Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.
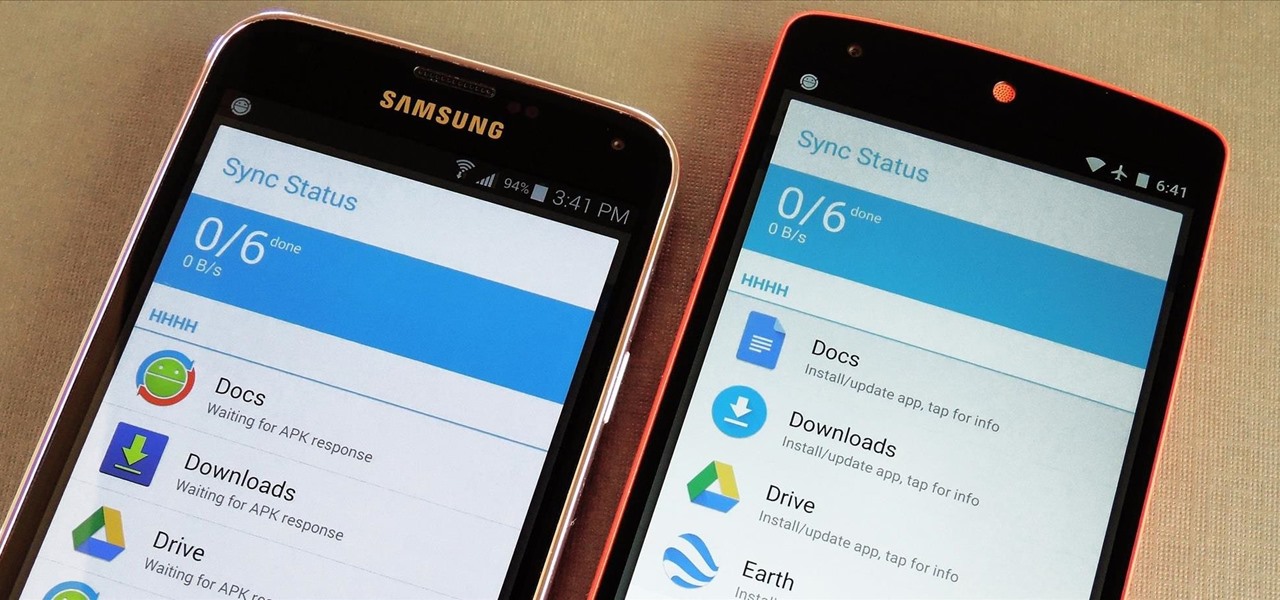
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.
There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...
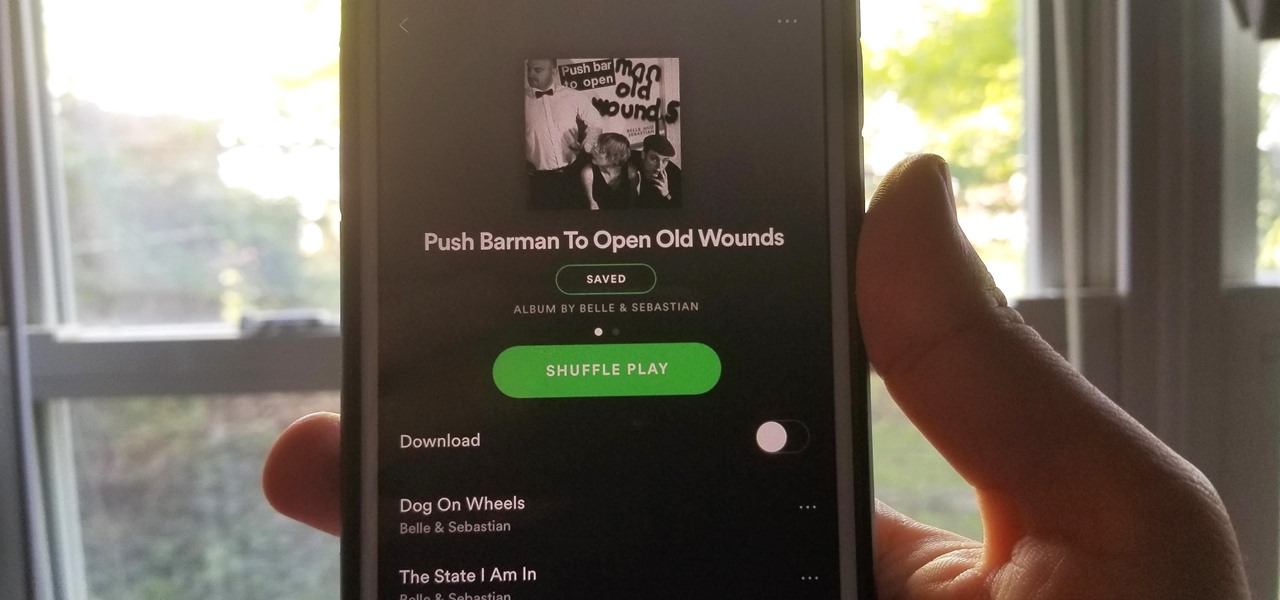
While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

These days, you can FaceTime with family and friends whether you're at home connected to Wi-Fi or on-the-go with mobile data. You may have noticed, however, that your iPhone will sometimes drop Wi-Fi and rely on cellular instead — whether you're placing or receiving a FaceTime call. While that's not an expected result, there is a workaround to get your FaceTime calls back on track.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

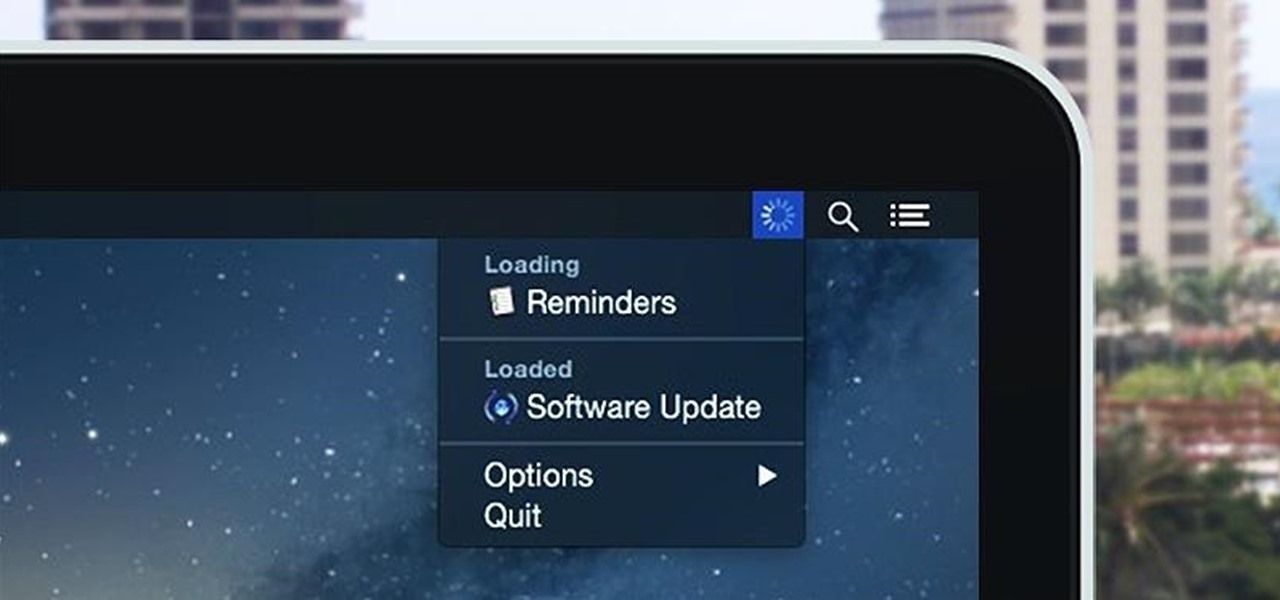
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

Oops... did you forget to connect to a Wi-Fi network before streaming HBO GO on your iPhone? While those episodes of The Wire may have been absolutely life-changing, your three-digit cellular bill is definitely going to hit you a little harder.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

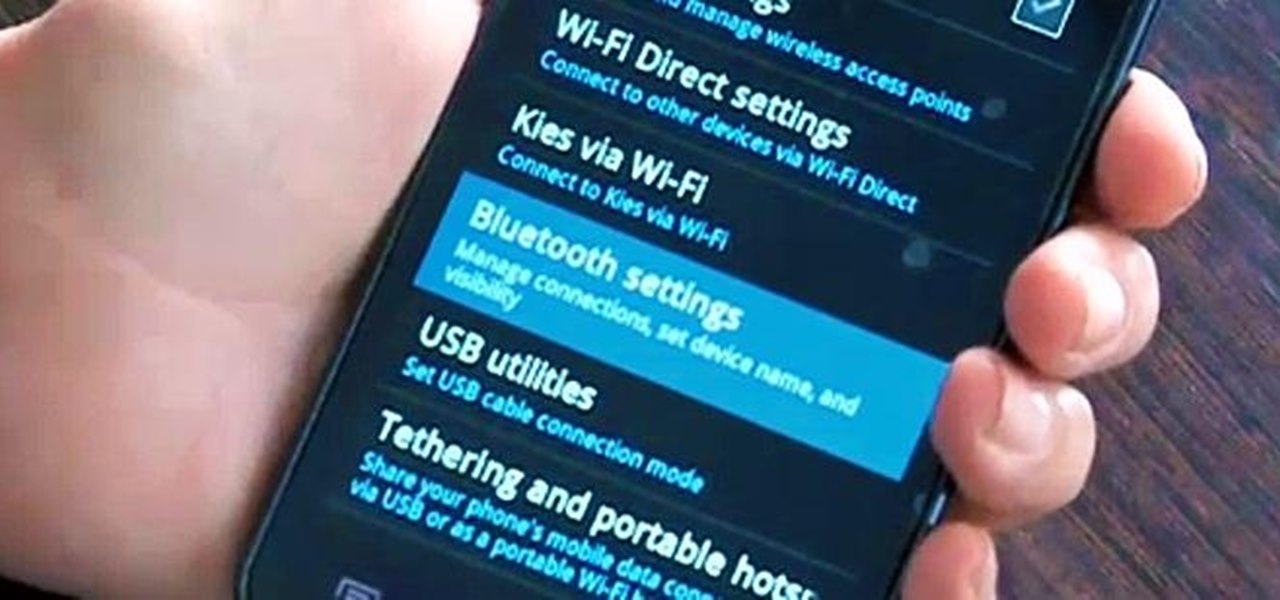
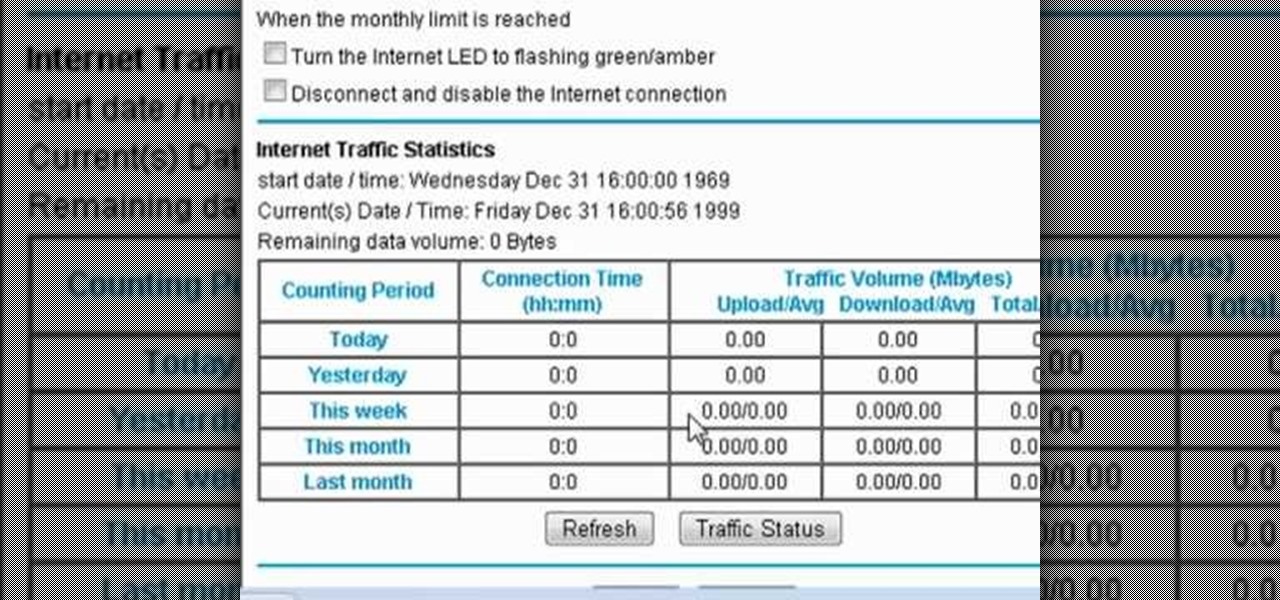
If your Internet plan includes a data limit, you might want to take certain precautions against accidentally exceeding it—like, for example, disabling your router This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about three minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

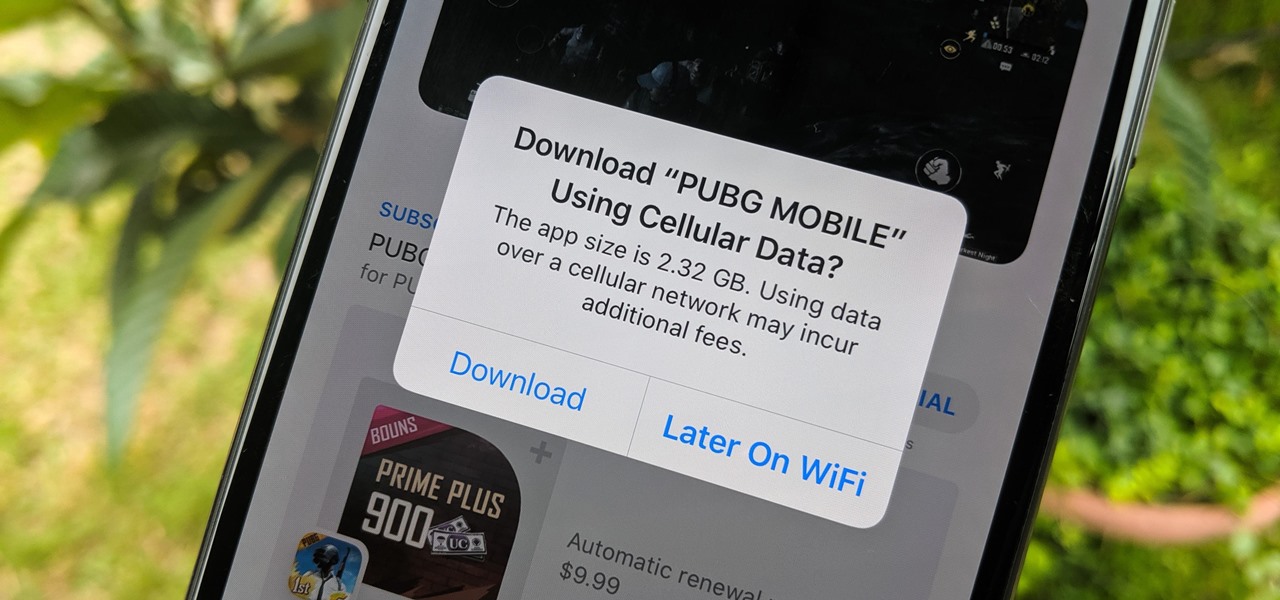
When there's a new game you want to play or app you need to use, but a Wi-Fi network isn't available, you can always download it over cellular data. If the size of the app is too large, however, you may not be able to on your iPhone. But that changes in iOS 13, which finally gives control over cellular data downloads in the App Store.

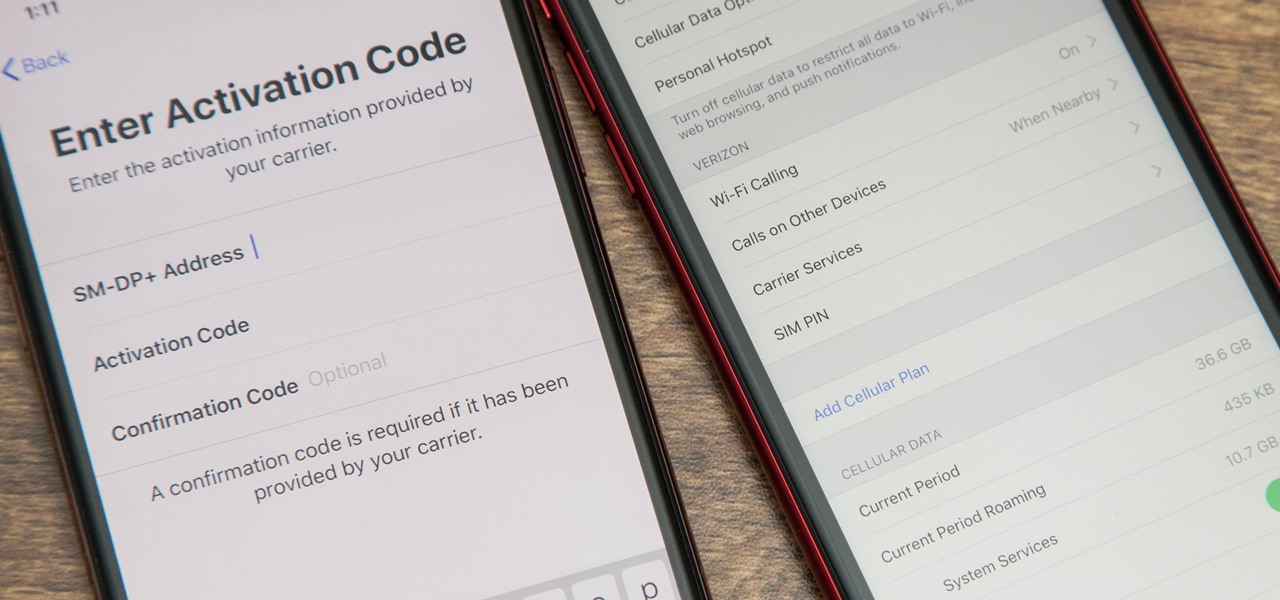
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.

This may not matter to you if you only FaceTime from your iPhone occasionally, but if you're FaceTiming every day on a limited data plan from your cellular provider, you're going to want to conserve as much data as possible by making sure that you're connected to Wi-Fi only — especially if they are video calls.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.

Verizon has long been king in the wireless provider market, but recently it has had to step up its game in the data department. A limited data plan — with supposedly superior service — was no longer cutting it for customers. Many of whom left to take up the sweet, sweet offers of competitors like Sprint and T-Mobile. This past fiscal year, Verizon had a net loss of customers in the first quarter. Something that has never happened to them before.

You can use MMS and Tethering on the iPhone 3GS. So first go to the settings and there you have to click on general and then go to network. there you can see Cellular data network, VPN, internet tethering etc.

In this video tutorial, viewers learn how to create drop down menus in Microsoft Excel. This task is very easy, fast and easy to do. Begin by highlighting a desired cell. Then click on the Data tab and click on Data Validation under Data Tools. When the Data Validates window opens, click on the Error tab and deselect "Show error alert after invalid data is entered". Then click on OK. Now simply type in the data into the selected cell. This video will benefit those viewers who use Microsoft Ex...

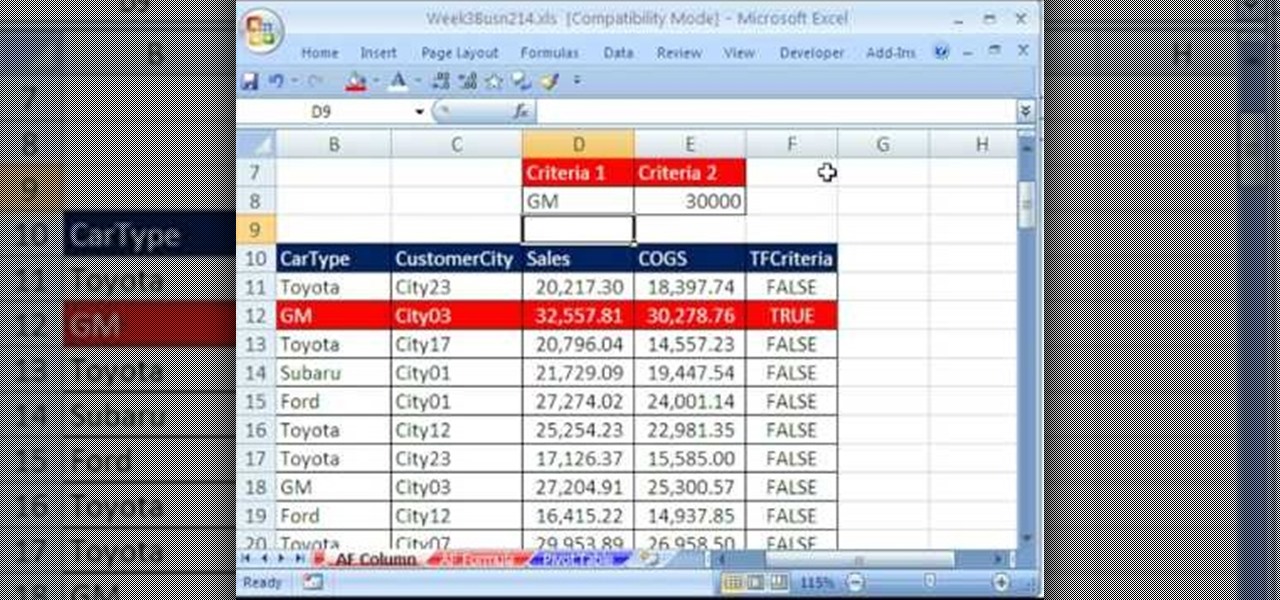
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 19th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about using Advanced Filter to extract data from an Excel List/Table/Database. See these 7 Advanced Filter examples:

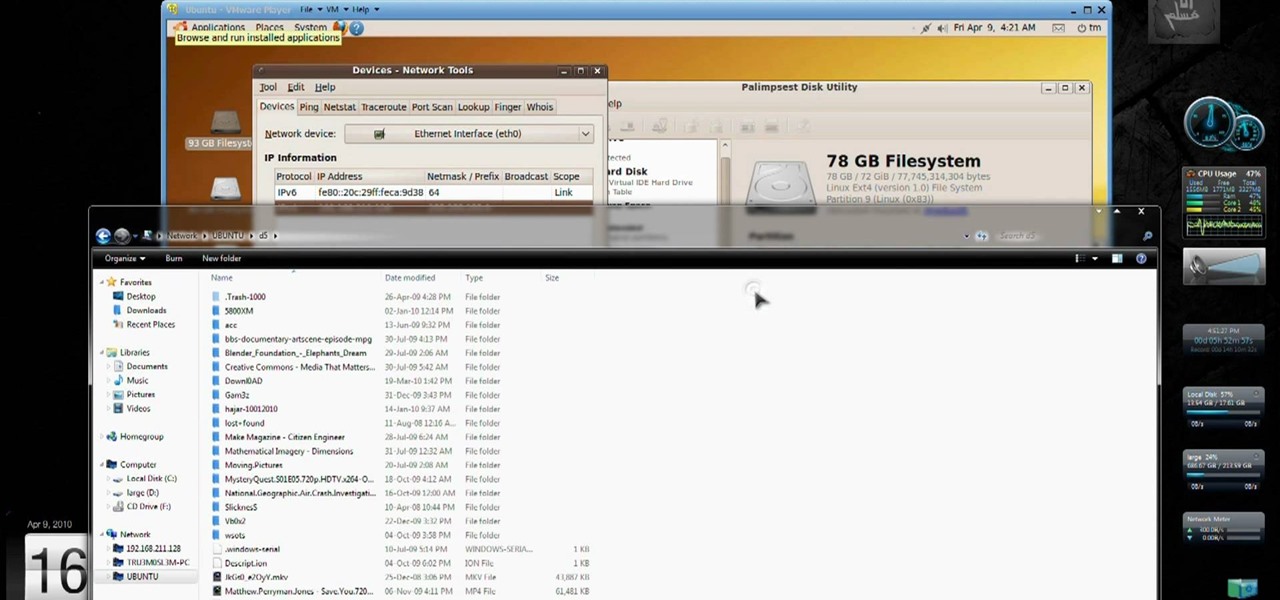
Want to access your Linux partition on your hard drive using Windows 7? With a little program called Vmware Player. So, check out this video tutorial to see how to see all of your Linux files on Windows 7 from your hard drive.

Core Data is a powerful data-management framework introduced with Mac OS X v10.4 Tiger. When you take advantage of Core Data, it slashes the amount of custom code you need to write in order to manage application data. Opening, saving and undo management can all be handled by Core Data, freeing you to concentrate on creating unique features for your application. This video tutorial, which presents a general introduction to using Core Data, will walk you through the process of building a simple...

Even Halo: Reach on the Xbox 360 has hidden collectable items! All in the convenient (for the people hiding them) size of a small data pad! Earlier you got access to the first 9 data pads that you can get on any difficulty. Next, you will get a look on the next 9 data pads that you can only acquire while being on Legendary difficulty!

Data thieves don't have to be programming wizards to get their hands on your personal information. They often find hard drives that contain financial and other sensitive data at flea markets, charity shops, the city dump—even on eBay. In this video tutorial, PC World explains how to completely erase sensitive data from old drives before recycling or discarding them. Wipe your old hard drives with this how-to.