Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Gigafide explains that with so many different social networking sites, it is hard to keep information up to date on all of them. He first introduces TweetDeck, an amazing desktop application that allows a user to update information for their Twitter, Facebook, MySpace, and LinkedIn accounts. If you don't want to go through the hassle of installing TweetDeck on your computer, there is HootSuite, a web application that allows you to do this and if you're interested in keeping track of much more...

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...
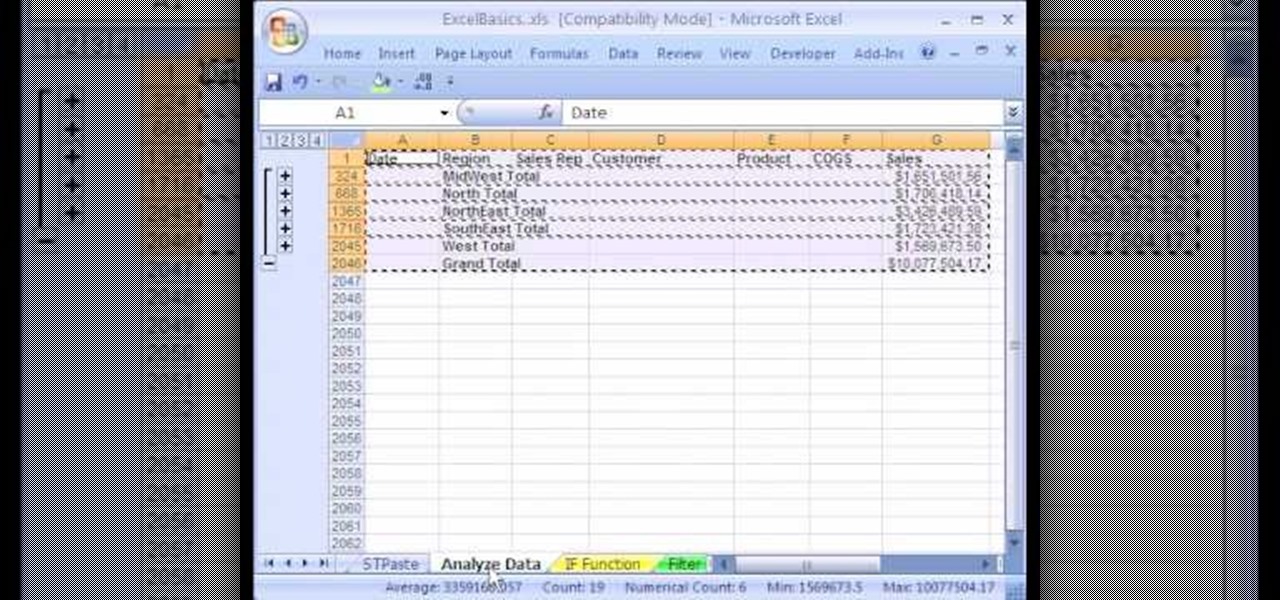
1. The following instruction describes how to generate sub totals in Microsoft Excel Sheet. 2. Take Region as a Primary column and Sales Rep as a Secondary Column. 3. First method to sort: Select a cell in Region and goto Data select A to Z. 4. Second method to sort: Select a cell in Region and Right click and select Sort A to Z 5. Then click a cell in Region and select Data->OutLine->SubTotal 6. In the SubTotal Window select 1.Each Change in: Region 2.Use function:Sum 3.Add subTotal to:Sales...

Need to sort a ton of data in Excel? Why waste time cutting and copying cells? In this tutorial, learn how make Microsoft Excel automatically sort columns or rows alphabetically.

Magicinwords teaches viewers how to change their facebook network! First, you will want to log onto Facebook.com. When signed in, go to the settings tab on the right of the screen. Under this, click on 'account settings'. Under account settings choose the tab that reads 'networks'. Here, you can click 'change your region' and then you can update it. Be sure this is right though, you can only change your regional network twice every 60 days. Under this same tab, you can also join any other net...

The video shows how to join a home group on a Windows 7 network by helves shows you how to join a home group on a Windows 7 network of computers. It is approximately one minute thirty seconds long. To join a home group on a Windows 7 network you first go to control panel, then you click on Network and Internet, after that you click on network and sharing center, and finally click join a home group in the top right. You now select what file types you want to share with the other Windows 7 comp...

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

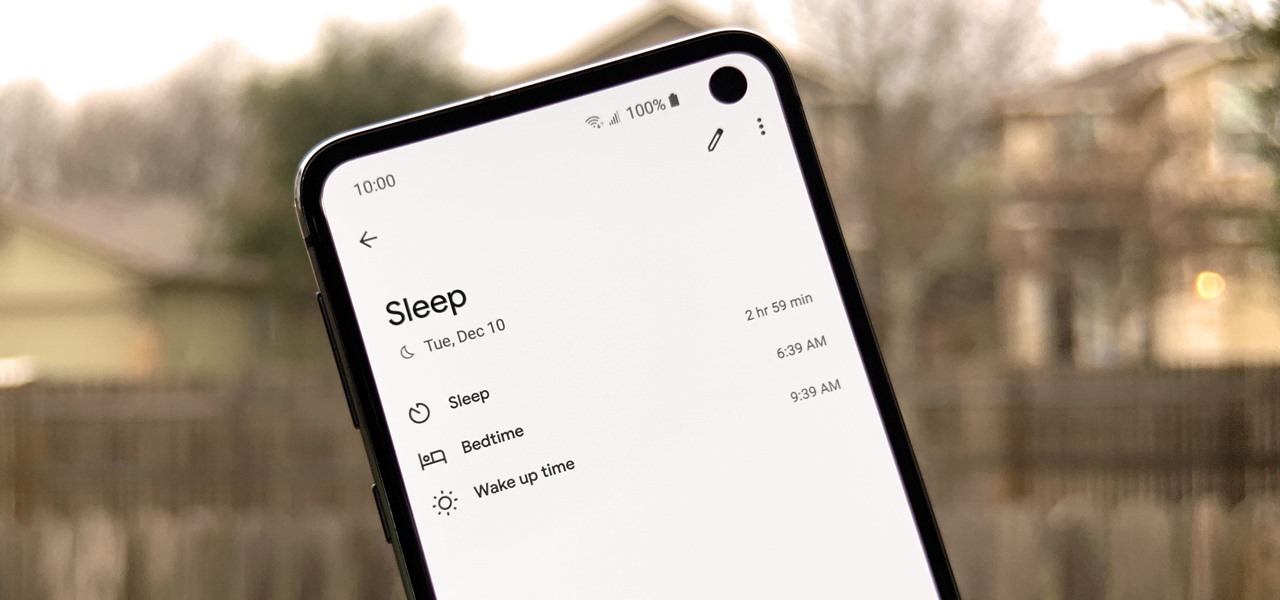
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

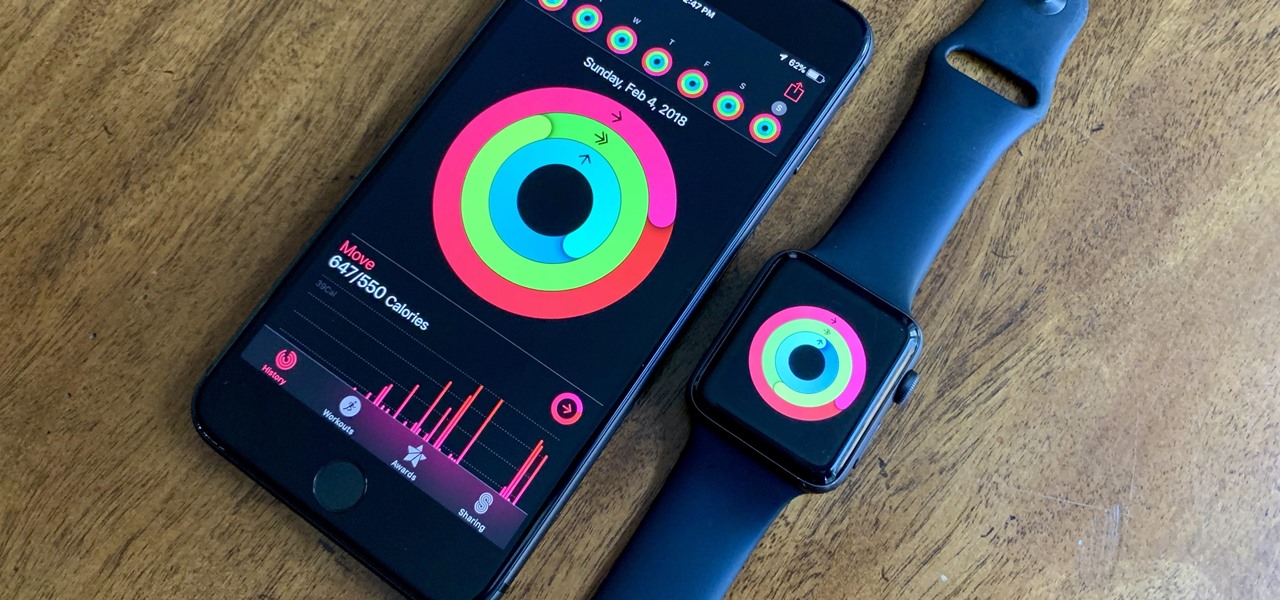
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

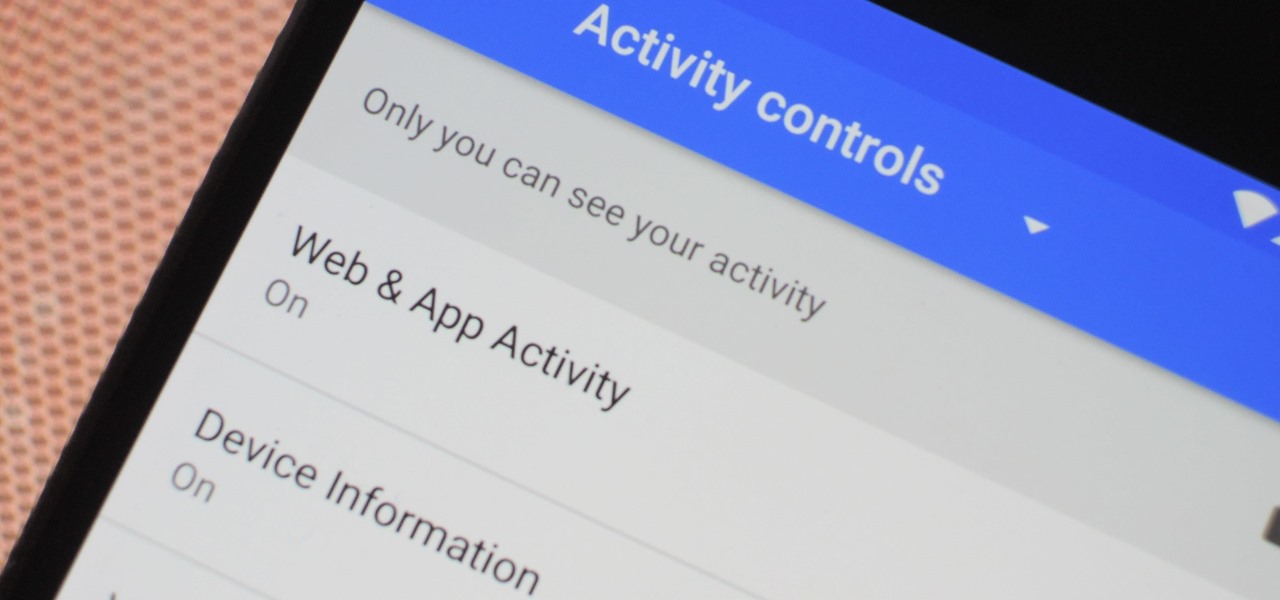
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

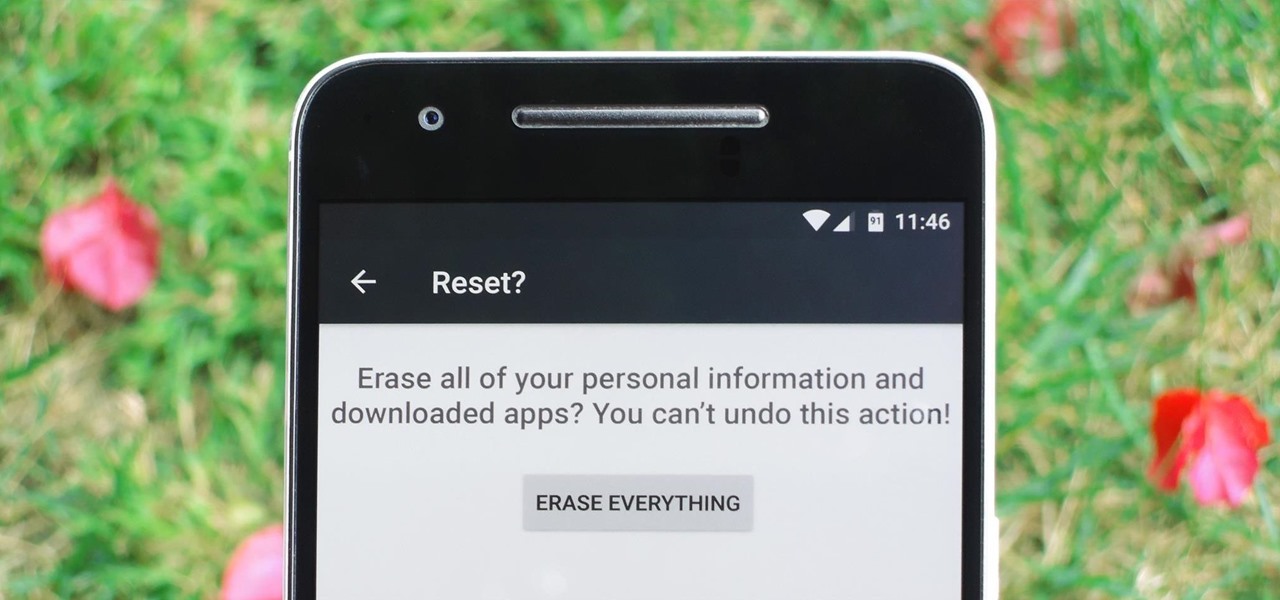
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.