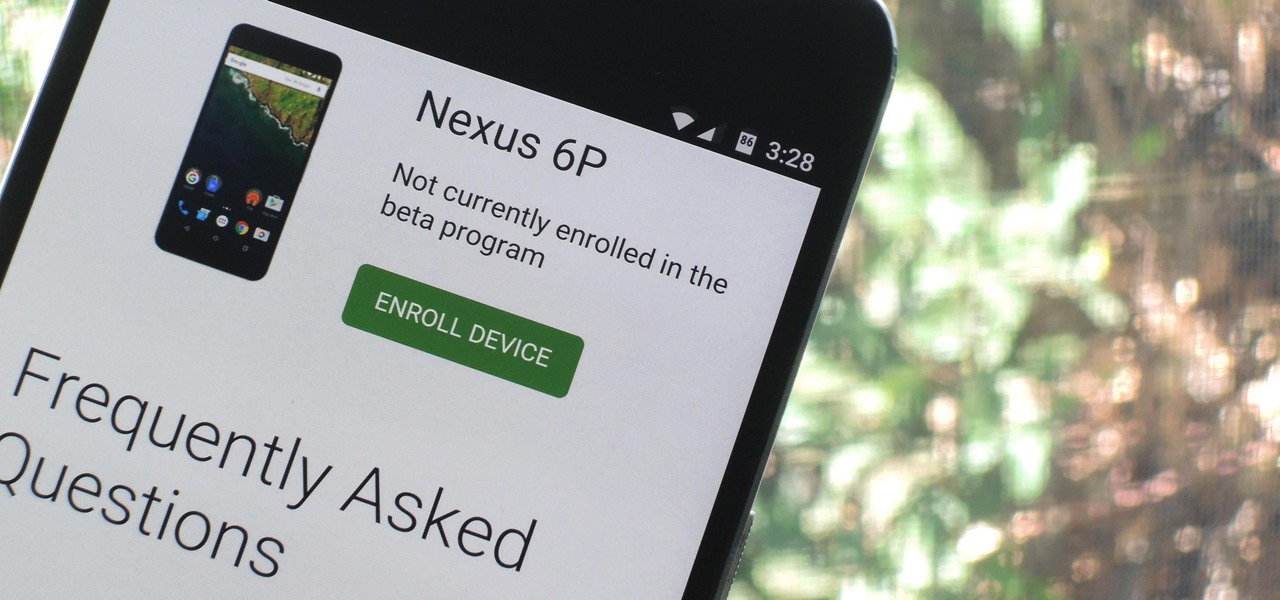
Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Of all the new features in Android 6.0 Marshmallow, an automatic battery-saving function called "Doze" might just be the most interesting. What it all boils down to is that if you set your phone down on a flat surface, the device uses internal sensors to detect that it's motionless and not in use, then responds by drastically scaling back battery-sucking services until the next time you pick your phone up.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.