How To: Create a Basic Client-Server Connection in C Part-1
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Welcome back my friends !! Today we'll go through the second part of this C# series

Five Phases of Hacking:- The five phases of Hacking are as follow:

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.
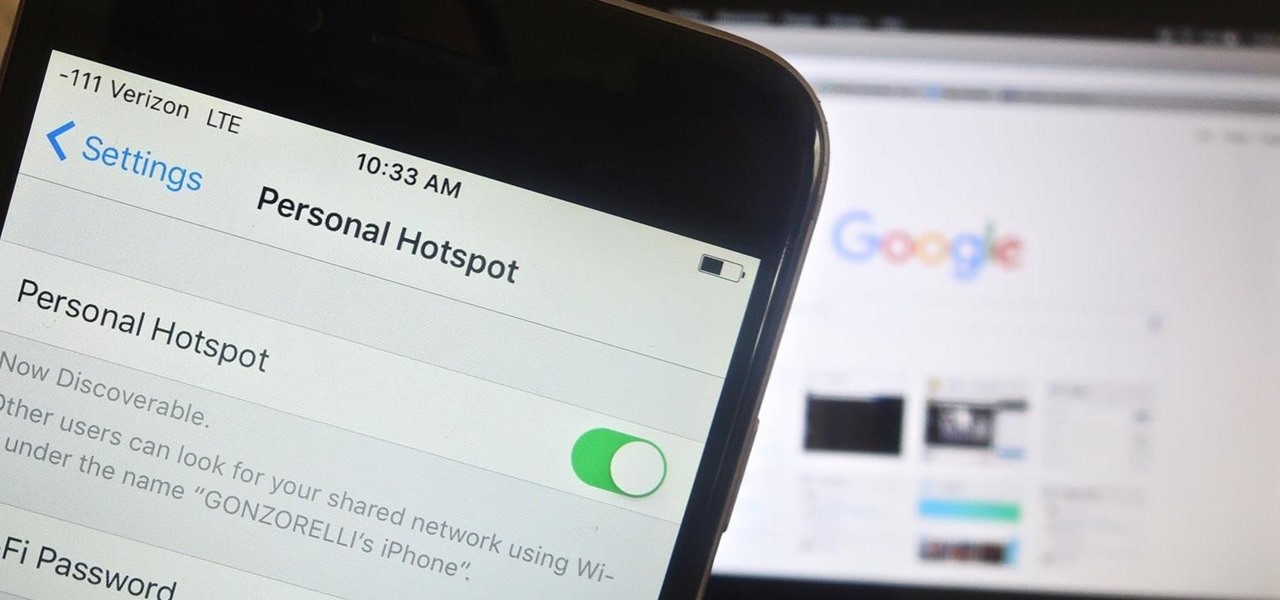
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.
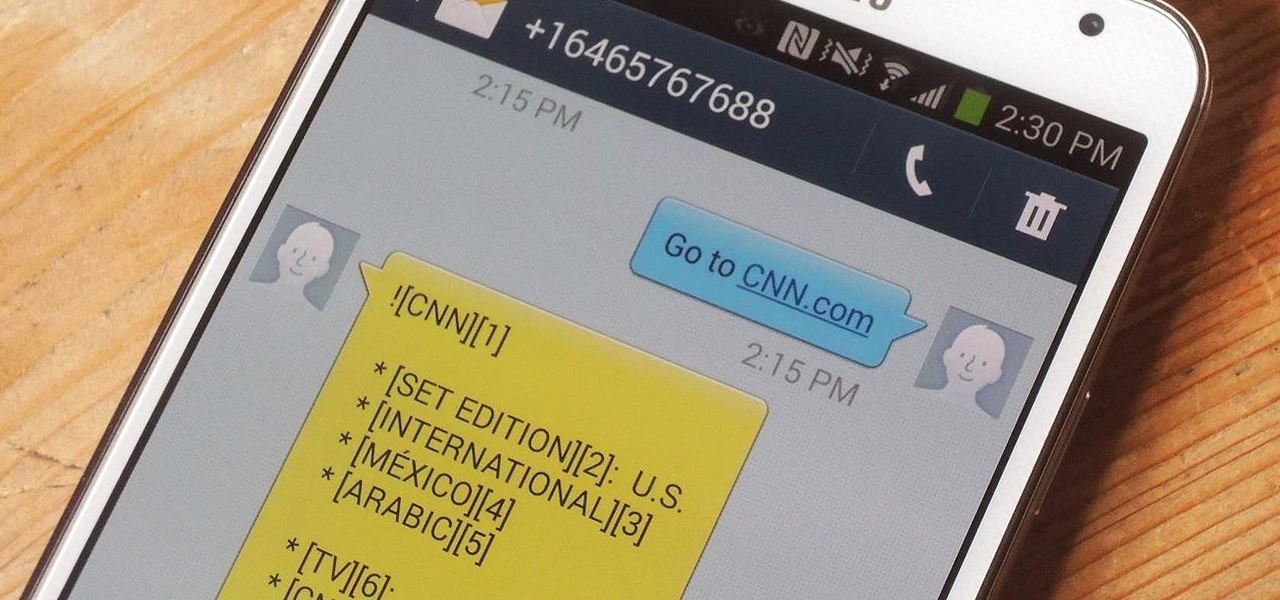
In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.
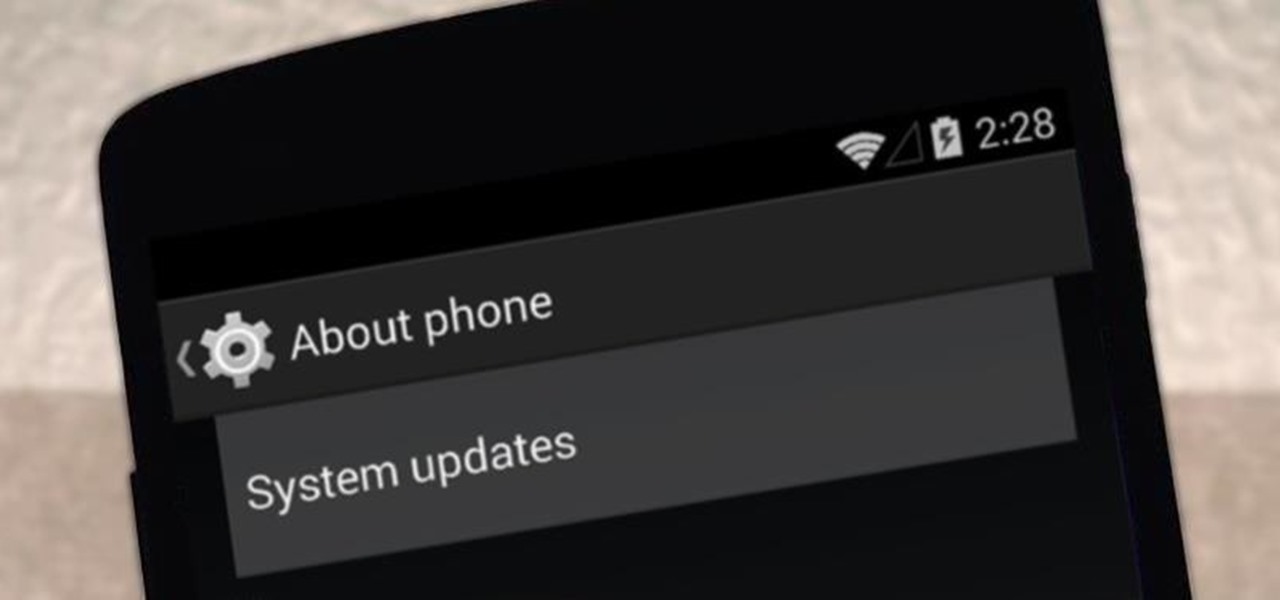
It appears that the next iteration of KitKat, Android 4.4.3, is fast approaching. If the past is any indication, today's update to the Nexus 5 software changelog on Sprint's website tells us a new version of Android will begin rolling out within 24 hours. Sprint has broken the news of a forthcoming Android release twice in the past. With 4.4.1 and 4.4.2, a mini-changelog was posted on the Sprint website about a day before Google began pushing updates to its Nexus devices.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.
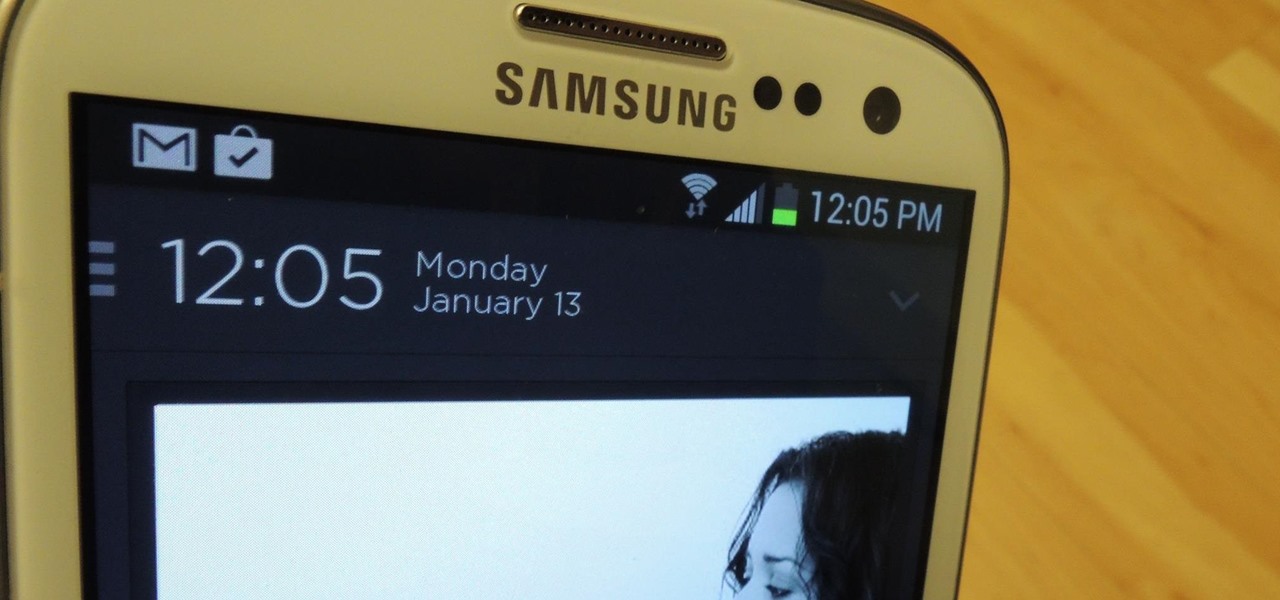
The sensors in your mobile device are integral for gaming (try to beat my Temple Run 2 score), as well as many of the basic Galaxy S3 features like Smart Stay and other fancy additions. But sometimes those sensors can become overly sensitive or just downright unusable.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Whether you're pressed against your bedroom window, hidden deep inside your linen closet, or lounging on the rooftop, finding that area of maximum Internet speed around your house is usually just trial and error. And when you finally find the sweet spot, apps like Speedtest.net can help you determine how fast your Wi-Fi or cellular connection is overall on your computer or smartphone, so you know your full capabilities. But, if you want to know exactly how fast your Samsung Galaxy Note 2 is u...
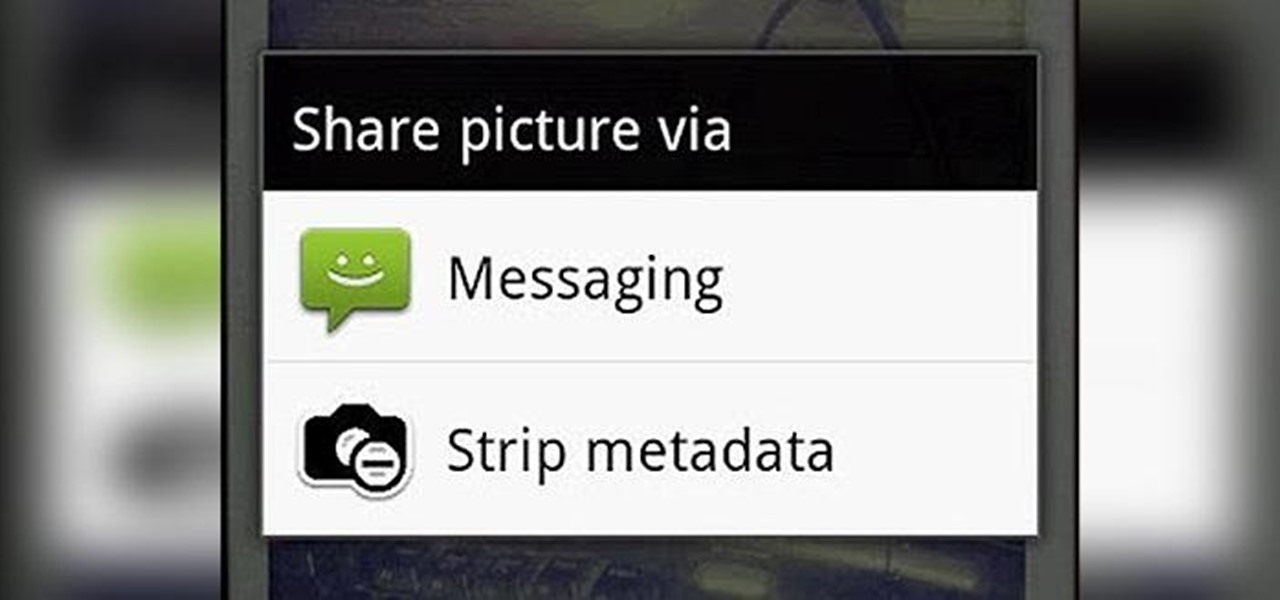
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.

We depend on our hard drives for our data storage and if they stop working, our important data can be lost, this could cause many problems like losing school projects making us to do them again, losing jobs and other problems . So here is a tutorial, on how to make a dead hard drive work again.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.
This video will teach you how to hack a WEP wifi network on a Mac. You'll need to follow the link, grab the prog and follow the steps. It's not too hard, so give it a try. Remember, stealing is illegal!

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Anyone can set up their own wireless network. All you need is a little know-how. You will need a computer with wireless capability, a high-speed modem, a wireless router, and a broadband internet connection. Don't get tied to the wall; a wireless connection will allow you to move the computer freely around your home and still get an internet connection. Watch this video tutorial and learn how to hook up a wireless network at home.

Tekzilla shows you how to troubleshoot network woes with ping and traceroute.
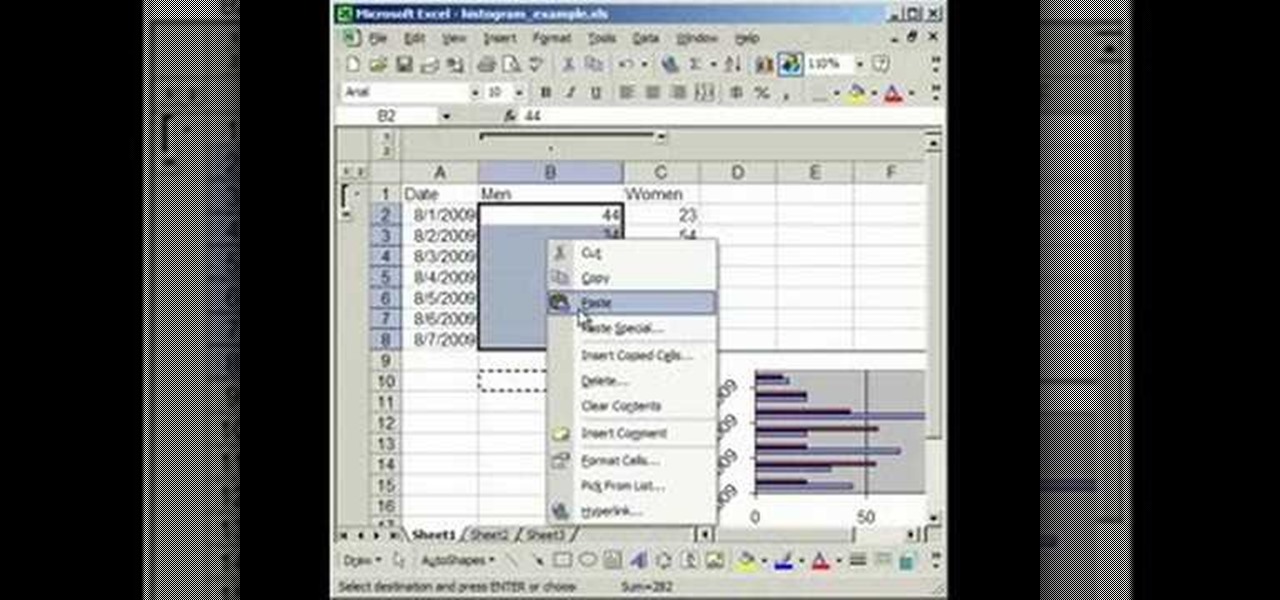
In this tutorial, we learn how to make a histogram chart in Excel. To create a vertical histogram, you will enter in data to the chart. Then, highlight all of the data and go to "insert", "chart", then choose a regular column chart. Grab a regular 2D column and then make sure your values are correct. Then, right click and go to "chart options", then take the legend off. Now, make these columns all touch each other by right clicking over the columns and formatting them. Go to "options" then ch...

Use PubSubHubbub
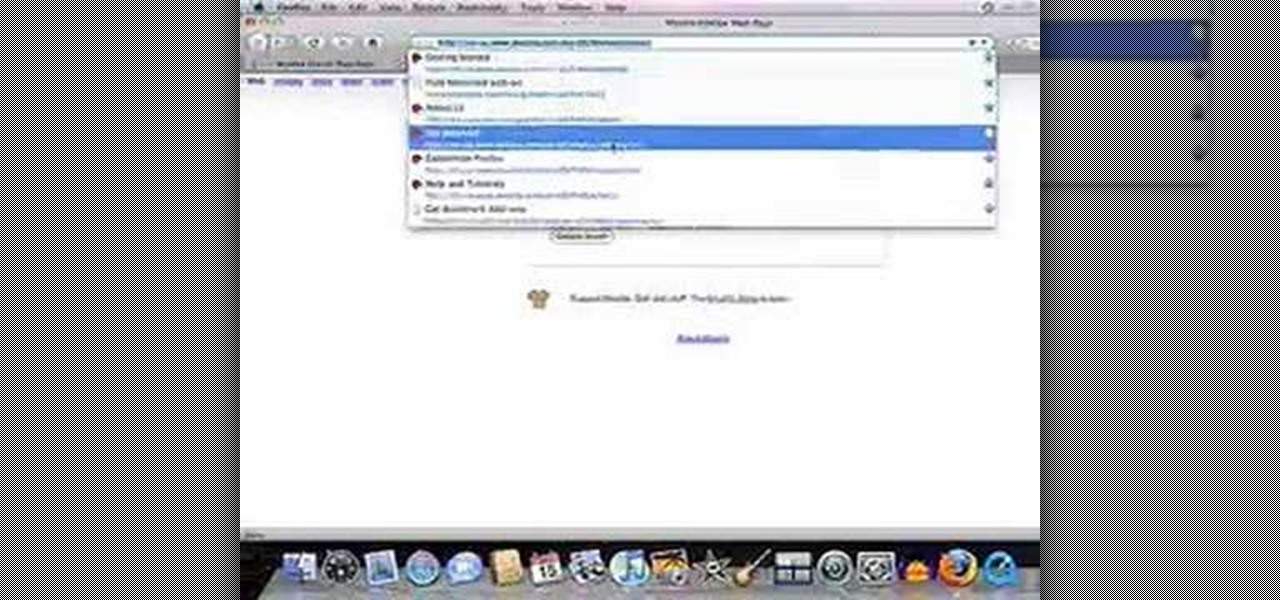
In this video, we learn how to clear Firefox location bar and browsing history. To get rid of an individual one, use your keyboard to go to the one you don't want. Then, press shift+delete and that one will be deleted. To remove them all, go to tools then click on "clear private data". Check the box of the browsing history, then click on the button to clear all the data. If you still have items in the list on your browser, then that means you have those websites bookmarked. To remove those, y...
In this video, we learn how to clear browsing history and cache in Firefox and Internet Explorer. First, while in Firefox, go to the tools menu, then click on clear private data. In the new window, click on the items that you want to have cleared, then click "clear private data now". After this, the computer will clear out all the internet files. Next, while you're in Internet Explorer, go to the tools menu, then click on "internet options". Once in here, click the appropriate sections to cle...

In this video, we learn how to quickly copy and paste data in Microsoft Excel. First, if you have two columns that you want to add up, you will highlight the columns and then copy and paste them into the other cells. Another way is to select the cell and go to the bottom right hand corner, then drag it down. This will fill your formula in to every cell below it! This will save you a lot of time instead of having to type in formulas for the columns that you are trying to do equations with! Thi...

In order to format graphs and charts using Microsoft Word 2007, click on Chart Tools. The tabs at the top of the screen provides you with your options. You can change the type of chart or graph by clicking on Change Chart Type. If there is a particular type of chart that you would like to use again and again, then you can save it as a template via the Save As a Template icon. You can edit the data in your chart of graph by clicking on Edit Data. You can modify the chart layout by clicking on ...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 637th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a dynamic two data series line chart for blood pressures — how to look up a chart using defined names, a data validation list, and a formula using the INDIRECT function inside a picture of a chart.
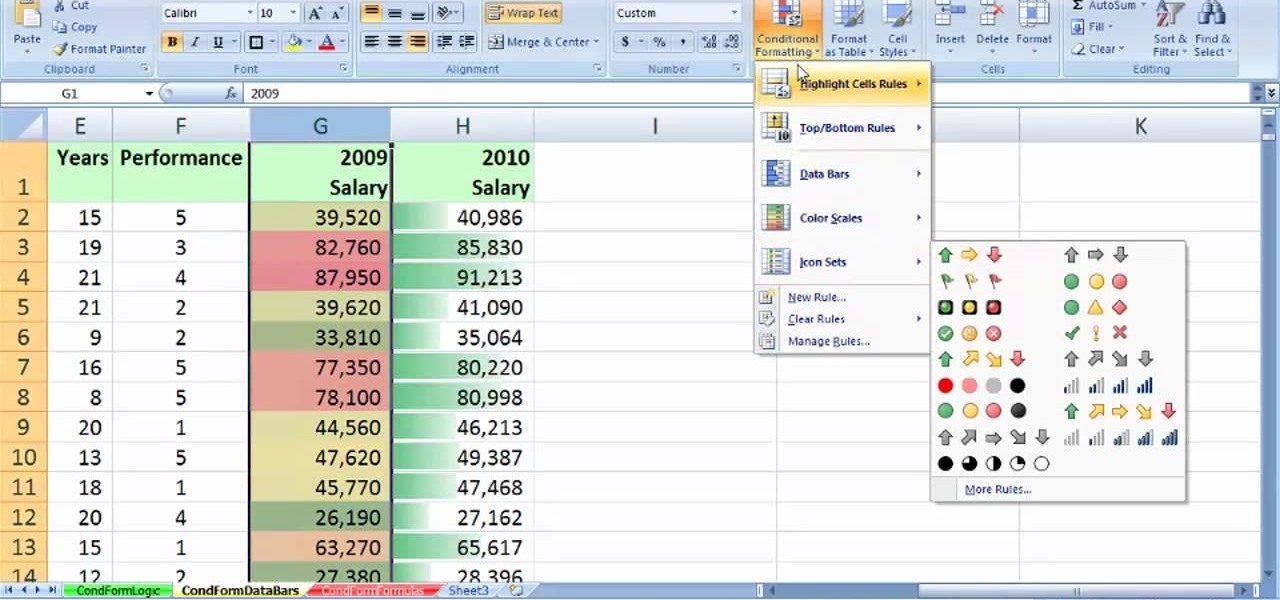
See how to create value-based formatting using data bars and color scales in Excel 2007. See how to use the Format Cells dialog box and the pop-up mini-toolbar in Microsoft Excel 2007. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned business professional just looking to better acquaint yourself with this particular iteration of the program, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, w...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 20th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to summarize survey data with a pivot table (grouping & report filter), COUNTIFS function (4 criteria), SUMPRODUCTS formula, SUMPRODUCTS & TEXT functions and DCOUNT database function.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 5th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to create horizontal subtotals for a data set using the IF, SUM and SUMIF functions. Also see conditional formatting for non-contiguous cell ranges using a TRUE/FALSE logical formula with the NOT symbols.
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 21st installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to add conditional formatting to data bars and icons to show relative size, icons to show relative size, to highlight values within 1 standard deviation, to highli...
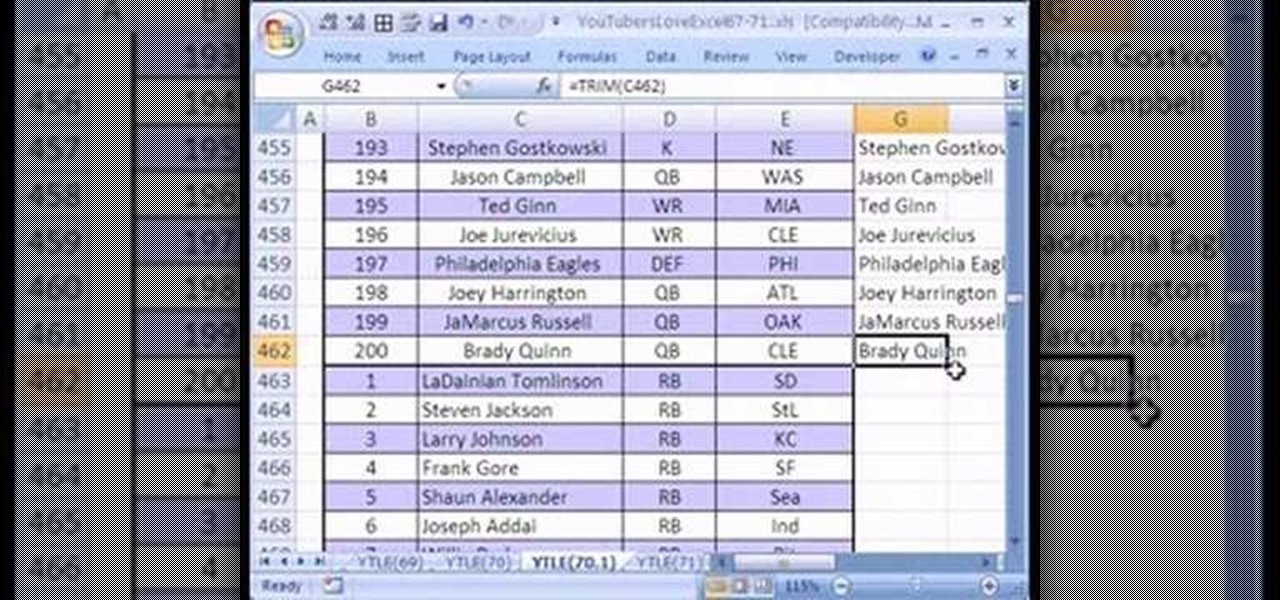
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 70th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to clean up a bad data set with the TRIM function before building a pivot table (PivotTable) to calculate an average. Learn to love digital spreadsheets more perfectly with the tricks outlined in this free Microsoft Office how-to.
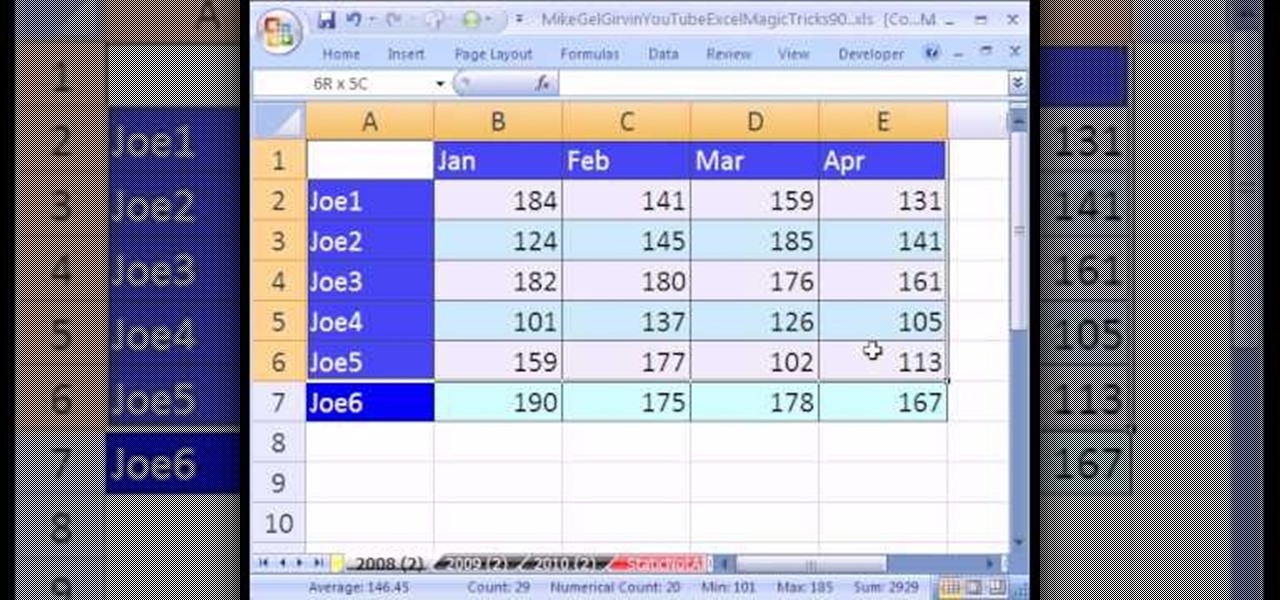
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 90th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the consolidation feature in Excel. Summarize data from a number of different tables quickly using consolidation.