New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 5th installment in their series of digital spreadsheet magic tricks, you'll learn how to name a cell range, use data validation to add a drop-down list, and how to use the VLOOKUP function to look up values.
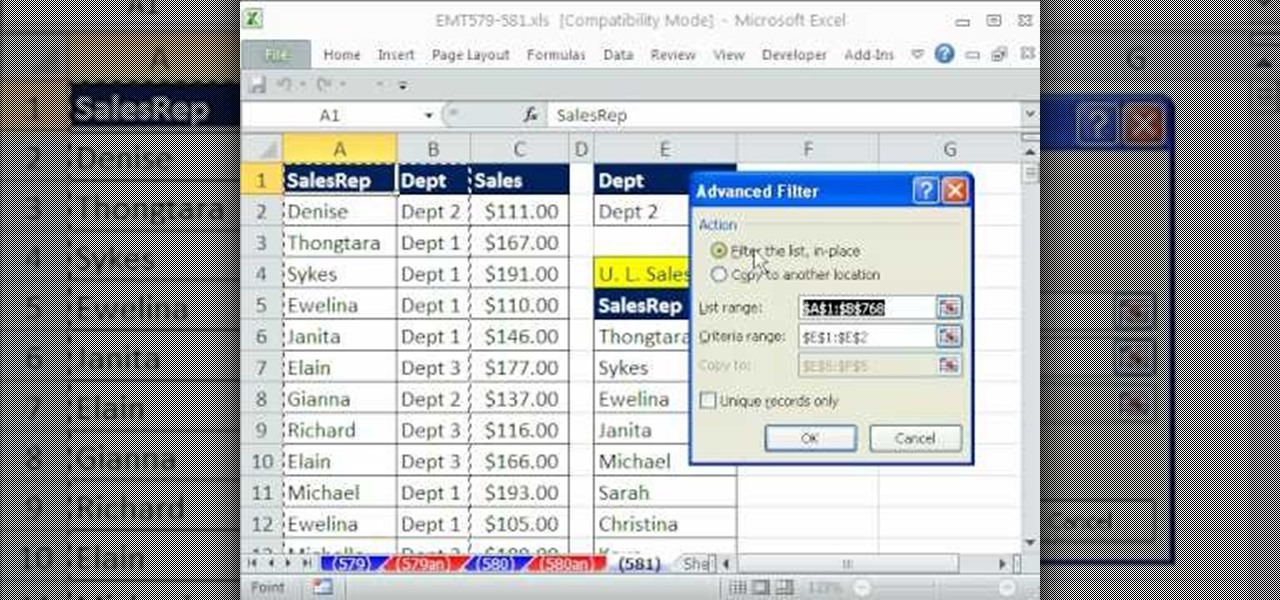
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 581st installment in their series of digital spreadsheet magic tricks, you'll learn how to use the advanced filter tool with criteria to extract a unique list of employees for each department from a huge data set with transactional records.
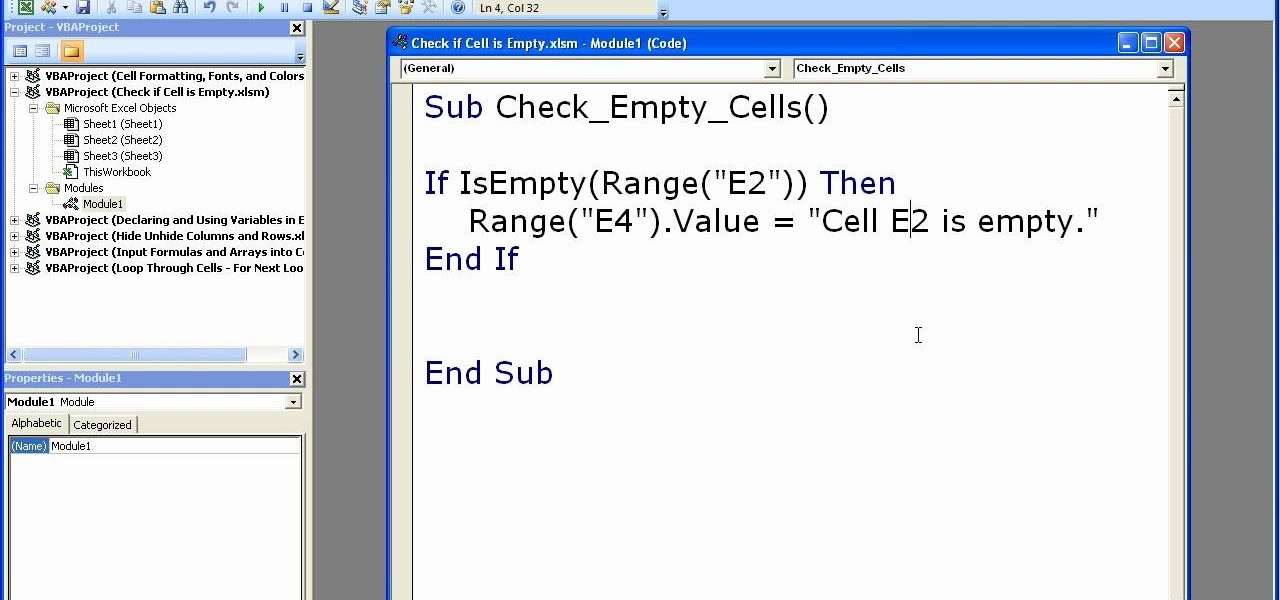
Microsoft Excel is used to store and work on data by storing them in rows and columns in tables. You can use a macros to check if a cell is empty. To do this you have to know two short cuts. The first is the VBA Window short cut which is Alt + F11 and the other one is View Macros short cut which is Alt + F8. So open an Excel spread sheet and insert some data into a small table. Now create a macro for this tutorial. You can use and IsEmpty() functions to check if a cell is empty. Use this func...
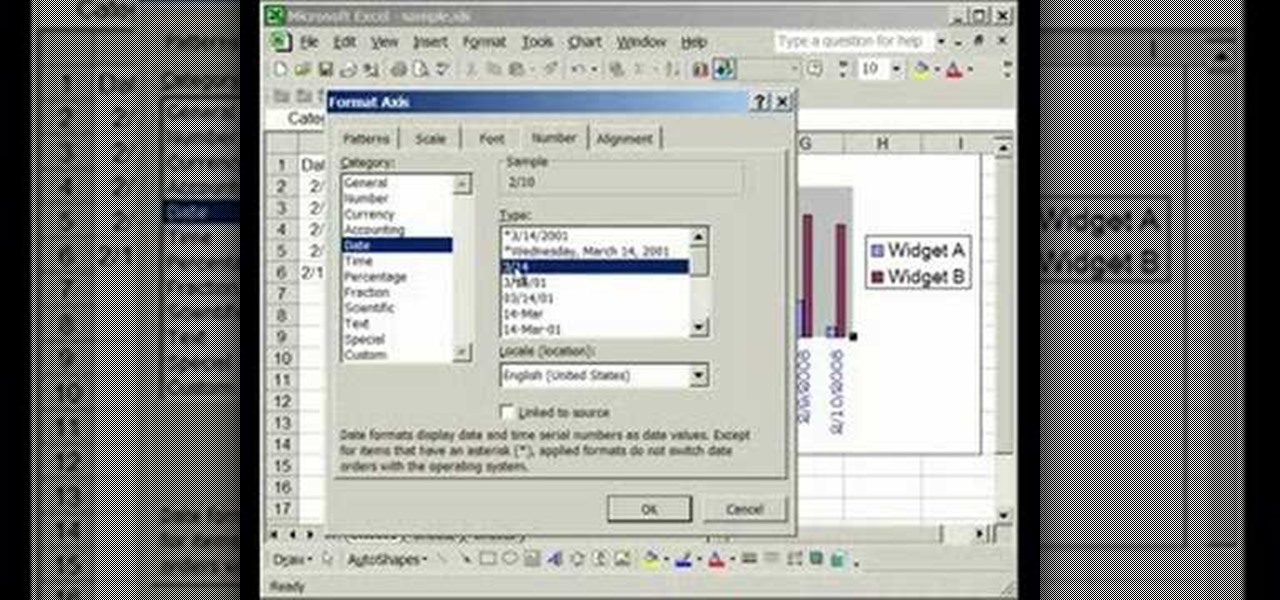
This video is about formatting the charts in Excel especially the x and y axes. The video begins by selecting a chart and right clicking the dates at the bottom of the data points. The format axis window pops up and by making changes to the style, color and the weight of lines given in the patterns tab, you can change the way the x-axis looks like. You can also change appearance of characters appearing close to the x-axis by selecting options in the font menu. You can also change the format o...

RAID, or Redundant Array of Independent Disks, lets you divide and replicate data among multiple hard disk drives for information storage security. This video tutorial demonstrates how to install Ubuntu in a RAID 0 array. Before starting, you'll need at least 2 hard drives and an Ubuntu alternate installation CD. RAID 0, or striped disks, let's you install an operating system, such as Ubuntu, on a partition, while using others for data storage, as illustrated in this instructional segment.

Open Microsoft Office Excel. Across the top notice letters (columns), along the sides are numbers (rows). The columns and rows can be extended by highlighting sections and right clicking and choosing the high of the row. You can also select to add a border, and change the orientation of your cells.

In this video the instructor shows how to create charts and graphs in Microsoft Word. First, open the Word document and select an area to insert the charts. Now go to the Insert tab in the ribbon and select the Chart icon. The Insert Chart window opens up with various chart templates. There are various categories of charts like Line, Pie, Bar in the left hand side. In the right hand side you can see the sample charts available and you can select any of them that you want. Now it transfers you...

Custom optioned installation includes the following: Copy the files to an external hard disk before starting your installation, then you will reinstall your programs by hand by using the windows easy transfer and transfer the data into the hard disk.

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

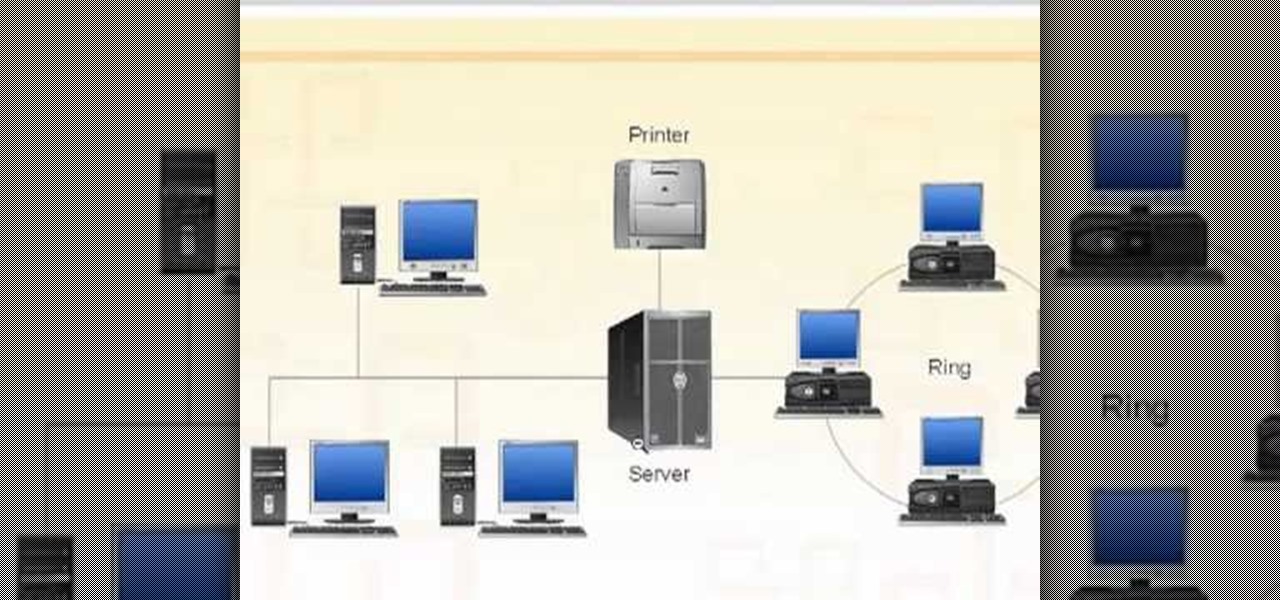
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Your Google history is mostly a binary choice — either you enable it fully, taking advantage of all its features while letting Google record your activity, or you disable it, staying incognito but also missing out on some fun stuff. But now, Google will let you auto-delete your history, allowing you to utilize all the perks that come with recording your history while maintaining some level of privacy.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

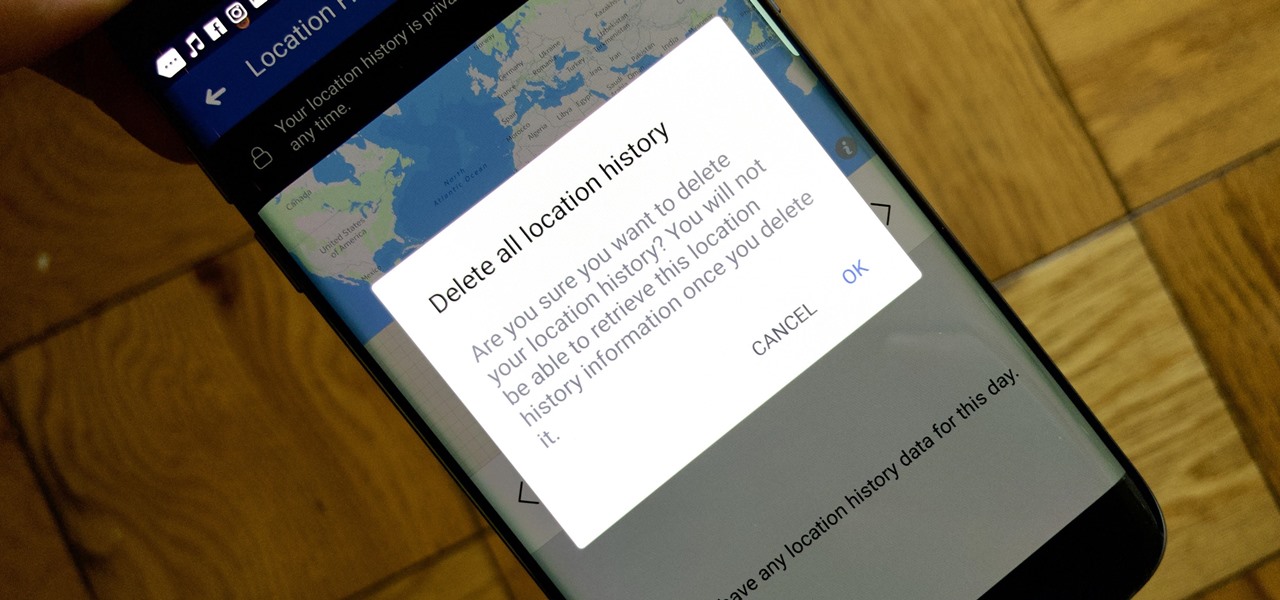
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

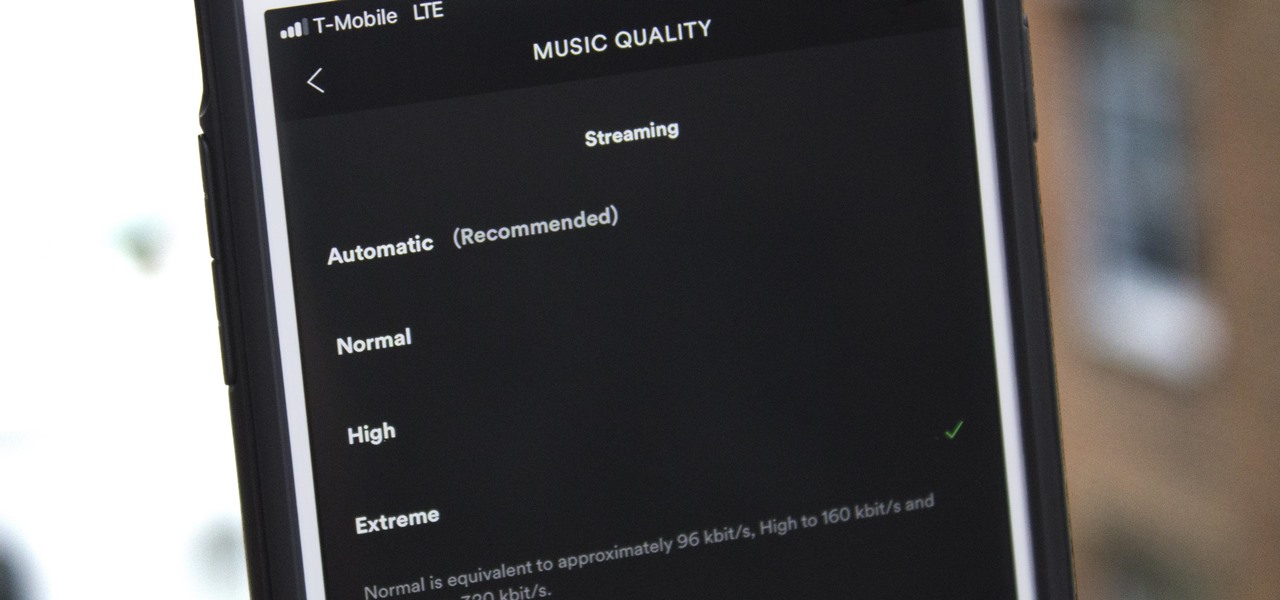
Spotify's massive song catalog can be streamed in decent quality on iPhone or Android without any tinkering. But if you're an audiophile, you've probably noticed that the sound quality can fluctuate from time to time.

How can something get more free than free? Well, in the case of Twitter, Virgin Mobile found a way with its newest promotion. If you have a 4G plan with Virgin Mobile, you can now access Twitter from your smartphone without it counting towards your monthly data allowance.

Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expandable status bars to suit their unique needs.

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Carriers really suck, don't they? We constantly have to monitor our data usage, even though many of us are on "unlimited" plans, which, in reality, will just be throttled to a slower 2G or 3G connection when we hit a certain download threshold.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.