Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Julian Oliver created the Transparency Grenade in January 2012 for the Studio Weise7 exhibition at Labor 8. It's a transparent device with a "payload" built from an ARM Chip, an Arduino Nano, a mic, and a strong Wi-Fi antenna. It taps into wireless networks and logs emails, webpages, images, and voice to a publicly available online map showing its "detonation" location. Apparently, development for an Android version (sans the pretty plastic shell) is under way thanks to interested donors. See...

Increasingly, I'm turning to Google+ as a source of news, and it looks like I'm not the only one. On Thursday, news of a small earthquake broke on both Twitter and Google+. One curious user, +Keith Barrett, decided to try and find out which social network was faster with the news. Turns out it was a tie. As Google integrates Google+ more closely with the rest of its services, and more users post relevant stories, I think we'll start to see Google+ as a place that can create and break stories,...

Social network fatigue sets in when it starts to feel impossible to keep up with all that new content from your friends, followers, and acquaintances on a daily basis. You lose track of stuff you wanted to read more about, and you miss important news from your friends, but are bombarded with inconsequential details from people you don't actually care about. What's the solution? Filter your streams so that you only see the content you do care about, and get rid of the rest.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

As with +Kimberly Lau, I also had the chance to meet up with all of the Googles and Googlers for the Photowalk in Venice beach on September 1st. I'm still getting used to the idea of another social network, but hanging out with a large group of pro and amateur photographers helped me to jump right into Google+, where I made an album of all the pics I took that day. Even though I had my DSLR on me, I was a little intimidated by the others just as much as Kim with her Samsung Infuse smartphone,...

This week, Google held back on introducing a slew of new Google+ features, and introduced new Chrome extensions instead. The new additions won't replace of your favorite Chrome extensions, but they are very useful, and elegant.

Check into this spreadsheet from +Kimberly Johnson if you want to participate in a Google+ usability study! Although right now it's only open to people in the Bay Area, you can still sign up fo the phone study. Onsite participants get an American Express gift card.

Things have only gotten more exciting for +Bradley Horowitz, VP of Product Management for Google. After launching Google's highly buzzed social networking sites, he took his girlfriend +Irene Au, a designer for Google, to Paris. While there, he proposed to her, and she said yes!

F.A.T. Lab (Free Art and Technology) is a network of artists, engineers, scientists, lawyers, and musicians dedicated to the research and development of new technologies and creative media. They are "committed to supporting open values and the public domain through the use of emerging open licenses, support for open entrepreneurship and the admonishment of secrecy, copyright monopolies and patents."
Social networks play an important role in the life of a blogger, they can deliver, what he writes about what he publishes ... Here are the steps to bind a Twitter account to their Facebook account.

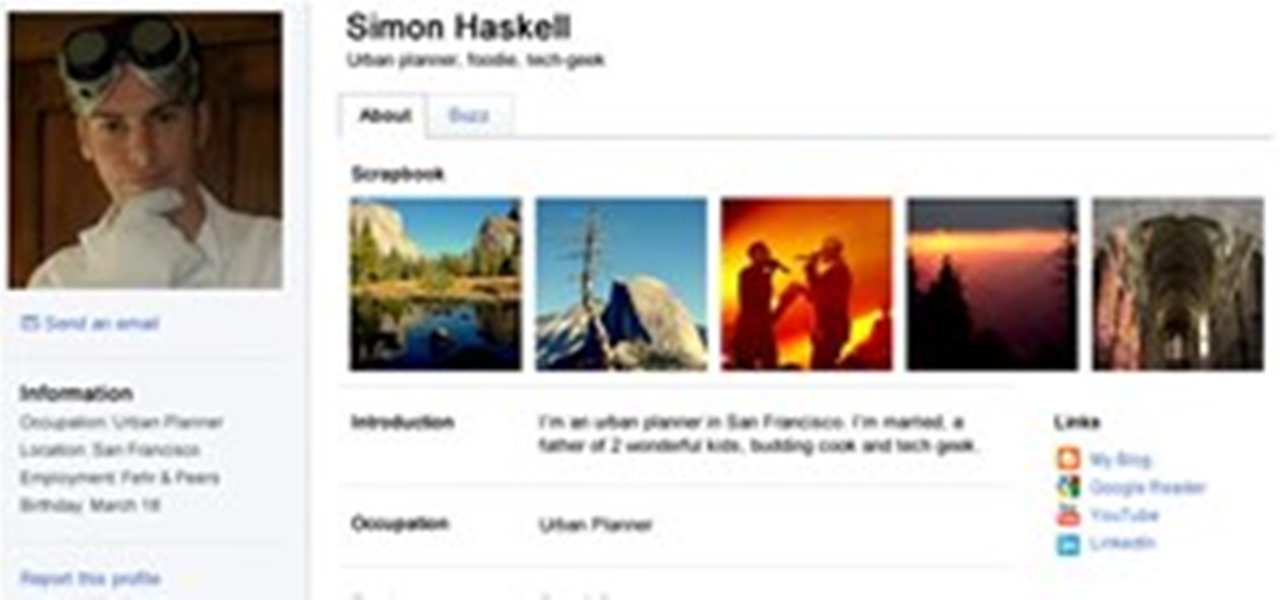
Err, I'd say "inspired" is putting it lightly. A recent Google Profiles redesign reveals a new profile page that looks nearly identical to the current Facebook profile page.

WELCOME & THANKzZz For Your Contribution, Support And Time...! ...Hello, zZz~AKA~StanDP Here...;

I know we have our fair share of FarmVille junkies here at WonderHowTo, but none insane enough to shake a baby to death for interrupting their game (um, I hope). Grisly story:

Life is getting more and more convenient. You can pick up a wireless signal at nearly any coffee shop these days (Starbucks is now officially free in every location across the nation), as well as airports, libraries, hotels and more. However, along with this convenience comes the risk of security breach. Passwords. Emails. Account numbers.

Ok, I know nothing about this, but if this is true, does that mean we can toss out the millions of cables that are hiding in closets, garages and basements? According to the article, there's going to be HDBaseT, which can carry both video and audio signals, and a network connection, a USB connection and electricity with a single cable.

GOOD, a Los Angeles-based magazine focused on doing good in the world, along with LAUSD, The USDA People’s Garden Initiative, The Environmental Media Association, The National Gardening Association, The Urban & Environmental Policy Institute, The California School Garden Network, and Mia Lehrer & Associates, is sponsoring a contest for people to help design a garden for a LAUSD school. GOOD will help build the winning garden design, and they'd like your participation, too.

The Kick Ass Game (PS3, Apple AppStore) From the Official Website ( www.thekickassgame.com ):• 3 playable characters (Kick-Ass, Big Daddy and Hit Girl)

What if you could plan your wedding twice as easily, on half the budget? How does the thought of saving some green - while being green - sound? If this kind of wedding planning is right up your aisle, then you're in the right spot!

After you have your PlayStation 3, you should set up your PlayStation Network account so you can fully benefit from PS3 games. In this video walkthrough, tour everything game related for download onto your PS3. Discover exclusive titles, demos, themes and add-ons to enhance your gaming experience. The PlayStation Store is a simple, user-friendly interface that's easy to use. Download games on your PS3 from the PlayStation Store.

There has been a lot of comings and goings among senior engineers and research staff at a handful of companies with the pretensions of offering the technology that will underpin the driverless revolution.

I felt our community would benefit from this article. Social engineering is a big part of what we do, so it's something you should all become familiar with.

It's no secret that Netflix streams different content based on location. Since your physical location in the digital world is simply a number, a simple switch of the DNS will make your digital "physical location" different. In your Apple TV setting, navigate to:

For a long time, Apple has had Remote—an app that can be used on any iOS device in order to remotely control iTunes. Remote allows users to walk around their home and change the music by simply going through their phone. And now, Android has released its own version of the Apple Remote app! Retune is a free app found on Google Play that has the capability to control iTunes—change songs, TV shows, and movies—using your Android device. You can view the entire iTunes library on your Android devi...

For everyone who's having a problem downloading new apps in iOS 6, or are missing apps that didn't transfer over from iTunes, here's a super quick solution.

With Facebook and Twitter dominating the world, playing chess opposite a real, touchable person is no longer necessary. With the ChessBot, you can now play on a real chessboard remotely - the next best thing to in-person play.

Check out this lesson in KhoeKhoegowab, the Namibian language commonly referred to as Click

Has your hard drive been broken, overheated, or simply worn down from old age? Learn how to recover data from a crashed hard drive with a few simple tips and utilities. Resurrect a crashed hard drive.

This video shows how to connect to a wireless network. Do away with the cords and get on line anywhere in your home and even in your yard. Connect to a wireless router.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Word's been out that there will be a new app coming from the people who brought us Hipstamatic. Well now, those rumours have been confirmed as Synthetic, the developers of Hipstamatic, have just announced a new social sharing app in the form of a disposable camera called D-Series. The D-Series iOS app is set to release tomorrow, December 15th. And the best part about it? It's free!

+Eric Cattell, the Social Graph Technical Lead of Google+, announced a lot of improvements and added features this morning, most of them having to do with circle management and blocking people.

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

There's a lot of talk going around about Google's new social network and how it's heavily influenced by Facebook, but truth be told, how could they build Google+ without taking a note

Charts can be used to visually present your data. In this tutorial we will take a look at how to create basic column and pie charts using MS Excel. Learn it to create a sales chart for your boss! Creat charts in Excel.

Dreamweaver's Validate Form behavior checks the contents of specified text fields to ensure the user has entered the correct type of data. In this Dreamweaver 8 video tutorial you will learn how to create validate forms. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create validate forms in Dreamweaver 8.

Capture photographs on the go, as long as you've got your mobile phone with you. Take pictures, send them via email, or upload them to your favorite social networking site. Watch this video cell phone tutorial and learn how to use the camera on a Samsung Instinct. Take pictures on a Samsung Instinct cell phone.