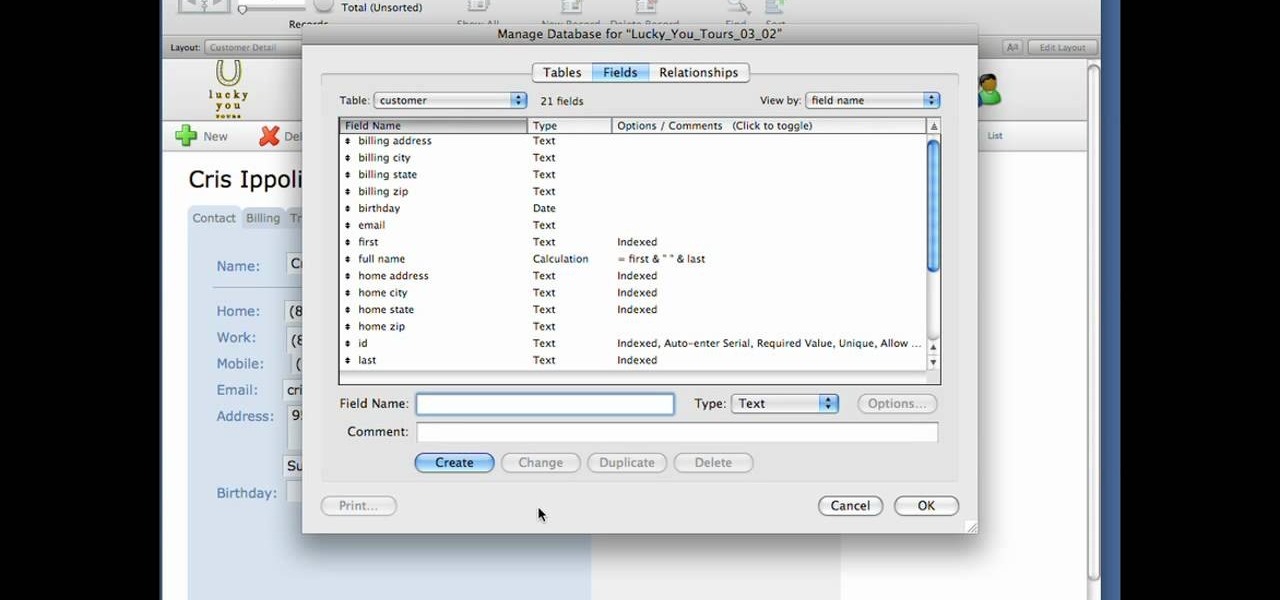
If your into data based business,then this one's for you. Text field's are very much important while making a data based solution in FileMaker Pro 10.You can go to file menu>manage>database and there is the field's tab. Text field is used for storing text and no other such use. Text field's can hold up to 2GB of information. It can help to store raw data and formatting information, i.e., color,point size as well as type face.
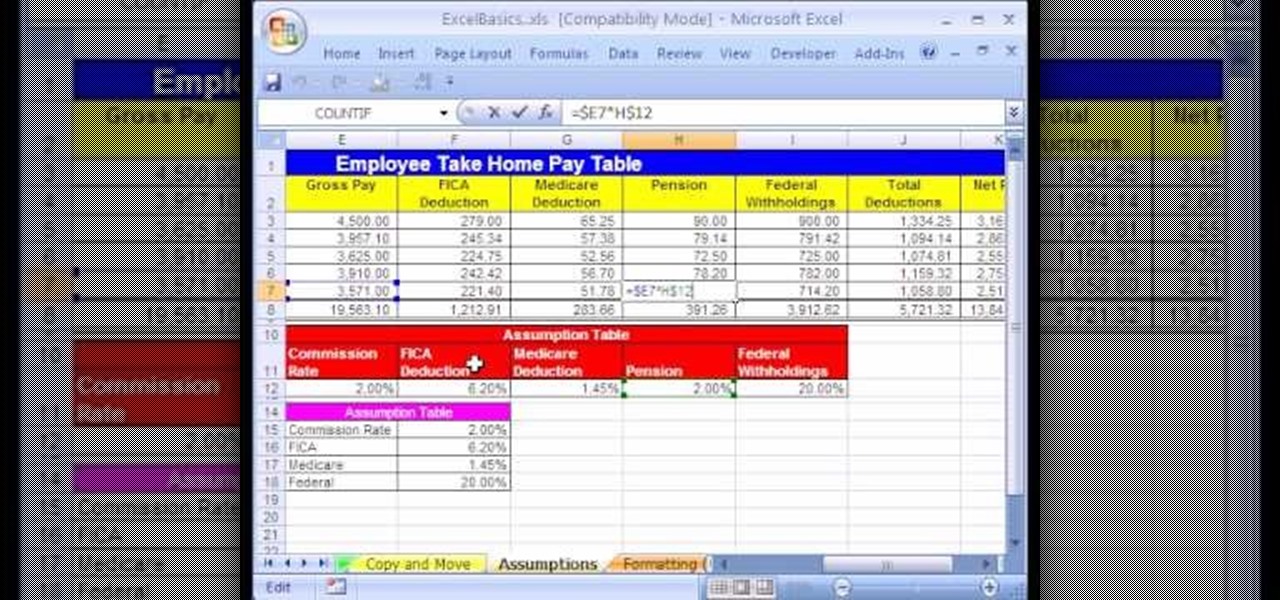
In this Excel basic video the instructor shows how to setup a spreadsheet and use cell references. Cell references are used in Excel to refer to other cells in a formula. When a formula contains data based on the cell reference the formula auto generates the result each time the value in the cell changes as the formula contains only the reference to the cell and not the actual data present in it. In this video the tutor goes on and shows how to write a few basic formulas using cell references...

Want to get more from the raw data you're entering into your Excel worksheets? Now you can create two distinct pivot tables in Excel comparing, for example, monthly and quarterly sales data. Not familiar with the pivot table? Pivot tables summarize spreadsheet input by counting, sorting and totaling data within a list and providing at-a-glance computations within the same sheet. Become an expert on the subject within 5 minutes and 24 seconds by following easy to understand instructions narrat...
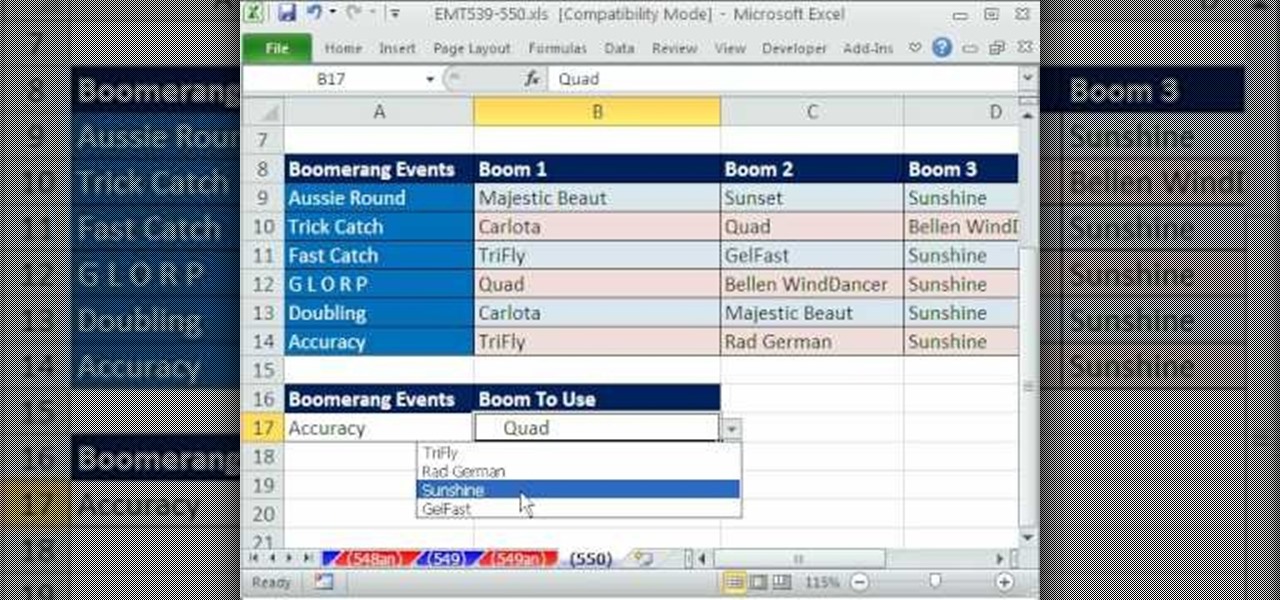
Excel dilettantes and seasoned Microsoft Office professionals alike may be surprised to learn that in Excel one can make a drop down list based upon a second drop down list (or, similarly, data validation list that is based on a second validation list).

MotionTraining gives an overview for using Microsoft Excel for beginners in this video. This video gives a rundown and overview of the basics of this spreadsheet program: from typing in the columns and rows, adding dollar signs to data, and how to make basic calculations. MotionTraining will show how to make text stand out with bold and italics, adding colors to your data, and how to make a grid appear during the printing process. Creating various charts of the data in the spreadsheet is also...
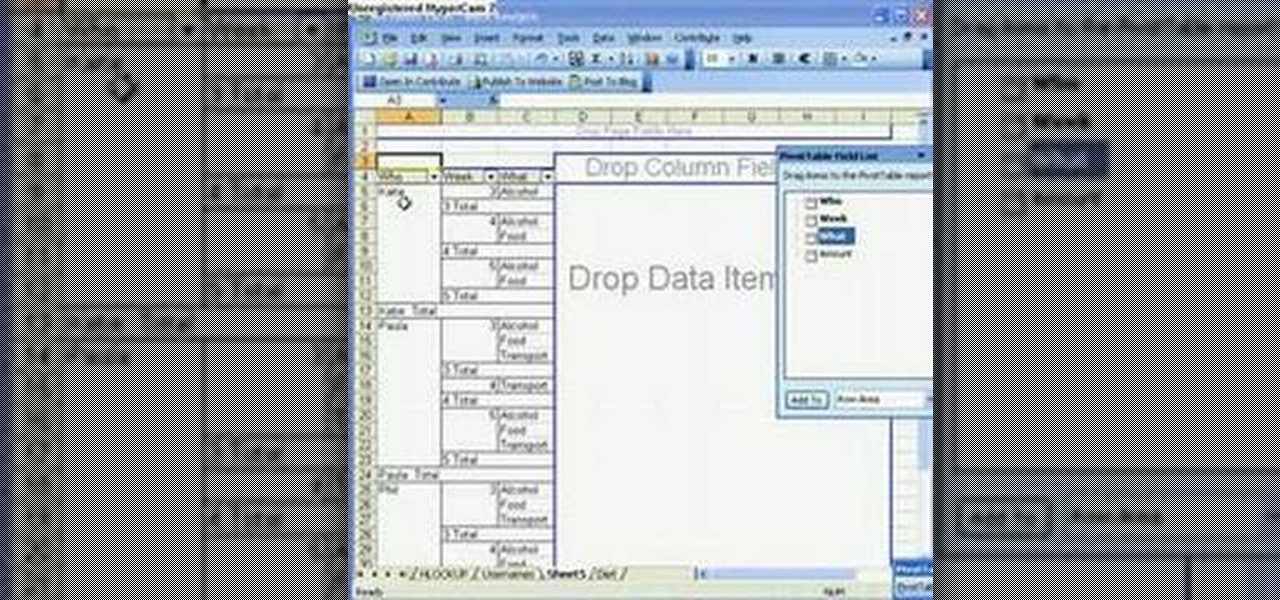
Microsoft Office Excel 2007 spreadsheet manager is a powerful tool that enables information workers to format spreadsheets, as well as analyze and share information to make more informed decisions. In this MS Excel video tutorial, you'll learn about using a pivot table to summarize data.

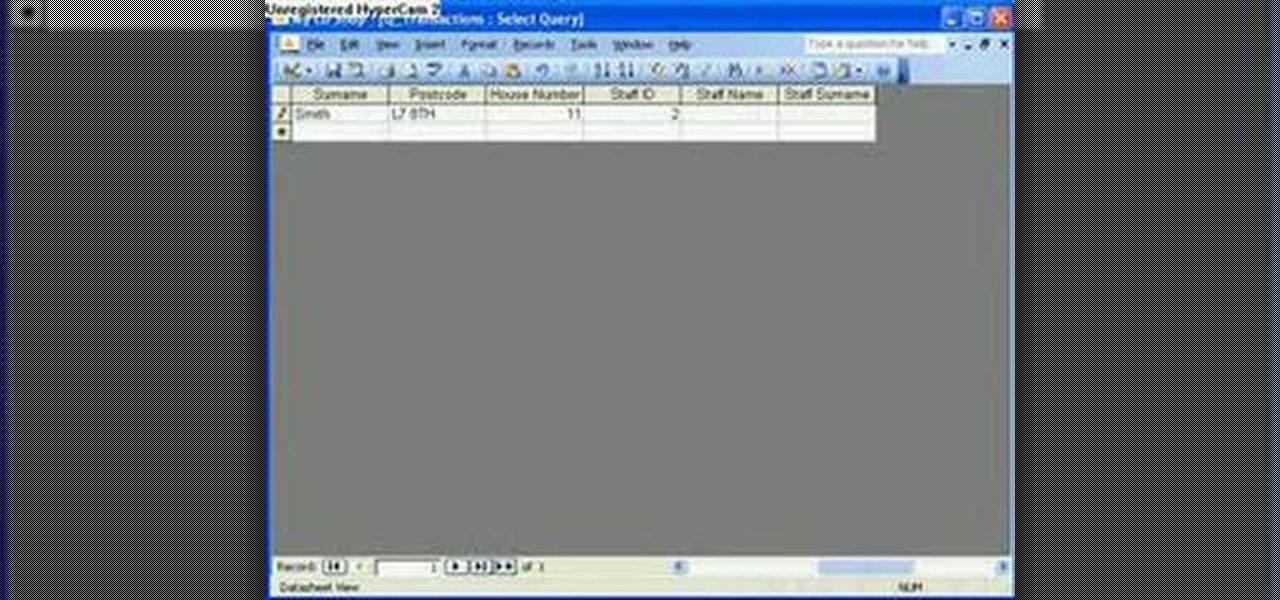
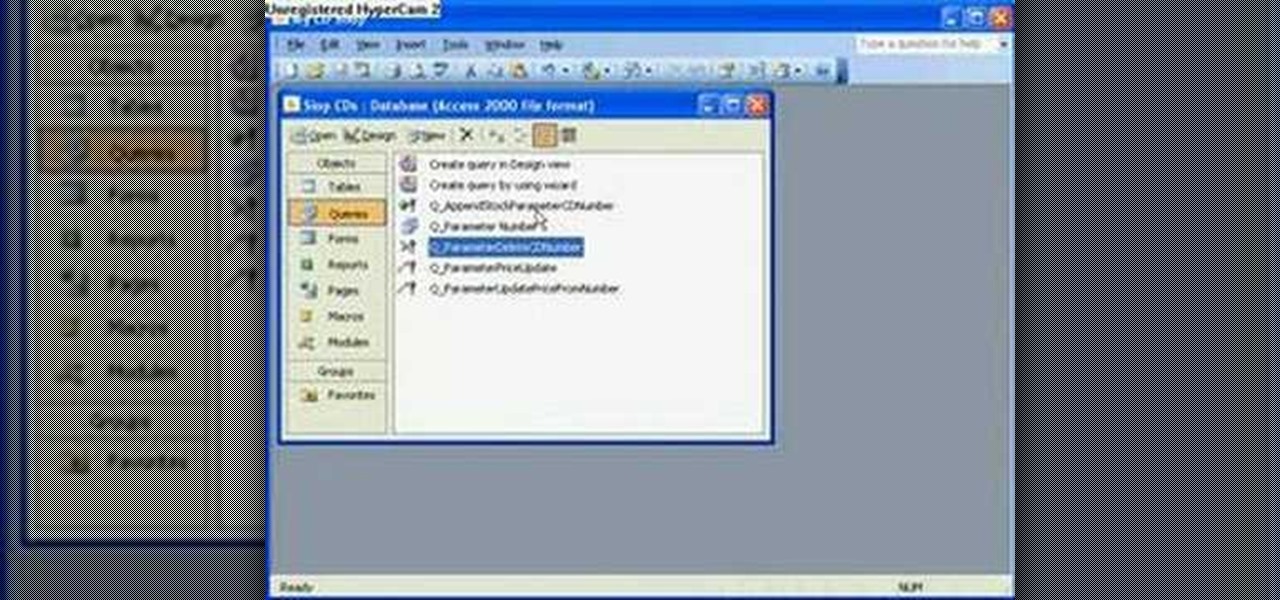
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about using relationships and queries to pull data from tables. For more information, watch this Microsoft Office Access how-to.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about using an append and delete query sequentially using a macro. For more on archiving data in Microsoft office, take a look.

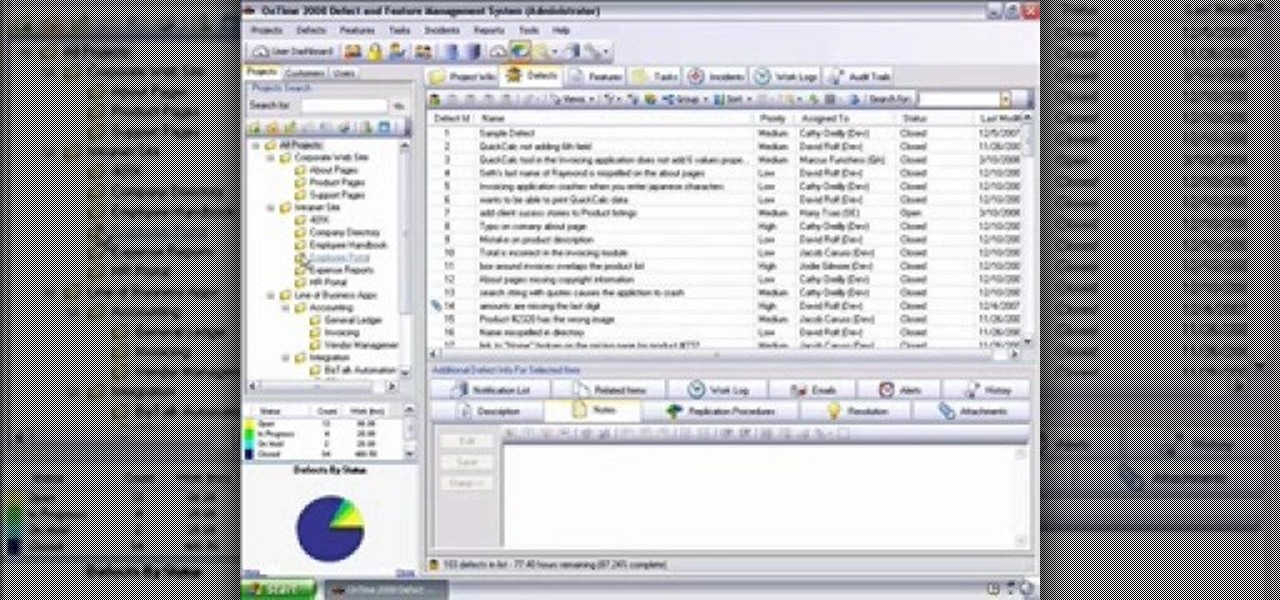
Need some help getting started running reports? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers the basics of running reports and sending data to those reports. Did you know there are four ways you can manipulate what data is sent to a report without any direct report customization? Take a look!

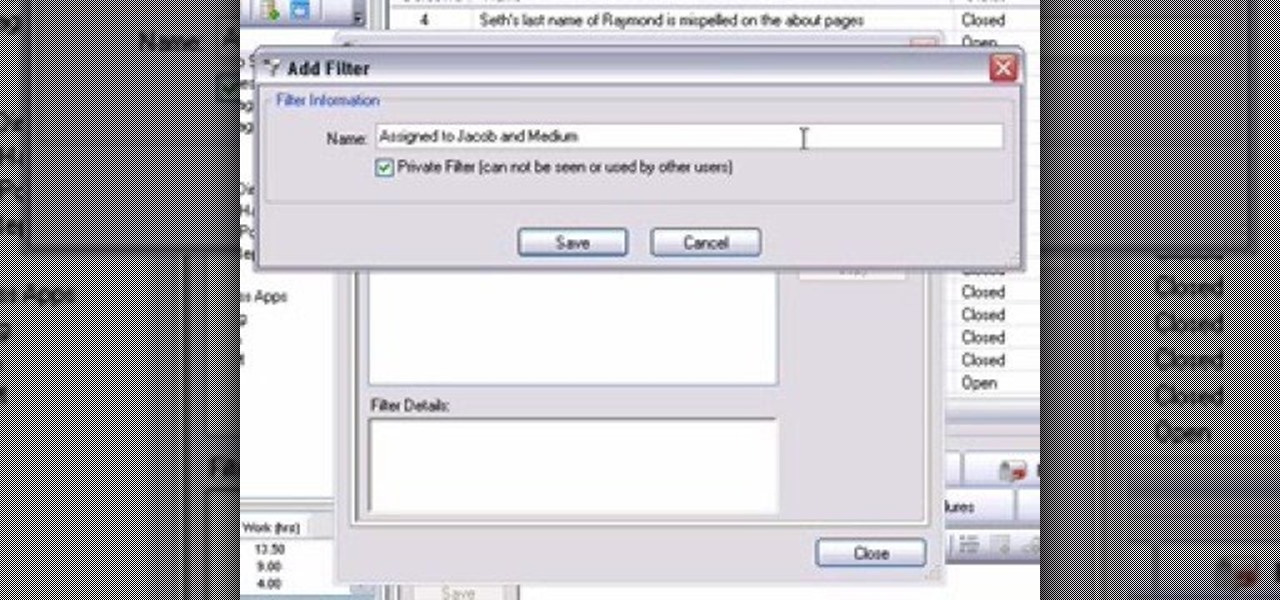
Filters are a powerful mechanism in OnTime used for searches and other forms of data manipulations. In this installment from Axosoft's own series of OnTime Project Management Suite video tutorials, you'll focus on the simplest application of filters: searching data in your main grid in OnTime 2008.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this introductory video, Alex James will show you how to build a simple Entity Data Model in a short amount of time.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this introductory video Diego Vega will show you how to use the Entity Data Source in an ASP.NET Application.

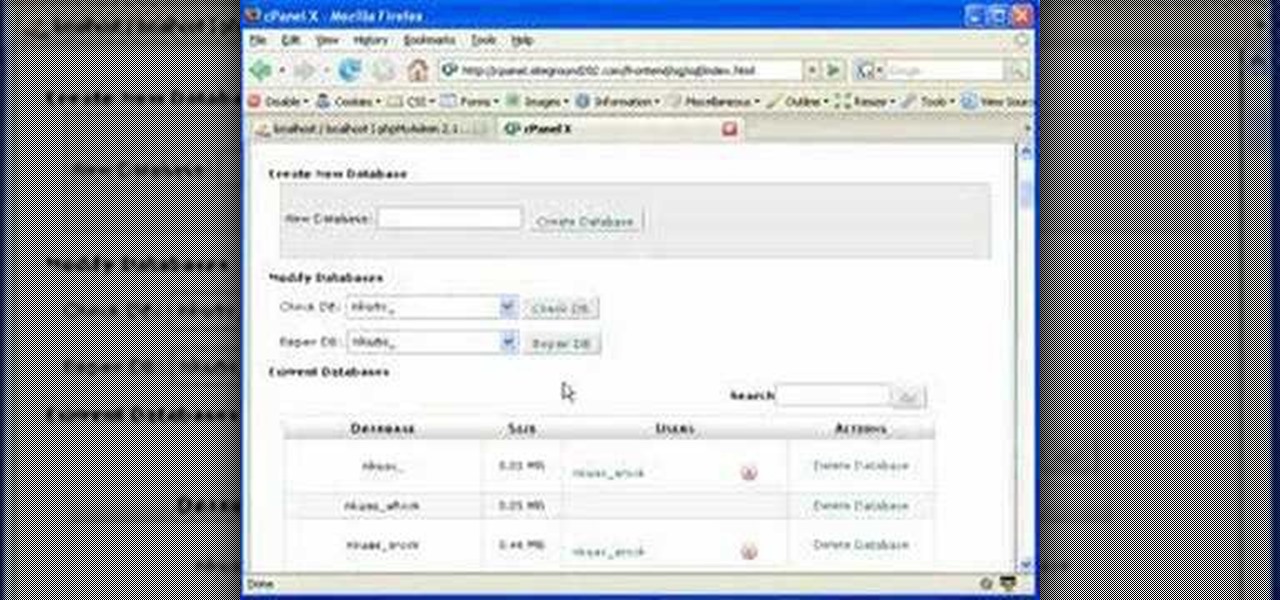
This data management tutorial shows you how to take a Microsoft Excel Spreadsheet and import it into a MySQL Database using CSV files and PHPMyAdmin in cPanel. Being able to move data from Excel to MySQL is an important part of database content management, so if you use cPanel to manage your databases, you'll want to watch and learn how to import Excel spreadsheets into your MysQL databases.

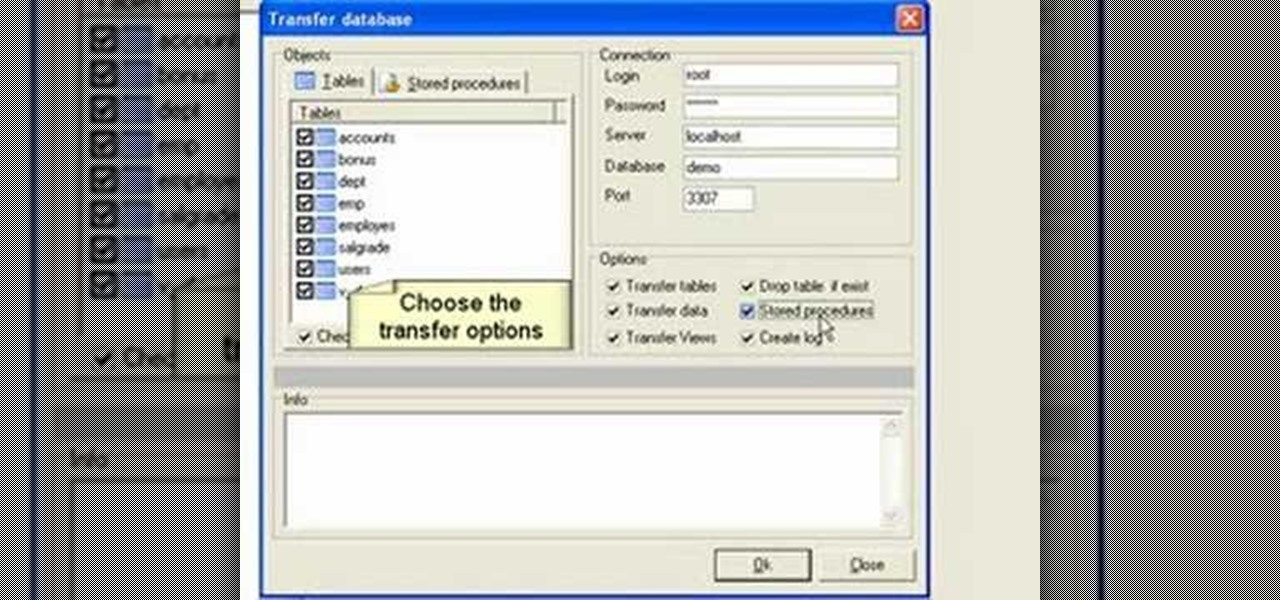
If you're new to DreamCoder for MySQL, one of the things you may want to know how to accomplish is how to exchange information between two remote MySQL databases. Happily, this tutorial will walk you, step by step, through the process. To learn how to transfer data between two MySQL databases simultaneously within DreamCoder for MySQL, take a look!

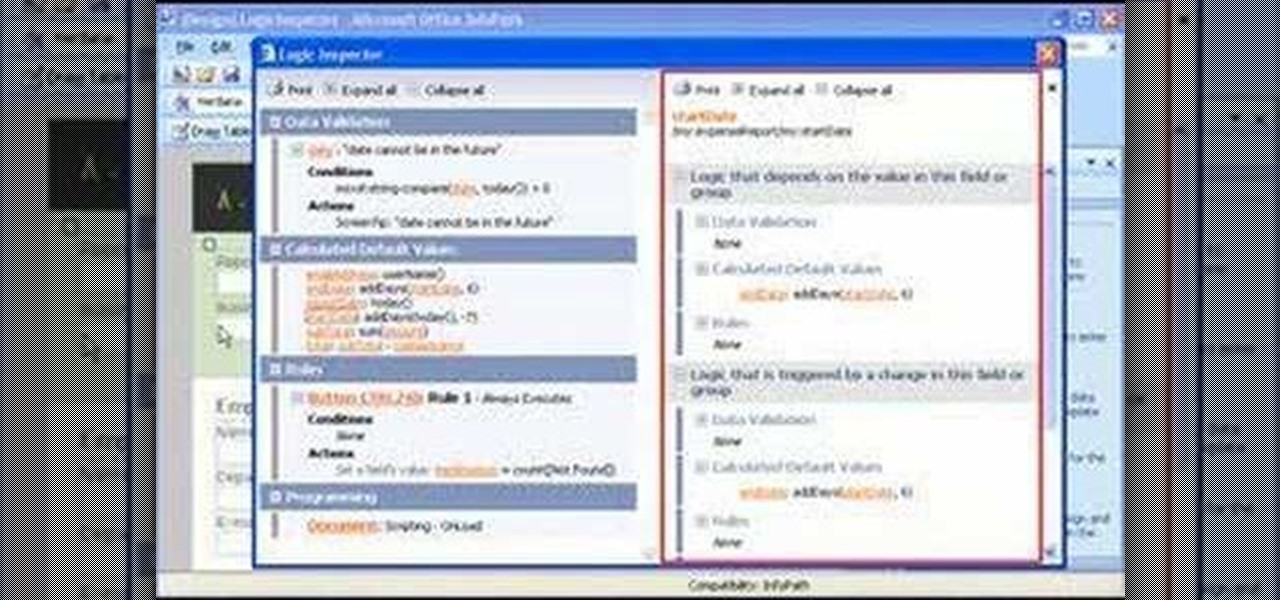
You don't have to check the settings for every control individually — you can use the Logic Inspector to see a form's business logic displayed in a single window, grouped by features such as data validation, calculated data values, rules, and programming. Take a look at this instructional video and learn how to view the logic in a form template with Microsoft InfoPath.

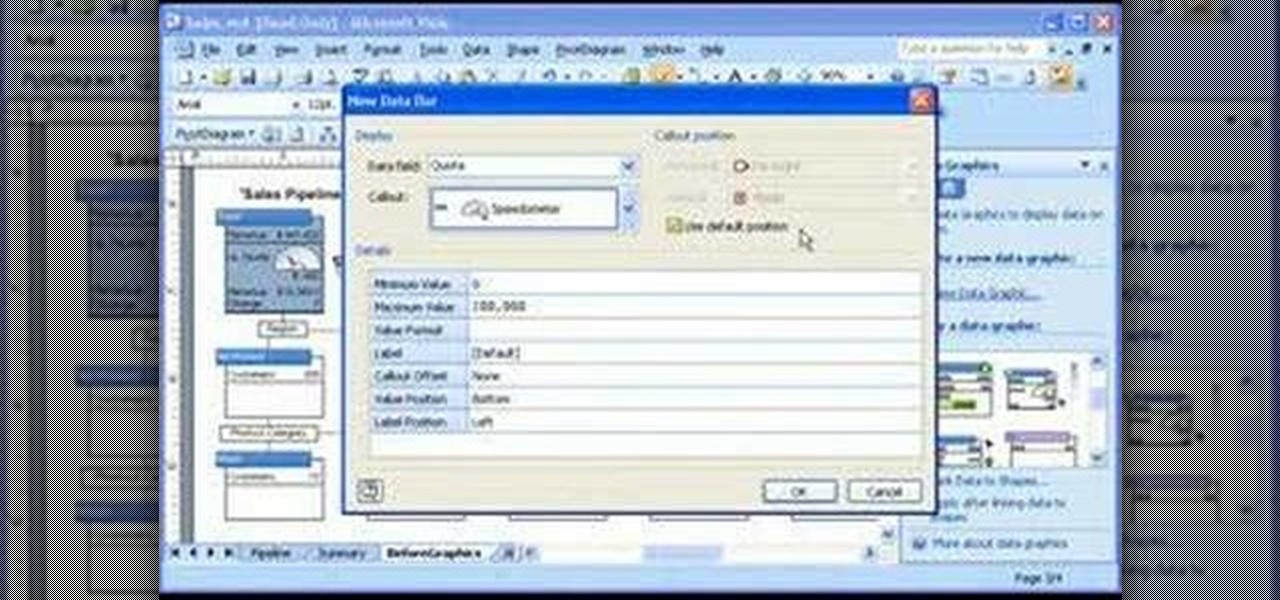
Take a look at this instructional video and learn how to customize progress meters, icons, color coding, and other graphical elements to emphasize sales trends, product performance, critical deadlines, or whatever information is contained in the data behind your diagram.

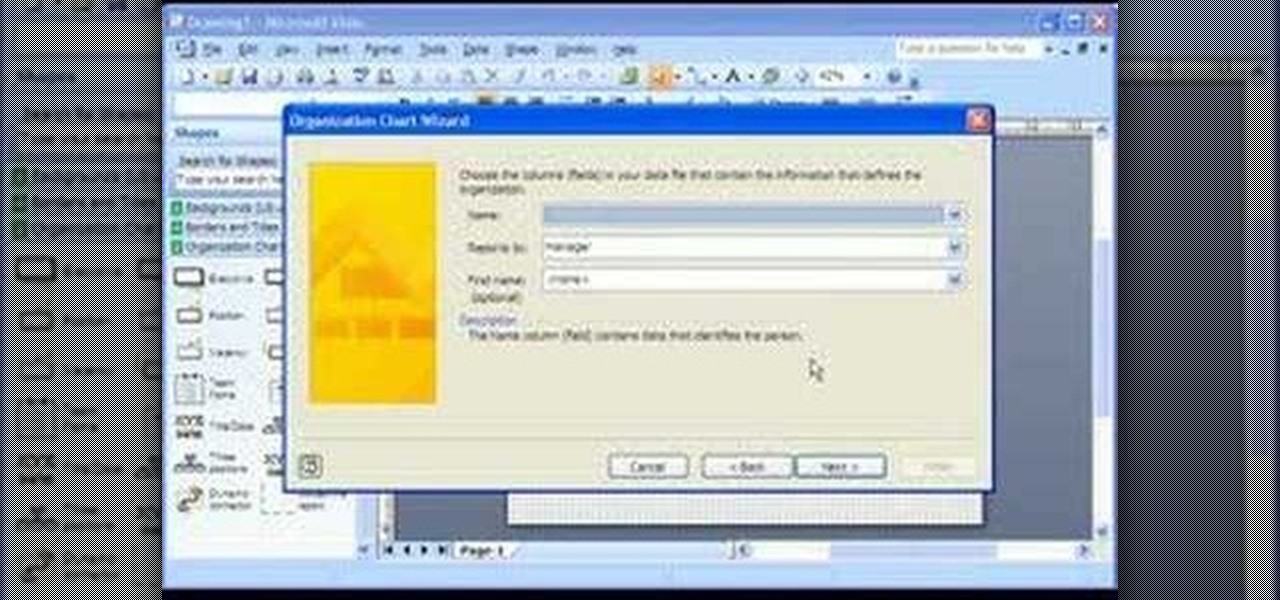
Take a look at this instructional video and learn how to use a Microsoft Office Excel worksheet that contains employee data to create shapes, connect them according to your organization's structure, and add data to each shape in your drawing automatically.

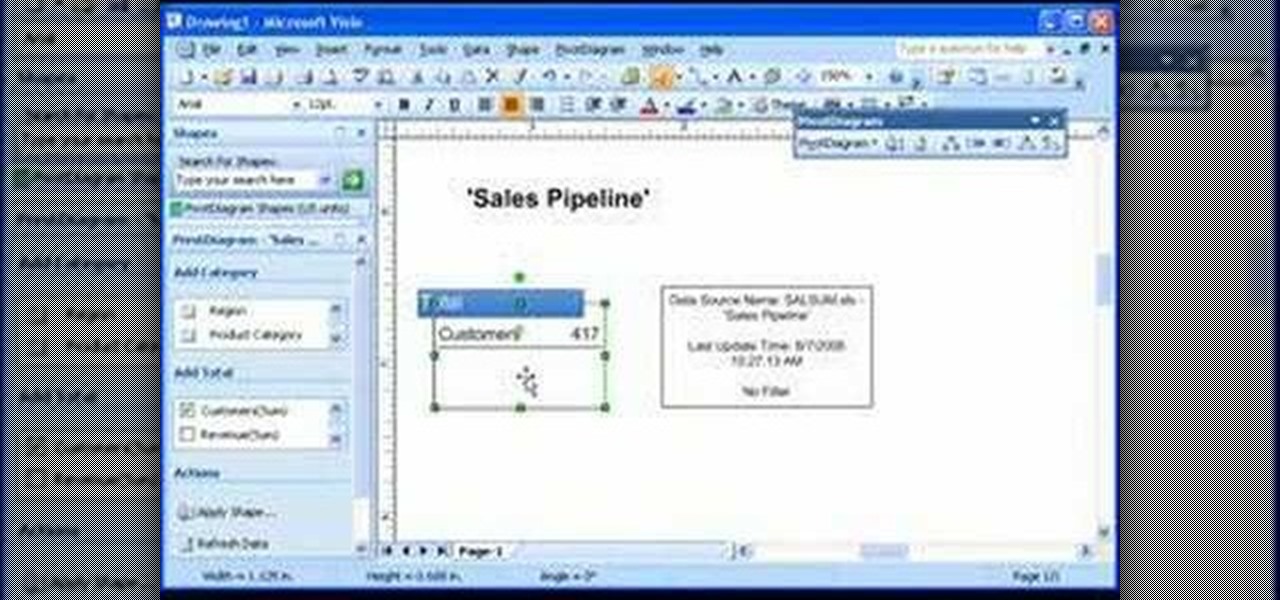
A PivotDiagram is similar to an Excel PivotTable report: It arranges data in a visual way. Check out this tutorial and learn how to look at the same data from different angles to establish and analyze relationships that you might miss in a table or a worksheet.

In this video tutorial, Scott Golightly shows how to implement a simple HttpModule that uses the BeginRequest and EndRequest events to store some data about the request and later display that data to the user. Scott also shows how to register the module in the Web.config file.

In this video tutorial, Chris Pels will show how to share data in between JavaScript and server-side code by using a hidden field in an ASP.NET page. Next, learn how to use the RegisterHiddenField method in server-side code to programmatically create a hidden field on the client. In addition, see how to programmatically create a HiddenField server control for sharing data on an ASP.NET page. Finally, use the RegisterArrayDeclaration method to create a container in server code for storing mult...

A video tutorial showing you how to export data from Excel to a Word document in a couple different ways. Copying from Excel to Word doesn't always do it right. Try exporting.

This video shows you how to take apart a Nintendo Wii. WARNING: this will void warranty. All time and date data will be reset, but the game save data should remain the same.

Austin Chau does a short tutorial about how to use the JavaScript Client Library with the Google Calendar Data API.

Name ranges of data to make formulas a bit easier to read and write when working in Microsoft Excel.

How to display the data in a MySQL database table in a web page using PHP.

One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

This tutorial covers gathering up all of your data. In AE: Collect Files. You can do the same in CINEMA 4D. If you're not familiar with collecting files in After Effects, the video hits the rough outline.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

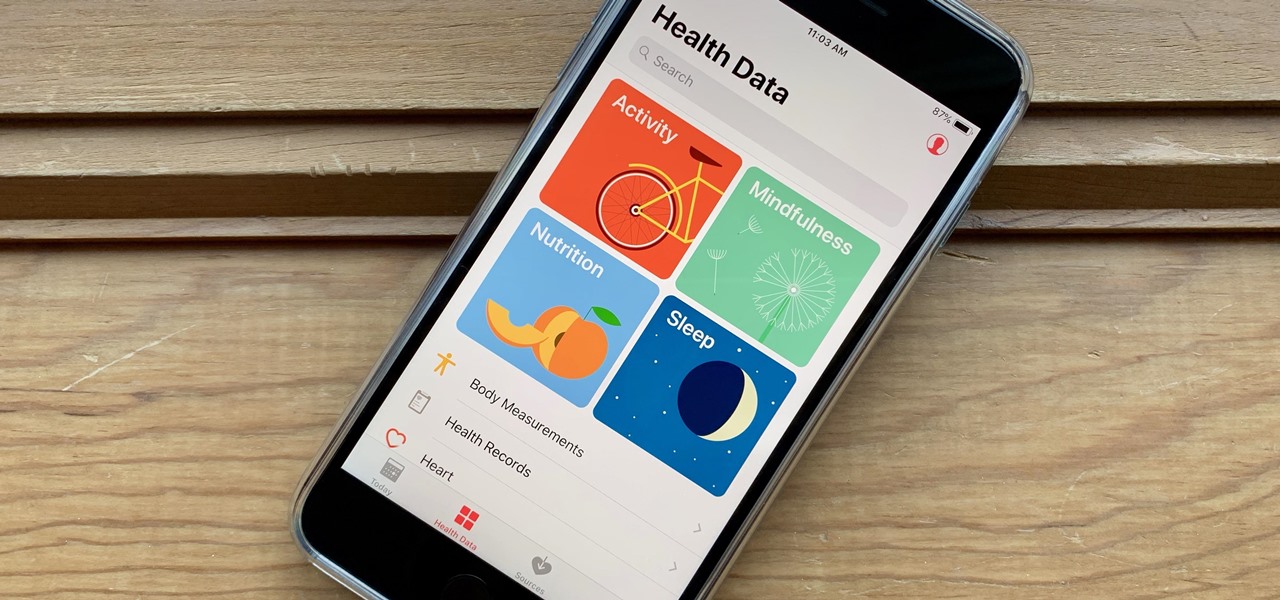
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

With the iPhone XS, XS Max, and XR, Apple introduced dual-SIM capabilities to iOS, made possible by eSIM technology. If you recently picked up one of these three new iPhones and need to utilize your eSIM while traveling abroad, you might want to take a look at the data plans offered by GigSky.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.